I made a WireGuard package for pfSense
-
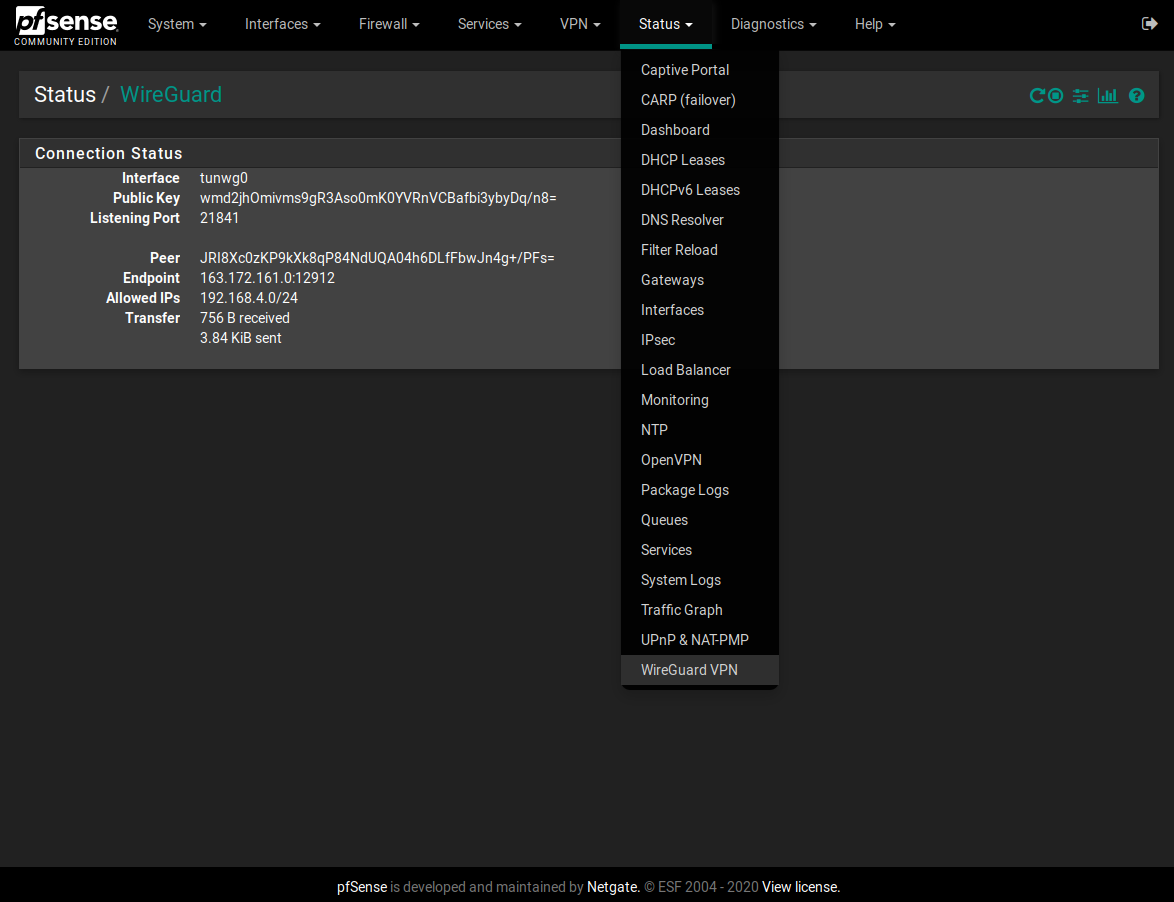
The VPN from my mobile already works!
In addition to opening the UDP port in WAN and allowing the necessary traffic in WIRE (tungw0), so that the mobile can go to the internet, it is necessary to create a manual outbound NAT witch source 10.23.5.0/24 rule in my case.
-
Is this plugin compatible with the new 2.4.5 release?
Has anyone done a performance comparison with ipsec and openvpn so far?Anyway, thank you and keep up with the good work!

