Cert Manager Export Password
-
Dear Developers,
It would enhance productivity (e. g., when working with client certificates via FreeRADIUS or HAProxy) if the Cert Manager in general could allow picking an export password for p12 password packages downloaded. OpenVPN Client Export contains a very nice model for this, but it is focused on OpenVPN as the only (very worthwhile) purpose.
Regards,
Michael
-
Hi,
I would like to use pfSense User Manager and Certificate Manager to create a user and associated certificate for certificate based authentication for EAP-TLS WiFi and IKEv2.
When importing a .p12 certificate identity into OS X Keychain Access .p12 file a password is required. However the pfSense User Manager and Certificate Manager does not provide an option to specify the password for the .p12 file.
How can an password be specified for an .p12 export ?
-
I have this same issue on 2.3.2_1. Is there a solution or workaround?
-
I just add the password using openssl. I think one of the work arounds is using the vpn export client. I recall someone saying you could do it that way. But just simple openssl command to add a password to your certs and just combine them into a .p12
I thought I added this to doc file..
Yeah I did
https://doc.pfsense.org/index.php/Using_EAP_and_PEAP_with_FreeRADIUSClient Requires password on .p12
If your client will not load the .p12 without a password on it, and space does not work you can add a password with openssl
Just download user cert and key vs the p12 and with the ca cert use the following command
openssl pkcs12 -export -certfile ca.crt -in user.crt -inkey user.key -out user.p12I use this to use eap-tls on my iphone and ipad - ios requires a password.
-
I just add the password using openssl. I think one of the work arounds is using the vpn export client. I recall someone saying you could do it that way. But just simple openssl command to add a password to your certs and just combine them into a .p12
I thought I added this to doc file..
Yeah I did
https://doc.pfsense.org/index.php/Using_EAP_and_PEAP_with_FreeRADIUSClient Requires password on .p12
If your client will not load the .p12 without a password on it, and space does not work you can add a password with openssl
Just download user cert and key vs the p12 and with the ca cert use the following command
openssl pkcs12 -export -certfile ca.crt -in user.crt -inkey user.key -out user.p12I use this to use eap-tls on my iphone and ipad - ios requires a password.
Actually you can export a P 12 Right from PFsense, Then import that into Windows but just be sure to check "Mark this Key as Exportable" Then go Export the Cert and set a password.
-
Yeah you can do it that way as well. But there is no way that I know of to set the password as you export the p12 in cert manager on pfsense with password already on it. You can do it in the openvpn export, but that is also a work around.
-
Just wanted to note I submitted a bug to request some joy on this: https://redmine.pfsense.org/issues/8492
It's been helpful to have workarounds but they range from inconsistently effective to tedious.
-
@johnpoz
i have tried to set up EA-TLS an iphone as johnpoz suggest, but I haven't been successful.- if I download the p12 from pfsense directly, I can open the p12 but installation fails because password is missing.
- if I add a password using openssl as documented by johnpoz, then I can't open the p12 at within ios. I can rename it, but I can't open it. Not even an error, nothing.
I have also tries first installing the FreeRadius CA first, but it doesn't make a difference. It looks like ios cannot read the encrypted p12, so it doesn't even try further to open it. Am I missing something?
Thanks a lot -
@batistuta said in Cert Manager Export Password:
I can rename it, but I can't open it. Not even an error, nothing.
Then you did it wrong... Where did I say to download the p12.. download the cert and the key and put them in p12 with the openssl.. I just did this with my new phone a few weeks back...
Lets see your work.. Do you really need pictures?
Here just created newuser cert.. downloaded the ca, usercert, userkey put them in a p12, sent it to my phone via email.
You prob also going to want to send the ca.crt on its own so you can just install it so you trust the cert, etc.. but not really required to install it..
The go to your profile settings, then you will see the p12, put in your pin, and then it will ask you for the p12 password - bobs your uncle.
