I made a WireGuard package for pfSense
-
@cappiz I didn’t write down the steps, but here is the rough take on what worked for me earlier today.
- Run the pkg get commands from today’s earlier post. I did have to swap the first and second commands because it told me wireguard-go was a dependency for wireguard. I also had to pkg install bash.
- Rebooted the server. I did this b/c I couldn’t find the wireguard interface in the Assign Interfaces area as I understood from the comments in this thread. The service also wouldn’t start.
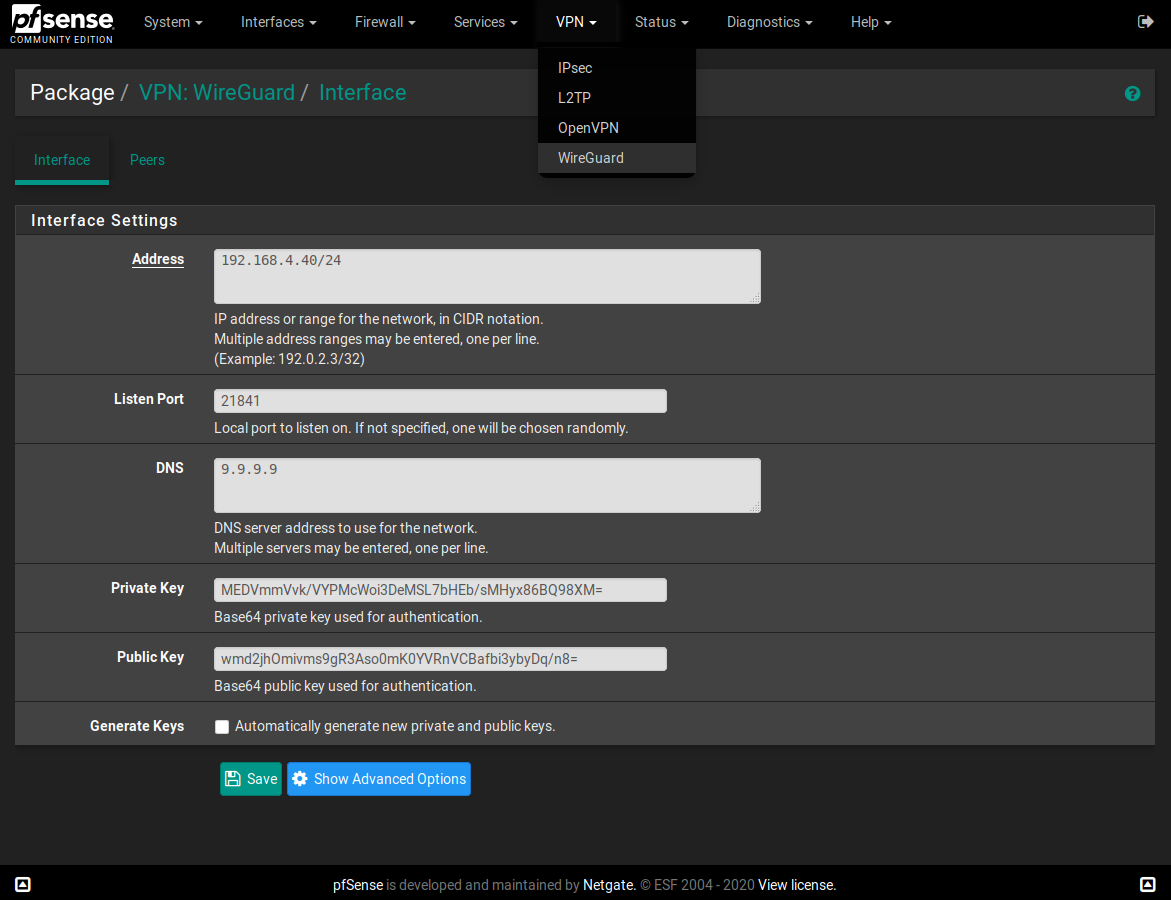
- After reboot, Wireguard showed up under my VPN lists, IIRC. I configured a network and had it autogen keys.
- Went into Services and saw Wireguard there, and I started it there.
- Went into Assign Interfaces and it was there, so I enabled the interface.
HTH. YMMV.
-
I did not use apt-get (ubuntu/debian based?) as I used pkg (and yes, I also had to swap the commands, and first install bash).
I have/had the interface (assigned) up and running (needed to create interface and peer first).
