OpenVPN and static IP for ALL clients
-
@noplan said in OpenVPN and static IP for ALL clients:
ifconfig-push 1.2.3.4 255.255.255.0;
What is wrong with the below setup?
The domain username is not TEST (it is DOMAIN\USERNAME, actually I don't even enter the DOMAIN\ part when authenticating with the OpenVPN prompt), but that shouldn't matter correct? It's just based off the CN name?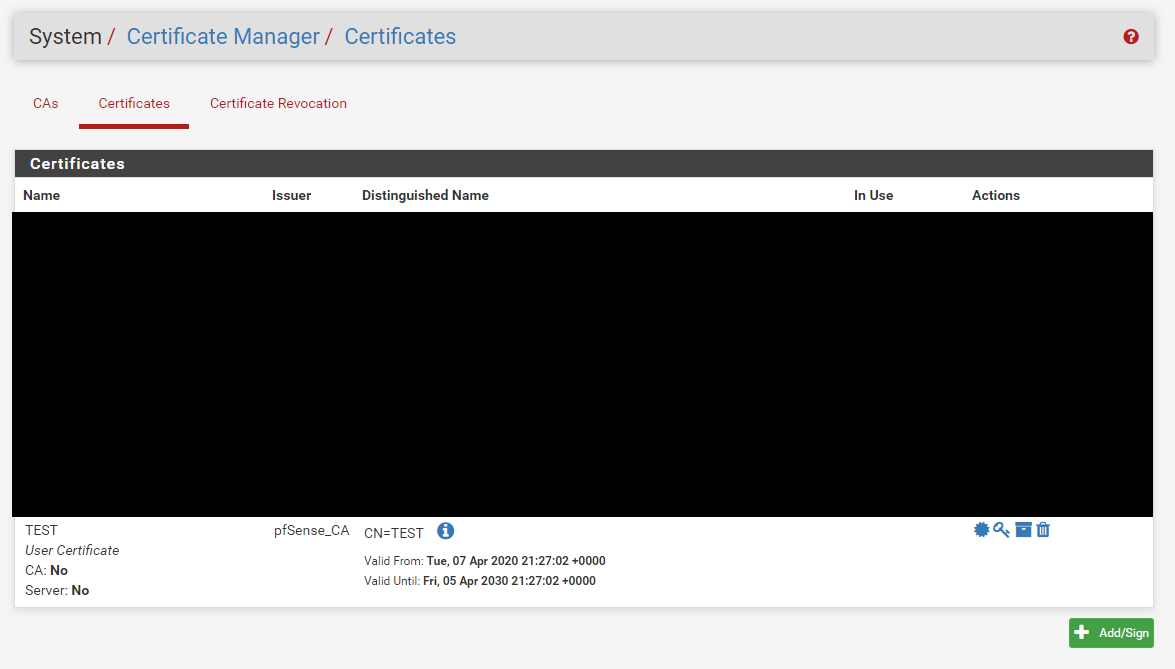
-
i use this here (and remember i use exact copy n paste) in:
and still in User Management:
u have to klick Crate a user certificate
and in client spec overrides :
and it works ...
read my other comments in this post why i use Advanced / ifconfig-push...(edit 10/04/20 more screenshots as requested)
brNp
-
@noplan said in OpenVPN and static IP for ALL clients:
i use this here (and remember i use exact copy n paste) in:



and in:

and in client spec overrides :

and it works ...
read my other comments in this post why i use Advanced / ifconfig-push...brNp
Can you take larger screenshots to see more of the page? I'm not sure where this username field would be...
-
done added more screenshots
-
@noplan said in OpenVPN and static IP for ALL clients:
done added more screenshots
So my users are domain users. How would using the User Manager certificate work?
