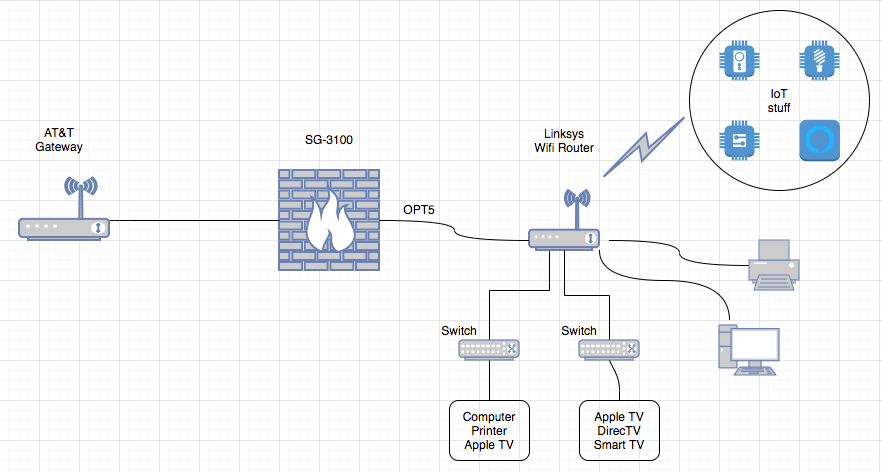
Incorporating 3100 into network
-
@ajtradtech NAT should already be disabled in bridge mode. You said you already had VLANs setup on the 3100, but neither the E4200 or the dumb switches support VLANs. With that diagram you could only have every device on the same VLAN which defeats the purpose.
-
@ipeetables said in Incorporating 3100 into network:
@ajtradtech NAT should already be disabled in bridge mode.
Got it.You said you already had VLANs setup on the 3100, but neither the E4200 or the dumb switches support VLANs. With that diagram you could only have every device on the same VLAN which defeats the purpose.
Baby steps :) I was afraid that would be the case. In the meantime, I guess I could move the other segments of the network to the 3100 so at least the wireless and IoT devices would be isolated on the E4200.If I ran the 3100 to a VLAN capable switch and connected the E4200 to that, would that work?
Thanks.
-
@ajtradtech Yes it would.
-
Ok. I'll soon have a VLAN capable switch in my hands.
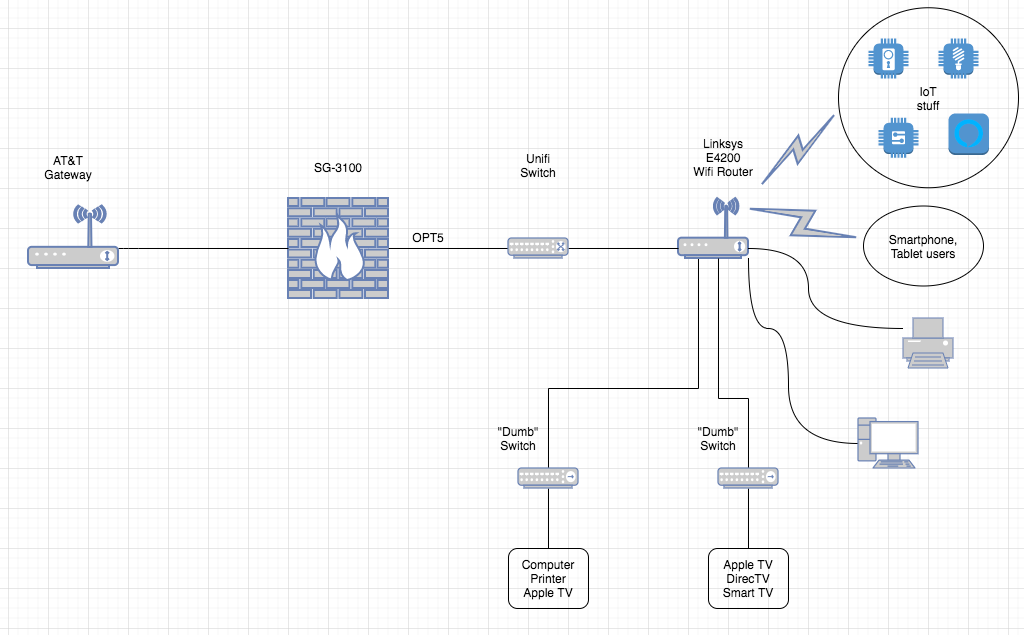
Based on the revised diagram below, I take it the connection between the unifi switch and the Linksys would be the trunk line? I'm hoping I can fence off the IoT devices and smartphone/tablet users into their own sandboxes. I could also move the dumb switch segments and the PC to the unifi switch. Sounds like a plan?
Thanks.
-
@ajtradtech said in Incorporating 3100 into network:
Ok. I'll soon have a VLAN capable switch in my hands
Avoid TP-Link. Some models don't handle VLANs properly.
-
The link between the 3100 and unifi switch would be a trunk/tagged link because it would be carrying traffic for multiple VLANs. The unifi switch port that connects to the linksys router would be an access port/untagged. This means everything that is connected to the linksys router, whether wired or wireless, would be on the same VLAN. Unfortunately you can't split those up because it doesn't understand vlans.
You are correct that moving the dumb switches directly to the unifi switch would allow you to assign them to any vlan.
-
@ipeetables said in Incorporating 3100 into network:
The link between the 3100 and unifi switch would be a trunk/tagged link because it would be carrying traffic for multiple VLANs. The unifi switch port that connects to the linksys router would be an access port/untagged. This means everything that is connected to the linksys router, whether wired or wireless, would be on the same VLAN. Unfortunately you can't split those up because it doesn't understand vlans.
Alright, any thought of separating the IoT devices from the other wifi clients using the linksys is a dead end. Got it. Guess if I want to accomplish that, I'll have to use an AP that also supports VLANs.
-
@JKnott said in Incorporating 3100 into network:
@ajtradtech said in Incorporating 3100 into network:
Ok. I'll soon have a VLAN capable switch in my hands
Avoid TP-Link. Some models don't handle VLANs properly.
Thanks. It's a UniFi switch that I purchased.
-
It's done and wow, that went smoother then I expected.
I first connected the UniFi switch to OPT5 on the SG. Adopted it, changed the IP so that it was on the same subnet. Everything connected to the Linksys was then moved to the UniFi switch.
Next, I reconfigured the gateway for IP Passthrough. Disabled the wifi. Entered the MAC address of OPT5- it's different from the one listed on the bottom of the SG.
The Linksys was reconfigured next. DHCP disabled along with SPI. Set to bridge mode.
Power cycled the gateway.
Power cycled the SG.
Power cycled the Linksys.
When all of the lights indicated systems ready, I logged into pfSense and bam! There's the public IP on the WAN interface!The only gotcha I encountered was when I attempted to access the settings on the Linksys. I can't use the static IP that I assigned it. I had to use the IP that SG assigned to it and that was easy to find in the UniFi controller.
Thanks for your assistance, all.
-
Nice, enjoy!