SNORT blocking too much
-
@interessierter said in SNORT blocking too much:
I have googled more than one time, the only point that I found was this thread. But I have not searched in this forum. Will do that.
Most home users have no need of the Snort or Suricata packages. These are very complex packages that require a thorough understanding of network security, network technical theory and how various threats are detected. Snort and Suricata are NOT like an anti-virus package that you can just install and configure the virus definitions (rules) to update periodically.
There is no cookie-cutter approach to configuring an IDS/IPS. If it is giving you troubles that you can't solve, simply uninstall the package. As I mentioned in the first paragraph, most home users do not need it.
If you want to learn about Snort, then Google is your friend, but don't go looking for "how can I do X" or "how can I stop Snort from blocking Netflix". Instead, look for articles, whitepapers and tutorials explaining how an IDS (Intrusion Detection System) works. There are tons and tons of things on the web about Snort. Snort has been around as an IDS for like forever basically. You will need to learn how an IDS actually works, then you will begin to understand its configuration and how to use it and tune it for optimum performance in your network.
-
I have tried to setup snort like here mentioned: https://docs.netgate.com/pfsense/en/latest/ids-ips/setup-snort-package.html
What I want to archive is, that I see in the alerts section more meaning full information like on the screenshots at the end of the side (facebook, icloud ect)I have my list with alerts, but this additional usefull info missing. why?
-
@interessierter said in SNORT blocking too much:
I have tried to setup snort like here mentioned: https://docs.netgate.com/pfsense/en/latest/ids-ips/setup-snort-package.html
What I want to archive is, that I see in the alerts section more meaning full information like on the screenshots at the end of the side (facebook, icloud ect)I have my list with alerts, but this additional usefull info missing. why?
Following your question is difficult due to the translation confusion (I'm guessing English is a second language for you), but it sounds like maybe you need to scroll over to see the Message column on the ALERTS tab. What type of device are you using to view the pfSense GUI screens? If it has a small screen, you will need to scroll over to the right. It could also be that if you choose a non-standard theme that could cause scrolling problems.
A screen capture of what you see on your device would be helpful in order to understand what is missing for you.
-
Jep, I hope it s not too bad.
