Encrypted GRE tunnel from Pfsense to Cisco Router
-
Hello,
I work for a MSP, we use GRE encrypted VPN tunnels to our customers to provide support and access to there Hosted servers, we have been Cisco focused, but are now getting customers asking if they can use Pfsense. We use iBGP to peer with our customers to provide ISP failover. I am having an issue encrypting a GRE tunnel between our Cisco router's and a test PFsense box. I am able to configure the GRE and iBGP peer on Pfsense but am unable to find a compatible ipsec configuration to match the Cisco router's.
Cisco Router Config
GigabitEthernet0/0/0 = 172.16.1.25 (substitute IP Address)crypto isakmp policy 14
encr aes 256
hash sha256
authentication pre-share
group 14crypto isakmp key *************** address 172.16.1.10 (substitute IP Address)
crypto ipsec transform-set aes256sha-trans esp-aes 256 esp-sha-hmac
mode tunnelcrypto ipsec profile PROTECT_GRE
set transform-set aes256sha-transinterface Tunnel180
description *** Test Tunnel to Pfsense ***
ip address 10.180.90.1 255.255.255.252
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source GigabitEthernet0/0/0
tunnel destination 172.16.1.10 (substitute IP Address)
tunnel protection ipsec profile PROTECT_GRE -
Hello
try using when setting up phase 2
mode transport
on both sides of the tunnelcon2000{1975}: INSTALLED, TRANSPORT, reqid 56, ESP SPIs: caa90ec3_i c23ff48d_o con2000{1975}: AES_CBC_256/HMAC_SHA2_256_128, 17826138 bytes_i (18420 pkts, 2s ago), 3228172 bytes_o (17177 pkts, 2s ago), rekeying in 14 minutes con2000{1975}: 79.XXX.XXX.XXX/32|/0[gre] === 37.XXX.XX.XX/32|/0[gre]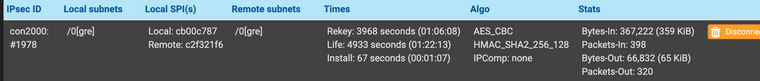
conn con2000 fragmentation = yes keyexchange = ikev2 reauth = yes forceencaps = no mobike = no rekey = yes installpolicy = yes type = transport dpdaction = restart dpddelay = 10s dpdtimeout = 60s auto = route -
Thank you! that was the combo i needed the VPN is up and stable. Now I just need to figure out why my BGP neighbor relationship is flapping :)
-
Can you post your pfSense config by chance? I am trying to do the same thing, but have trouble with the pfSense GRE tunnel coming up. Thanks!
-
I am sorry, I no longer have this up and running.
-
No worries. Thanks anyways!