Servers on same lan
-
So they are connecting using VPN? Did you add a firewall rule on the VPN interface allowing access to LAN?
-
@mururoa said in Servers on same lan:
and LAN interface 193.193.193.223 (once again fictive).
We al use 192.168.1.0/24 or 192.168.2.0/24, 10.0.0.0/24 etc
It's like talking about those wires behind a wall outlet, the one you use to plugin your TV. Theya ll use a bleu wire for neutral and red or brown for live (don't touch that one). No need to hide these colours on a public form neither.Which bring us to :
@mururoa said in Servers on same lan:
my clients can access every servers on every lan BUT no server on the LAN subnet.
That's ... I don't know.
You have this LAN network using example 192.168.1.0/24, being pfSense LAN's interface using the default 192.168.1.1 (yes, I know that already) a server using 192.168.1.2 - another server using 192.168.1.2 etc and your VPN users can access these servers.
What is your LAN subnet (for you) ? If you can access servers on the LAN, your can access the LAN subnet.@teamits said in Servers on same lan:
add a firewall rule on the VPN interface allowing access to LAN?
The OpenVPN wizard creates one. It should be there.
-
No, I did basic Server and client configuration.
So OpenVPN Wizard added only one rule on WAN for allowing UDP 1194 and one in OPENVPN section allowing IPv4.
Which rule should I add in which section (LAN, WAN, OPENVPN) ? -
@mururoa said in Servers on same lan:
OPENVPN
Is it called OPENVPN or OpenVPN ?
It should list something like :
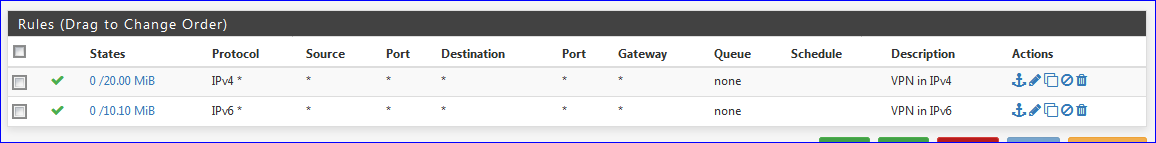
The second one, IPv6 is needed if you actually use IPv6.
They can even be combined these two in one rule.
Btw : these are pass-all rules. -
@Gertjan
I use only IPv4 so there is only the first one. -
What kind of servers are your servers on your LAN ?
-
@Gertjan
Any kind, with many subnets. 400+
Using OpenVPN, once connected I can access all subnets BUT the one of the LAN interface.
For exemple servers on the same subnet that the WAN interface.
WAN IP is xxx.xxx.182.4
I can reach xxx.xxx.182.10 (/24)
I can reach xxx.xxx.181.10 (/24)
I can reach xxx.xxx.159.126 (/24)
LAN IP is 192.168.135.223 (/24)
I cant reach 192.168.135.93
I cant reach 192.168.135.78
...
And if I connect from the openvpn connected client to the pfsense box (ssh 192.168.0.223) I can reach other servers in this lan like .93 or .78 from pfsense itself but not from the client directly. -
This server / LAN device : 192.168.135.93
@mururoa said in Servers on same lan:I cant reach 192.168.135.93
does it have this gateway 192.168.135.223 ? :
@mururoa said in Servers on same lan:
LAN IP is 192.168.135.223 (/24)
192.168.135.223 is the pfSense LAN IP, right ?
Btw : really ? Your LAN subnet is 192.168.135.0/24 and pfSense as a router has a LAN IP : 192.168.135.223 ?
Why not 192.168.135.1 or 192.168.135.254
Never understood why a gateway is thrown in the middle of a network like this.
Anyway, not really important. -
@Gertjan
So far I understand :
The client network is a local (IE between clients and pfsense box) not used elsewhere subnet.
In my case 192.168.144.0/24.
PFsense box has address 192.168.144.1 on this subnet and clients are .2, .3 ...
On my first client I have 192.168.144.2.
From there, on my routing table, on the client, I have :
none 0.0.0.0/1 via 192.168.144.1 dev eth2 proto unspec metric 0
none 128.0.0.0/1 via 192.168.144.1 dev eth2 proto unspec metric 0
So for anything outside other clients subnets, wich are 192.168.0.0/24 (client lan outside vpn) and 192.168.56.0/24 (client wifi outside vpn) all traffic goes to the pfsense box.
So far so good.
Then, on the pfsense box I have this :Internet:
Destination Gateway Flags Netif Expire
default xxx.xxx.182.1 UGS vmx0
127.0.0.1 link#4 UH lo0
xxx.xxx.182.0/24 link#1 U vmx0
xxx.xxx.182.4 link#1 UHS lo0
192.168.135.0/24 link#2 U vmx1
192.168.135.223 link#2 UHS lo0
192.168.144.0/24 192.168.144.2 UGS ovpns1
192.168.144.1 link#7 UHS lo0
192.168.144.2 link#7 UH ovpns1So, when packets are destinated to anything than 192.168.135.0/24 they goes through vmx0 (WAN) and when packets are destinated to 192.168.135.0/24 they should go through vmx1 (LAN). And this is the case if I connect to the pfsense box and then I can access anything on 192.168.135.0/24 like ssh 192.168.135.93 for example.
So so, I guess they are blocked because the correct rule(s) is(are) not set on pfsense box.
Or maybe a route to push somewhere.
What is this rule or route and where do I have to set it ? -
Routes are not to be mixed up with Firewall rules.
Firewall rules are for traffic that comes IN to an interface. pfSense is the "inside" in this point of view. Firewall rules do not apply to outgoing traffic (just forget about floating rules right now, themselves rarely being used)To be sure that firewall rules are not an issue, put on any (V)LAN type interface a first rule that is a pass-all rule.
Routes : every LAN type network that is not declared as a WAN type can reach other because an (LAN's) network mask matches. If there is no match with an existing local network, then a WAN type network is used to send the traffic out to have the traffic being handled by an upstream router.
In the vast majority of all possible network scenarios, there is no need to manipulate the routing table.
I know, I'm probably not answering your question.
What I want to say is : routing tables is never a problem. They can seem to be a problem if the network structure is fckd up severely.
In that case the network's logical structure needs to be redone. Not the routing table.Example :
Like you, I'm using the OpenVPN server build into to access my companie's nerwork.
My LAN is 192.168.1.1/24 - all companie's PC's, printers, file servers, backup units, etc are on this LAN.
A second LAN network uses 192.168.2.1/24
My VPN tunnel network is a third local network 192168.3.1/24 (and surely not 192.168.1.1/24 which will conflict with LAN - breaking the routing)
So, when I connect remotely, my PC @home will have a 192.168.3.2 IP.
Traffic going to my OpenVPN server comes into pfSense and can go
192.168.1.0/24 which is local
Anywhere else : the Internet, so it's leaving on the WAN interface.