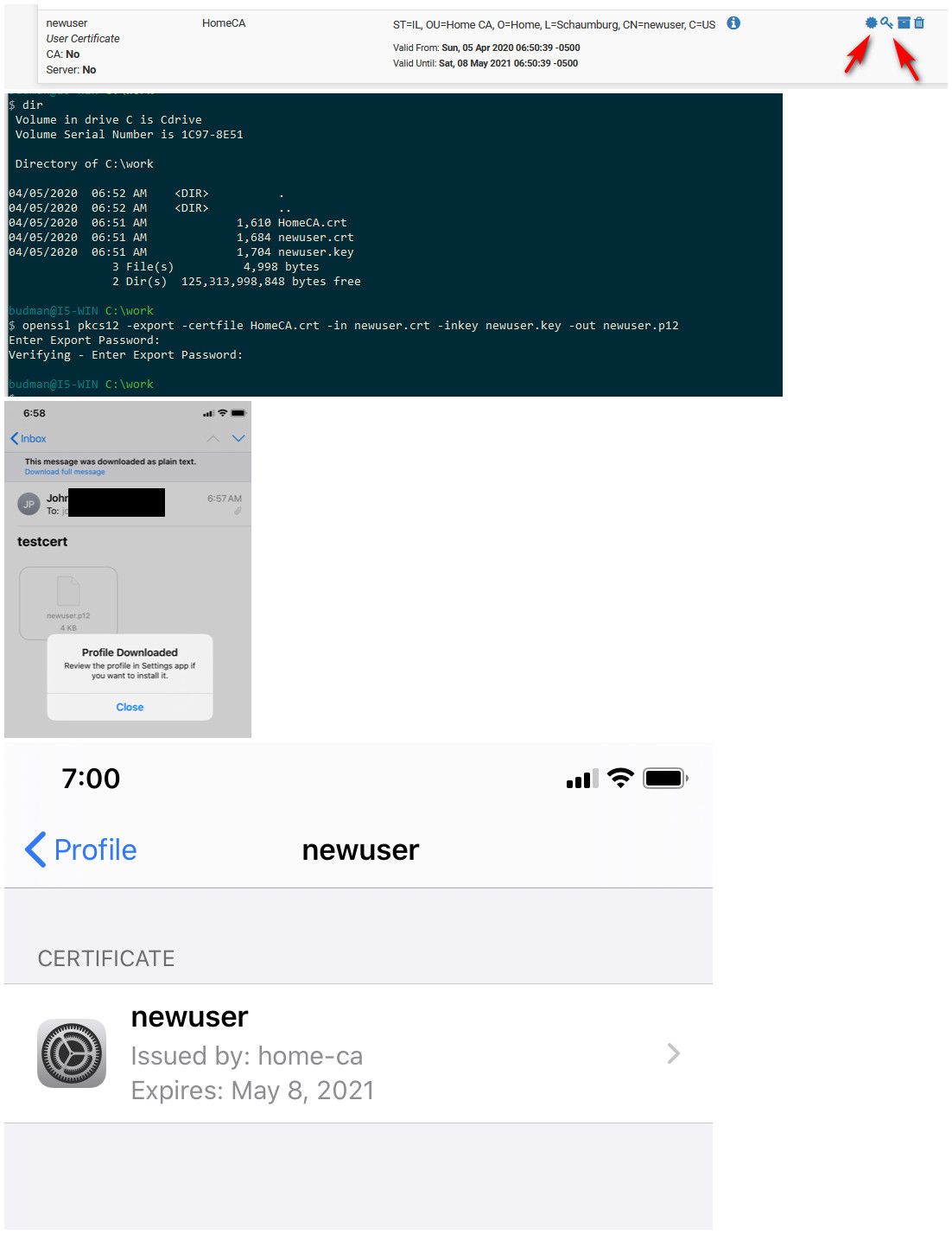
here - you can see now have that new ca in there, and my newuser cert just created.