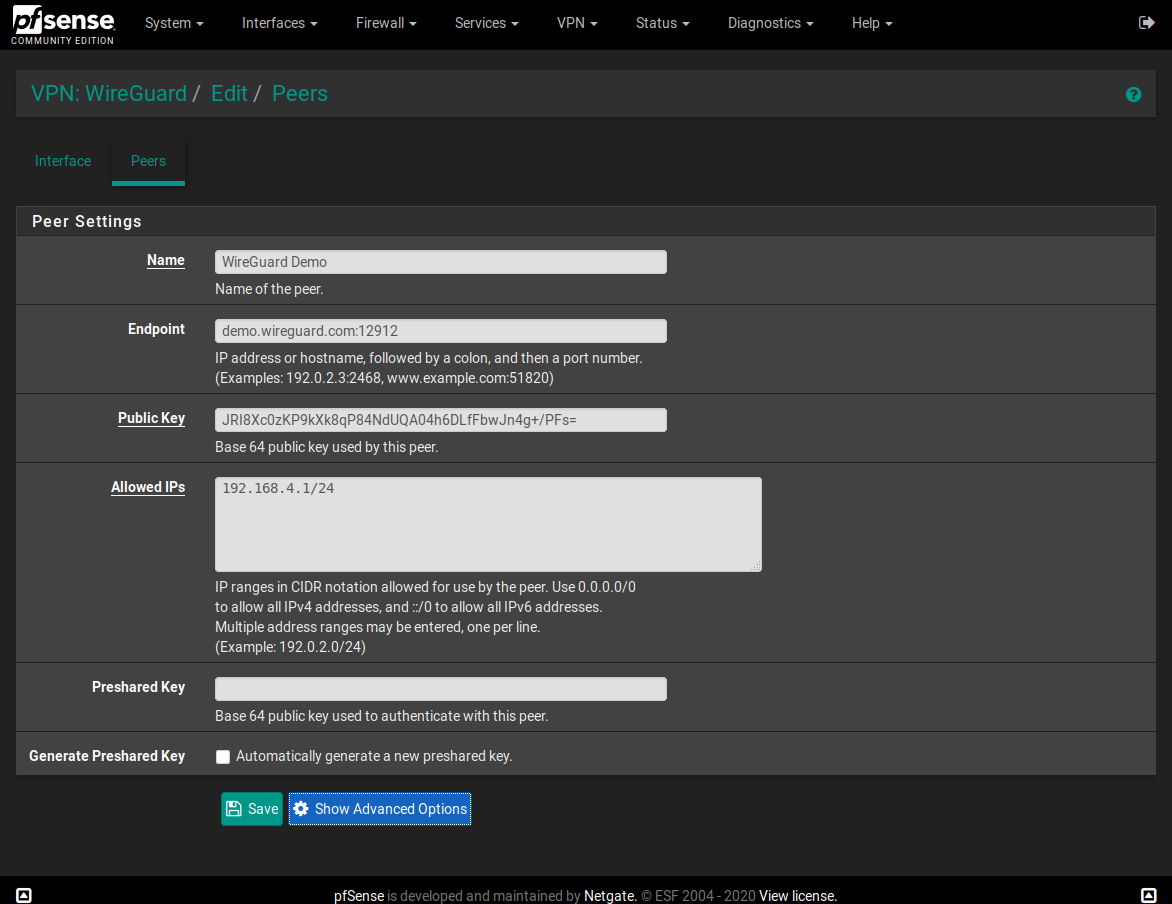
In the peer config - what is preshared key? I can't find any references to it in the documentations.
-
While I do believe at some point this will get added to pfsense.. Until it is "officially" supported, be it added to the official package system - or just natively in the pfsense distro.. I would not suggest anyone play with this unless your ready to break your config, or be concerned with its security.
When either someone takes the time to vet this through the pfsense developers to the point they add it to the package system. Or the official pfsense developers incorporate into the code - its not something anyone should be messing with that are not fully aware of all the possible consequences
If you want to deploy this now, before its officially supported - I suggest you run this on some other box in your network and do it that way before you go dicking with anything to do with the pfsense install.
If someone wants to help the community in deploying this - they should be putting together guides on how to run this on a different box in there network, vs suggesting anyone mess with base pfsense deployment.
-
This post is deleted! -
@cappiz My apologies - misspoke there. You’re right, it was pkg get - corrected.
-
So here's another question for the crew. I realized that I'm actually going to run Wireguard on another device in my IOT zone and the msg from @johnpoz reminded me that if I don't have to have it here I probably shouldn't install it this way.
How do you remove it? I used pkg delete to remove wireguard, wireguard-go, and bash, and I rolled back my config as well and rebooted, and I'm STILL seeing Wireguard as a service and in the VPN menu and defined interfaces.
-
@cappiz As I said in my first post, using WireGuard here is very much at your own risk; if you're having this much difficulty, please consider @johnpoz 's advice in setting WG up on a separate device instead. Also, please do NOT post any private keys publicly, they are private for a reason! I suggest changing your private and public key immediately.
