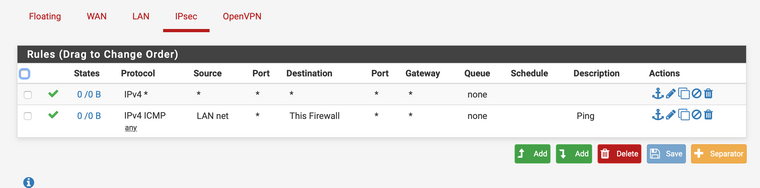
Маршрутизация клиента OpenVPN в две сети IPSec
-
May 20 23:25:38 ipsec_starter 4358 Starting strongSwan 5.8.2 IPsec [starter]... May 20 23:25:38 charon 00[DMN] Starting IKE charon daemon (strongSwan 5.8.2, FreeBSD 11.3-STABLE, amd64) May 20 23:25:38 charon 00[KNL] unable to set UDP_ENCAP: Invalid argument May 20 23:25:38 charon 00[NET] enabling UDP decapsulation for IPv6 on port 4500 failed May 20 23:25:38 charon 00[CFG] loading unbound resolver config from '/etc/resolv.conf' May 20 23:25:38 charon 00[CFG] loading unbound trust anchors from '/usr/local/etc/ipsec.d/dnssec.keys' May 20 23:25:38 charon 00[CFG] ipseckey plugin is disabled May 20 23:25:38 charon 00[CFG] loading ca certificates from '/usr/local/etc/ipsec.d/cacerts' May 20 23:25:38 charon 00[CFG] loading aa certificates from '/usr/local/etc/ipsec.d/aacerts' May 20 23:25:38 charon 00[CFG] loading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts' May 20 23:25:38 charon 00[CFG] loading attribute certificates from '/usr/local/etc/ipsec.d/acerts' May 20 23:25:38 charon 00[CFG] loading crls from '/usr/local/etc/ipsec.d/crls' May 20 23:25:38 charon 00[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets' May 20 23:25:38 charon 00[CFG] loaded IKE secret for %any 1.1.1.2 May 20 23:25:38 charon 00[CFG] loaded IKE secret for 1 May 20 23:25:38 charon 00[CFG] opening triplet file /usr/local/etc/ipsec.d/triplets.dat failed: No such file or directory May 20 23:25:38 charon 00[CFG] loaded 0 RADIUS server configurations May 20 23:25:38 charon 00[LIB] loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac drbg curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap xauth-pam whitelist addrblock counters May 20 23:25:38 charon 00[JOB] spawning 16 worker threads May 20 23:25:38 ipsec_starter 4787 charon (4926) started after 20 ms May 20 23:25:38 charon 16[CFG] received stroke: add connection 'bypasslan' May 20 23:25:38 charon 16[CFG] conn bypasslan May 20 23:25:38 charon 16[CFG] left=%any May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] right=%any May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] dpddelay=30 May 20 23:25:38 charon 16[CFG] dpdtimeout=150 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] added configuration 'bypasslan' May 20 23:25:38 charon 13[CFG] received stroke: route 'bypasslan' May 20 23:25:38 ipsec_starter 4787 'bypasslan' shunt PASS policy installed May 20 23:25:38 charon 16[CFG] received stroke: add connection 'con1000' May 20 23:25:38 charon 16[CFG] conn con1000 May 20 23:25:38 charon 16[CFG] left=1.1.1.1 May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] leftauth=psk May 20 23:25:38 charon 16[CFG] leftid=1.1.1.1 May 20 23:25:38 charon 16[CFG] right=shop.domen.ru May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.1.0/24 May 20 23:25:38 charon 16[CFG] rightauth=psk May 20 23:25:38 charon 16[CFG] rightid=1.1.1.2 May 20 23:25:38 charon 16[CFG] ike=aes256-sha1-modp1024! May 20 23:25:38 charon 16[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 23:25:38 charon 16[CFG] dpddelay=10 May 20 23:25:38 charon 16[CFG] dpdtimeout=60 May 20 23:25:38 charon 16[CFG] dpdaction=3 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] keyexchange=ikev1 May 20 23:25:38 charon 16[CFG] added configuration 'con1000' May 20 23:25:38 charon 13[CFG] received stroke: route 'con1000' May 20 23:25:38 charon 13[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 13[CHD] CHILD_SA con1000{1} state change: CREATED => ROUTED May 20 23:25:38 ipsec_starter 4787 'con1000' routed May 20 23:25:38 charon 