PC Engines apu2 experiences
-
@Qinn Thanks for the tips. I don't think I'll reinstall pfSense to a single disk ZFS. My NAS haves it, but it haves 12x 4TB disks.
Regarding watchdog, it's enabled and working, but somehow it isn't showing on the dashboard nor in status --> services.
-
@kevindd992002 I'm afraid I didn't explain myself clearly.
Sorry for that.One customer needed to access to their provider servers.
The access is granted via Site2Site IPsec VPN with very low crypto requirements and also quite unusual IPs (they use "fake" public IPs inside the tunnel).
We had some trouble getting Phase2 working for that customer and provider so we planned some lab tests.
There's no need for provider at all in general but just for this case, our customer, in particular.When doing local tests we did realize the speed change on IPSec tunnels compared to OpenVPN so we did some other test for our own purposes.
Again.There's no need for external or any provider. It was just only on our specific customer needs.
-
@cysiacom said in PC Engines apu2 experiences:
@kevindd992002 I'm afraid I didn't explain myself clearly.
Sorry for that.One customer needed to access to their provider servers.
The access is granted via Site2Site IPsec VPN with very low crypto requirements and also quite unusual IPs (they use "fake" public IPs inside the tunnel).
We had some trouble getting Phase2 working for that customer and provider so we planned some lab tests.
There's no need for provider at all in general but just for this case, our customer, in particular.When doing local tests we did realize the speed change on IPSec tunnels compared to OpenVPN so we did some other test for our own purposes.
Again.There's no need for external or any provider. It was just only on our specific customer needs.
No worries, I see what you mean now. Would you happen to have any best practice guide in setting up an IPSec tunnel in pfsense, at least for a home setup with "relaxed but secure" crypto requirements?
As for Remote Access VPN, is OpenVPN still the way to go? There's nothing stopping me of creating an IPSec s2s link and an OpenVPN remote access VPN gateway, right?
-
@stefanl said in PC Engines apu2 experiences:
@Qinn Thanks for the tips. I don't think I'll reinstall pfSense to a single disk ZFS. My NAS haves it, but it haves 12x 4TB disks.
Regarding watchdog, it's enabled and working, but somehow it isn't showing on the dashboard nor in status --> services.
I thought and have the same, this service isn't present in the services status, but if you stop 1 service, you will see it will come up again (if you have an mail address setup for notices, you should also receive a mail. Maybe read https://forum.netgate.com/topic/59761/new-package-service-watchdog/9
-
Bios Update from 4.11.0.4 to 4.11.0.6 on APU2C0, until now without any issues :-)
Regards,
fireodo -
Yes the PCIe power management feature is now disabled by default (ie maximum performance) and ACPI change reverted (ie
sysctl dev.cpuworks).Detailed APU* Coreboot v4.11.0.6 release notes:
- Rebased with official coreboot repository commit d6f7ec5.
- Updated sortbootorder to v4.6.18 bringing the PCI Express power management features runtime option. For details refer to sortbootorder documentation. When PCI Express power management features features are enabled, the network controllers (NICs and WIFi cards) may have reduced performance at the cost of reduced power consumption. By default this option will be disabled to not impact the network performance.
- Reverted changes to ACPI CPU definitions causing BSD systems to not probe CPU frequency driver. The ACPI compliance of current BSD systems is not up to date, the situation should improve when the distribution will start to use FreeBSD 12.x, which works well with most recent rules of defining processors in ACPI.
- Reverted changes with PCIe reset logic causing mPCIe2 slot connected modules to not appear in OS. The change did more harm than good. We are working to improve the PCIe modules detection in firmware, which is dependent on the AGESA.
- Added IOMMU IVRS generation expanded with IVHD type 11h for newer Xen. This change should allow newer Xen images to utilize more IOMMU features.
- Fixed memtest hang on apu1.
- Fixed TPM2 detection on FreeBSD 12.1. Since FreeBSD 12.1 the TPM2 support is available along with FreeBSD ports offering TPM2 tools. We will provide documentation how to install and utilize those tools on FreeBSD systems soon.
- Fixed a problem where SD 3.0 mode could not be disabled.
Applied to apu2c4 test system. All good so far.
-
@dugeem said in PC Engines apu2 experiences:
Yes the PCIe power management feature is now disabled by default (ie maximum performance) and ACPI change reverted (ie
sysctl dev.cpuworks).Detailed APU* Coreboot v4.11.0.6 release notes:
- Rebased with official coreboot repository commit d6f7ec5.
