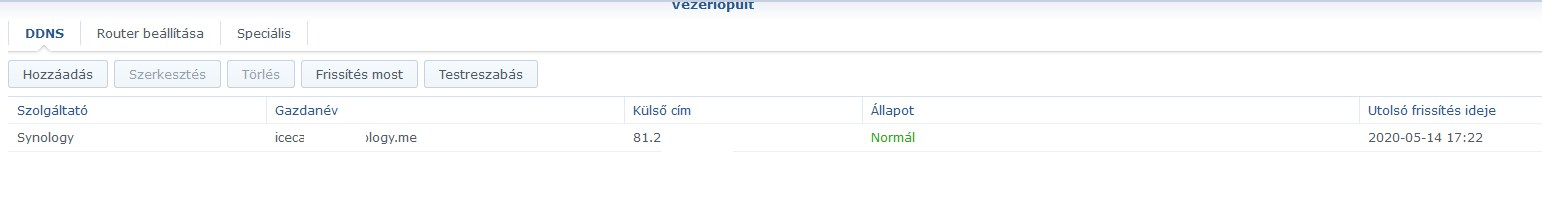
Synology DDNS not work
-
Synology behind pfSense is a strange animal pairing, but it works if you consider a few things.
https://www.synology.com/en-global/knowledgebase/DSM/tutorial/Network/What_network_ports_are_used_by_Synology_servicesTo use Synology DDNS, you need port forward to port 443
Since Synology uses CDN worldwide, make sure your Synology account is active in this menu.
-
what I forgot:

in many cases it may be necessary and I suggest that:
https://www.synology.com/en-global/knowledgebase/DSM/help/DSM/AdminCenter/connection_certificate -
Just did certificate.
Synology working fine when i connect it directly to router\modem. Only when i connect it behind Pfsense i cannot use xxx.synology.meJust tried to forward port 443 but nothing change
-
This is perfectly normal since pfSense is a firewall, not a SOHO router.
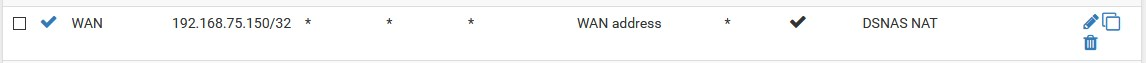
Try this trick, more of our Synology NAS works this way:hybrid outbound NAT for Syno
if Synology can't reach its own CDN network, it can't do a lot of things, can't update packages, or antivirus package, for example....
(this is a known problem or Synology wants just that)Above you mentioned you're trying to connect on http, That's why I suggested https + Let'sEnc / this can be seen in the linked description that it is also required for the DDNS provided by Synology, as it is Synology's own service, i.e. CDN .....
-
Don't forget, if you are also running IPS / IDS or pfBlockerNG, keep an eye on the logs for what is preventing the NAS from accessing your own CDN network.
This will be clearly visible in the logs....(jahhh and it varies from country to country and region to region.
Synology tech support couldn’t even give me an IP range (for country CDN) when I first encountered this problem.)
-
Ok seems snort blocked my public IP.
I quit snort and now, as before, i can reach Nas typing https://name.synology.me/5001or http://name.synology.5000. If i try with name.synology.me give me error 403
-
This is not very good, if your Snort config have blocked the WAN public IP because it means it is misconfigured...
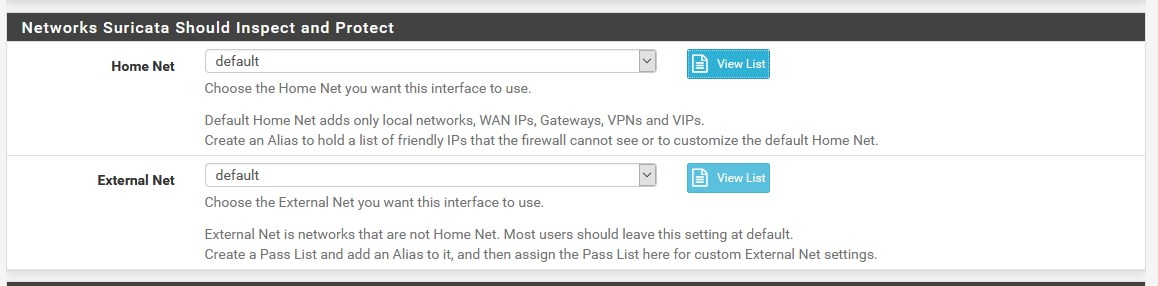
This parameter is important to Snort / Suricata (this setting does not allow blocking of WAN IP + gateways, DNS servers, etc.):
Yes, yes the DSM port (5000 or 5001) is also important in the connection header

-
Check, Snort parameters are on default for each two voices
-
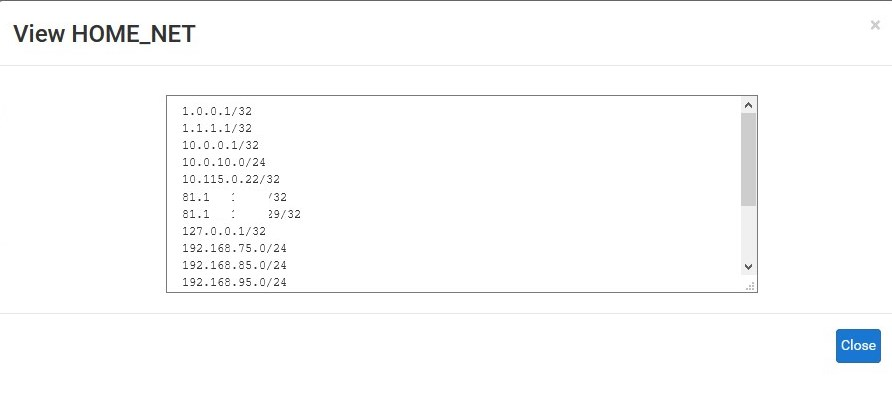
What does the View List show?
and

-
No data here
-
Then this is exactly the problem with the basic configuration, you have to think through where you made a mistake during the installation.
Only based on these parameters does the firewall know who is inside and who is outside (and who shall not be harmed), so the entire firewall is malfunctioning. -
One problem is solved, the firewall in my modem was still active and blocked port 80
 now i can connect to nas via web using name.synology.me
now i can connect to nas via web using name.synology.meAbout snort how i can solve the problem? Do you suggest to unistall and reinstall snort?
-
It may be a good start at first,
since IPS / IDS works based on $ HOME_NET and $ EXTERNAL_NET, as shown here, for example the structure of a rule is such:
but I suspect there are several problems with NGFW configuration, interfaces, DNS setup, etc
-
For security reasons only, external http (80) connections are not appropriate, especially for a NAS, use https, if you want to access the NAS remotely.
Or use Syno's built-in OpenVPN package for external access