This link shows that using User Certificates is not part of the process.
https://fastinetserver.wordpress.com/2013/03/09/pfsense-openvpn-static-ip-for-clients/Pictures for location reference
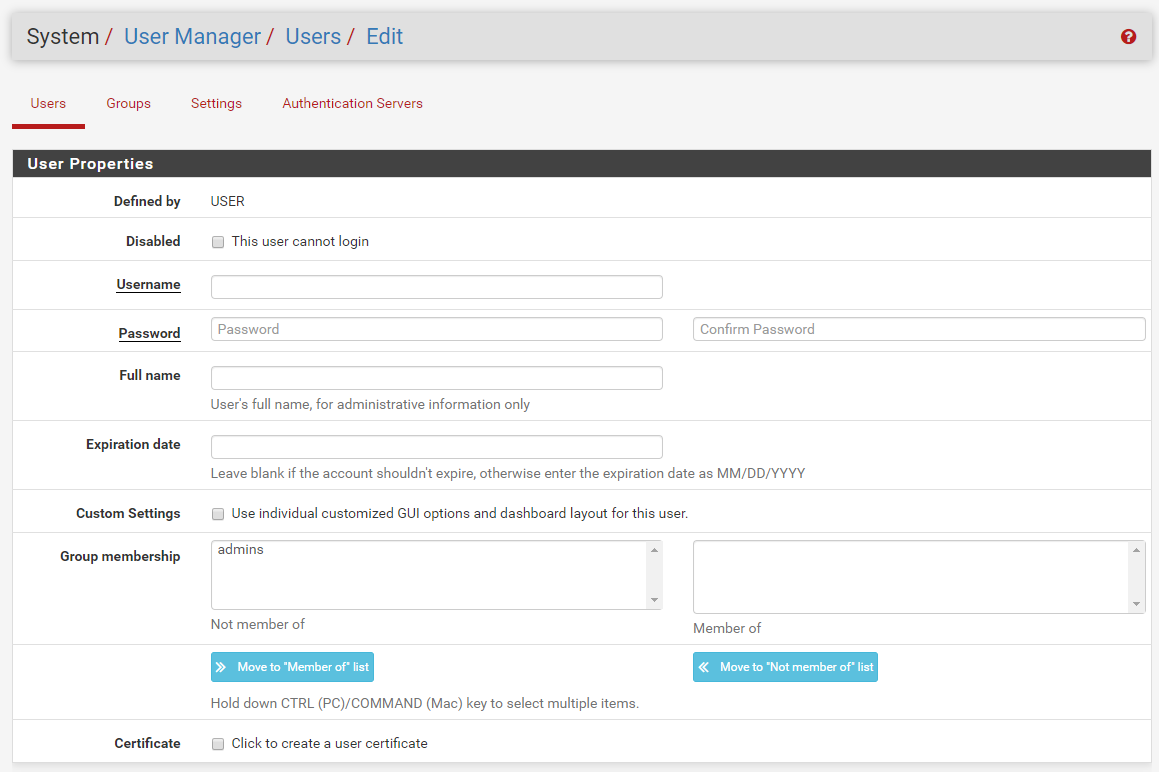
User Manager User Certificate
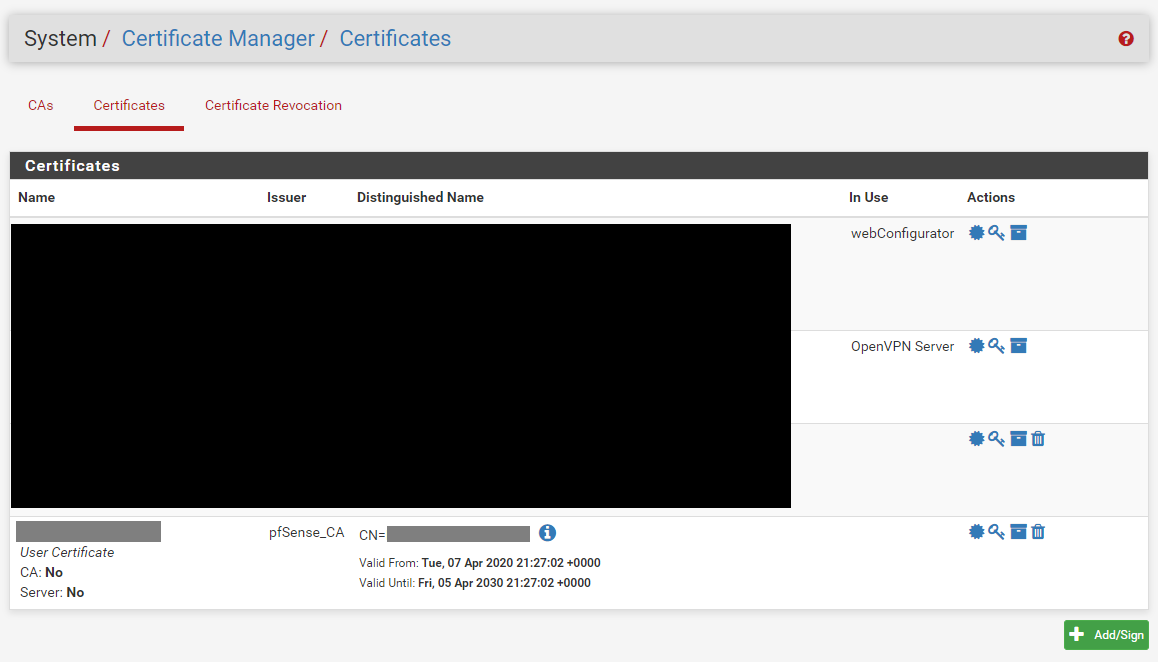
Certificate Manager Certificate
-
hey @ThePieMonster
dont get me wrong ...
add a user / click to add a user certificate
and follow the instructions here in that post. and test it if it works for you then go to the next step.
(all of the information you need is provided here)as far as i m concerned the link --> klick you provided is a) from 2013 and b) mentions as u can see in the screenshot
that User Certificates is part of the process.
possibly the next step my be
check how to import the DOMAIN User Cert to pfS ore use the domainUserDB as Backend in pfS