- Updated sortbootorder to v4.6.18 bringing the PCI Express power management features runtime option. For details refer to sortbootorder documentation. When PCI Express power management features features are enabled, the network controllers (NICs and WIFi cards) may have reduced performance at the cost of reduced power consumption. By default this option will be disabled to not impact the network performance.
- Reverted changes to ACPI CPU definitions causing BSD systems to not probe CPU frequency driver. The ACPI compliance of current BSD systems is not up to date, the situation should improve when the distribution will start to use FreeBSD 12.x, which works well with most recent rules of defining processors in ACPI.
- Reverted changes with PCIe reset logic causing mPCIe2 slot connected modules to not appear in OS. The change did more harm than good. We are working to improve the PCIe modules detection in firmware, which is dependent on the AGESA.
- Added IOMMU IVRS generation expanded with IVHD type 11h for newer Xen. This change should allow newer Xen images to utilize more IOMMU features.
- Fixed memtest hang on apu1.
- Fixed TPM2 detection on FreeBSD 12.1. Since FreeBSD 12.1 the TPM2 support is available along with FreeBSD ports offering TPM2 tools. We will provide documentation how to install and utilize those tools on FreeBSD systems soon.
- Fixed a problem where SD 3.0 mode could not be disabled.
Applied to apu2c4 test system. All good so far.