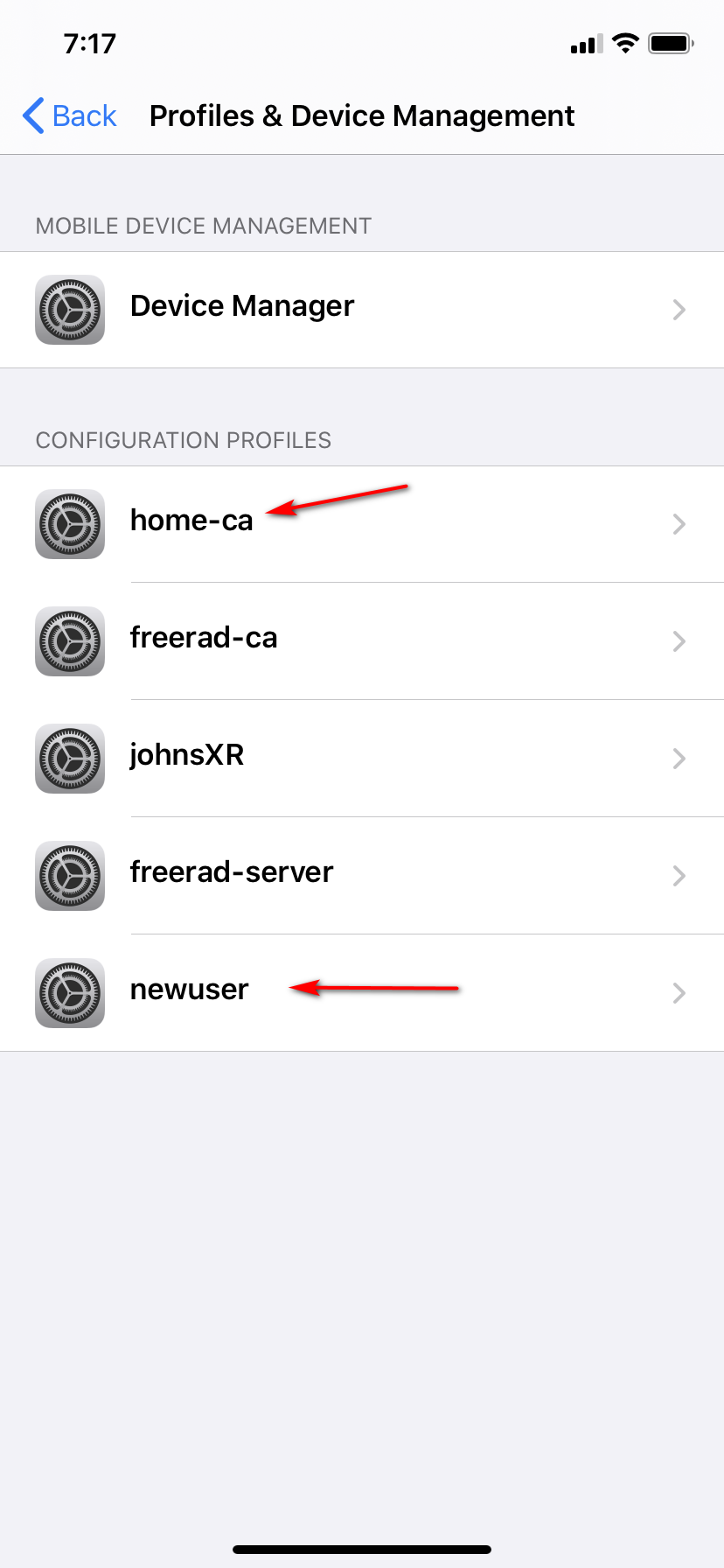
Along with my freerad server cert, and the freerad CA created, and my phones cert so I can get on my eap-tls authed wifi... Those have been on there from before. the newuser and homeca just added.. for the pictures.. now can remove since have no use for those..