and test the whole loop again, let me mention that it would be pretty sweet when you keep us all informed how it works / or even not. But this is not part of this topic i think, cuz static IP for VPN-clients is pretty much solved here.br nP
-
If you need per-client firewall rules, a more efficient way is to use Cisco-AVPair RADIUS ACLs:
https://docs.netgate.com/pfsense/en/latest/book/openvpn/controlling-client-parameters-via-radius.html -
oh yeah i like that, but lack of useCase :(
i think @ThePieMonster needs a static IP for his vpn-clients
but a static Ip only helps when rules are set ;) so whats NEXT ! -
As I mentioned the user cert is from the the Certificate Manager / Certificates section of pfSense, not from the User Manager section. There are two locations where a user certificate can be created.
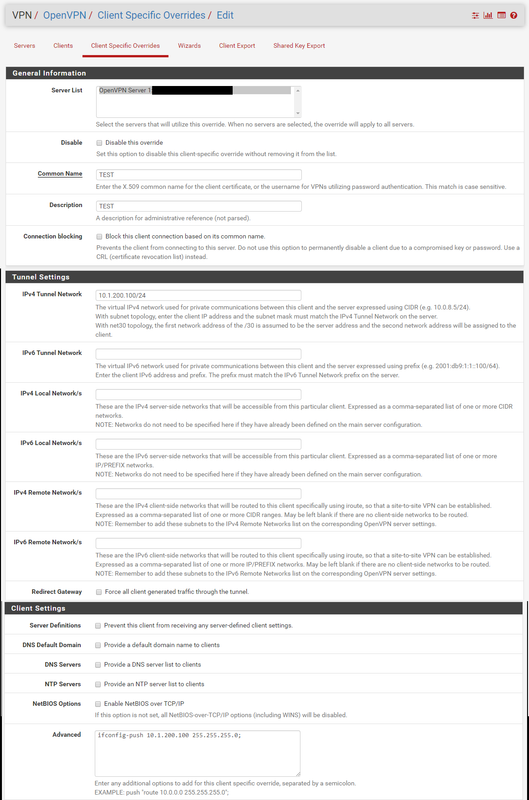
I also found out today, that the common name, is not the CN name of the cert, that can be whatever you like, but the username of the domain user. Switching this info around in the client override solved the issue for me.
