Wifi AP to LAN communication
-
Hi all,
Starting to get the hang of things however come up against an issue I'm not sure about. My setup is now as follows.
Em0=WAN (Pppoe connection to DM200 Modem to ISP)
Em1=LAN > 8port switch with computers and smart hubs
Em2=Wi-Fi AP(NETGEAR X6 R8000 in AP mode)An issue I have discovered this morning is my firetv on WiFi connects to the AP and Internet works, YouTube etc however I cannot connect to my Plex server on the server on the LAN.
I figured I'd check before fiddling as was up till 0130 getting it working.Many thanks


-
ok so here are the results of my efforts last night until 0130!
I am currently unable to get my plex to work.
the plex server is on the server 192.168.1.251 and I am trying to access it via the tv firestick. can anyone help?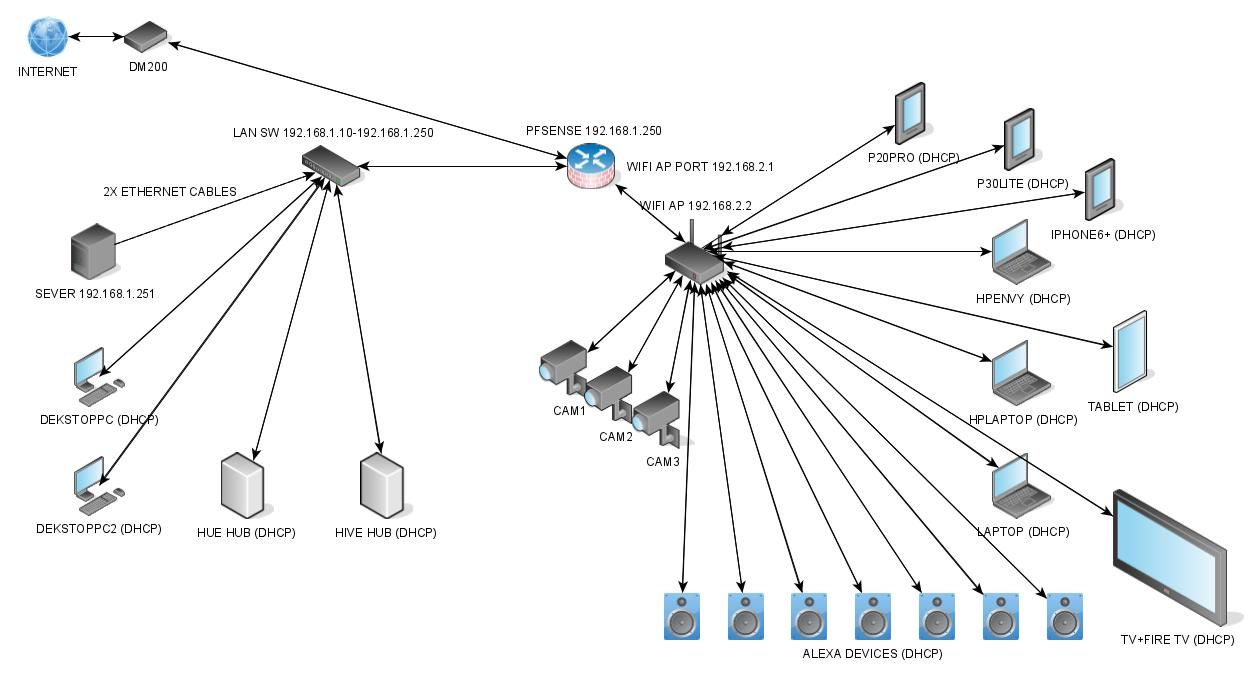
-
This is not a wifi problem. Moved to general.
Can anything on the 192.168.2.X subnet connect to anything on the 192.168.1.X subnet?
How is the firestick trying to access the plex server? By IP address? By hostname? By discovering it?
Steve
-
@stephenw10 morning Steve, I believe I may have solved it. I can use my mobile to connect to pfsense 192.168.1.250 and configure things. I have added a port forward to allow plex and it now will connect to the server.
Honestly I am trying to fiddle as little as possible as I have now 'gone live' with the pfsense and it is now part of my network.
My biggest concern is ensuring I have not cobbled it together, got it working but at the same time left myself open to attack. I also need to get remote desktop connection for my server to work so I can manage it on the fly.
I guess I am not 100% confident in my setup.
If you or anyone can help go through it I'd really appreciate it. -
I would not expect a port forward to be required there as Plex can usually be accessed from anywhere, even externally.
UPnP is disabled by default in pfSense and you should leave it that way unless you have a very good reason not to. Plex can open port forwards in the firewall to allow access otherwise.
Usually when people device their network like you have it is for security. Consider what would happen if one of your cameras was found to have a vulnerability and was hacked for example. What would that give anyone access to?
You probably want firewall rules on the 192.168.2.1 interface in pfSense that allow only the required access outbound. So the cameras may not need any external access or maybe only to a known IP or set of IPs. Wifi IoT style devices may not need any access to to the LAN subnet. Though maybe you want Alexa to be able to control Hive....
What you want to do is allow only the traffic that is needed and segregate devices as much as possible to mitigate any security issues should they occur.
Does your access point allow for multiple SSIDs / VLANs?
If so I would create more so you can separate general access devices like laptops and tablets from IoT devices like cameras and Alexa.Currently you have separated devices simply by wired or wifi and that might not be the best way. The Hive and Hue hubs are IoT devices. I would want those on a separate subnet to desktop PCs and servers if possible.
Steve