VPN Woes..
-
Hi.
I'm new to pfSense but not to firewalls, but here goes.
I've just purchased an old Watchguard XTM5 from ebay, pimped it with 2GB ram, E5700 controller and a 120GB SSD,
.
Installation was no problem, got it talking to my PPPOE and Virgin providers, but I have one problem with IPSEC VPN.I have the tunnel established and traffic flowing from one side to the other (I can reliably RDP and PING), but, there is a problem with Windows processing group policy (when a user logs on to a PC / Server which is at the other end of the tunnel from the domain controller).
Also, when I try to push Hyper-V replication traffic through the tunnel (I'm using Active Directory Krebros Auth here), I can get them to communicate but the replication fails at the traffic send / authentication part.
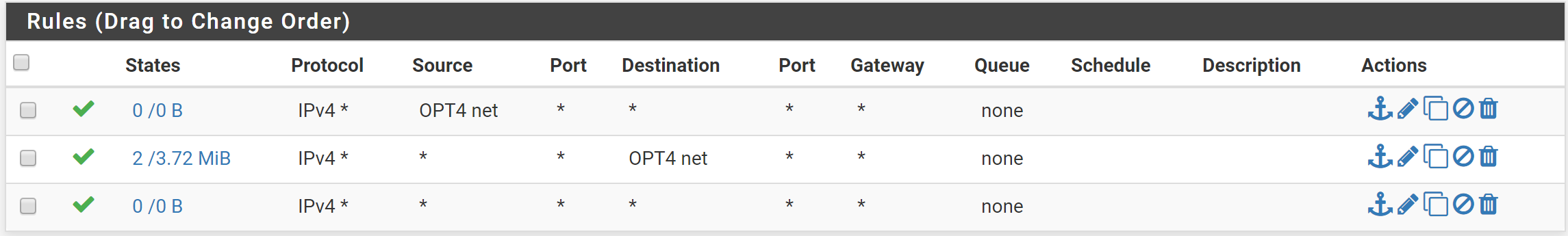
I have setup IP Sec Rules in the firewall as below...
I know this is overkill as the lowest ruls should take care of it, but I am confused by how the rules work in pfSense.
Any advice as to why this is failing would be appreciated as well as how the firewall rules work in the software. Links for basic stuff for me to read would be cool as well as I've done a lot of googling and this should just "work", but it sort of is, but isn't!
I use Watchguards (and an old XTM330 is what I currently have in place and am looking to use pfSense to replace), so am not a 100% noob, but looking to get my head round this!
Cheers in advance,
BigDaddyCainer.
-
For docs, try the book: https://www.netgate.com/docs/pfsense/book/
On your IPsec tab, the traffic is incoming from the other site, so as you can see, it's matching your OPT4 net. I'd guess that's what the p2 matches. The rules are first match, then exit. Not sure about the replication- maybe a mismatch with the other side?, mtu? -
It's all a bit strange to be honest.
The two sites are on 160.0.0.0 / 16 and my pfSense is on 192.168.88.0/24.
The tunnel comes up no problem, and these rules seem to work, but it's just the traffic. 192.168.88.0 is a VLAN which I have on em3 as the master interface. This is then plugged into an HP 1810-24g with the latest firmware.
The port on this switch is marked as tagged for this VLAN and has another port specified as untagged which the member server / ws is plugged into.
Ping works fine, it's just any other data which causes an issue. I'll look at frame size, but it's very strange.
Any issues running pfSense on old XTM boxes? I'm running 2.4.5 and it just doesn't seem "right", if that makes sense.
Anything you guys can suggest ?
Cheers,
-
@bigdaddycainer
2.4.5 has serious issues for many installation with multi core CPUs. If you hare experiencing lagging, poor internet performance, high CPU, this could be all due to a serious underlying issue in FreeBSD 2.4.5 uncovered.2.4.5-p1 is now actively being worked on (I'm not pfSense team, I could only speculate a release date, which I won't do)
See thread;
https://forum.netgate.com/topic/149595/2-4-5-a-20200110-1421-and-earlier-high-cpu-usage-from-pfctl/65 -
Still some work to do. :-)
https://redmine.pfsense.org/projects/pfsense/roadmap#2.4.5-p1-Rico
-
Right.
So after tearing out what little hair I had, I found the answer to this.
Did some wiresharking and it appeared that anything other than a ping was resulting in the servers not being able to "acknowledge" each other.
It just smelled of "not enough room in the packet" to me. So, manually set the limit on the PPPoE interface to 1500 and then, everything started to work!
(Oh, also wiped config and downgraded to 2.4.4 which seems a lot more stable).
Thanks for all the feedback - Appreciated.
-
@Rico
We are having issues with a normally perfect openvpn setup since upgrading to 2.4.5.
VPN tunnel latency is floating between previous latency (normal av) to 300% or more
with 2.4.5 install on pfsense vpn server and a linux vpn server,the same result is evidient.Tried changing link mtu and tun mtu with no stability changes.
Seems to be mtu related as the mtu dynamic config bit on the client appears to be now
enabled and maybe some new openvpn options ?? (will check for new manual) ,this is mentioned in the openvpn debug logs.Looks like a regress to 2.4.4
Any light to shed on this new issue ? or suggestions.
Thankyou all.
-
Hi.
I went back to 2.4.4 to get everything working - 2.4.5, just didn't "smell" right. I have also read that there are a lot of issues with dual processor cores in 2.4.5.
My VPN was site to site using IPSec and to get it to work, I manually set the 1500MTU on the WAN interface for my PPPoE connection, which cured the data flow issue. Tunnel would always come up under with the MTU set to auto, but any high flow of data clagged it.
If all was working under 2.4.4, it might be worth going back to that version. I won't be upgrading to 2.4.5 until some of the bugs have been ironed out.
Have had PFSense installed for a couple of months now and it works very, very well.
Allows for re-use of otherwise redundant hardware!
Cheers.
-
Yes i agree ,regression is the answer,unfortunately and painfully,hope i kept the old gz or iso
as pfsense arent in the habit ( like they previosuly did) of visually indexing the links to each version,like
they previously did!!.I knew i shouldnt have done this as per past experience ,tis best to wait for the 2nd rev on a new release.
Cheers