-
I would also love to know if anyone has tried this out on 2.5, I imagine there could potentially be an issue because of the kernel update? But I have no clue myself.
I just updated to 2.5 and was wondering if there was any update on wireguard working and of course only saw that someone had figured out a way to get it working after I updated.
I'm so glad that someone decided to try to make it work! Been waiting on wireguard integration for too long. Keep up the great work!
-
@oneiro I intend to upgrade my router to 2.4.5 soon, along with
wireguardandwireguard-go, and will post results; since it's a security/maintenance release, I don't expect too many issues.@BRH212 Unfortunately I don't have a spare physical machine to use for testing 2.5, but I did install all three packages on a VM and did some preliminary testing. Haven't see see any issues with the UI package so far.
Keep in mind that this package is only an interface for the
wireguardandwireguard-gopackages (which I am not involved in the development of). You could theoretically use WG on pfSense without my package and it should still work, you'd just have to configure it from the console instead of the web UI.Also, be sure that the versions of
wireguardandwireguard-gothat you install match the version of FreeBSD for your pfSense install, otherwise you could potentially run into some issues. pkg should warn you if there's a version or architecture mismatch when attempting to add a package. -
I would like to give this a try but I’m not a CLI person so don't know how to install the package or where to even start. Do I unpack the compressed file(s) and use something like WinSCP to place them into the directory? Thanks in advance
-
This post is deleted! -
All right, I upgraded to 2.4.5 and so far I'm not seeing any issues. During the upgrade process
pfSense-pkg-wireguardwas removed, and after reboot I had to remove the oldwireguardandwireguard-gopackages before adding the new ones. I'm now using wireguard-1.0.20200319_2 and wireguard-go-20200320.@S762 Perhaps this page would be helpful to you? Assuming you haven't downloaded anything yet, you can use the command
pkg add http://<url_to_pkg>to download and install a package from a URL - no need to unpack anything.If you're using pfSense 2.4.5 like I am, you can use these commands on the command line interface, or the Command Prompt page on the web interface:
pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-1.0.20200319_2.txz pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz pkg add https://github.com/Ascrod/pfSense-pkg-wireguard/releases/download/v1.0.0/pfSense-pkg-wireguard-1.0.0.txz(I cannot stress enough that you should heed all the warnings about how using the command line or installing outside packages can possibly break your system. This is all very experimental and not officially supported in any way, and not for the faint of heart. If you don't mind taking a risk and/or are comfortable with the possibility of having to fix or reinstall your firewall, and you still want to try it out, make a configuration backup first!)
-
@Ascrod So I found this yesterday and I tired it for the first time just now. I'm on 2.4.5 and I used the links from your post just a few hours ago. I got no errors, but if I can into Assign Interfaces I don't see it. I see the Wireguard package status in my dash and it is stopped, but when I try to start it then it tries for a bit and then fails. The system log shows these entries every time I go through that process;
Apr 12 12:29:22 kernel tunwg0: link state changed to DOWN
Apr 12 12:29:22 kernel tun0: changing name to 'tunwg0'
Apr 12 12:29:22 kernel tun0: link state changed to UP
Apr 12 12:28:26 kernel tunwg0: link state changed to DOWN
Apr 12 12:28:26 kernel tun0: changing name to 'tunwg0'
Apr 12 12:28:26 kernel tun0: link state changed to UP
Apr 12 12:27:41 kernel tunwg0: link state changed to DOWN
Apr 12 12:27:41 kernel tun0: changing name to 'tunwg0'
Apr 12 12:27:41 kernel tun0: link state changed to UP
Apr 12 12:27:34 kernel igb3: promiscuous mode enabledAny ideas what it could be tripping up on?
