Pfsense WireGuard Client Working ( With Catch 22 )
-
you should not take it personally, johnpoz is like that, you can teach english, he can teach networking and security, people will read your tutorial and try to mimic it, if they do something wrong it may be dangerous for a firewall or it could interfere with future updates, alot of thing can go wrong. it's the duty of a moderator to advise against stuff like this, if you want something to be officially added to pfsense you should go to redmine.pfsense.org and ask for a new feature. that said if someone is interested in your work no one will prevent him from following it. provided they understand that they do so at their own risk.
The protocol called DNS over TLS run on port 853, network operators that dislike DoT can easily block it. Most corporate networks will in fact do this by default, then we have all the other stuff like doh doc
It is generally possible to tell where a TLS connection is going even without looking at DNS since the name still travels in plaintext.. there is little/no privacy differential when using DNS over HTTPS
if it's your concern. the request will be in any case decrypted by the dns you query. so moving your personal information from your ISP to google IMHO it's bullshit, an excess of privacy. the other reason to have DNS over HTTPS / TOR it's to break the censorship in your country so you are free to search for all that illegal stuff / censored pornography that your country impose. i really don't think any of this have anything to do with a product of a certain seriousness that points to security.
this is only my 2cents -
@kiokoman
Dear kiokoman,
I opened my reply to johnpoz by stating that I do understand and accept the validity of your comments and criticisms of " hacking " pfSense FireWall. Further I ended with I can assure you that I will not post any additional " hacking " solutions on the pfSense Forum. On the topic of DNS OVER TLS - you can also run that protocol on Port 443 as many of the providers here from The DNS PRIVACY Project : https://dnsprivacy.org/jenkins/job/dnsprivacy-monitoring/ - offer DNS TLS on port 443. Also, DNS OVER TLS is suggested to be run in conjunction with a secure VPN service. Again, thank you and johnpoz and I will be a good team player
Peace
ubernupe -
-
The shellcmd utility is used to manage commands on system startup.
i suggest to take a look to this package, you can put that script inside shellcmd, this way it will survive even after an upgrade of pfsense -
@kiokoman
Dear @kiokoman,
Hello and I hope that you are safe and well in these times. I am writing to ask you if you would be so kind as to provide the correct manner to enter this solution listed above :vi /etc/pfSense-rc
/usr/local/etc/rc.d/wireguard.sh start 2>/dev/null
to shellcmd utility - so that WG0 survives ( will survive even after an upgrade of pfsense )
To be clear - I am asking for the exact entry and type - thanks
Peace
-
Hi, I got it working fine until I wanted to change config in: /usr/local/etc/wireguard/wg0.conf to other server details.. when I have updated the config and use command: wg-quick down wg0 and then wg-quick up wg0, the internet just stops working... do I need to change some other places or restart something else in order to load new wireguard server config ? And seems like battle.net games aint working, need to use another wireguard vpn on windows in order get it working so seems like the NAT is not working right ?