16[CFG] received stroke: add connection 'con1001' May 20 23:25:38 charon 16[CFG] conn con1001 May 20 23:25:38 charon 16[CFG] left=1.1.1.1 May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.192.0/24 May 20 23:25:38 charon 16[CFG] leftauth=psk May 20 23:25:38 charon 16[CFG] leftid=1.1.1.1 May 20 23:25:38 charon 16[CFG] right=shop.domen.ru May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.1.0/24 May 20 23:25:38 charon 16[CFG] rightauth=psk May 20 23:25:38 charon 16[CFG] rightid=1.1.1.2 May 20 23:25:38 charon 16[CFG] ike=aes256-sha1-modp1024! May 20 23:25:38 charon 16[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 23:25:38 charon 16[CFG] dpddelay=10 May 20 23:25:38 charon 16[CFG] dpdtimeout=60 May 20 23:25:38 charon 16[CFG] dpdaction=3 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] keyexchange=ikev1 May 20 23:25:38 charon 16[CFG] added child to existing configuration 'con1000' May 20 23:25:38 charon 13[CFG] received stroke: route 'con1001' May 20 23:25:38 charon 13[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 13[CHD] CHILD_SA con1001{2} state change: CREATED => ROUTED May 20 23:25:38 ipsec_starter 4787 'con1001' routed May 20 23:25:38 charon 15[KNL] creating acquire job for policy 1.1.1.1/32|/0 === 1.1.1.2/32|/0 with reqid {1} May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_CERT_PRE task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing MAIN_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_CERT_POST task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_NATD task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing QUICK_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_CERT_PRE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating MAIN_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_CERT_POST task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_NATD task May 20 23:25:38 charon 16[IKE] <con1000|1> sending XAuth vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending DPD vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending FRAGMENTATION vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending NAT-T (RFC 3947) vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> initiating Main Mode IKE_SA con1000[1] to 1.1.1.2 May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] state change: CREATED => CONNECTING May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ SA V V V V V ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (180 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (160 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ SA V V V V ] May 20 23:25:38 charon 16[IKE] <con1000|1> received XAuth vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received DPD vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received FRAGMENTATION vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received NAT-T (RFC 3947) vendor ID May 20 23:25:38 charon 16[CFG] <con1000|1> selecting proposal: May 20 23:25:38 charon 16[CFG] <con1000|1> proposal matches May 20 23:25:38 charon 16[CFG] <con1000|1> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[CFG] <con1000|1> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> MAIN_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ KE No NAT-D NAT-D ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (244 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (244 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ] May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> MAIN_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (108 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (76 