-
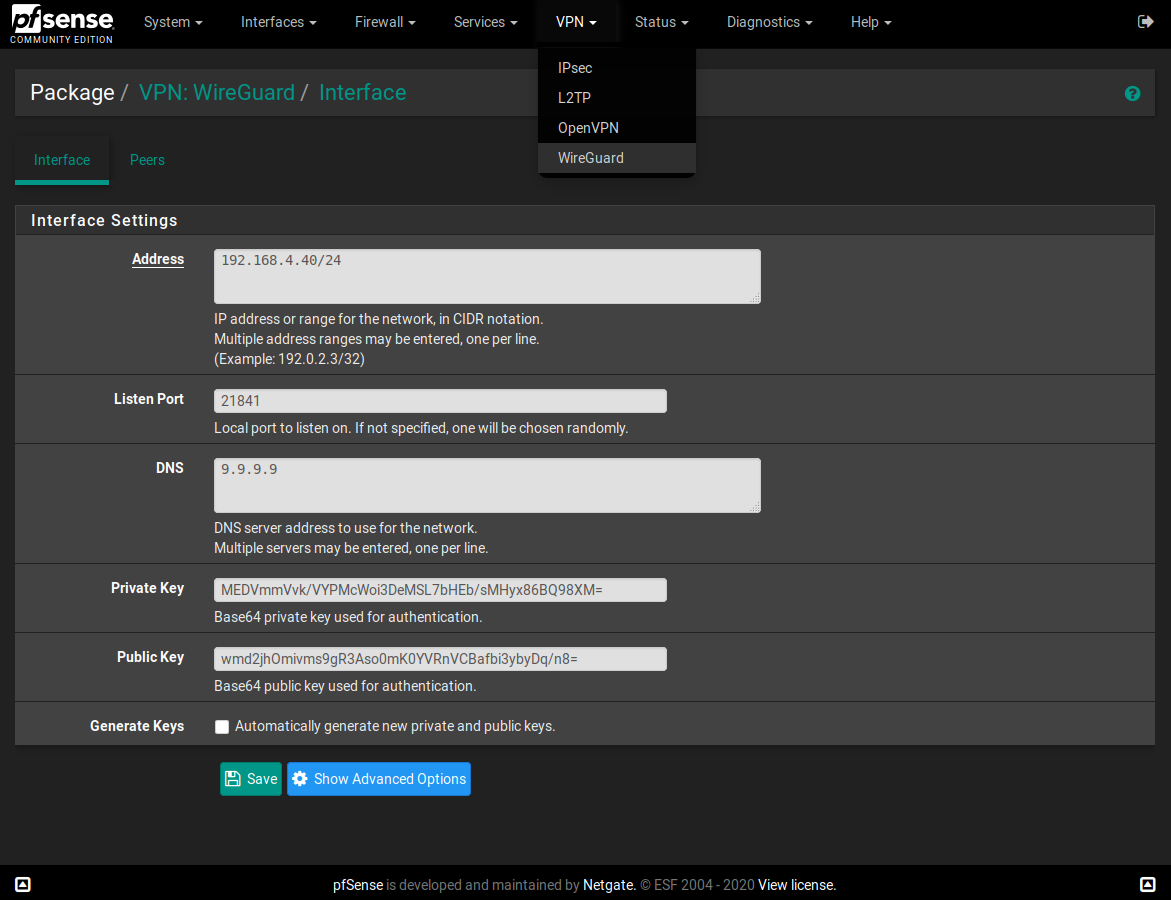
As a follow up, it does show in VPN and I can configure things like the IP range and have it gen private and public keys. It seems the key will be being able to get that interface up and running and I'll be in business. Thanks for any suggestions you can provide.
UPDATE - Once I'd input the items above, I could get the service to start. Once the service was started, i was able to assign the interface. Looks like I am in pretty good shape now. This is great work - I really hope they can get something like this into pfSense ASAP so we'll have support for upgrades and backups and such.
-
@burntoc You have to configure the VPN before you can use it... was that your issue?
If you need to troubleshoot further, running WireGuard from the command line might help. I haven't figured out how to pipe all of WG's output to the log yet, so some errors may not be easy to troubleshoot from the web interface alone.
-
Hi and thanks for your effort.
It would be great if you could make a step-by-step howto on how to set this up as as server, and with peers (road warrior) from a fresh install (and with client configs).