If your having issues - show your work!! So can figure out what your doing wrong.
Once you install the CA cert on its own, you will see that your new user cert is now verified even.
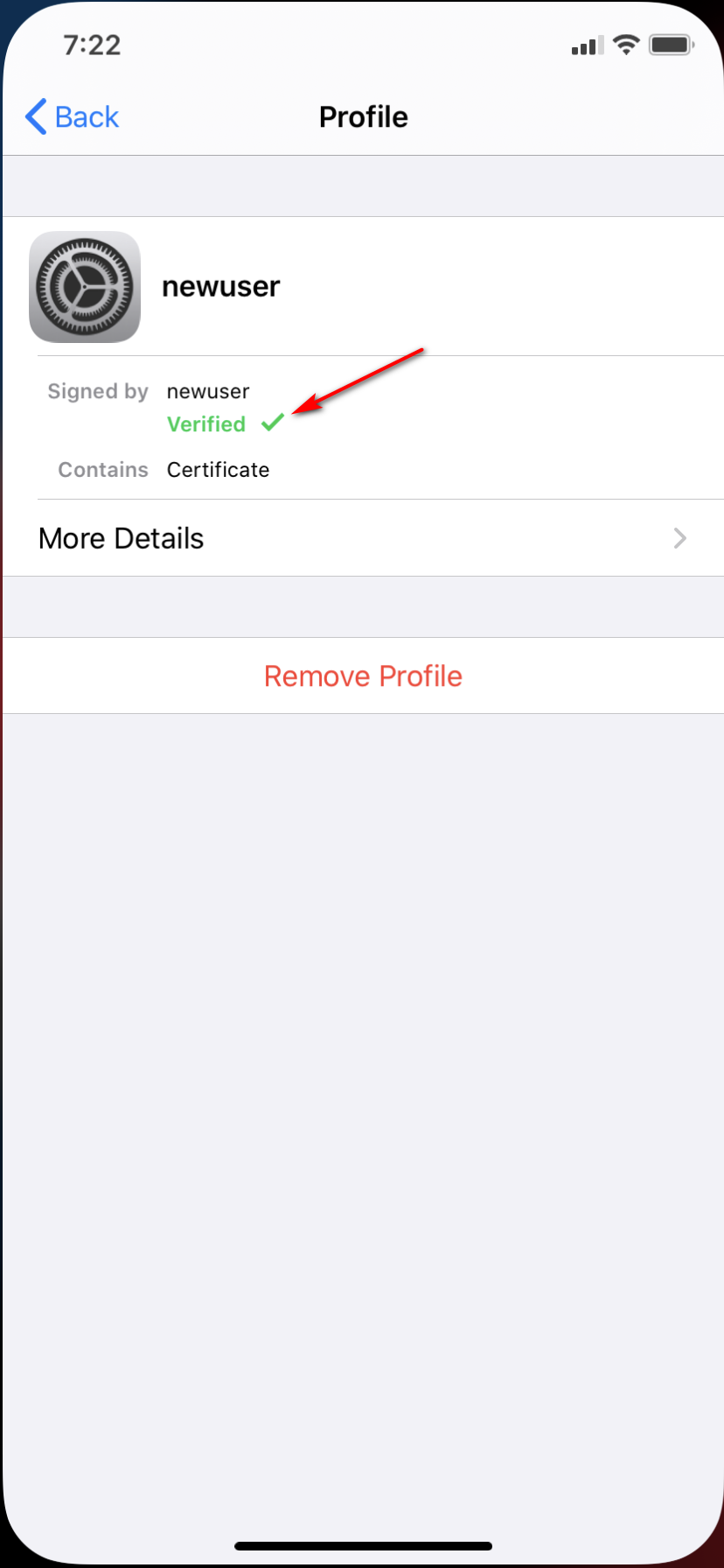
-
@johnpoz said in Cert Manager Export Password:
First, my warmest "thank you" for your detailed walk-through and patience along the way. Very much appreciated.Then you did it wrong... Where did I say to download the p12.. download the cert and the key and put them in p12 with the openssl.. I just did this with my new phone a few weeks back...