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ ID HASH ] May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] established between 1.1.1.1[1.1.1.1]...1.1.1.2[1.1.1.2] May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] state change: CONNECTING => ESTABLISHED May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> activating QUICK_MODE task May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> proposing traffic selectors for us: May 20 23:25:38 charon 16[CFG] <con1000|1> 192.168.0.0/24|/0 May 20 23:25:38 charon 16[CFG] <con1000|1> proposing traffic selectors for other: May 20 23:25:38 charon 16[CFG] <con1000|1> 192.168.1.0/24|/0 May 20 23:25:38 charon 16[ENC] <con1000|1> generating QUICK_MODE request 2775791088 [ HASH SA No ID ID ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (220 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (188 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed QUICK_MODE response 2775791088 [ HASH SA No ID ID ] May 20 23:25:38 charon 16[CFG] <con1000|1> selecting proposal: May 20 23:25:38 charon 16[CFG] <con1000|1> proposal matches May 20 23:25:38 charon 16[CFG] <con1000|1> received proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[IKE] <con1000|1> received 28800s lifetime, configured 0s May 20 23:25:38 charon 16[CHD] <con1000|1> CHILD_SA con1000{3} state change: CREATED => INSTALLING May 20 23:25:38 charon 16[CHD] <con1000|1> using AES_CBC for encryption May 20 23:25:38 charon 16[CHD] <con1000|1> using HMAC_SHA1_96 for integrity May 20 23:25:38 charon 16[CHD] <con1000|1> adding inbound ESP SA May 20 23:25:38 charon 16[CHD] <con1000|1> SPI 0xcf0cb126, src 1.1.1.2 dst 1.1.1.1 May 20 23:25:38 charon 16[CHD] <con1000|1> adding outbound ESP SA May 20 23:25:38 charon 16[CHD] <con1000|1> SPI 0xc32a300a, src 1.1.1.1 dst 1.1.1.2 May 20 23:25:38 charon 16[IKE] <con1000|1> CHILD_SA con1000{3} established with SPIs cf0cb126_i c32a300a_o and TS 192.168.0.0/24|/0 === 192.168.1.0/24|/0 May 20 23:25:38 charon 16[CHD] <con1000|1> CHILD_SA con1000{3} state change: INSTALLING => INSTALLED May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> QUICK_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating QUICK_MODE request 2775791088 [ HASH ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (60 bytes) May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> nothing to initiate May 20 23:25:43 charon 10[CFG] vici client 1 connected May 20 23:25:43 charon 09[CFG] vici client 1 registered for: list-sa May 20 23:25:43 charon 08[CFG] vici client 1 requests: list-sas May 20 23:25:43 charon 09[CFG] vici client 1 disconnected -
@Kowex В настройках фазы 1 есть опция
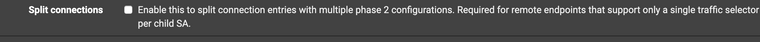
Попробуйте ее отметить с обеих сторон и посмотреть результат
-
@Konstanti странно, но у меня в фазе 1 нет такого параметра.
-
@Kowex В самом низу , Advanced options
-
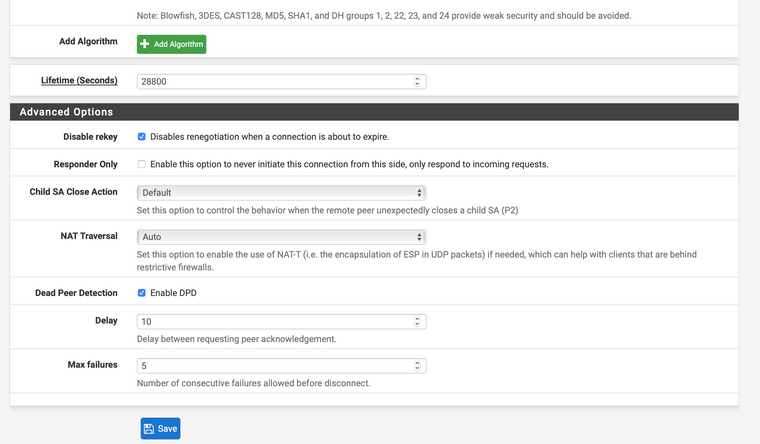
@Konstanti да я уже понял что там должно быть.
-
@Kowex
Поменяйте ikeV1 на ikeV2 -
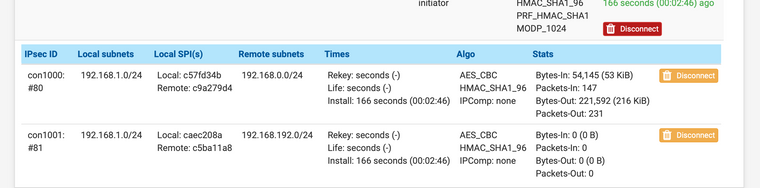
@Konstanti вторая фаза в фазе 2 появилась, но так и не видно сеть сервера 2
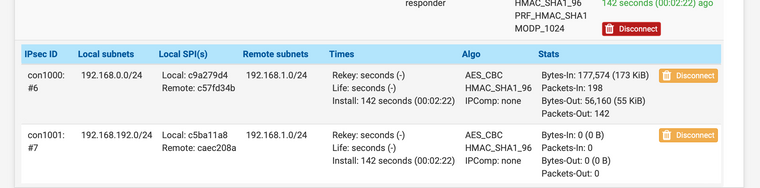
-
@Kowex
Не видно кому и откуда ???
В любом случае - проверьте правила на Ipsec интерфейсе
и если там все нормально , то надо уже подключать Packet Capture и смотреть , что происходит -
-
И после перезагрузки серверов опять пропала вторая фаза из фаз.
Сплит подключения надо галки поставить на обеих серверах? -
@Kowex
Здр
Для начала нужно перейти на IKEv2 и снова смотреть логи , почему не поднимается дополнительная фаза-2. Или все заработало ? -
Добрый.
