pfSense DNS resolver (Unbound) - aggressive-nsec option
-
Hello!
Maybe...
server:aggressive-nsec: yes
John
-
I tried that, and DNS resolver will not resolve.
EDIT: My syntax was wrong, didnt realize I had to add "server:" for each individual option. Also, since I have pfBlocker running, gotta give Unbound some time to load everything up. Thanks!
-
You do not need more than one server: statement
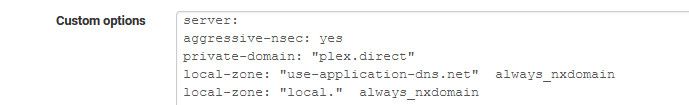
-
@johnpoz by the way this will not broke insecure subdomains resolving?
Offtopic: pfSense need update documentation about Python module in Unbound.
I create script with Filer and sh script to reload Unbound on change of this python script to:- override ::1 and 127.0.0.1 for list of domains, e.g: dev, localdomain, etc for local development
- remove aaaa for list of domains.
This can be as example in docs?
-
Do you have a example we could test against?
-
@johnpoz I can check aggressive-nsec out of working hours and reply here.
In short: my domain has enabled DNSSEC but due IPv4 I had to have private SplitDNS resolving which of course not signed by DNSSEC. So I have exclusions for subdomains in my domain that allows insecure resolving internally, like:
I had to have private SplitDNS resolving which of course not signed by DNSSEC. So I have exclusions for subdomains in my domain that allows insecure resolving internally, like:server: # Allow private resolving for Internal domains: private-domain: "sub1.example.com" private-domain: "sub2.example.com" # Allow insecure resolving for Internal domains: domain-insecure: "sub1.example.com" domain-insecure: "sub2.example.com" # Forwarding sub1.example.com forward-zone: name: "sub1.example.com." forward-ssl-upstream: no forward-addr: 2001:470:abc::1@53 forward-addr: 2001:470:abc::2@53 forward-first: yes forward-no-cache: no # Forwarding sub2.example.com forward-zone: name: "sub2.example.com." forward-ssl-upstream: no forward-addr: 2001:470:abc::1@53 forward-addr: 2001:470:abc::2@53 forward-first: yes forward-no-cache: noI curious how this aggressive option will work in this case =)
-
This post is deleted! -
@johnpoz from my test looks like it working. Maybe add Redmine task to add check-box option in advanced setting for it?
-
You can always add a feature request sure.
-
@johnpoz https://redmine.pfsense.org/issues/10449 someone was more faster then I =D