IPsec ikev 2 mobile, disconnetcs after 7:45 -- 8 hours - Windows 10 client
-
Hello everyone!
I'm trying to overcome the problem with Windows clients IPsec
connection breaks after 7:45 hours
at the same time, the Disable Rekey values are set, or, I set the tunnel lifetime longer, for example 86400 seconds (24 hours) (default 28800 seconds) - restart the IPsec service - and everything also, on Windows connects lasts 7:45 hoursIf you set the values of the tunnel lifetime in phase 1 to less than 28800 sec, then yes, disconnection initiates pfsense
in IPsec logs on pf, while the connection is live, every hour there is a key exchange
User authentication occurs through RADIUS, in the domain.
maybe there is some kind of timeout setting in windows ..
here someone casually mentioned this ...
[http://rockhoppervpn.sourceforge.net/ref_tips_win7.html](link url) -
What shows up in the IPsec log on pfSense when the client disconnects?
It sounds like a client-side problem to me, though. You might want to post about it on a Windows-focused forum of some kind instead.
-
Could it be this one (Phase 2 lifetime)?
https://forum.netgate.com/topic/139727/ikev2-ipsec-d%C3%A9connect%C3%A9-apr%C3%A8s-60min/2
-
@jimp Thanks fo answer!
this is my log
I deleted a lot of extra lines vici with content"May 7 18:41:27 charon 08[CFG] vici client 200 connected
May 7 18:41:27 charon 11[CFG] vici client 200 registered for: list-sa
May 7 18:41:27 charon 07[CFG] vici client 200 requests: list-sas"
so that the log is a little lessI deleted a lot of extra lines with content
so that the log is a little less
in the settings of phase_1, Disable Rekey and the tunnel lifetime are set to 24 hours (nother settings of phase_1 are set by default
in phase_2 Rekey is by default 3600 secI deleted the middle of the log
left only the beginning and end of the log(not fit here all, and right)
username who connected is TESTUSER_DOMAIN
MY7 12:11:00 ch 10[NET] <1> received packet: from CLNT_IP_ADRS-YY[500] to SRV_IP_ADDR[500] (604 bytes)
MY7 12:11:00 ch 10[ENC] <1> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V ]
MY7 12:11:00 ch 10[CFG] <1> looking for an IKEv2 config for SRV_IP_ADDR...CLNT_IP_ADRS-YY
MY7 12:11:00 ch 10[CFG] <1> candidate: %any...%any, prio 24
MY7 12:11:00 ch 10[CFG] <1> candidate: SRV_IP_ADDR...%any, prio 1052
MY7 12:11:00 ch 10[CFG] <1> found matching ike config: SRV_IP_ADDR...%any with prio 1052
MY7 12:11:00 ch 10[IKE] <1> received MS NT5 ISAKMPOAKLEY v9 vendor ID
MY7 12:11:00 ch 10[IKE] <1> received MS-Negotiation Discovery Capable vendor ID
MY7 12:11:00 ch 10[ENC] <1> received unknown vendor ID:
MY7 12:11:00 ch 10[IKE] <1> CLNT_IP_ADRS-YY is initiating an IKE_SA
MY7 12:11:00 ch 10[IKE] <1> IKE_SA (unnamed)[1] state change: CREATED => CONNECTING
MY7 12:11:00 ch 10[CFG] <1> selecting proposal:
MY7 12:11:00 ch 10[CFG] <1> no acceptable ENCRYPTION_ALGORITHM found
MY7 12:11:00 ch 10[CFG] <1> selecting proposal:
MY7 12:11:00 ch 10[CFG] <1> no acceptable INTEGRITY_ALGORITHM found
MY7 12:11:00 ch 10[CFG] <1> selecting proposal:
MY7 12:11:00 ch 10[CFG] <1> no acceptable ENCRYPTION_ALGORITHM found
MY7 12:11:00 ch 10[CFG] <1> selecting proposal:
MY7 12:11:00 ch 10[CFG] <1> proposal matches
MY7 12:11:00 ch 10[CFG] <1> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024
MY7 12:11:00 ch 10[CFG] <1> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
MY7 12:11:00 ch 10[CFG] <1> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
MY7 12:11:00 ch 10[IKE] <1> remote host is behind NAT
MY7 12:11:00 ch 10[IKE] <1> sending cert request for "DC=ru, DC=TSTDOM, CN=TSTDOM-SRV-ADX-CA"
