Internet alias
-
WAN = Internet
-
Thank you for your answer, I saw I was not clear, I meant a system alias to make rules, for example to grant or restrict access to the internet to some device. Not just !LAN, not !RFC_1918, why there wasn't an internet alias to set destination to make a rule.
-
I'm new to pfsense.
You mean like this? Defining alias yourself?
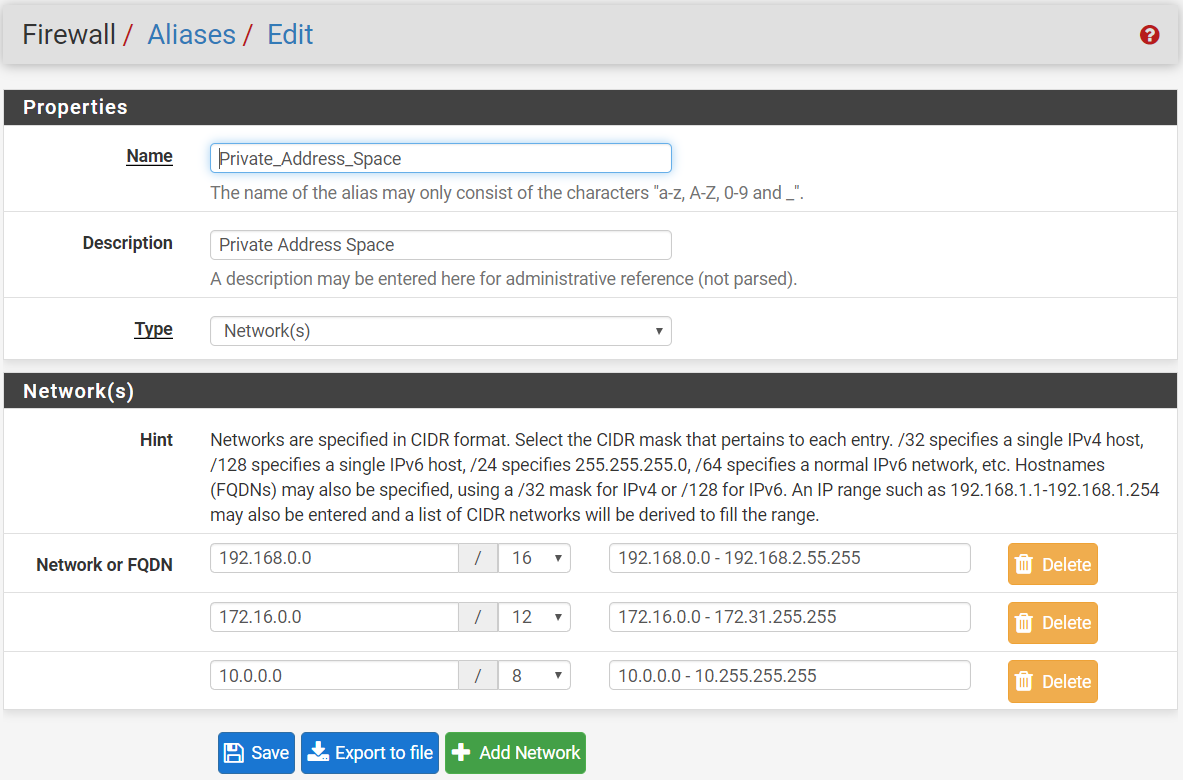
Below is the default rules already defined right after you installed pfsense.
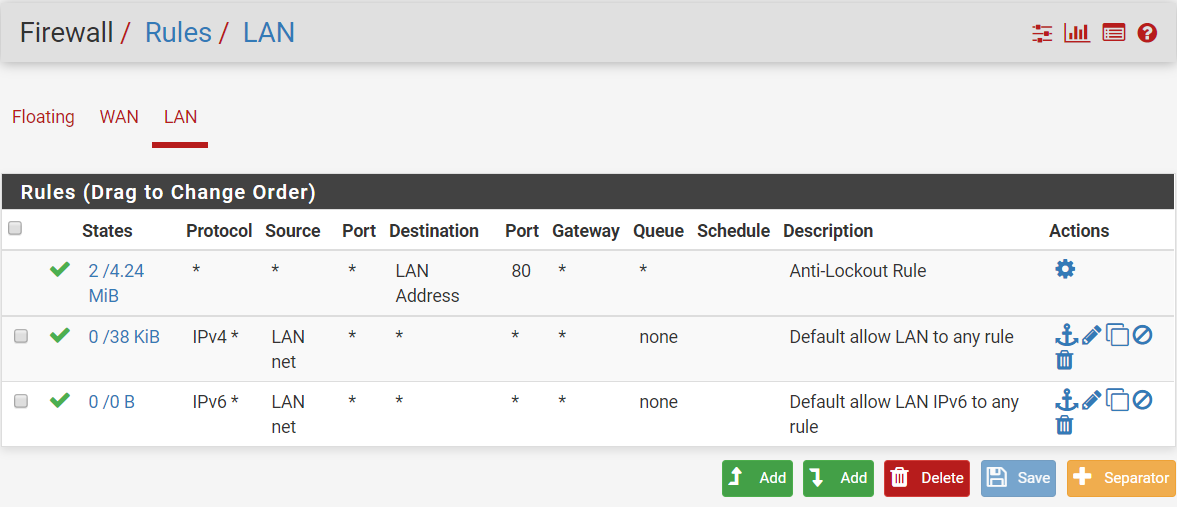
After I created the alias and added to the rules.
-
@maya95 said in Internet alias:
WAN = Internet
No it doesn't.. Wan Net = Wan Net.. The network directly attached to your wan.. Nothing More, Nothing Less.