@burntoc It sounds like you also need to remove
pfSense-pkg-wireguard. I'm not sure why pkg wouldn't have caught it when you removed wireguard and wireguard-go, but that might be your issue. -
@Ascrod Thank you for the message. As best I can tell, there may be some package reinstallation tasks that try to put things back in order. I saved the config I'd restored to and removed the wireguard entries then reloaded it and everything looks good so far. If it acts up, I guess it will be my excuse to kick the tires on 2.5, LOL.
-
It is working! Thanks for package. How can I see wireguard logs?
-
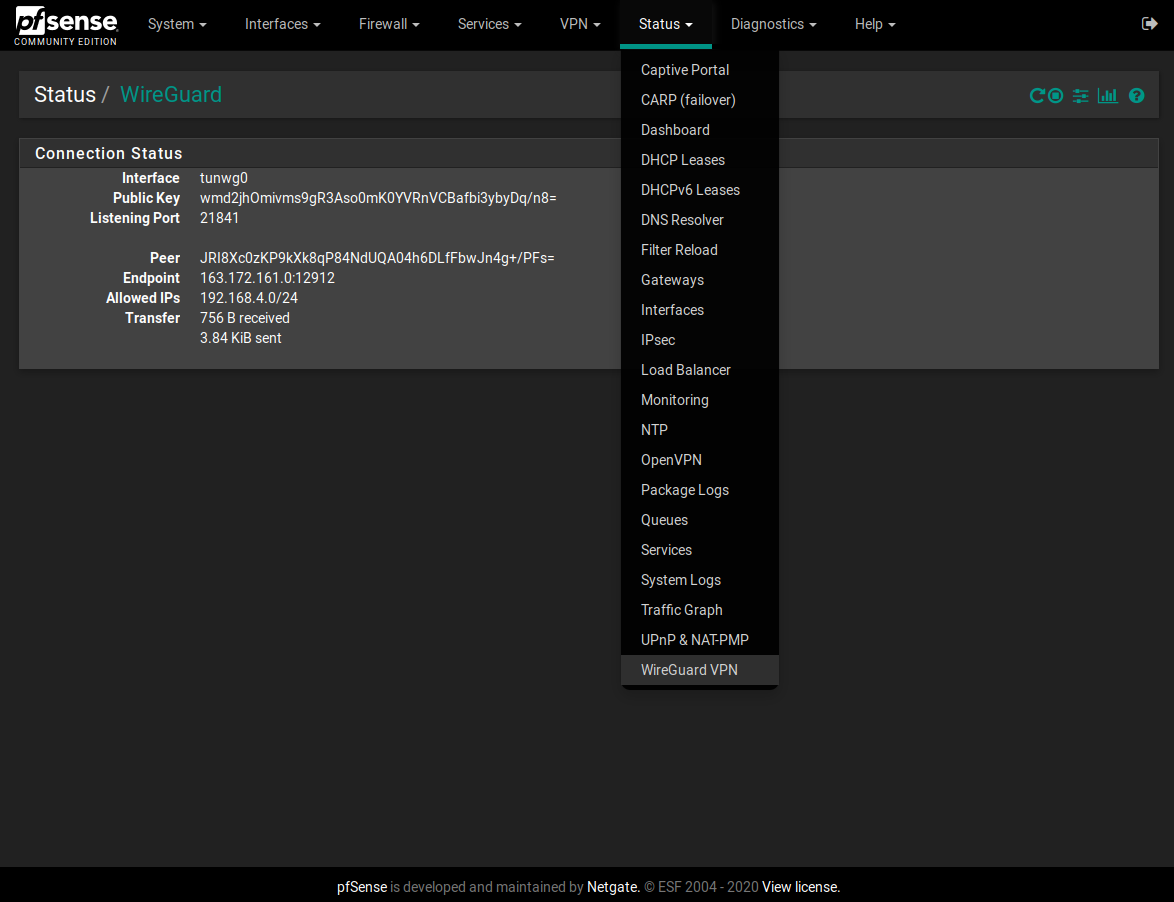
@baran WireGuard doesn't provide much in the way of log files. You can check the status of the interface and peers on the status page, though (Status > WireGuard VPN)
-
Hi All,
Would like some input. Im testing this on a pfsense install running in a vm. I seem to have all the port forwarding from my real/physical pfsense box to my vm-pfsense machine running the wireguard server.
Im testing a connection from my android phone over cellular data connection. It seems to be able to connect to the wireguard vpn server. When i run the command "wg" it shows my cellphone's public IP as an endpoint. If i run a tcpdump on the vpn port i see a lot of UDP acitivy between the vpn server and my cell phone public IP.