MY7 12:11:00 ch 10[ENC] <1> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ]
MY7 12:11:00 ch 10[NET] <1> sending packet: from SRV_IP_ADDR[500] to CLNT_IP_ADRS-YY[500] (353 bytes)
MY7 12:11:00 ch 10[NET] <1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (580 bytes)
MY7 12:11:00 ch 10[ENC] <1> parsed IKE_AUTH request 1 [ EF(1/3) ]
MY7 12:11:00 ch 10[ENC] <1> received fragment #1 of 3, waiting for complete IKE message
MY7 12:11:00 ch 10[NET] <1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (580 bytes)
MY7 12:11:00 ch 10[ENC] <1> parsed IKE_AUTH request 1 [ EF(2/3) ]
MY7 12:11:00 ch 10[ENC] <1> received fragment #2 of 3, waiting for complete IKE message
MY7 12:11:00 ch 10[NET] <1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (148 bytes)
MY7 12:11:00 ch 10[ENC] <1> parsed IKE_AUTH request 1 [ EF(3/3) ]
MY7 12:11:00 ch 10[ENC] <1> received fragment #3 of 3, reassembled fragmented IKE message (1136 bytes)
MY7 12:11:00 ch 10[ENC] <1> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV) SA TSi TSr ]
MY7 12:11:00 ch 10[IKE] <1> received cert request for "DC=ru, DC=TSTDOM, CN=TSTDOM-SRV-ADX-CA"MY7 12:11:00 ch 10[IKE] <1> received 39 cert requests for an unknown ca
MY7 12:11:00 ch 10[CFG] <1> looking for peer configs matching SRV_IP_ADDR[%any]...CLNT_IP_ADRS-YY[192.168.1.99]
MY7 12:11:00 ch 10[CFG] <1> candidate "bypasslan", match: 1/1/24 (me/other/ike)
MY7 12:11:00 ch 10[CFG] <1> candidate "cn-mble", match: 1/1/1052 (me/other/ike)
MY7 12:11:00 ch 10[CFG] <1> ignore candidate 'bypasslan' without matching IKE proposal
MY7 12:11:00 ch 10[CFG] <cn-mble|1> selected peer config 'cn-mble'
MY7 12:11:00 ch 10[IKE] <cn-mble|1> initiating EAP_IDENTITY method (id 0x00)
MY7 12:11:00 ch 10[IKE] <cn-mble|1> processing INTERNAL_IP4_ADDRESS attribute
MY7 12:11:00 ch 10[IKE] <cn-mble|1> processing INTERNAL_IP4_DNS attribute
MY7 12:11:00 ch 10[IKE] <cn-mble|1> processing INTERNAL_IP4_NBNS attribute
MY7 12:11:00 ch 10[IKE] <cn-mble|1> processing INTERNAL_IP4_SERVER attribute
MY7 12:11:00 ch 10[IKE] <cn-mble|1> peer supports MOBIKE
MY7 12:11:00 ch 10[IKE] <cn-mble|1> authentication of 'mail.TSTDOM.ru' (myself) with RSA signature successful
MY7 12:11:00 ch 10[IKE] <cn-mble|1> sending end entity cert "C=RU, ST=Moscow, L=Moscow, O=TSTDOM, OU=it, CN=vpn.wrong_domain"
MY7 12:11:00 ch 10[ENC] <cn-mble|1> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
MY7 12:11:00 ch 10[ENC] <cn-mble|1> splitting IKE message (1936 bytes) into 2 fragments
MY7 12:11:00 ch 10[ENC] <cn-mble|1> generating IKE_AUTH response 1 [ EF(1/2) ]
MY7 12:11:00 ch 10[ENC] <cn-mble|1> generating IKE_AUTH response 1 [ EF(2/2) ]
MY7 12:11:00 ch 10[NET] <cn-mble|1> sending packet: from SRV_IP_ADDR[4500] to CLNT_IP_ADRS-YY[4500] (1236 bytes)
MY7 12:11:00 ch 10[NET] <cn-mble|1> sending packet: from SRV_IP_ADDR[4500] to CLNT_IP_ADRS-YY[4500] (772 bytes)
MY7 12:11:00 ch 08[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (80 bytes)
MY7 12:11:00 ch 08[ENC] <cn-mble|1> parsed IKE_AUTH request 2 [ EAP/RES/ID ]
MY7 12:11:00 ch 08[IKE] <cn-mble|1> received EAP identity 'TESTUSER_DOMAIN'
MY7 12:11:00 ch 08[CFG] <cn-mble|1> RADIUS server 'radius' is candidate: 210
MY7 12:11:00 ch 08[CFG] <cn-mble|1> sending RADIUS Access-Request to server 'radius'
MY7 12:11:00 ch 08[CFG] <cn-mble|1> received RADIUS Access-Challenge from server 'radius'
MY7 12:11:00 ch 08[IKE] <cn-mble|1> initiating EAP_MSCHAPV2 method (id 0x01)
MY7 12:11:00 ch 08[ENC] <cn-mble|1> generating IKE_AUTH response 2 [ EAP/REQ/MSCHAPV2 ]