Do you happen to know the what the recommendations are for the APU2C4 v4.11.0.6 BIOS settings to achieve max performance?
-
@kevindd992002 said in PC Engines apu2 experiences:
Do you happen to know the what the recommendations are for the APU2C4 v4.11.0.6 BIOS settings to achieve max performance?
Defaults are fine. Only two that matter are:
- Core Performance Boost (CPB) enabled (default)
- PCIe Power Management disabled (now default)
Cheers
-
@dugeem good to know. Im planning to update too.
-
@dugeem said in PC Engines apu2 experiences:
@kevindd992002 said in PC Engines apu2 experiences:
Do you happen to know the what the recommendations are for the APU2C4 v4.11.0.6 BIOS settings to achieve max performance?
Defaults are fine. Only two that matter are:
- Core Performance Boost (CPB) enabled (default)
- PCIe Power Management disabled (now default)
Cheers
Got it. I know CPB enabled is the default but was disabled in the older BIOS'es where it was initially introduced. Just for the heck of it, is there a way to know if CPB is enabled aside from checking it during runtime? I currently don't have physical access to the pfsense boxes.
-
-
@Qinn said in PC Engines apu2 experiences:
/boot/loader.conf.local
@cysiacom and others
Not sure why but my OpenVPN remote access server only 55-60Mbps speed when I'm trying to saturate the link. I'm not sure if my test is right but I connect my local laptop (same network as the OpenVPN remote access server) to the OpenVPN server and download a game in steam. My Internet connection