VPN IPsec Site-to-Site with NAT.
-
Hi everybody.
I have this situation:
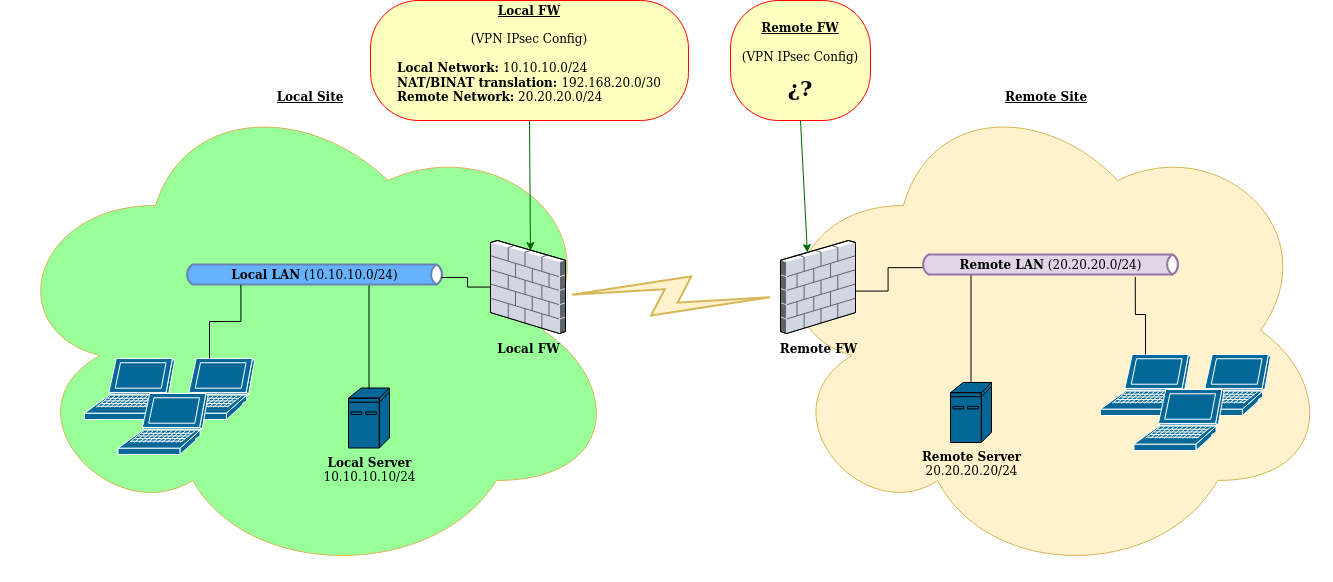
The IPsec config in the Phase 2 on my Local FW is:
Local Network: 10.10.10.0/24
NAT/BINAT translation: 192.168.20.0/30
Remote Network: 20.20.20.0/24I can access from my Local LAN to the Remote LAN without problems.
Local Server (10.10.10.10) -> Local FW (NAT: 10.10.10.0/24 -> 192.168.20.0/30) -> Remote Server (20.20.20.20)
But I need access from Remote LAN (20.20.20.0/24) to my Local Server (10.10.10.10)
What whould I need to configure in my Local FW to permit that the Remote LAN, or at least the Remote Server, can connect to my Local Server?
The Remote LAN only need connect to my Local Server.
I unknow the IPsec config of the Remote FW and I haven't access to it.
Regards,
Ramsés
-
Well, I think that there is two solutions, depending of the objective:
Objetive 1.- Local Server <---> Remote Server
Create a Phase 2 and configure:
Local Network: Address > 10.10.10.10
NAT/BINAT translation: Address > 192.168.20.1
Remote Network: Address > 20.20.20.20Only the Host that We put in Local Network can go through the VPN to the Host that We put in Remote Network.
We also need add a Firewall Rule (Firewall > Rules > IPsec) that permit the traffic from 20.20.20.20 to 192.168.20.1
The Local Server can connect to Remote Server through the IP 20.20.20.20 and the Remote Server can connect to Local Server through the IP 192.168.20.1
Objetive 2.- Local LAN <---> Remote LAN
Create a Phase 2 and configure:
Local Network: Network > 10.10.10.0/24
NAT/BINAT translation: Network > 192.168.20.0/24
Remote Network: Network > 20.20.20.0/24All de Hosts in the network that We put in Local Network can go through the VPN to the Hosts in the network that We put in Remote Network.
We also need add a Firewall Rule (Firewall > Rules > IPsec) that permit the traffic from 20.20.20.0/24 to 192.168.20.0/24
In this situation, the NAT is done Host to Host, that is:
10.10.10.1 > 192.168.20.1
10.10.10.2 > 192.168.20.2
10.10.10.3 > 192.168.20.3
10.10.10.4 > 192.168.20.4And the Remote Hosts can reach the Local Hosts by the corresponding NATed IP (192.168.20.x)
I think that this is correct. If It is not correct, please, tell me.
We are thinking that all config is correct in the Remote FW.
Regards,
Ramsés