MY7 12:11:00 ch 08[NET] <cn-mble|1> sending packet: from SRV_IP_ADDR[4500] to CLNT_IP_ADRS-YY[4500] (112 bytes)
MY7 12:11:00 ch 08[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (144 bytes)
MY7 12:11:00 ch 08[ENC] <cn-mble|1> parsed IKE_AUTH request 3 [ EAP/RES/MSCHAPV2 ]
MY7 12:11:00 ch 08[CFG] <cn-mble|1> sending RADIUS Access-Request to server 'radius'
MY7 12:11:00 ch 08[CFG] <cn-mble|1> received RADIUS Access-Challenge from server 'radius'
MY7 12:11:00 ch 08[ENC] <cn-mble|1> generating IKE_AUTH response 3 [ EAP/REQ/MSCHAPV2 ]
MY7 12:11:00 ch 08[NET] <cn-mble|1> sending packet: from SRV_IP_ADDR[4500] to CLNT_IP_ADRS-YY[4500] (128 bytes)
MY7 12:11:00 ch 09[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (80 bytes)
MY7 12:11:00 ch 09[ENC] <cn-mble|1> parsed IKE_AUTH request 4 [ EAP/RES/MSCHAPV2 ]
MY7 12:11:00 ch 09[CFG] <cn-mble|1> sending RADIUS Access-Request to server 'radius'
MY7 12:11:00 ch 09[CFG] <cn-mble|1> received RADIUS Access-Accept from server 'radius'
MY7 12:11:00 ch 09[IKE] <cn-mble|1> RADIUS authentication of 'TESTUSER_DOMAIN' successful
MY7 12:11:00 ch 09[IKE] <cn-mble|1> EAP method EAP_MSCHAPV2 succeeded, MSK established
MY7 12:11:00 ch 09[ENC] <cn-mble|1> generating IKE_AUTH response 4 [ EAP/SUCC ]
MY7 12:11:00 ch 09[NET] <cn-mble|1> sending packet: from SRV_IP_ADDR[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 12:11:00 ch 09[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDR[4500] (112 bytes)
MY7 12:11:00 ch 09[ENC] <cn-mble|1> parsed IKE_AUTH request 5 [ AUTH ]
MY7 12:11:00 ch 09[IKE] <cn-mble|1> authentication of '192.168.1.99' with EAP successful
MY7 12:11:00 ch 09[IKE] <cn-mble|1> authentication of 'mail.TSTDOM.ru' (myself) with EAP
MY7 12:11:00 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[1] established between SRV_IP_ADDR[mail.TSTDOM.ru]...CLNT_IP_ADRS-YY[192.168.1.99]
MY7 12:11:00 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[1] state change: CONNECTING => ESTABLISHED
MY7 12:11:00 ch 09[IKE] <cn-mble|1> peer requested virtual IP %any
MY7 12:11:00 ch 09[CFG] <cn-mble|1> assigning new lease to 'TESTUSER_DOMAIN'
MY7 12:11:00 ch 09[IKE] <cn-mble|1> assigning virtual IP 10.80.5.1 to peer 'TESTUSER_DOMAIN'
MY7 12:11:00 ch 09[IKE] <cn-mble|1> building INTERNAL_IP4_SUBNET attribute
MY7 12:11:00 ch 09[IKE] <cn-mble|1> building UNITY_DEF_DOMAIN attribute
MY7 12:11:00 ch 09[IKE] <cn-mble|1> building UNITY_SPLITDNS_NAME attribute
MY7 12:11:00 ch 09[IKE] <cn-mble|1> building INTERNAL_IP4_DNS attribute
MY7 12:11:00 ch 09[CFG] <cn-mble|1> looking for a child config for 0.0.0.0/0|/0 ::/0|/0 === 0.0.0.0/0|/0 ::/0|/0
MY7 12:11:00 ch 09[CFG] <cn-mble|1> proposing traffic selectors for us:MY7 19:37:00 ch 05[CFG] vc clnt 822 disconnected
MY7 19:37:02 ch 11[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (352 bytes)
MY7 19:37:02 ch 11[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 20 [ N(REKEY_SA) SA No TSi TSr ]
MY7 19:37:02 ch 11[CFG] <cn-mble|1> selecting proposal:
MY7 19:37:02 ch 11[CFG] <cn-mble|1> proposal matches
MY7 19:37:02 ch 11[CFG] <cn-mble|1> received proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ
MY7 19:37:02 ch 11[CFG] <cn-mble|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_512_256/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_GCM_16_192/NO_EXT_SEQ, ESP:AES_GCM_16_192/NO_EXT_SEQ, ESP:AES_GCM_16_192/NO_EXT_SEQ, ESP:AES_GCM_16_192/NO_EXT_SEQ, ESP:AES_GCM_12_192/NO_EXT_SEQ, ESP:AES_GCM_12_192/NO_EXT_SEQ, ESP:AES_GCM_12_192/NO_EXT_SEQ, ESP:AES_GCM_12_192/NO_EXT_SEQ, ESP:AES_GCM_8_192/NO_EXT_SEQ, ESP:AES_GCM_8_192/NO_EXT_SEQ, ESP:AES_GCM_8_192/NO_EXT_SEQ, ESP:AES_GCM_8_192/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ
MY7 19:37:02 ch 11[CFG] <cn-mble|1> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
MY7 19:37:02 ch 11[CFG] <cn-mble|1> selecting traffic selectors for us:
MY7 19:37:02 ch 11[CFG] <cn-mble|1> config: 10.100.1.0/24|/0, received: 0.0.0.0/0|/0 => match: 10.100.1.0/24|/0
MY7 19:37:02 ch 11[CFG] <cn-mble|1> config: 10.100.1.0/24|/0, received: ::/0|/0 => no match
MY7 19:37:02 ch 11[CFG] <cn-mble|1> selecting traffic selectors for other:
MY7 19:37:02 ch 11[CFG] <cn-mble|1> config: 10.80.5.1/32|/0, received: 0.0.0.0/0|/0 => match: 10.80.5.1/32|/0
MY7 19:37:02 ch 11[CFG] <cn-mble|1> config: 10.80.5.1/32|/0, received: ::/0|/0 => no match
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{9} state change: CREATED => INSTALLING
MY7 19:37:02 ch 11[CHD] <cn-mble|1> using AES_CBC for encryption
MY7 19:37:02 ch 11[CHD] <cn-mble|1> using HMAC_SHA1_96 for integrity
MY7 19:37:02 ch 11[CHD] <cn-mble|1> adding inbound ESP SA
MY7 19:37:02 ch 11[CHD] <cn-mble|1> SPI 0xc0dcd51a, src CLNT_IP_ADRS-YY dst SRV_IP_ADDRS
MY7 19:37:02 ch 11[CHD] <cn-mble|1> registering outbound ESP SA
MY7 19:37:02 ch 11[CHD] <cn-mble|1> SPI 0xa9f0bc36, src SRV_IP_ADDRS dst CLNT_IP_ADRS-YY
MY7 19:37:02 ch 11[IKE] <cn-mble|1> inbound CHILD_SA cn-mble{9} established with SPIs c0dcd51a_i a9f0bc36_o and TS 10.100.1.0/24|/0 === 10.80.5.1/32|/0
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{9} state change: INSTALLING => INSTALLED
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{8} state change: INSTALLED => REKEYING
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{8} state change: REKEYING => REKEYED
MY7 19:37:02 ch 11[ENC] <cn-mble|1> generating CREATE_CHILD_SA response 20 [ N(ESP_TFC_PAD_N) SA No TSi TSr ]
MY7 19:37:02 ch 11[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (208 bytes)
MY7 19:37:02 ch 11[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (80 bytes)
MY7 19:37:02 ch 11[ENC] <cn-mble|1> parsed INFORMATIONAL request 21 [ D ]
MY7 19:37:02 ch 11[IKE] <cn-mble|1> received DELETE for ESP CHILD_SA with SPI ca0f503e
MY7 19:37:02 ch 11[IKE] <cn-mble|1> closing CHILD_SA cn-mble{8} with SPIs ceb7ae5c_i (750246 bytes) ca0f503e_o (1603624 bytes) and TS 10.100.1.0/24|/0 === 10.80.5.1/32|/0
MY7 19:37:02 ch 11[IKE] <cn-mble|1> sending DELETE for ESP CHILD_SA with SPI ceb7ae5c
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{8} state change: REKEYED => DELETING
MY7 19:37:02 ch 11[IKE] <cn-mble|1> CHILD_SA closed
MY7 19:37:02 ch 11[CHD] <cn-mble|1> CHILD_SA cn-mble{8} state change: DELETING => DELETED
MY7 19:37:02 ch 11[CHD] <cn-mble|1> adding outbound ESP SA
MY7 19:37:02 ch 11[CHD] <cn-mble|1> SPI 0xa9f0bc36, src SRV_IP_ADDRS dst CLNT_IP_ADRS-YY
MY7 19:37:02 ch 11[IKE] <cn-mble|1> outbound CHILD_SA cn-mble{9} established with SPIs c0dcd51a_i a9f0bc36_o and TS 10.100.1.0/24|/0 === 10.80.5.1/32|/0
MY7 19:37:02 ch 11[ENC] <cn-mble|1> generating INFORMATIONAL response 21 [ D ]
MY7 19:37:02 ch 11[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:37:05 ch 15[CFG] vc clnt 823 connected
MY7 19:37:05 ch 10[CFG] vc clnt 823 disconnected
MY7 19:37:07 ch 16[IKE] <cn-mble|1> queueing CHILD_DELETE task
MY7 19:37:07 ch 16[IKE] <cn-mble|1> activating new tasks
MY7 19:37:07 ch 16[IKE] <cn-mble|1> activating CHILD_DELETE task
MY7 19:37:07 ch 16[CHD] <cn-mble|1> CHILD_SA cn-mble{8} state change: DELETED => DESTROYING
MY7 19:37:07 ch 16[IKE] <cn-mble|1> activating new tasks
MY7 19:37:07 ch 16[IKE] <cn-mble|1> nothing to initiate