However i cannot ping any internal IPs or internet ip e.g 8.8.8.8. Its like no traffic is passing through the tunnel.
On the client side i do have allowed IPs set 0.0.0.0
From the vpn server i can ping the phone on the vpn ip address, but i cannot ping the vpn servers interface Ip from the phone! -
This post is deleted! -
How can I add a new interface and configure it seperately from this package?
-
@baran WireGuard only supports one interface per configuration file. You will need to create and use a new config file entirely from the command line. Unfortunately you won't be able to use it with this package at this time.
-
Any input would be appreciated. I have the same issue as @cappiz where, when my wireguard service is running, my pfsense loses all internet connectivity on the WAN interface. Is there a need of some additional rules to be added or something?
-
@alirz I haven't been able to reproduce this, so I'm not sure what exactly would be causing it. A cursory Google search shows that others have had this problem, and doesn't appear to be specific to a particular OS. What happens if you restart the WG service? Are you only seeing traffic in one direction to/from the WAN port? Do you see anything unusual in your system logs?
-
@Ascrod if i restart the wireguard interface, i lose internet again at home. its like there is some conflict of routing between WAN/LAN/TUNWG0 or something.
Do i need to some ip forwarding/NAT rules between WAN/TUNWG0/LOCALHOST etc ?I have wireguard server successfully running on an ubuntu machine on my LAN.However i would prefer to run that on my pfsense box also. on ubuntu I had to enable ip4 forwarding and add some NAT iptable rules etc to get the traffic flowing as per all the intrucions out there in almost all tutorials.... Does the same need to be done on pfsense? I cant find any info on this. Thank you.
-
@alirz I didn't have to set up anything special on my actual setup or my test VM, other than port forwarding inbound traffic to the VPN interface and actually enabling the interface, so I would ensure that you have done both of those. You shouldn't have to set up any other special forwarding on pfSense like you would on Ubuntu, because pfSense is designed to be a router (this post goes into some detail about that). Also, iptables rules definitely won't work on pfSense because it uses pf rather than iptables.
I'm not entirely sure what's going on here, but I would double-check your WG config against some working examples (again, ignoring the PostUp/PostDown commands that most people use for routing in Ubuntu) as well as your logs. Make sure your interface address is a range if necessary (I use /24 on mine) and that your client is routing properly. (One time I ran into an issue where I had set the allowed IPs on one of my "client" peers to 0.0.0.0 rather than 0.0.0.0 /0. That caused a few hours of headache.)
-
@Ascrod ok so I didn't add any inbound route to the VPN interface(tunwg0) yet.
So am I to a FW RULE for udp traffic from any port, Where source is ANY or WAN? and destination is the particular VPN interface? -
@Ascrod It looks like I'm almost there. But missing some routing.
Here is my setup.Pfsense WG config: I've hidden real keys. But still showing which keys are used where
[Interface] # Generated by pfSense Address = 10.100.100.1/24 ListenPort = 51830 DNS = 10.0.0.1 <----- Pfsense local LAN IP PrivateKey = xxxxxxxxxxxxxxxx [Peer] # phone PublicKey = cccccccccccccccccc AllowedIPs = 10.100.100.2/32 [Peer] # IPAD PublicKey = vvvvvvvvvvvvvvvvv AllowedIPs = 10.100.100.3/32Client config of Android Phone
[Interface] Address = 10.100.100.2/32 DNS = 10.100.100.1 PrivateKey = dddddddddddddd [Peer] AllowedIPs = 0.0.0.0/0 Endpoint = my_ddns.com:51830 PersistentKeepalive = 21 PublicKey = ccccccccccccccccccNow im not sure which and where i need to add the rule for the vpn interface. Is it under NAT and port forward from WAN to OPT4 Address? OR is it under NAT> Outbound?
Note my above config works fine if i move that to my ubuntu wireguard server and simply forward UDP port 51830 from pfsense to my ubuntu machine IP.. NOTE: For testing purpose im using the same private and public keys on my ubuntu wireguard server and this one im trying to setup on the PF box. I believe that should not be an issue? Thanks for your helpI tried the following rule but i dont think thats correct
If i tcpdump on my pfsense internet side(WAN) interface, i see constant incoming connection attempts from phone and then the pfsense reponding back to the phone from the WAN interface.
But if I trace on the TUNWG0 interface i only 1 request from 10.100.100.2(Phones vpn ip) to the pf sense WAN inteface.
This is the furthest ive been able to get now. From the pfsense and from my LAN devices, i can ping the phone's vpn ip(10.100.100.2) but thats it. I cannot ping LAN IPs, lan DNS, 8.8.8.8 etc from the phone.