CARP with single PPOE - Make internet working from the slave node
-
Hi all,
I have set up CARP on two nodes with PPOE as WAN and everything it's working properly, but WAN it's obviously up only for the main one because I can establish just one PPOE session to my ISP.Is there a way to make the slave node able to reach internet through the main one when the main is active? Because I'd like to upgrade to 2.4.5 and as documentation I should do it on slave node first, but I'm unable to upgrade (both pfSense and packages that are already ahead of the main one) because it's lacking internet access..
I've tried to add the main pfSense LAN interface as gateway, then create a new gateway group with PPOE WAN as Tier 1 and main pfSense LAN as Tier 2, then set the the new group as Default Gateway. It should be working, but the gateway with main pfSense LAN it's always down on both. I've used 8.8.8.8 as monitoring address, what could be the issue?
Thanks!
EDIT: I think I've found the issue, when adding an IP as monitoring, then it creates on the firewall itself a static route for that IP and it's always pointing at the interface IP instead of the monitoring IP. How can I solve that? I cannot put the interface itself as monitoring, because if the LAN interface it's up, it doesn't mean that WAN it's up as well..
-
So after some test and a suggestion by @viragomann I've found a workaround (I guess not supported, because even CARP with a single WAN IP it's not supported) that works as expected, so:
- Single WAN PPOE
- Keep sync active for all configuration, including static routes
- Do not block the public IPs used for monitoring
These are the steps required:
-
Create a new gateway with the CARP LAN address
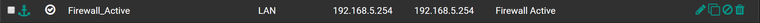
-
Create a new gateway group with WAN as Tier 1 and CARP LAN as Tier 2
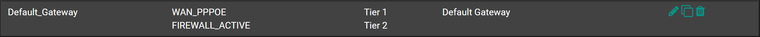
-
Set the new gateway group as default gateway
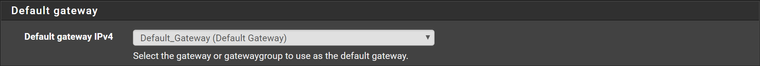
* Here the trick, create a Port Forward NAT rule with source Main and Backup pfSense LAN IPs, destination LAN CARP address and NAT Address the public IP that you want to monitor. IMPORTANT: NAT reflection must be disabled
EDIT: Probably it's not needed because even if the CARP Gateway won't reflect the real WAN status, it should be used only as Tier 2I'll test everything next week even in CARP Maintenance mode when probably I'll be onsite for 2.5 Upgrade, fingers crossed!
-
It survived also the CARP Maintenance and the upgrade of both units, without the Port Forward NAT.
The only issue is that in this way OpenVPN Client (to a VPN Service) binded to WAN interface will start on both nodes because both will have connectivity. Solution is to bind to a real CARP VIP like LAN and it correctly starts only on the node where LAN is MASTER.