MY7 19:37:11 ch 16[CFG] vc clnt 824 connected
MY7 19:37:11 ch 07[CFG] vc clnt 824 registered for: list-sa
MY7 19:37:11 ch 07[CFG] vc clnt 824 requests: list-sas
MY7 19:37:11 ch 06[CFG] vc clnt 824 disconnected
MY7 19:46:55 ch 05[CFG] vc clnt 933 disconnected
MY7 19:47:00 ch 16[CFG] vc clnt 934 connected
MY7 19:47:00 ch 07[CFG] vc clnt 934 registered for: list-sa
MY7 19:47:00 ch 07[CFG] vc clnt 934 requests: list-sas
MY7 19:47:00 ch 07[CFG] vc clnt 934 disconnected
MY7 19:47:01 ch 10[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:01 ch 10[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:01 ch 10[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:01 ch 09[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:01 ch 09[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:01 ch 09[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:01 ch 09[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:01 ch 09[IKE] <cn-mble|1> CLNT_IP_ADRS-YY is initiating an IKE_SA
MY7 19:47:01 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[2] state change: CREATED => CONNECTING
MY7 19:47:01 ch 09[CFG] <cn-mble|1> selecting proposal:
MY7 19:47:01 ch 09[CFG] <cn-mble|1> no acceptable ENCRYPTION_ALGORITHM found
MY7 19:47:01 ch 09[CFG] <cn-mble|1> selecting proposal:
MY7 19:47:01 ch 09[CFG] <cn-mble|1> no acceptable INTEGRITY_ALGORITHM found
MY7 19:47:01 ch 09[CFG] <cn-mble|1> selecting proposal:
MY7 19:47:01 ch 09[CFG] <cn-mble|1> no acceptable ENCRYPTION_ALGORITHM found
MY7 19:47:01 ch 09[CFG] <cn-mble|1> selecting proposal:
MY7 19:47:01 ch 09[CFG] <cn-mble|1> proposal matches
MY7 19:47:01 ch 09[CFG] <cn-mble|1> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024
MY7 19:47:01 ch 09[CFG] <cn-mble|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
MY7 19:47:01 ch 09[CFG] <cn-mble|1> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
MY7 19:47:01 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[2] state change: CONNECTING => ESTABLISHED
MY7 19:47:01 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[2] rekeyed between SRV_IP_ADDRS[mail.TSTDOM.ru]...CLNT_IP_ADRS-YY[192.168.1.99]
MY7 19:47:01 ch 09[IKE] <cn-mble|1> IKE_SA cn-mble[1] state change: ESTABLISHED => REKEYED
MY7 19:47:01 ch 09[ENC] <cn-mble|1> generating CREATE_CHILD_SA response 22 [ SA No KE ]
MY7 19:47:01 ch 09[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:02 ch 09[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:02 ch 09[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:02 ch 09[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:02 ch 10[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:02 ch 10[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:02 ch 10[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:02 ch 10[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:02 ch 10[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:02 ch 10[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:03 ch 10[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:03 ch 10[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:03 ch 10[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:03 ch 09[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:03 ch 09[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:03 ch 09[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:03 ch 09[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:03 ch 09[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:03 ch 09[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:05 ch 10[CFG] vc clnt 935 connected
MY7 19:47:05 ch 15[CFG] vc clnt 935 disconnected