is 300Mbps symmetrical speed, so I'm expecting much higher speed. As soon as I disconnect the VPN connection of the laptop, the download speed soars up to saturate the 300Mbps link.
Here are my OpenVPN settings:
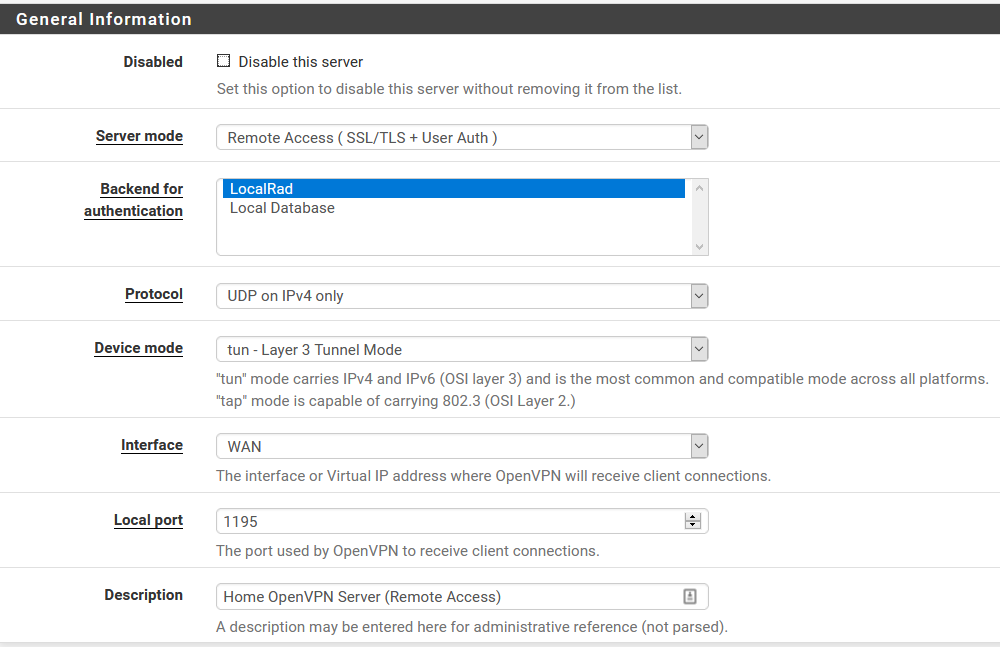
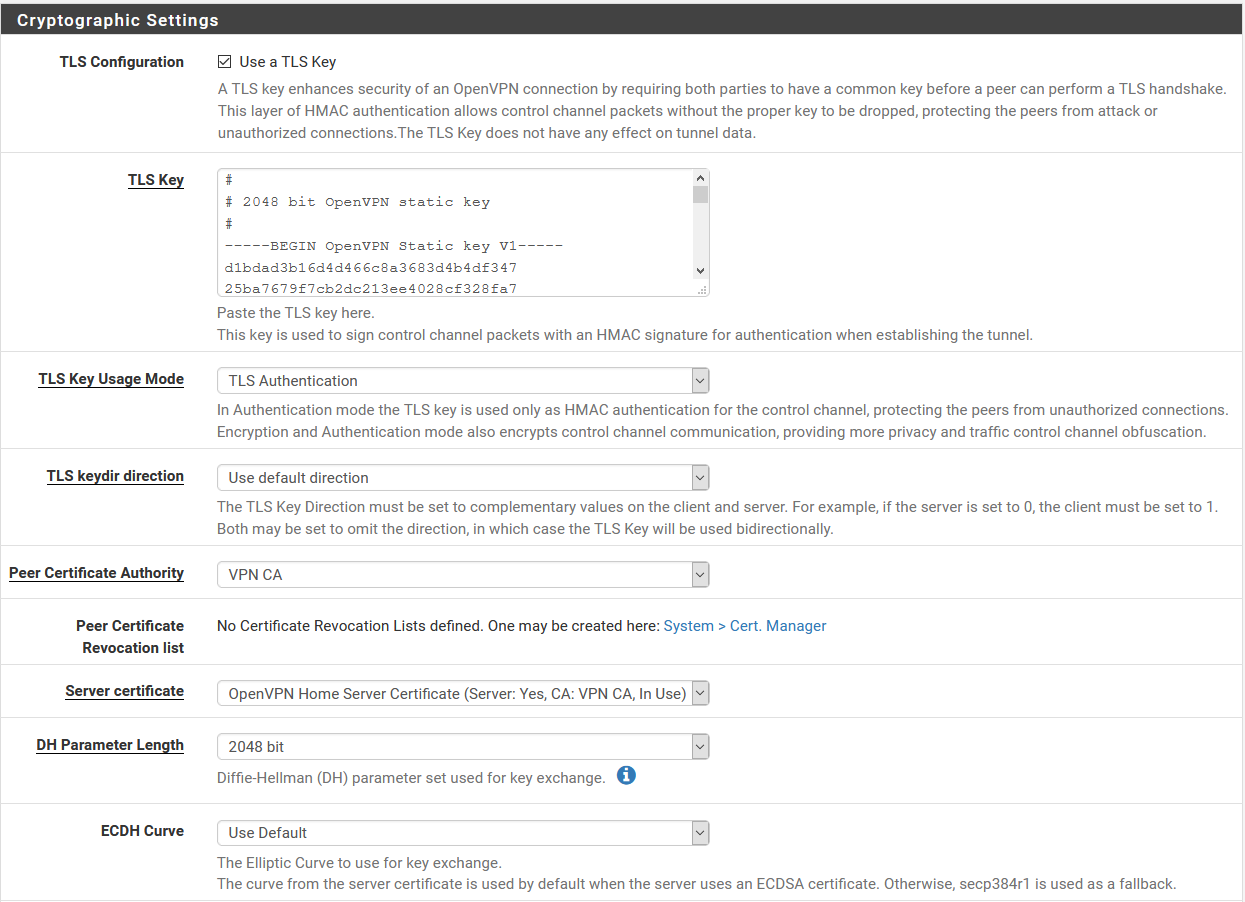
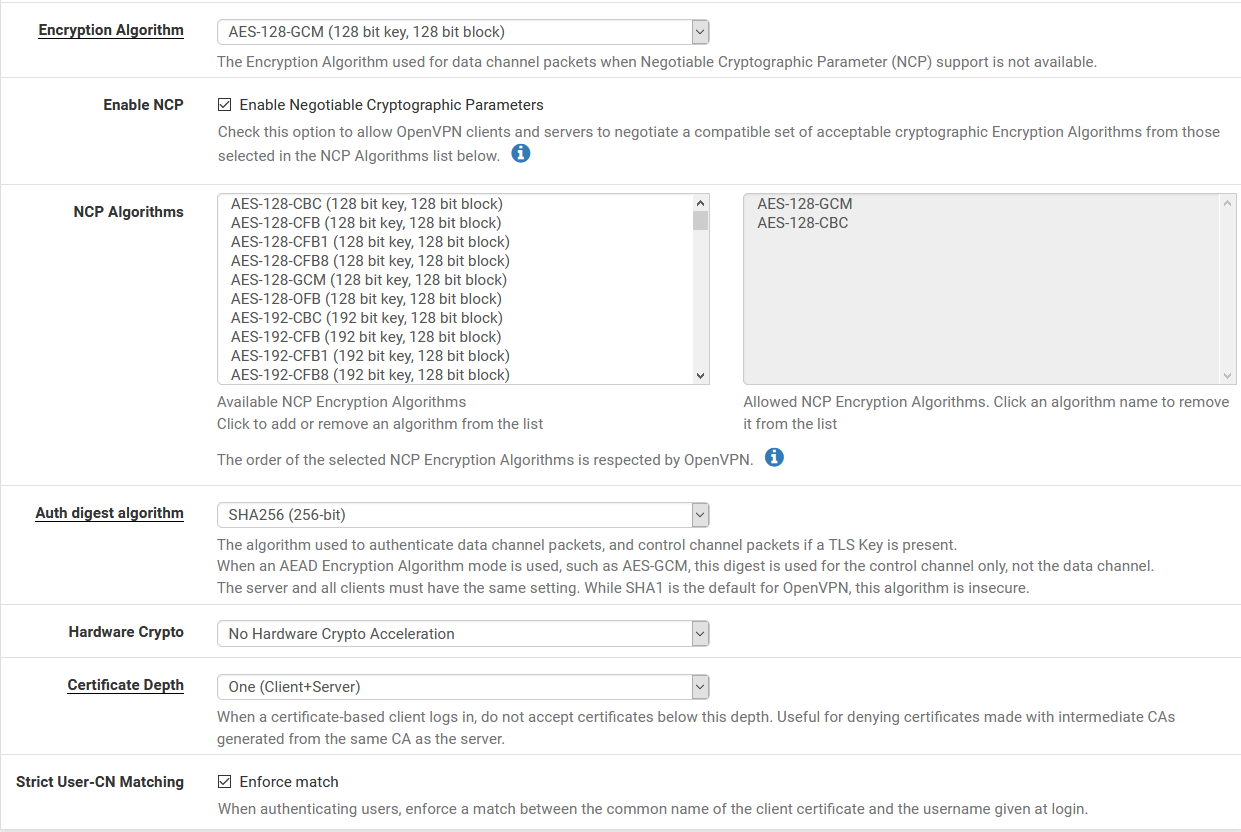
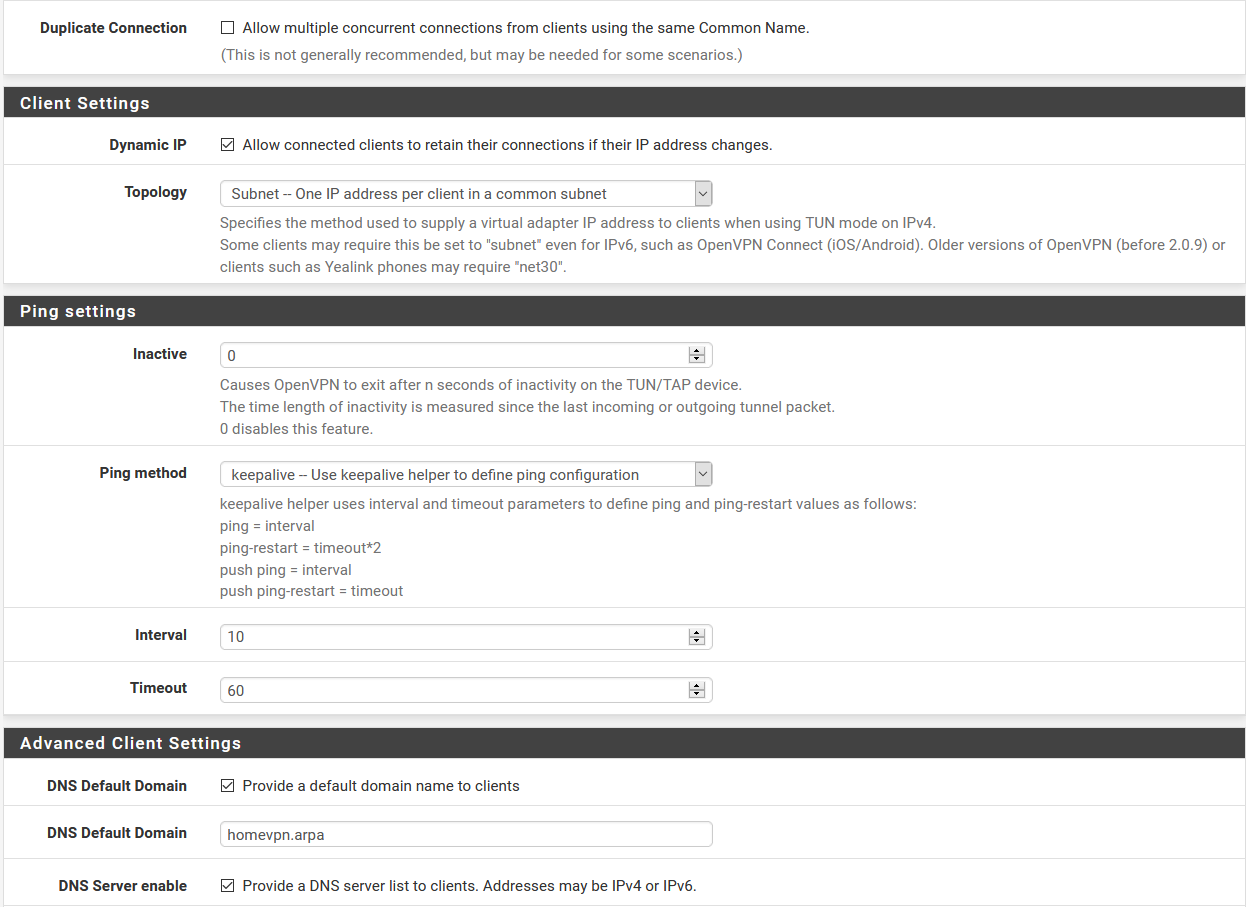
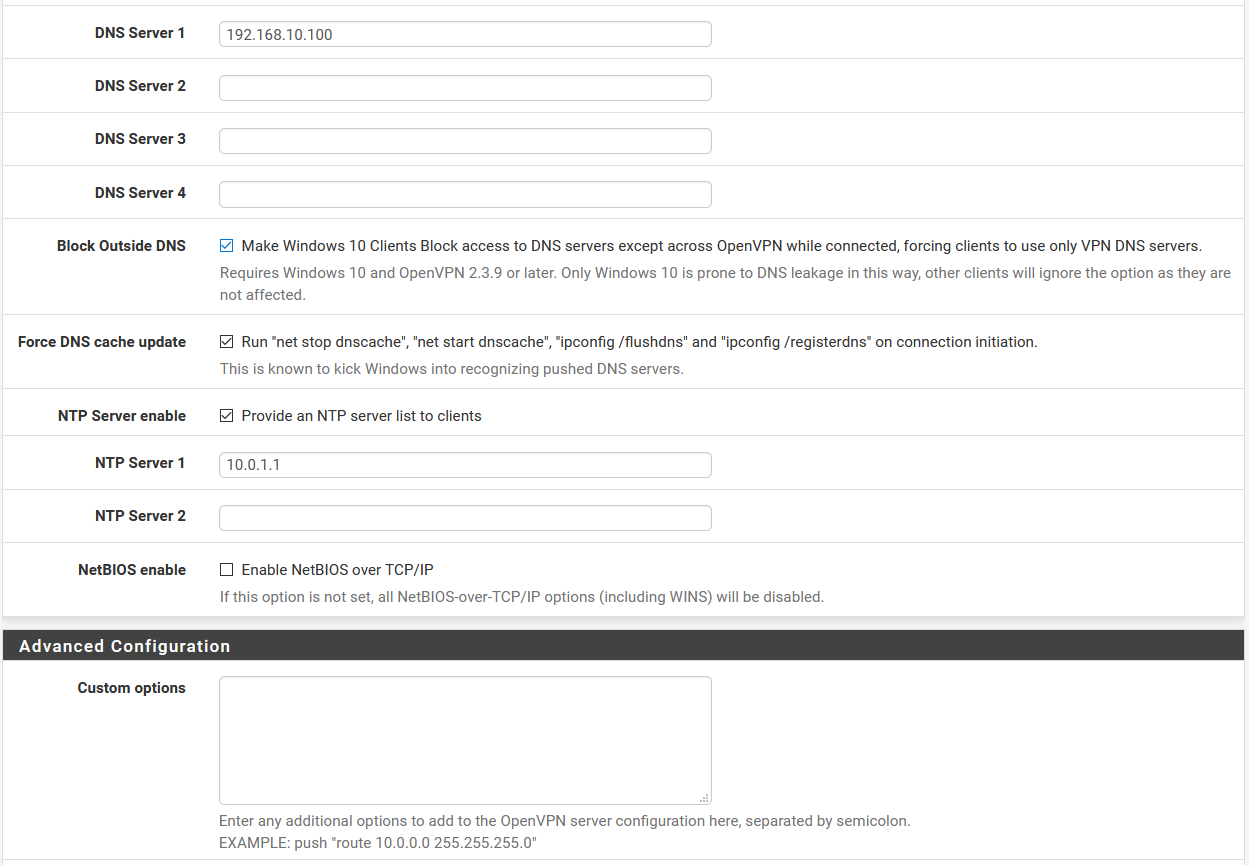
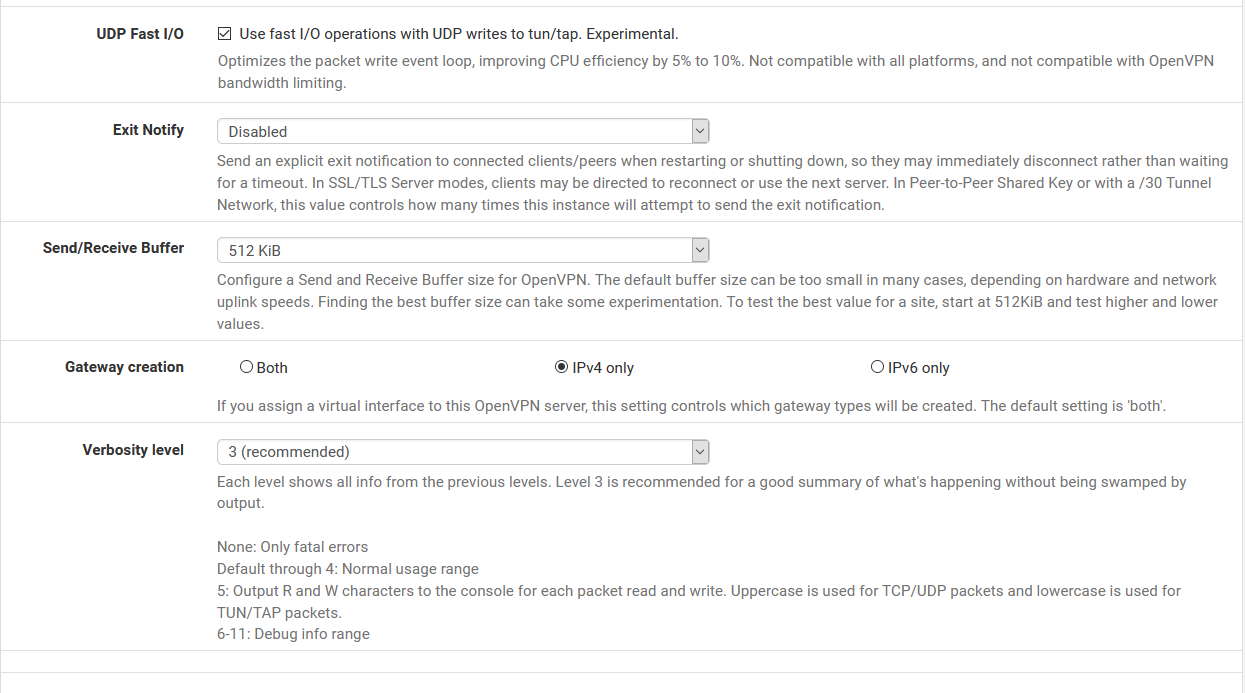
When my laptop is NOT connected to the VPN server, here are the traffic graphs:
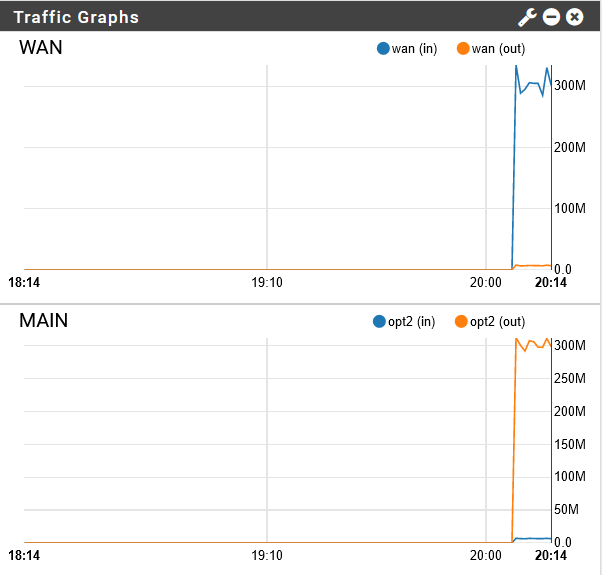
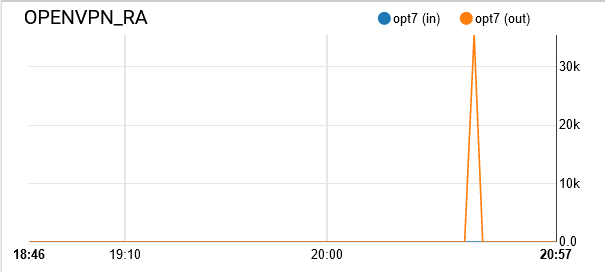
As soon as I connect it to the VPN server:
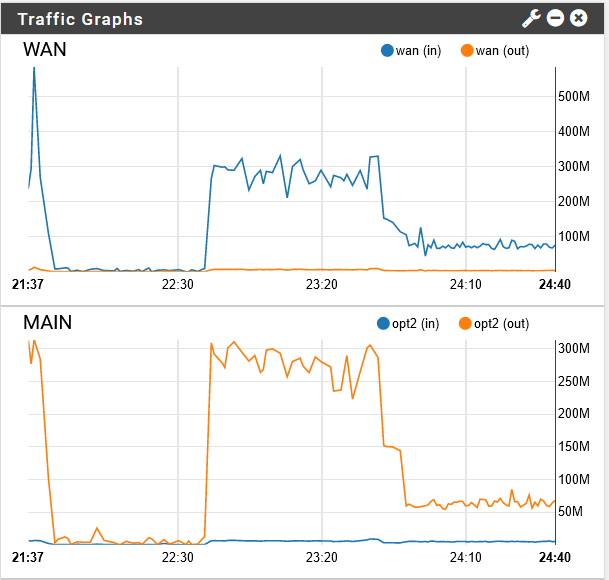
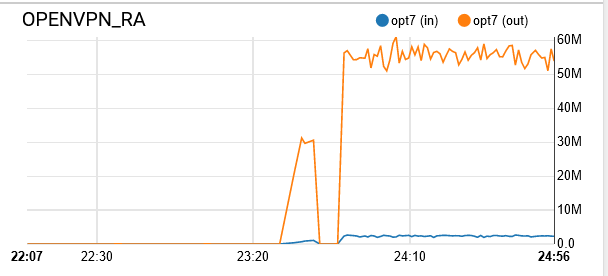
See the sudden drop in speed? When I disconnect from the VPN server, the speed goes back up to the saturation point. Any ideas?
-
We use more than 20 APU4 boards in our system with OpenVPN.
The value will not be higher! (cca. 55 Mbps)
This is what the APU board can screw out of of itself, since OpenVPN uses only 1 CPU core and in this case is1 .0 GHz or 1.4 GHz (1.4 if you do the tuning, but that only applies to one core).
We've been experimenting for a long time to achieve higher speeds, but low CPU clock can do just that with OpenVPN.Under the same conditions, a Supermicro M11SDV-4C-LN4F-based pfSense 310 to 340 Mbps can be accessed in the same location with the same installation.
This is proof of the above.BTW, your setting is completely correct!