I have installed, restarted services, assigned interface, created outbout NAT etc. in every different order, without any luck.
I cannot make a conenction that routes traffic correctly. I can make a connection to the server, but the traffic does not pass.
Br
-
@Ascrod Thank You! it took several attempts before it installed. Again I'm not a CLI person but received an error about “bash” so after an hour or so I figured bash needed to be installed once installed with
pkg install bashand then was able to execute your commands in putty. I removed the bash withpkg remove bashand it removed the WG, not sure why that happened but I reinstalled bash and re-ran your commands and all is good again.Understood on the advice to use at your own risk, right now I have it on a test box and will continue with the test box before trying on the main system. As far as the client and peer setting I have the keys them from a Raspberry Pi WG install from a few weeks ago so I should just be able to plug those values in. I had the Pi working somewhat. The client would say active but I couldn’t see my Lan from the WG client so hoping to have better luck here with pfsense.
Thanks again for doing this and the detailed explanation. Going to enter the Interface and Peer info tomorrow and see how it goes.
-
Well, fortunately, most of the existing guides out there for WireGuard will still be helpful here. This package doesn't do anything particularly special; it just provides a graphical interface for bringing the interface down or up, and for configuring the VPN. For the most part, WireGuard functionality and troubleshooting on pfSense/FreeBSD should be close to how it works on Ubuntu.
Maybe you'd find the unofficial WireGuard docs useful? They have a number of examples posted that can probably get you started. The configuration interface should match pretty closely with the parameters used in the config file, and the start/restart button simply calls the
wg-quickup and down commands.I have been having some issues with getting DNS requests to route through the VPN. If you set your DNS setting to something other than the VPN server, does traffic route properly?
-
It might be straight forward for people used to wireguard config interface/peers, for me it's not - even though I consider myself pretty advanced in config and troubleshooting.
My last config broke my servers, resulting in some strange routing or whatever, so my internet went down. Everything started working once I stopped the wireguard service.
I don't think its about DNS, as I cannot even ping LAN IP on pfsense server, or the wireguard interface IP of the server.
I know my client works, because I already have a wireguard streisand server on another host behind my firewall (pfsense). Connecting to that server works great!
I have even tried to compare the configs provided by streisand server, output of wg show/wg showconfig interface on both servers - without any luck on setting the parameteres on server and client config.
-
@cappiz I didn’t write down the steps, but here is the rough take on what worked for me earlier today.
- Run the pkg get commands from today’s earlier post. I did have to swap the first and second commands because it told me wireguard-go was a dependency for wireguard. I also had to pkg install bash.
- Rebooted the server. I did this b/c I couldn’t find the wireguard interface in the Assign Interfaces area as I understood from the comments in this thread. The service also wouldn’t start.
- After reboot, Wireguard showed up under my VPN lists, IIRC. I configured a network and had it autogen keys.
- Went into Services and saw Wireguard there, and I started it there.
- Went into Assign Interfaces and it was there, so I enabled the interface.
HTH. YMMV.
-
I did not use apt-get (ubuntu/debian based?) as I used pkg (and yes, I also had to swap the commands, and first install bash).
I have/had the interface (assigned) up and running (needed to create interface and peer first).