MY7 19:47:06 ch 08[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:06 ch 08[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:06 ch 08[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:06 ch 05[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:06 ch 05[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:06 ch 05[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:06 ch 05[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:06 ch 05[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:06 ch 05[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:11 ch 08[CFG] vc clnt 936 connected
MY7 19:47:11 ch 08[CFG] vc clnt 936 disconnected
MY7 19:47:13 ch 16[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:13 ch 16[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:13 ch 16[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:13 ch 07[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:13 ch 07[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:13 ch 07[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:13 ch 07[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:13 ch 07[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:13 ch 07[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:16 ch 16[CFG] vc clnt 937 connected
MY7 19:47:22 ch 05[IKE] <cn-mble|1> sending DPD request
MY7 19:47:22 ch 05[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:47:22 ch 05[IKE] <cn-mble|1> activating new tasks
MY7 19:47:22 ch 05[IKE] <cn-mble|1> nothing to initiate
MY7 19:47:27 ch 08[CFG] vc clnt 939 connected
MY7 19:47:27 ch 05[CFG] vc clnt 939 disconnected
MY7 19:47:27 ch 05[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:27 ch 05[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:27 ch 05[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:27 ch 06[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:27 ch 06[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:27 ch 06[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:27 ch 06[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:27 ch 06[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:27 ch 06[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:32 ch 16[CFG] vc clnt 940 connecteds
MY7 19:47:32 ch 07[CFG] vc clnt 940 disconnected
MY7 19:47:37 ch 09[IKE] <cn-mble|1> sending DPD request
MY7 19:47:37 ch 09[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:47:37 ch 09[IKE] <cn-mble|1> activating new tasks
MY7 19:47:37 ch 09[IKE] <cn-mble|1> nothing to initiate
MY7 19:47:37 ch 10[CFG] vc clnt 941 connectedist-sa
MY7 19:47:43 ch 08[CFG] vc clnt 942 disconnected
MY7 19:47:47 ch 13[IKE] <cn-mble|1> sending DPD request
MY7 19:47:47 ch 13[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:47:47 ch 13[IKE] <cn-mble|1> activating new tasks
MY7 19:47:47 ch 13[IKE] <cn-mble|1> nothing to initiateas
MY7 19:47:54 ch 11[CFG] vc clnt 944 disconnected
MY7 19:47:55 ch 14[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (580 bytes)
MY7 19:47:55 ch 14[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(1/2) ]
MY7 19:47:55 ch 14[ENC] <cn-mble|1> received fragment #1 of 2, waiting for complete IKE message
MY7 19:47:55 ch 08[NET] <cn-mble|1> received packet: from CLNT_IP_ADRS-YY[4500] to SRV_IP_ADDRS[4500] (84 bytes)
MY7 19:47:55 ch 08[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ EF(2/2) ]
MY7 19:47:55 ch 08[ENC] <cn-mble|1> received fragment #2 of 2, reassembled fragmented IKE message (576 bytes)
MY7 19:47:55 ch 08[ENC] <cn-mble|1> parsed CREATE_CHILD_SA request 22 [ SA KE No N(FRAG_SUP) ]