-
@ubernupe i don't have wireguard installed but i suppose that something like this should work
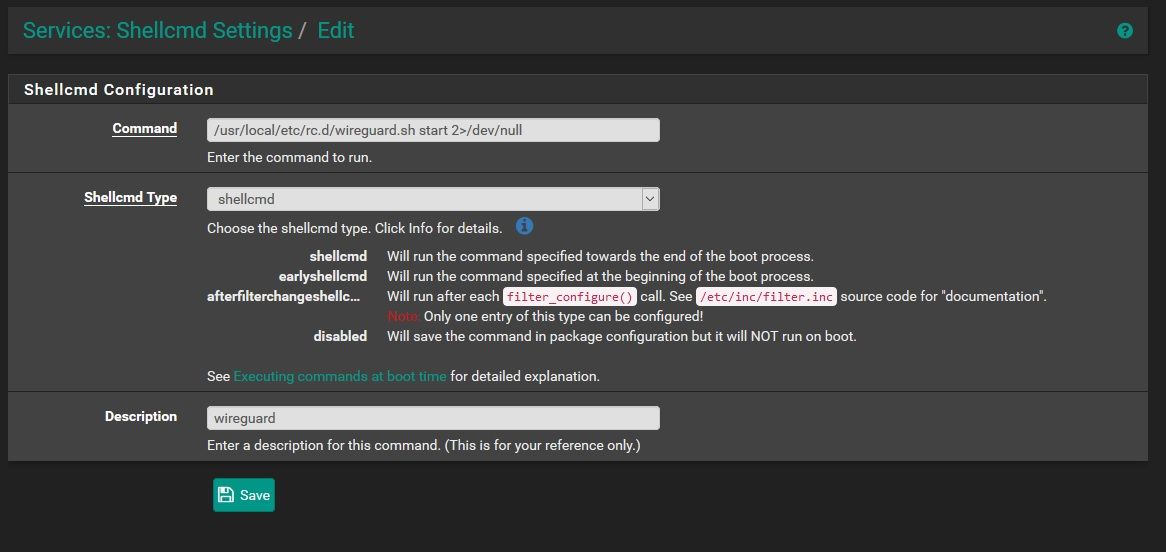
-
Dear @kiokoman,
Hello and thanks for the advice.I tried your suggestion - and that does not work ( at least on a test VMWare Machine ) - maybe it will work on real hardware. I am going to try earlyshellcmd and see how that works. Adding the line /usr/local/etc/rc.d/wireguard.sh start 2>/dev/null
works fine. However I am running 2.5.0 Development Snapshot - so I really hope that someone here can help me out when it comes to using proper shellcmd utility entry. anyway, thanks - and I do appreciate your assitance andreply. Stay Safe -God Bless You and Yours Always In Peace and Grace,
-
Hey all,
Having had a bit more time at home to play with my configs, I figured I'd kick in some observations:
-
The most important thing here is that one should acknowledge that this is definitely a hackjob at present. None of the netgate people are in the slightest responsible if your setup catches fire, nor should they be. But, if you want to play with something that's the "new hotness" before it (hopefully) becomes a kernel addition for BSD and integrated into pfsense some day (sounds like this may be in progress), go for it! Hacking up your home router is a rite of passage for some. Maybe don't do this to your production pfsense box, though.
-
My pfsense box is in a closet and is headless. Having a "missing interface" prompt is not something I would want (having had it happen before). Nobody wants to have to go over with a serial cable or monitor to kick their router over to get internet. Having said that, the trick to fixing this involves renaming your wireguard interface to one of the interfaces that pfsense skips on boot. For example, if you rename your interface to, say, ovpns2 (with ovpns2.conf), it'll skip looking for it on boot and allow you to manually start. Again, very hacky and not intended, but it works.
-
As much as I love the shellcmd utility and recommend it over manual edits, there's a slight issue with when it fires in the boot order. I can't remember as I set it aside a while ago, but I think the issue is that you'll have to make it count to 10 (or more likely 300) before it tries bringing up wireguard as otherwise it hangs when nothing is ready on boot yet. Might be worth trying it with the interface renaming scheme above.
-
Calling a user's contributions "an utter waste of time" is disappointing to see from anyone, let alone a position of authority. Being critical and being dismissive are two different things. Just my .02 as a person.
-
-
@ravenium
Dear ravenium,
My man - I hope that you are well and safe in these days and times. Thanks for your thoughtful and measured contribution and observations regarding the specific issue here and your philosophy about " hacking " pfSense in general. I am the OP ( in case you don't know ) - and you are obviously an erudite thinker - and once again - I for one greatly appreciated your .02 as a person
Later my brother - Peace and God Bless You and Yours Always in God's GracePS - I will try your proposed solution as stated here in # 1 of your reply ( just for sh*t and giggles ) - and thanks for that one more again