I m on the last pfsense version, and I use a 34 " screen. Scrolling in "all" directions does not change it. Maybe now you understand, why I was asking for lists to whitelist and help. With only this alerts it s really hard to find "good" traffic!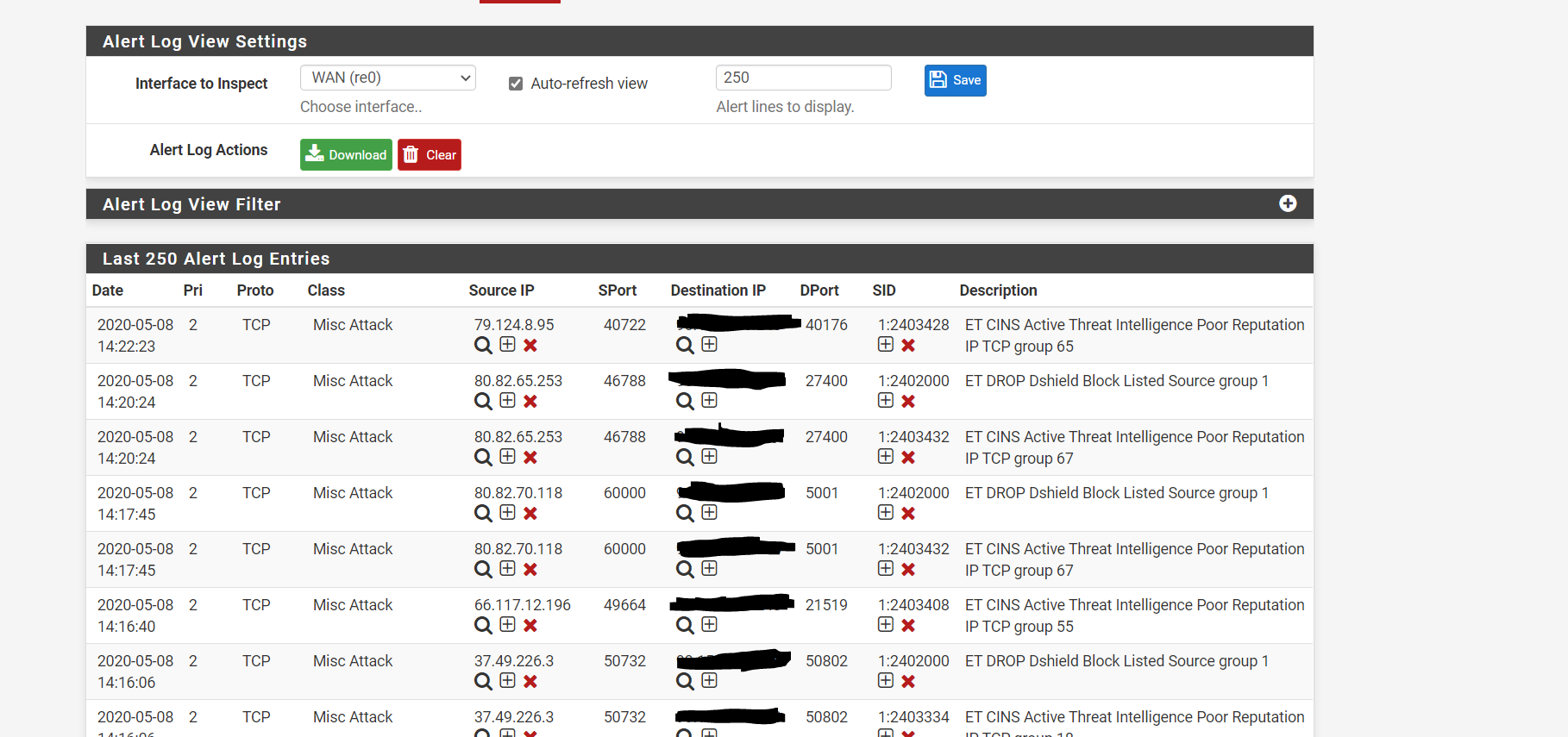
-
@interessierter said in SNORT blocking too much:
Jep, I hope it s not too bad.
I m on the last pfsense version, and I use a 34 " screen. Scrolling in "all" directions does not change it. Maybe now you understand, why I was asking for lists to whitelist and help. With only this alerts it s really hard to find "good" traffic!
I'm sorry, but I completely do not understand what you are asking for. Everything available from the alerting rules log is displayed on that screen. I mistakenly said Message column but the actual name is Description. I thought perhaps you were viewing on a mobile device and that column was scrolled off the screen. This tab shows alerts coming from the rules you have enabled. If you don't enable the rules (and necessary preprocessors), then no alerts can happen from those rules. Again, though, I really don't understand what you are trying to say is missing.
The best guess I can come up with is you are really not experienced in intrusion detection systems, and if that is true, then Snort is not going to be fun for you. You need to learn about the technology first if this is new to you. You will need to learn the Snort rule syntax and then examine the text of triggering rules to determine what they are alerting on. Research on the rules vendor sites can also help. And learning about the technology requires lots of reading and studying on the web, or else take some classes.
-
Please go back the the fololowing URL: https://docs.netgate.com/pfsense/en/latest/ids-ips/setup-snort-package.html
An the end of the article you see the ALERT section as discussed. The only difference is, that on this screenshot you have on the right side a information, that is request was related to Amazon, icloud what ever.For this information I m looking for
-
@interessierter said in SNORT blocking too much:
Please go back the the fololowing URL: https://docs.netgate.com/pfsense/en/latest/ids-ips/setup-snort-package.html
An the end of the article you see the ALERT section as discussed. The only difference is, that on this screenshot you have on the right side a information, that is request was related to Amazon, icloud what ever.For this information I m looking for
Oh, so you don't have the OpenAppID rules enabled? That's where that type of information comes from. Did you follow all of the steps in that article you linked? Sounds like you missed one if you are not seeing OpenAppID alerts (or else there is no traffic on your network matching those rules).