MY7 19:47:55 ch 08[IKE] <cn-mble|1> received retransmit of request with ID 22, retransmitting response
MY7 19:47:55 ch 08[NET] <cn-mble|1> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (304 bytes)
MY7 19:47:59 ch 14[CFG] vc clnt 945 connected
MY7 19:48:05 ch 09[IKE] <cn-mble|1> sending DPD request
MY7 19:48:05 ch 09[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:48:05 ch 09[IKE] <cn-mble|1> activating new tasks
MY7 19:48:05 ch 09[IKE] <cn-mble|1> nothing to initiate
MY7 19:48:15 ch 15[IKE] <cn-mble|1> sending DPD request
MY7 19:48:15 ch 15[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:48:15 ch 15[IKE] <cn-mble|1> activating new tasks
MY7 19:48:15 ch 15[IKE] <cn-mble|1> nothing to initiate
MY7 19:48:25 ch 12[IKE] <cn-mble|1> sending DPD request
MY7 19:48:25 ch 12[IKE] <cn-mble|1> queueing IKE_DPD task
MY7 19:48:25 ch 12[IKE] <cn-mble|1> activating new tasks
MY7 19:48:25 ch 12[IKE] <cn-mble|1> nothing to initiate
MY7 19:48:26 ch 09[CFG] vc clnt 950 connected
MY7 19:48:26 ch 12[CFG] vc clnt 950 disconnected
MY7 19:48:31 ch 15[IKE] <cn-mble|1> destroying IKE_SA in state REKEYED without notification
MY7 19:48:31 ch 15[IKE] <cn-mble|1> IKE_SA cn-mble[1] state change: REKEYED => DESTROYING
MY7 19:56:37 ch 06[IKE] <cn-mble|2> sending DPD request
MY7 19:56:37 ch 06[IKE] <cn-mble|2> queueing IKE_DPD task
MY7 19:56:37 ch 06[IKE] <cn-mble|2> activating new tasks
MY7 19:56:37 ch 06[IKE] <cn-mble|2> activating IKE_DPD task
MY7 19:56:37 ch 06[ENC] <cn-mble|2> generating INFORMATIONAL request 0 [ ]
MY7 19:56:37 ch 06[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:56:39 ch 11[CFG] vc clnt 1042 connected
MY7 19:56:39 ch 14[CFG] vc clnt 1042 disconnected
MY7 19:56:41 ch 08[IKE] <cn-mble|2> retransmit 1 of request with message ID 0
MY7 19:56:41 ch 08[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:56:49 ch 16[IKE] <cn-mble|2> retransmit 2 of request with message ID 0
MY7 19:56:49 ch 16[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:56:49 ch 13[CFG] vc clnt 1044 connected
MY7 19:57:00 ch 15[CFG] vc clnt 1046 disconnected
MY7 19:57:02 ch 05[IKE] <cn-mble|2> retransmit 3 of request with message ID 0
MY7 19:57:02 ch 05[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:57:25 ch 09[IKE] <cn-mble|2> retransmit 4 of request with message ID 0
MY7 19:57:25 ch 09[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)sas
MY7 19:57:27 ch 09[CFG] vc clnt 1051 disconnected
MY7 19:58:07 ch 08[IKE] <cn-mble|2> retransmit 5 of request with message ID 0
MY7 19:58:07 ch 08[NET] <cn-mble|2> sending packet: from SRV_IP_ADDRS[4500] to CLNT_IP_ADRS-YY[4500] (80 bytes)
MY7 19:59:23 ch 13[IKE] <cn-mble|2> giving up after 5 retransmits
MY7 19:59:23 ch 13[CFG] <cn-mble|2> RADIUS server 'radius' is candidate: 210
MY7 19:59:23 ch 13[CFG] <cn-mble|2> sending RADIUS Accounting-Request to server 'radius'
MY7 19:59:23 ch 13[CFG] <cn-mble|2> received RADIUS Accounting-Response from server 'radius'
MY7 19:59:23 ch 13[IKE] <cn-mble|2> IKE_SA cn-mble[2] state change: ESTABLISHED => DESTROYING
MY7 19:59:23 ch 13[CHD] <cn-mble|2> CHILD_SA cn-mble{9} state change: INSTALLED => DESTROYING
MY7 19:59:23 ch 13[CFG] <cn-mble|2> lease 10.80.5.1 by 'TESTUSER_DOMAIN' went offline -
I think I found where the problem is growing from.
In the Windows Firewall settings, in the IPsec tab, these values
and default algorithms used for IKEand most importantly time of life. 480 min = 8 hours
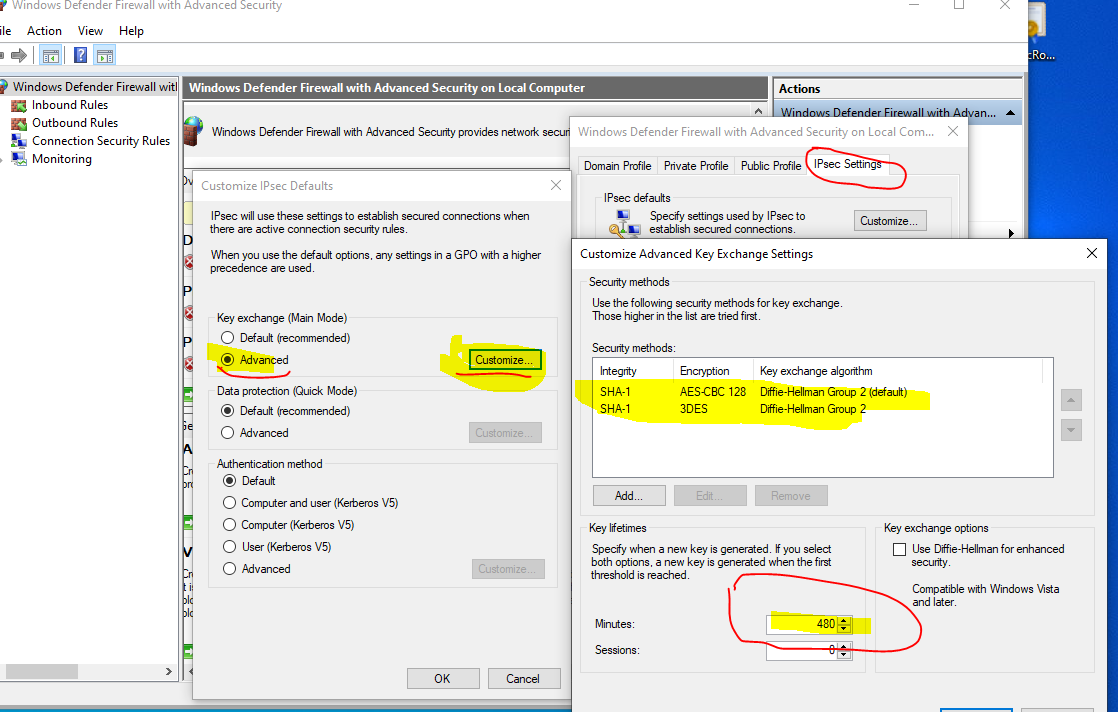
-
interesting that disable rekey does not help. I have to test that too. Normally I don't use my VPN connection so long.