TLDR: CN = Domain Username, not Certificate name.
-
@ThePieMonster said in OpenVPN and static IP for ALL clients:
Switching this info around in the client override solved the issue for me.
so please mark this posting als SOLVED !
-
@noplan I would but I'm not OP. :)
-
There seems to be some mis-information in this thread.
You do not need to add the custom push line in a Client Specific Override. Adding the tunnel network as an IP address already does exactly that.
You often do need to restart the OpenVPN server to read in the CSOs: https://redmine.pfsense.org/issues/10337
That should probably be marked a feature though, nothing has changed there.Steve
-
@stephenw10 said in OpenVPN and static IP for ALL clients:
You do not need to add the custom push line in a Client Specific Override
as i mentioned earlier
the reason why i added it and still doin itthere are clinets out there in the wild where the CSO is not working without
the custom push added.thanks for pointin me to issue 10337
brNP
#staysafe -
@ThePieMonster said in OpenVPN and static IP for ALL clients:
I also found out today, that the common name, is not the CN name of the cert, that can be whatever you like, but the username of the domain user. Switching this info around in the client override solved the issue for me.
TLDR: CN = Domain Username, not Certificate name.
You can change this behavior on 2.5 branch,
or by applying patch https://redmine.pfsense.org/issues/8289 on 2.4.4/2.4.5 -
I would suggest those clients must have typo or similar because adding the custom line does exactly the same thing.
For example I created a CSO for a user with a cert CN oftestand added only this: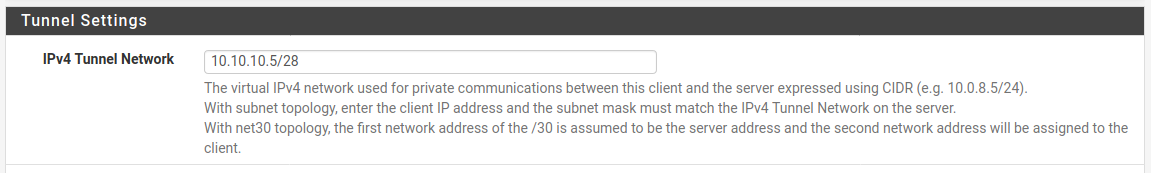
If I check what that actually creates:
[2.4.5-RELEASE][admin@google.stevew.lan]/root: cat /var/etc/openvpn-csc/server2/test ifconfig-push 10.10.10.5 255.255.255.240If I now add the custom line in addition:
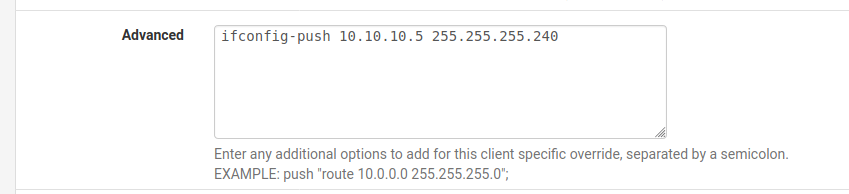
I now get:
[2.4.5-RELEASE][admin@google.stevew.lan]/root: cat /var/etc/openvpn-csc/server2/test ifconfig-push 10.10.10.5 255.255.255.240 ifconfig-push 10.10.10.5 255.255.255.240Clearly both those lines are not required!

Steve
-
tested it with some older android clients right now
without the ifconfig-push not working on device
added the lines working
maybe / pretty shure it is the client not the config on the Server