sorry if I wasn't clear. I was trying to explain what I tried (and failed):
-
first I tried what we all know it doesn't work: download the p12 from pfsense. The reason why I've mentioned this is because I could send this file via email, download the attachment to internal storage, click on it, attempt to install it, enter pincode, and then of course get stuck because the p12 doesn't have a password. But at least I got to that point.
-
then I also the workflow that you mentioned below. To recap: downloaded the CA.crt (FreeRADIUS CA in my screenshot below)
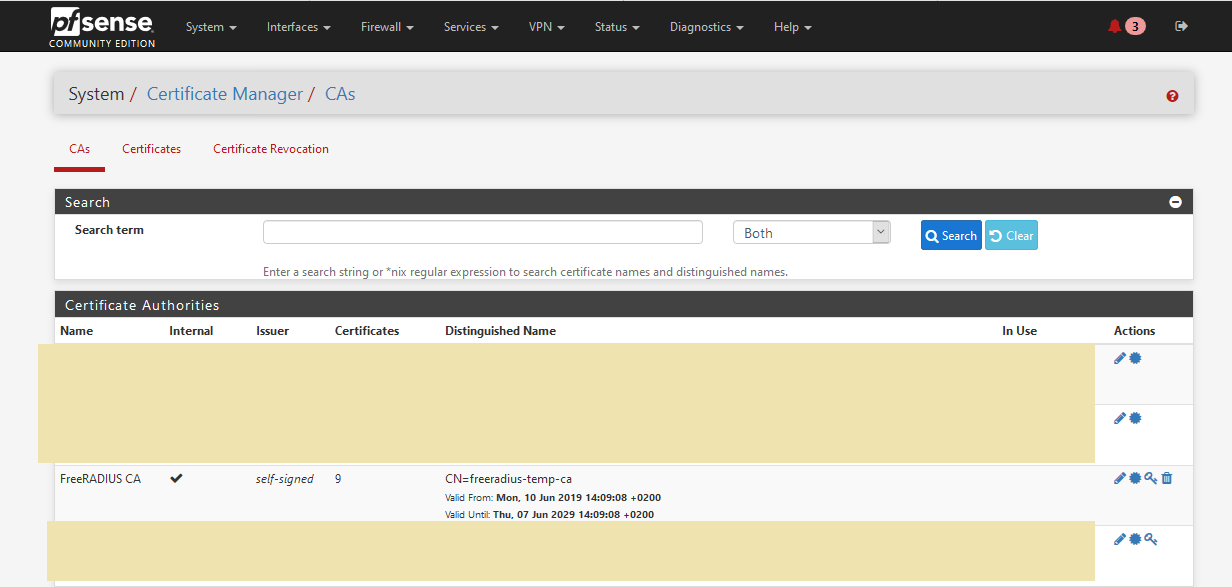
then nina_60.crt, and nina_60.key from pfsense
and encrypt them using openssl on a raspbian box
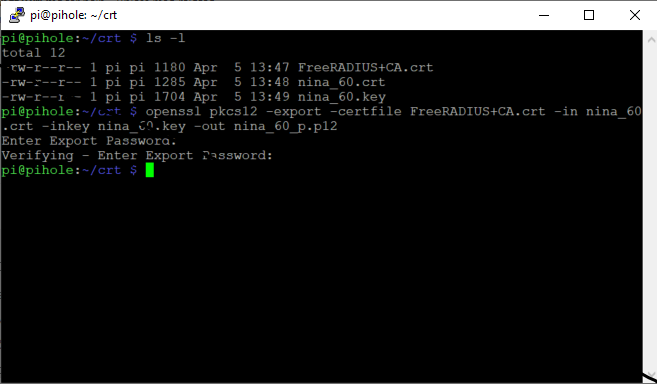
at this point I got the encrypted p12. I sent this to the iphone in question via emai. Downloaded the attachment into internal storage, and attempted to open it. This is where I got stuck. When touch the file icon in order to open/import the file nothing happens. No error, no response, nothing. As if I had not touched the screen at all. I can long press and go into "info"
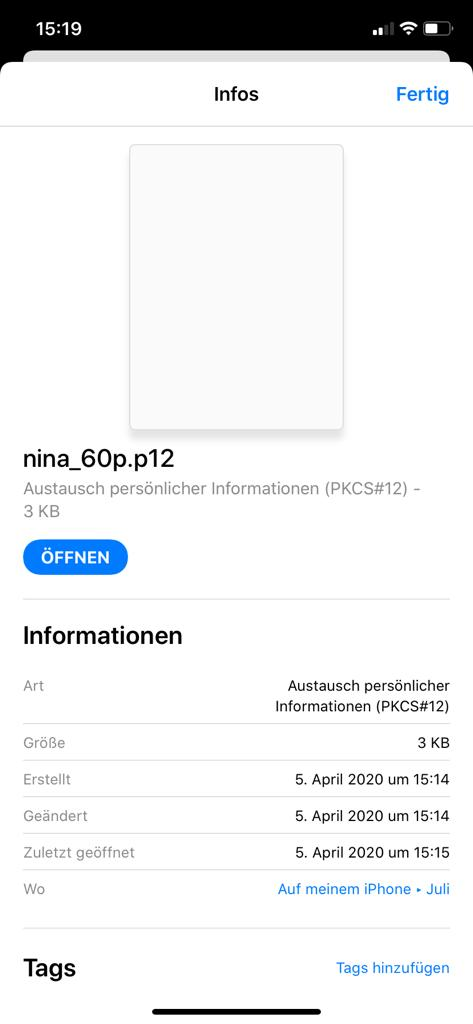
If I click on "Offnen" (open), nothing happens. It looks to me as if iOS is somehow refusing to open a file that it can't pre-parse/preview itself. So this is where I got stuck.
I hope this helps to explain the issue better and can find the root-cause. Thanks again!
-
-
Once you have the p12 file you install it in your profile section... look in general profiles - do you see it there to install..
See the popup I showed where it says to look in profiles - did you miss that? As soon as you download the file from say your email attachment - that is where it will go.. Atleast in Ios 13.4 which is what I am using.. But its always been that way from what I can remember..