-
@Alitai yes, as a rule, not everyone needs to be connected to work for so long
but nevertheless, many do not have time or still want to sit to work
well, or for someone the uptime of the tunnel is important for more than 8 hours - in my case there are 3D designers - they use network rendering, farms are on the network, and resources (textures, models, that's all, in the same place) put it for the night, for exampleI will put to the test with a large number of minutes of rekey (12 hours) on Windows
I will test further, maybe there is still a problem in the mismatch of phases_1 and 2 on the client (windows) and on pfsense -
I can't confirm. After over 8 hours it's still working. After 7:36 Hours it reestablished the VPN Phase 1 Connection.
-
7h36m is 27,360 seconds which is exactly 95% of 28,800 (8 hours) so a rekey does seem likely.
-
I understood what the problem was, I solved it, there are no more breaks after 8 hours.! (there is a rekey from windows, but it passes successfully)
in Windows by default there were phase_1 algorithms that did not match my Pfsense!:)from GUI, Windows Defender FIrewall with advansed security-Windows Defender Firewall Settings-IPcec Settings, changing the parameters of Phases 1 and 2 do not lead to a positive result, both by algorithms and by the phase life time (Rekeys)
solves the issue of adding a registry parameter to the section:
HKLM\SYSTEM\CurrentControlSet\Services\RasMan\Parameters
parameter(DWORD):
NegotiateDH2048_AES256
value:
1
other parameters can be set, 1 in my opinion is optimal
I give a table with the values of 1 and 2 phases for the registrythis parameter in table:
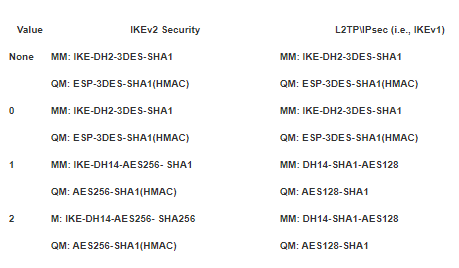 
Of course, you can do all this through power-shell, and probably better, but through the registry it will be easier for someone)
then create a connection (powershell)
in my case it was like this:Add-VpnConnection -Name "TEST" -ServerAddress "vpn.server.com" -TunnelType Ikev2 -EncryptionLevel Required -AuthenticationMethod Eap -SplitTunneling -AllUserConnection -RememberCredential -PassThrusuccessfully connect and look at the parameters of the created SA through a powershell:
Get-NetIPsecMainModeSAin my case it looks like this:
Name : 2 LocalEndpoint : 192.168.1.30 RemoteEndpoint : XXX.XXX.XXX.XXX LocalFirstId.Identity : LocalFirstId.ImpersonationType : None LocalFirstId.AuthenticationMethod : EAP LocalFirstId.Flags : None RemoteFirstId.Identity : vpn.server.com RemoteFirstId.ImpersonationType : None RemoteFirstId.AuthenticationMethod : Certificate RemoteFirstId.Flags : None LocalSecondId.Identity : LocalSecondId.ImpersonationType : LocalSecondId.AuthenticationMethod : LocalSecondId.Flags : RemoteSecondId.Identity : RemoteSecondId.ImpersonationType : RemoteSecondId.AuthenticationMethod : RemoteSecondId.Flags : CipherAlgorithm : AES256 HashAlgorithm : SHA1 GroupId : DH14 KeyModule : IkeV2 MaxQMSAs : 0 LifetimeSeconds : 28800 LocalUdpEncapsulationPort : 4500 RemoteUdpEncapsulationPort : 4500 ExtendedFilterId : 0LifetimeSeconds : 28800I did not find how to change to a smaller or greater side ..
this is some kind of system, hard-wired parameter
there is no information on it
neither registry keys nor power-shell cmdlets, nothing .. (only for Azure IPsec)Well, okay
Anyway, after 28800 sec, Rekey is successful and the connection does not break!
(this is for the test, I wanted to do less so as not to wait 8 hours)summarizing - you need to be more careful about the parameters and algorithms of 1-2 phases both on the server and on the client so that the phases correspond to each other.
and of course, in windows everything is constantly changing from build to version ..
in my case, the problem was on Windows 1903
further you should test more rigorous algorithms.)to all who answered, thank you very much !!!
-
@Alitai you were right!
I needed to check the settings of phase algorithms on windows! -
here also, earlier here on the forum, @groupers made recommendations, you can also stick to them
[https://forum.netgate.com/topic/150670/safe-ikev2-configuration-for-pfsense-and-windows-10-and-macos](link url)
although they contradict what I wrote above, (deleting the registry key, and setting up the algorithms through the powershell) the essence is the same = setting the same parameters both on the pfsense and on Windows