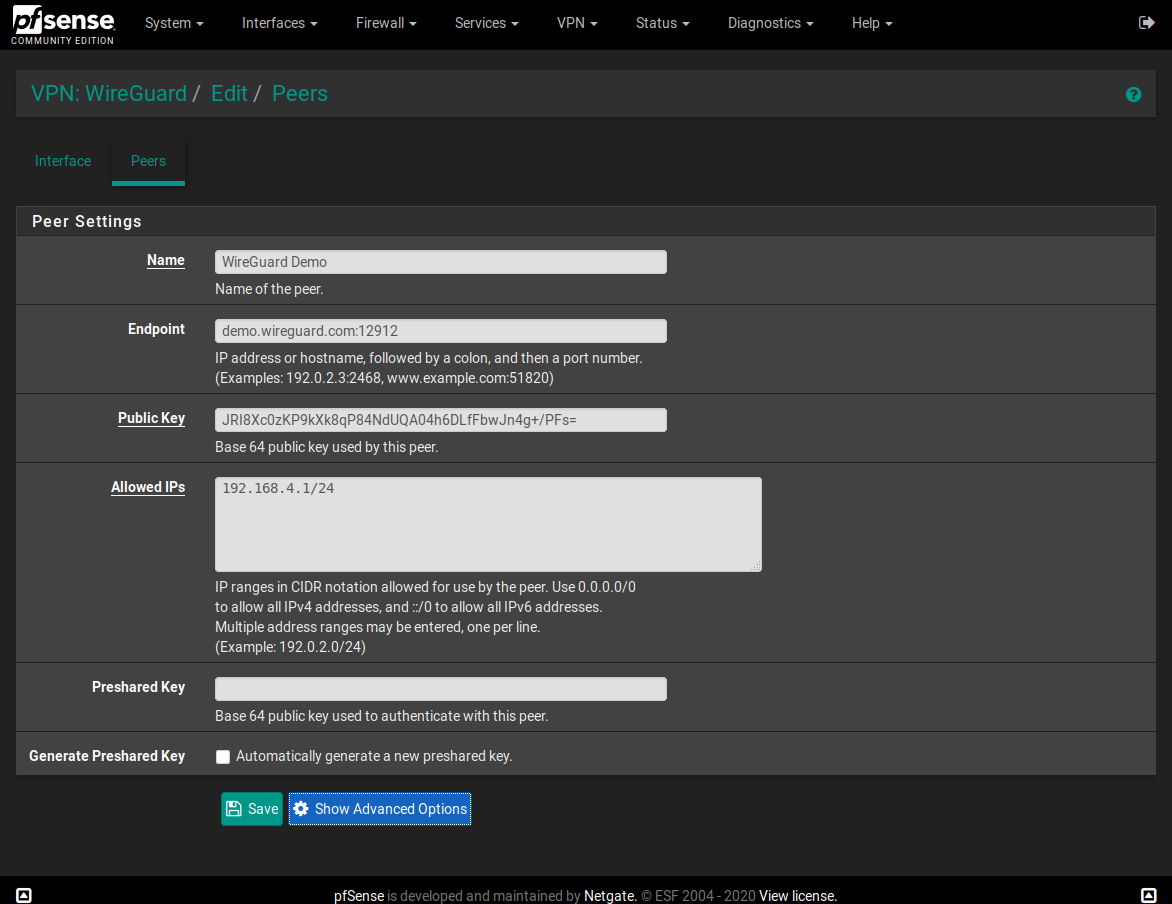
In the peer config - what is preshared key? I can't find any references to it in the documentations.
-
While I do believe at some point this will get added to pfsense.. Until it is "officially" supported, be it added to the official package system - or just natively in the pfsense distro.. I would not suggest anyone play with this unless your ready to break your config, or be concerned with its security.
When either someone takes the time to vet this through the pfsense developers to the point they add it to the package system. Or the official pfsense developers incorporate into the code - its not something anyone should be messing with that are not fully aware of all the possible consequences
If you want to deploy this now, before its officially supported - I suggest you run this on some other box in your network and do it that way before you go dicking with anything to do with the pfsense install.
If someone wants to help the community in deploying this - they should be putting together guides on how to run this on a different box in there network, vs suggesting anyone mess with base pfsense deployment.
-
This post is deleted! -
@cappiz My apologies - misspoke there. You’re right, it was pkg get - corrected.
-
So here's another question for the crew. I realized that I'm actually going to run Wireguard on another device in my IOT zone and the msg from @johnpoz reminded me that if I don't have to have it here I probably shouldn't install it this way.
How do you remove it? I used pkg delete to remove wireguard, wireguard-go, and bash, and I rolled back my config as well and rebooted, and I'm STILL seeing Wireguard as a service and in the VPN menu and defined interfaces.