So why there is not alias.. What you want an alias that contains every possible IP address that is not rfc1918, bogon, multicast, etc. ? What would be the point?
Internet in firewall rule = ANY...
-
@johnpoz Thanks for the clarification!
-
No problem trying to create a alias that contains pretty much all of IPv4 space would be nuts ;)
-
@johnpoz I thought it would be more useful to just have an alias and a pass rule to it, instead of blocking here and there, and then adding a pass rule. For instance, if I have a working setup and some any rules on different interfaces, and in some point I add a new network, I have to remember to block it on all the other interfaces that have that any rule, just to use internet, if I wanted them not to access that new interface.
But yeah, considering the alias size, I think I would overload it a bit... -
If all your interfaces have the same rules, its pretty pointless to have multiple interfaces... But if they are all going to have the same rules.. Just put those rules in floating..
How many networks do you have 1400, so its a pain to manage? I have 8 networks, I fire up new networks all the time and remove others.. I have no idea why you think the possible 2 minutes it would take to setup rules on a new interface would be worth setting up an alias that has x and y in it, an the all of IPv4 space it..
So that you could just pick 1 rule vs say setting up 2 rules maybe 3. What you wan to block, and then your any rule.
If your blocks are common, then create this alias and use it as your block.. Put in all the ports you don't want things to talk to.. And block that, then use your any rule..
Please post up a copy of your rules, and why you think it would be easier to make an alias with all of IPv4 space in it, and how that would save you time vs any.. What would you leave out of this alias specifically..
-
Hello!
I have never used them, but would multiple interfaces with similar base rules be a good spot for interface groups?
"If many interfaces of a similar function are present on the firewall that need practically identical rules, an interface group may be created to add rules to all of the interfaces at the same time. Interfaces can still have their own individual rules, which are processed after the group rules."
https://docs.netgate.com/pfsense/en/latest/book/interfaces/interfacetypes-groups.html?highlight=interface%20group
John
-
And what sort of rules would you put in this group... Keep in mind rules on a network.. Quite a few of them you would want to be specific to that network... Pinging the specific interface for example - so you clients can validate they can actually talk to the gateway.. Maybe use dns to that interface... Sure you could allow dns to this firewall sort of rule..
Or you could use this firewall alias if you don't care if client pings another IP on the firewall..
How best to do the rules would depend on your specific setup and your specific wants and needs for what is allowed and what is not allowed. Do you even know what these are as of now?
If so spell them out, and we can go through how you can do what you want with the min amount of rules. But smallest amount of rules is not always the best case..
Its very handy to put the rules on each interface so you can easy check with simple glance at that interface what that network can do.. Example... Here is a common sort of lock down that you might do for a network.
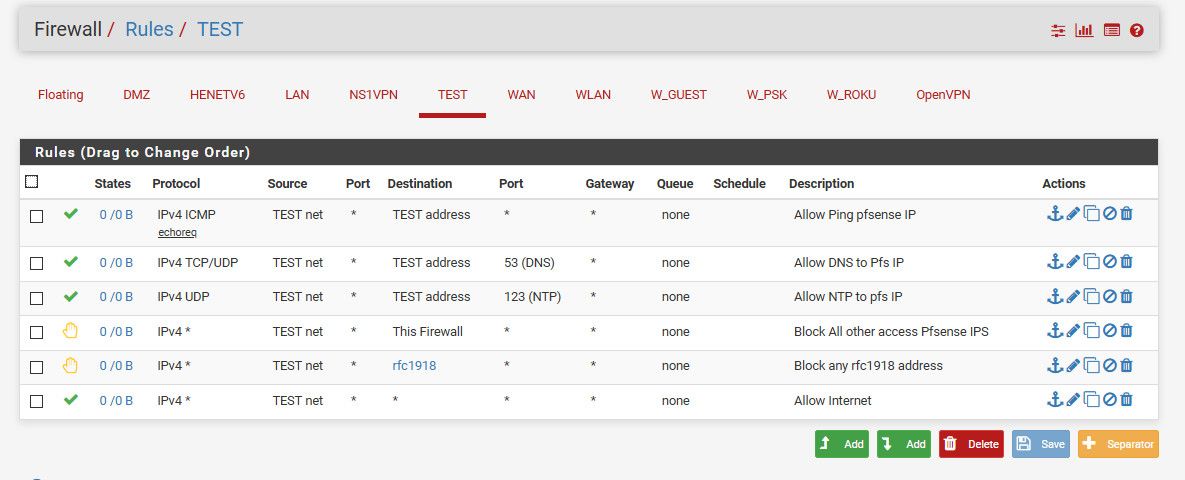
I can look at that, and in seconds understand exactly what this network can an can not do..
It can ping pfsense IP on that network, it can ask it for dns, it can talk to it for ntp.. Any other port it can not talk to the firewall on.. That would be any other vlan, or the wan.. It can not talk to any rfc1918 address - ie any other network at all.. Then anywhere else - Ie the internet, it can do anything it wants.. Those rules take all of like 1 minute to setup.. And are easy and clear and easy to understand. I don't have to check floating tab and look to see if a specific rule as interface X in it.. I don't have to check an interface group..
Here is a group rule... But what interfaces are in that?
If I would just take the extra 15 seconds and put the rule directly on the interface - I can easy see on any network EXACTLY what the rules are for that network... I don't have to jump all over looking to see if floating rule applies or if group has interface X in it, etc..
So while these features are handy if you have 100's of interfaces.. If your managing a handful.. Its easier to just do the rules on the interfaces directly - even if you might have to duplicate a bit of work.. It will make your life easier going forward!!!