-
@johnpoz said in Cert Manager Export Password:
See the popup I showed where it says to look in profiles - did you miss that?
It is a very valid point. It is easy to miss. But I haven't. Going back to the two things I have tried.
- If using the unencrypted p12 (which I know it is not meant to work): when I click on it, I see the pop up at the bottom saying that I have to go to my profiles to add it. If I go to general-->profiles I can see it there, I can click to install it, enter the pin code, and then I get stuck waiting for the password. But the p12 does get sent to profiles and an install can be attempted.
- when using the encrypted version, nothing happens when I click on the p12 file. When I say "nothing", I mean as if I had not touched the screen at all. No error, no "open with" menu, nothing.
UPDATE: I have noticed that you used the Windows version of openssl. So just for the sake of it, I decided to install it and give it a shot. Surprisingly, it worked this time. Thinking that there can't be a difference between the two openssl, my head pointed towards the transfer between my raspbian and my Windows computer. Per default winscp transfers text file, and apparently doing this messed up the base64 and made it unusable for the encrypted version. After repeating the process with a binary transfer mode, I could import that encrypted p12 as well.
So in the end, I could solve the problem and I hope this can help someone else. Thanks a lot @johnpoz for pointing me in the right direction. Without your screenshot I wouldn't have thought about looking into that and find the root-cause.
-
F furom referenced this topic on