Routing configuration issue between 3 interfaces on pfsense (New to pfsense)
-
Routing configuration issue between 3 interfaces on pfsense:
pfsense version : 2.4.3
Network Address as below:
NW -A - 10.1.1.0/24 / GW - 10.1.1.1
NW -B - 10.1.2.0/24 / GW - 10.1.2.1
NW -C - 10.1.3.0/24/ GW - 10.1.3.1- The above mentioned Gateways are the ones that are configured as gateway to the respective machines in each subnet.
- ICMP rule (any,any) has been open between all the 3 networks, so that I can verify basic connectivity via ping.
Questions:
- Ping requests appear to work only between some IPs within the above mentioned subnet and not to all. Why ?
- Does pfsense work in stateful mode or do we need to configure both inbound and outbound rules separately.?
Thanks in Advance.
Regards
Viki -
@Viki-R said in Routing configuration issue between 3 interfaces on pfsense (New to pfsense):
Ping requests appear to work only between some IPs within the above mentioned subnet and not to all. Why ?
Probably it is blocked by the destination device.
@Viki-R said in Routing configuration issue between 3 interfaces on pfsense (New to pfsense):
Does pfsense work in stateful mode or do we need to configure both inbound and outbound rules separately.?
pfSense use states to allow responses.
However, ICMP is stateless. -
@viragomann Thank you on the quick response.
Would like to share a config info with an example below:
NW -A - 10.1.1.0/24 / GW - 10.1.1.1
NW -B - 10.1.2.0/24 / GW - 10.1.2.1
NW -C - 10.1.3.0/24/ GW - 10.1.3.1NW-A
PC-1 - 10.1.1.50/24
PC-2 - 10.1.1.100/24NW-B
PC-1 - 10.1.2.50/24
PC-2 - 10.1.2.100/24PC-1-A can ping to PC-1-B
PC-1-A cannot Ping to PC-2-B & vice versaBoth the networks we only have Win 10 desktops where windows firewall is off.
===========
With regards to your answer "pfSense use states to allow responses."
Does this mean i do not have to allow both inbound and outbound traffic separately?
-
Do we need to configure static routing between the different networks on pfsense.
I thought pfsense would be aware of all the interfaces that has been attached to it and we only have to mange the rules part.
Please correct me if wrong -
Yes, you have only to add rules to that interface, where the traffic is coming into pfSense. So to allow ping from NW A to B you only need an allow rule on A tab.
Check the docs for details: https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
Seem you're a beginner on pfSense. Maybe you did something wrong in basic setup.
@Viki-R said in Routing configuration issue between 3 interfaces on pfsense (New to pfsense):
NW -A - 10.1.1.0/24 / GW - 10.1.1.1
NW -B - 10.1.2.0/24 / GW - 10.1.2.1
NW -C - 10.1.3.0/24/ GW - 10.1.3.1So you have configured these networks on different interfaces. The GW IP is assigned to the pfSense interface?
And in the interface settings there is- no Upstream gateway set
- not "Block private networks" checked
If that is ok, check all the interface settings on all involved devices. Ensure that the mask is set correctly, and the default gateway is set to the respective IP stated above.
@Viki-R said in Routing configuration issue between 3 interfaces on pfsense (New to pfsense):
we only have Win 10 desktops where windows firewall is off.
Check that twice to be sure.
-
@viragomann said in Routing configuration issue between 3 interfaces on pfsense (New to pfsense):
Check that twice to be sure.
Than check it again... Your lan rules are by default any any so if you did not mess with that, then any devices on the lan would be able to talk any device on either of your 2 networks with no rules even on those interfaces.
So as long as the device in the other vlans is pointing back to pfsense as its gateway.. Its most likely the devices firewall, or other security software on it that you didn't disable..
Simple test can device in nework A ping pfsense IPs you have listed there 10.1.2.1 and 10.1.3.1 from the 10.1.1.0 network..
If so simple do a sniff on pfsense say on network B interface - while you ping something network be at 10.1.2.x -- do you see the ping go out from pfsense.. If so then its not pfsense..
Here example..
My lan rules.
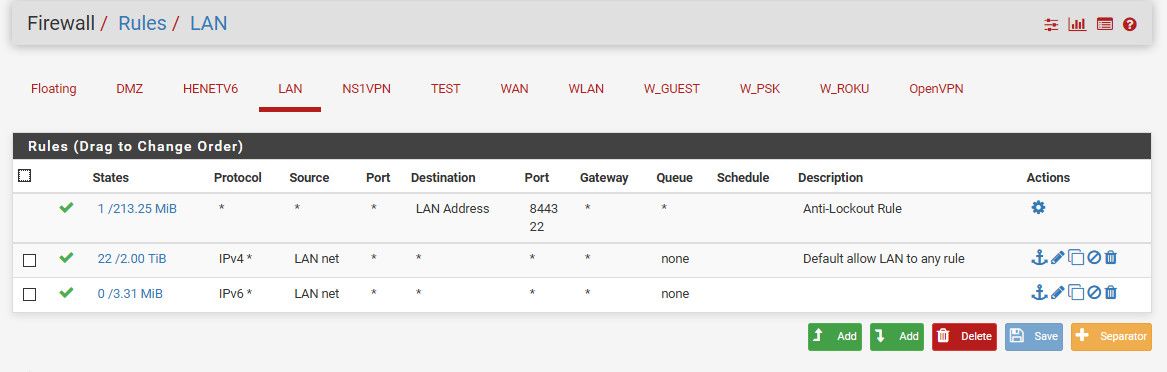
My lan is 192.168.9.0/24, pfsense IP is 192.168.9.253
Another segment of mine (dmz) is 192.168.3.0/24 where pfsense IP in that is 192.168.3.253I can ping 192.168.3.253 from my 192.168.9.100 box.