To use OpenAppID you must do four things.
-
On the GLOBAL SETTINGS tab enable the download of the OpenAppID Stub Detectors and the OpenAppID text rules (that's two different checkboxes) and save the change.
-
On the PREPROCESSORS tab for the interface, enable the OpenAppID preprocessor and save the change.
-
On the CATEGORIES tab for the interface, enable the OpenAppID rule categories that you want to use by checking the boxes and then saving the change.
-
Restart Snort on that interface using the GUI icon on the INTERFACES tab.
Note that the OpenAppID rules are not perfect. They were created by a volunteer maintainer in Brazil and are hosted by the pfSense team's infrastructure. I don't believe the maintainer has updated them in a while, so that means there is likely some types of traffic they will miss.
Finally, a last warning, if you turn on OpenAppID rule blocking your life will be miserable if folks on your network routinely use social media and streaming apps. That's the type of traffic those rules are designed to detect and usually block. The rules are really designed for corporate enterprise networks where the management does not want the workers wasting work time on social media.
Your question seems to have wandered from "snort is blocking too much" to "I want to see more info". If your original problem is Snort is blocking too much, then turning on OpenAppID is going to make it a whole lot worse! I suspect your real issue is several of the HTTP_INSPECT preprocessor rules are causing you grief when you have blocking enabled. Read through this very long thread to see some examples from more experienced users showing which rules are typically disabled: https://forum.netgate.com/topic/50708/suricata-snort-master-sid-disablesid-conf.
-
-
I have followed exactly the guide and also for steps, all is set like you mentioned. I miss still this information
-
@interessierter said in SNORT blocking too much:
I have followed exactly the guide and also for steps, all is set like you mentioned. I miss still this information
Then you don't have traffic matching those rules in your network. Remember I said the rules will not detect everything because they are not actively maintained by the original author.
Go back and read my additional comments at the end of my post above and follow that link I included.
-
Hi!
I don t believe that. First of all the table is simply missing in my view. And I expect that the rules now amazon, Netflix, O365 whatever. I have simply nothing. Yes I will review the Blog.
PS: The thread is from 2017, thats the reason why the first ask is not 100% match the last one
thanks
-
@interessierter said in SNORT blocking too much:
Hi!
I don t believe that. First of all the table is simply missing in my view. And I expect that the rules now amazon, Netflix, O365 whatever. I have simply nothing. Yes I will review the Blog.
PS: The thread is from 2017, thats the reason why the first ask is not 100% match the last one
thanks
What table is missing from your view, and where (which tab)?
If you are talking about that very last graphic on the page, that is not an actual table in the application. The person creating that article just cut and then pasted individual alert lines from the regular ALERTS tab entries and then put them in separate sections for illustration. There is not and never was a table in Snort formatted that way.
Is this what you think is missing? This is not a real table in Snort. This was created by the author of the documentation article for illustration purposes.
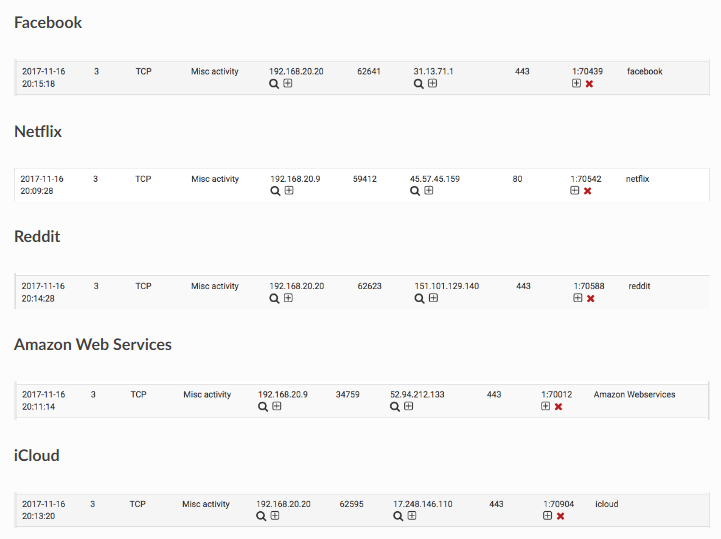
To help you find stuff on the ALERTS tab, several of the columns are sortable. Click the column headers to sort on that field. Where you see "facebook", "reddit" and other values in the screenshot above, look for those under the Description column of the ALERTS tab. As I mentioned, the image in the documentation was created by copying just a single line from the ALERTS tab view in the pfSense GUI. So each of the little light-gray background boxes in the image is a cut-and-pasted single line entry from the ALERTS tab.