@Kowex
Когда настроите ipsec + openvpn , то меняйте адресацию в своих сетях. И никогда не пользуйте сети 192.168.(0|1).X в работе. Потому что такая адресация со 100% вероятностью будет у тех, кто вам подключается извне по впн со своих ви-фи "мыльниц". 100500 раз говорено было ( -
@Konstanti Добрый день. Нет не заработало, но фаза вторая поднялась.
-
@Kowex Если поднялась вторая фаза-2 , то запускайте tcpdump и смотрите , где теряются пакеты
-
@werter если стоит такая адресация, значит так и надо и я знаю какие клиенты с какими адресами будут подключаться.
-
@Kowex
Запустите бесконечный пинг со стороны любого клиента , который не работает
и покажите ,для начала , вывод tcpdump на на wan интерфейсах с обеих сторон туннеля
в идеале должно выглядеть вот так[2.4.4-RELEASE][admin@ru.xxxxxx.org]/root: tcpdump -netti igb0 esp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on igb0, link-type EN10MB (Ethernet), capture size 262144 bytes 1590054954.221616 , ethertype IPv4 (0x0800), length 346: 79.1.1.1 > 94.1.1.1: ESP(spi=0xc9790a7d,seq=0x3a79), length 312 1590054954.392088 ethertype IPv4 (0x0800), length 138: 94.1.1.1 > 79.1.1.1: ESP(spi=0xc3f0cd08,seq=0x4e1a), length 104 -
@Konstanti said in Маршрутизация клиента OpenVPN в две сети IPSec:
tcpdump -netti igb0 esp
сервер №1 - WAN
[2.4.5-RELEASE][admin@office.domen.ru]/root: tcpdump -netti re0 esp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on re0, link-type EN10MB (Ethernet), capture size 262144 bytes 1590065560.560319 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e83), length 148 1590065560.560424 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e84), length 148 1590065560.560481 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e85), length 148 1590065570.849217 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e86), length 148 1590065570.849363 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e87), length 148 1590065570.849396 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e88), length 148 1590065580.891418 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e89), length 148 1590065580.891486 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8a), length 148 1590065580.891529 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8b), length 148 1590065620.561597 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8c), length 148 1590065620.561694 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8d), length 148 1590065620.562191 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8e), length 148 1590065630.895852 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e8f), length 148 1590065630.895920 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e90), length 148 1590065630.895961 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e91), length 148 1590065640.897340 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e92), length 148 1590065640.897411 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e93), length 148 1590065640.897454 00:9a:67:33:1b:02 > 6c:1e:d5:11:82:01, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2e94), length 148 -
@Kowex said in Маршрутизация клиента OpenVPN в две сети IPSec:
@werter если стоит такая адресация, значит так и надо и я знаю какие клиенты с какими адресами будут подключаться.
Уверен на 146%, что будет иначе. Дело ваше.
Есть 2 офиса которые между собой объединены IPSec,
Мысль использовать openvpn вместо ipsec для связи между офисами приходила? Овпн и проще и гибче.
-
This post is deleted! -
Сервер №2 - WAN
всё что прошло, больше ничего не было.[2.4.5-RELEASE][admin@shop.domen.ru]/root: tcpdump -netti re1 esp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on re1, link-type EN10MB (Ethernet), capture size 262144 bytes 1590066544.951370 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f16), length 148 1590066544.951398 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f17), length 148 1590066544.951420 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f18), length 148 1590066554.951883 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f19), length 148 1590066554.951975 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f1a), length 148 1590066554.951991 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f1b), length 148 1590066594.434426 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f1c), length 148 1590066594.434461 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f1d), length 148 1590066594.434551 14:6b:1e:2a:a5:03 > 00:9a:67:33:1b:02, ethertype IPv4 (0x0800), length 182: 1.1.1.2 > 1.1.1.1: ESP(spi=0xced89d52,seq=0x2f1e), length 148@werter said in Маршрутизация клиента OpenVPN в две сети IPSec:
Уверен на 146%, что будет иначе.
Вот интересно, откуда такая уверенность? Написал же что я знаю из каких сетей будут клиенты, а вы опять про своё.
@werter said in Маршрутизация клиента OpenVPN в две сети IPSec:
Мысль использовать openvpn вместо ipsec для связи между офисами приходила?
Ну вот в последнее время эта мысль приходит всё чаще. Просто изначально всё было сделано на ipsec, только потом уже прикрутил ovpn.