$ ping 192.168.3.253 Pinging 192.168.3.253 with 32 bytes of data: Reply from 192.168.3.253: bytes=32 time<1ms TTL=64 Reply from 192.168.3.253: bytes=32 time<1ms TTL=64Here is sniff of that 192.168.3.253 interface only for stuff going to 192.168.3.10 while I ping that ip
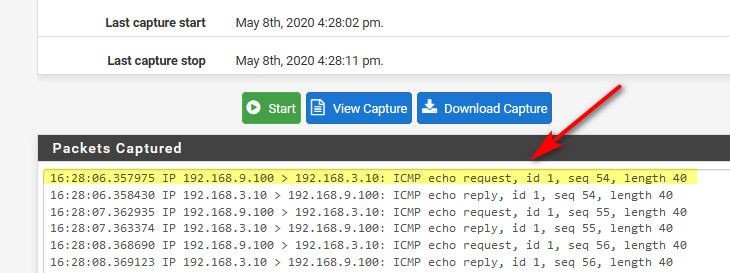
So you see the ping go out, and in my case get a response... Do you see ping request go out.. Make sure your sniffing on pfsense B interface, while you ping from A (your lan with rules that are any any)..
Just to be complete - my dmz rules do not allow pinging anything in my other networks.
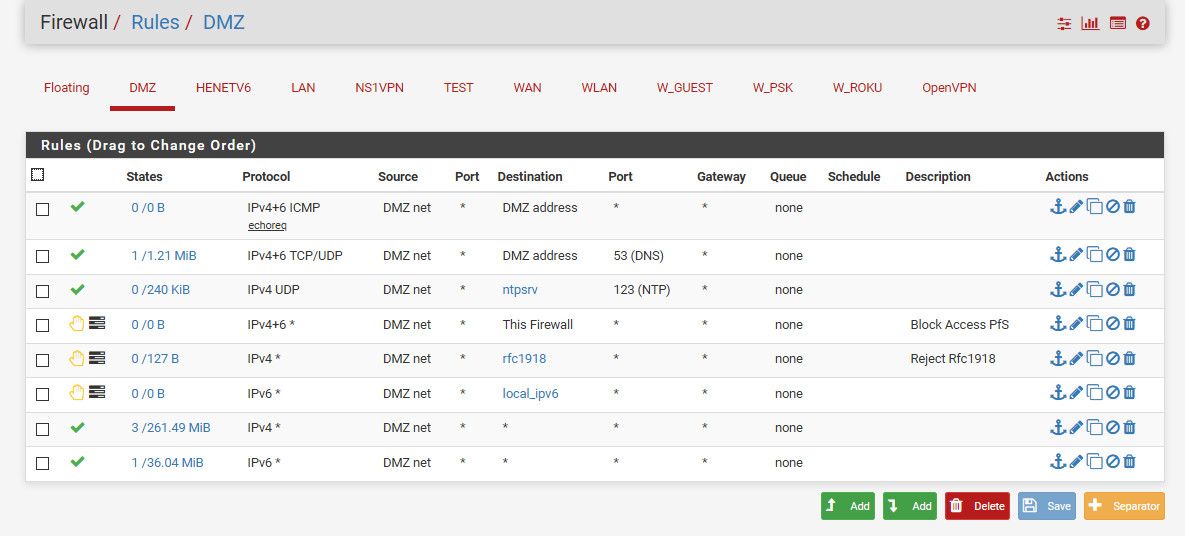
So while something in my dmz can ping pfs IP 192.168.3.253, can not ping pfsense IP say 192.168.9.253
root@pi-hole:/home/pi# ping 192.168.3.253 PING 192.168.3.253 (192.168.3.253) 56(84) bytes of data. 64 bytes from 192.168.3.253: icmp_seq=1 ttl=64 time=0.653 ms 64 bytes from 192.168.3.253: icmp_seq=2 ttl=64 time=0.497 msTrying to ping 192.168.9.253 just fails..
root@pi-hole:/home/pi# ping 192.168.9.253 PING 192.168.9.253 (192.168.9.253) 56(84) bytes of data. ^C --- 192.168.9.253 ping statistics --- 10 packets transmitted, 0 received, 100% packet loss, time 9350ms