-
I have spent three years so far learning IDS/IPS ... from being a neophyte implementing all rules to where I am today ... and guess what, I am still learning. It a never ending process ... one cannot simply install the package, have some ice cream, and forget about it. Right now, Suricata's STREAM excessive retransmissions is pulling my hair.
-
I have no started to whitelist all my topics, now its working. Sometimes the performance is not the best.
However how is than a big company doing that? There are always changes in the infrastructure and applications, the users start very often different clients to use. Can not believe that there is always one guy sitting the entire day to whitelist parts of the connections. Thats way I was asking for pattern file to whiteliste "defaults"
-
@interessierter said in SNORT blocking too much:
Can not believe that there is always one guy sitting the entire day to whitelist parts of the connections.
That's why others told you to turn off blocking so you can sort out your network need. It seems that you also had enabled all rules then started complaining ... not cool!
-
@interessierter said in SNORT blocking too much:
However how is than a big company doing that?
Mostly by actually paying some guys in a corner that's maintaining the lists. Not knowing that that guys exists gives the impression security is for free. But the one who makes the pay checks knows better.
Or, as usual, by paying monthly fees to have have access to well maintained feeds.edit : it's most probably a combination of the two options mentioned above.
-
Guys please stop this.
I m working in the IT area since more than 10 years +. I have not the impression that security is for free, and I also didn t expected that I install it and take ice cream or what ever.When I m a company with 100.000 employee s it get hard to "know" my traffic. Because of that, I was expecting that there are pattern available that allow the minimum of default traffic like normal webpages. When the snort rules gets sold to enterprise customers, than I was expecting here a bit more.
Good, it seems like that is here, and in Snort not the case. Sowe can close the thread. The rest of the posts does not help here
-
@interessierter said in SNORT blocking too much:
Guys please stop this.
Not meant to be personal ^^
Didn't know what you know, but now I get the picture.@interessierter said in SNORT blocking too much:
When I m a company with 100.000 employee s it get hard to "know" my traffic
The easy one : that corner guy exists !!!
But ok, serious : as you said "100 000" means a totally random bit stream is what snort will be seeing.
DPI became already quiet impossible then : TLS killed the access real to the data payload years. A solution that still might pull it off : Use a proxy on/in front of your snort device, have it "unpacked" all traffic, scan, and pack it back into TLS again.
This proxy device would be situated on pfSense, but in front of it. Centralized administration of all devices in the network would be needed to handle the 'cert' issues.For a small group of persons (small society or even family) it's actually possible to find some common patterns, but a huge group will always trigger some (random) pattern/rule. You're talking of several OS's - thousands of application, that can all have there "network errors", that might trigger some rule.
Keep in mind : snort is somewhat limited to the packet headers, or "headers in headers" and some transport flags. It's like reading a postal envelop, and drawing a conclusion when seeing the destination and sender, and the type of letter, and their occurrence.Btw : for purely learning how DPI works, I've been using snort and friends for some years in the past. It became a close to 7/7 daily job to maintain traffic flowing. And I was using the rules accessible by subscription.
I'm still using it (DPI) today, on my mail server, as that one still 'sees' the traffic 'in clear' in the mail boxes.IMHO : I lost somewhat of the faith in the usefulness of DPI as it exists today. It's goes totally against the all TLS hype.
@interessierter said in SNORT blocking too much:
When the snort rules gets sold to enterprise customers, than I was expecting here a bit more.
Rule support should be found there where they are created ;)