Regarding OpenVPN, the CPU clock is your best friend. -
That's what I thought. Does that mean that the CPU usage in the pfsense dashboard means overall CPU usage and not just single core? I just don't see it peaking at 100% while running the test. I tried it again with speedtest and got it to be higher:
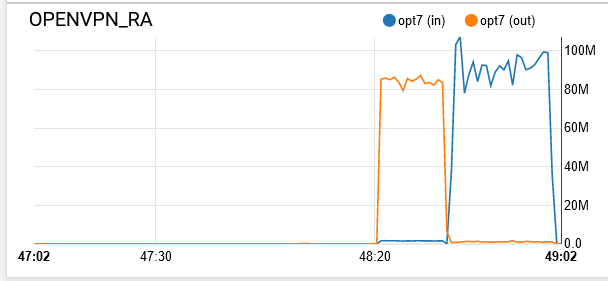
https://www.speedtest.net/result/9415734802I don't understand how it got higher though. The battle.net game download I had earlier was saturating the link without the VPN connection so I was expecting it to be more or less the same as the speedtest result.
Does that mean that it's better to do IPsec road warrior server then?
-
@kevindd992002 said in PC Engines apu2 experiences:
https://www.speedtest.net
Exactly! if you want better values then IPsec. (multithreading)
Since we use ExpressVPN and our own OpenVPN tunnels, we can't switch to IPsec, we just accepted the fact that, these motherboards can do just that.
The measurements depend on a lot of things, the current load and what else is running on the APU under pfSense, such as Squid, pfBlocketNG, Snort / Suricata.The graphs show aggregate values and can be suggestive.
Measurements can also be performed in several ways, such as https://fast.com/ and https://speedof.me/ and https://www.meter.net/ping-test/.
I personally don't like the https://www.speedtest.net -
Run
top -aSHat the command line while testing to see how the CPU cores are loaded.You have NCP enabled and you have AES-CBC and AES-GCM set as NCP ciphers. Which is it actually connecting with?
I would disable NCP there to force it to use AES-128-GCM which you have selected. I would expect that to be fastest.
Steve
-
NCP is a good idea Steve, but it won’t help much.
Compare these two settings with one NCP and the other W/O NCP.
(We work with each provider and have experience with these settings.)
or
There is no significant difference between the obtained velocities.
We have been using APU boards for 5 years and these are long-term experiences. -
@DaddyGo said in PC Engines apu2 experiences:
@kevindd992002 said in PC Engines apu2 experiences:
https://www.speedtest.net
Exactly! if you want better values then IPsec. (multithreading)
Since we use ExpressVPN and our own OpenVPN tunnels, we can't switch to IPsec, we just accepted the fact that, these motherboards can do just that.
The measurements depend on a lot of things, the current load and what else is running on the APU under pfSense, such as Squid, pfBlocketNG, Snort / Suricata.The graphs show aggregate values and can be suggestive.
Measurements can also be performed in several ways, such as https://fast.com/ and https://speedof.me/ and https://www.meter.net/ping-test/.
I personally don't like the https://www.speedtest.netI see. I have to get my head around using IPsec then. I tried establishing an Ipsec connection as described here but failed.
Yes, I understand that they show aggregate values but I only have one test client connected to the OpenVPN server when I tested that. Here's what I see with the other test sites:
fast.com = 82 Mbps
speedof.me = 60 Mbps
meter.net = 68 MbpsFor me, usually fast.com and speedtest.net almost always saturates my link.
@stephenw10 said in PC Engines apu2 experiences:
Run
top -aSHat the command line while testing to see how the CPU cores are loaded.You have NCP enabled and you have AES-CBC and AES-GCM set as NCP ciphers. Which is it actually connecting with?
I would disable NCP there to force it to use AES-128-GCM which you have selected. I would expect that to be fastest.
Steve
Ok, yeah I see that the process is only using one CPU while running the test.
The connection is using the AES-128-GCM as expected but disabling NCP to force AES-128-GCM makes sense.
-
@DaddyGo said in PC Engines apu2 experiences:
NCP is a good idea Steve, but it won’t help much.
Compare these two settings with one NCP and the other W/O NCP.
(We work with each provider and have experience with these settings.)
or

There is no significant difference between the obtained velocities.
We have been using APU boards for 5 years and these are long-term experiences.I don't think he's saying that NCP helps. If anything, he's suggesting to disable NCP on my settings to force the AES-128-GCM cipher.
-
Of the above two providers, it uses one CBC and the other GCM, due to the finite performance of the APU board, no significant difference is seen.
I know he doesn't say it helps ;-) (NCP)
IPsec requires a little more care to set up, there are several good descriptions as I have seen in the forum in the past.
What I can tell you for sure is that I know APU boards very well, and we love them very much.
Only as long as the Chihuahua is a good lap dog, he is a very bad Caucasian bear killer. :-)