Help with my pfsense + unifi AP setup
-
I was able to change my Asus router from AP mode back to router mode. I will keep the Unifi AP unplugged for now to remove that from the equation and just use the wifi from my Asus router.
How can I access my pfsense gateway (192.168.69.1) thru a client (192.168.50.X) connected to the Asus router/wifi (192.168.50.1)?
I've tried:
Services > DNS Resolver > added Host override using:
Host: pfSense (same as System> general setup > host)
Domain: localdomain (from System > general setup > domain)
IP to return for host: 192.168.69.1 (is this correct?)When I punch in 192.168.69.1 on a client (connected thru the Asus router as 192.168.50.X), I can't get to the pfsense gateway (192.168.69.1). I can get to the Asus router gateway just fine (192.168.50.1).
Thanks for the patience. I'm sure I'm over complicating this with 2 routers running together. I dont want the pfense to assign IP's yet because various clients have been assigned static IP's my Asus router and I don't want to mess this setup up for now (i.e., wifi printers that were a pain for me to configure).
-
If the Asus is in router mode it should be connected to pfSense via it's WAN port. In that setup you should be able to access the pfSense webgui at it's LAN IP, 192.168.69.1, without making any changes in pfSense.
Is the Asus pulling an IP from pfSense on it's WAN via DHCP? Or is it set statically in that subnet correctly?
Steve
-
Connecting to the pfsense gateway thru a device connected to the Asus would work on some device but not others. Weird... The Asus seems to have better speed and range on the 2.4Ghz band than both the nanoHD and the Pro AP's.
I received the Unifi Switch 8 and have the nanoHD connected to it now. Currently experimenting on this separate network w/ a few devices then will transitioning most if not all devices onto it.
-
I'm having some issues getting my WLAN clients to ping to my wireless VLAN clients network... I suspect it has something to do with how the vlan and the unifi switch 8 is talking to each other (conflicting firewall rules or how vlan is being separated from main WLAN?). Here's what I'm doing:
-Using pfsense (192.168.69.1, igb0, default "LAN"port), connected to Unifi switch 8 (port 1), connected to Unifi nanoHD access point (POE port 5)
-Regular WLAN and VLAN both being broadcasted by the same nanoHD
-Raspberry pi 4b as a Unifi controller is connected to Unifiswitch port 8 as 192.168.69.2
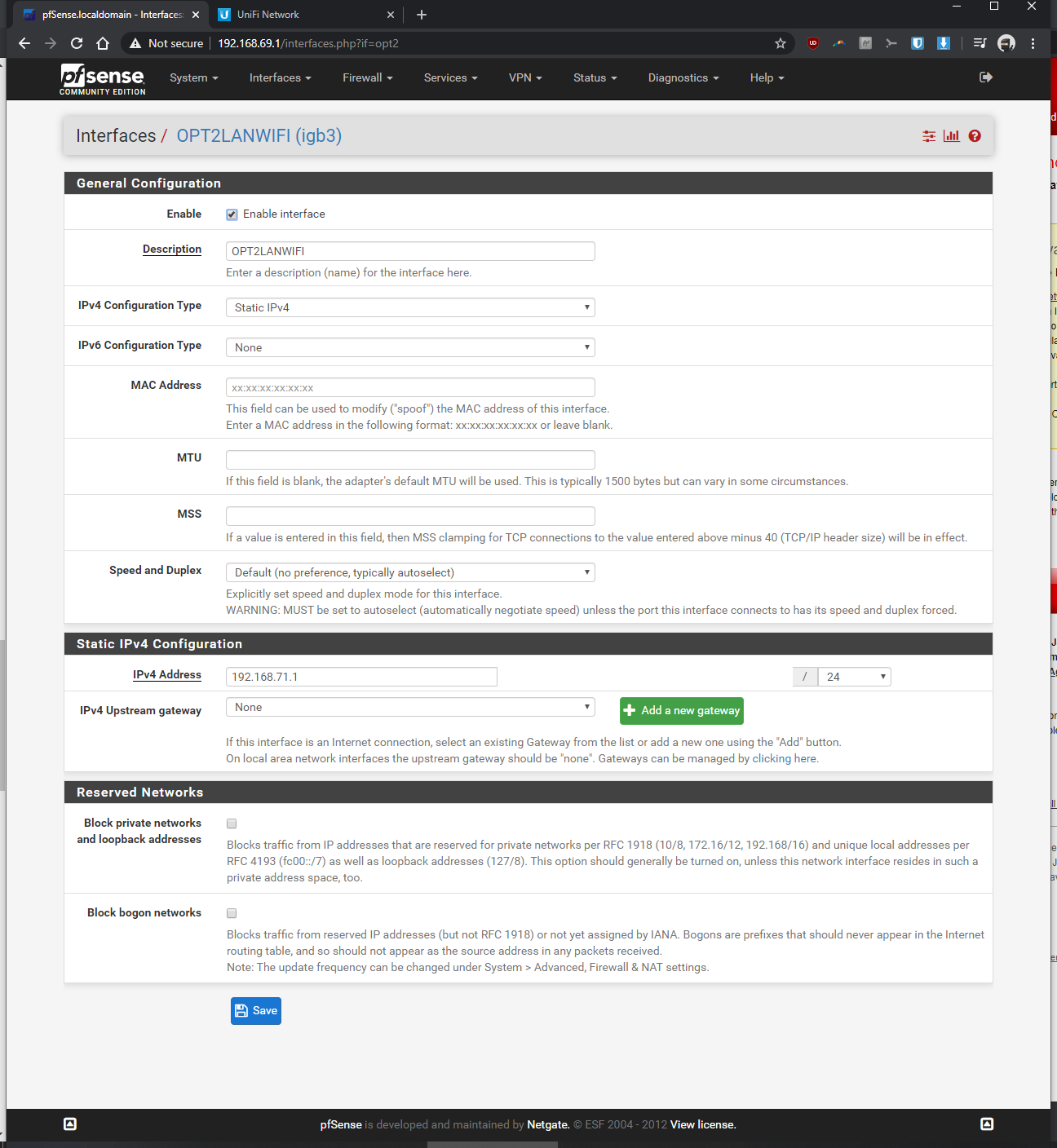
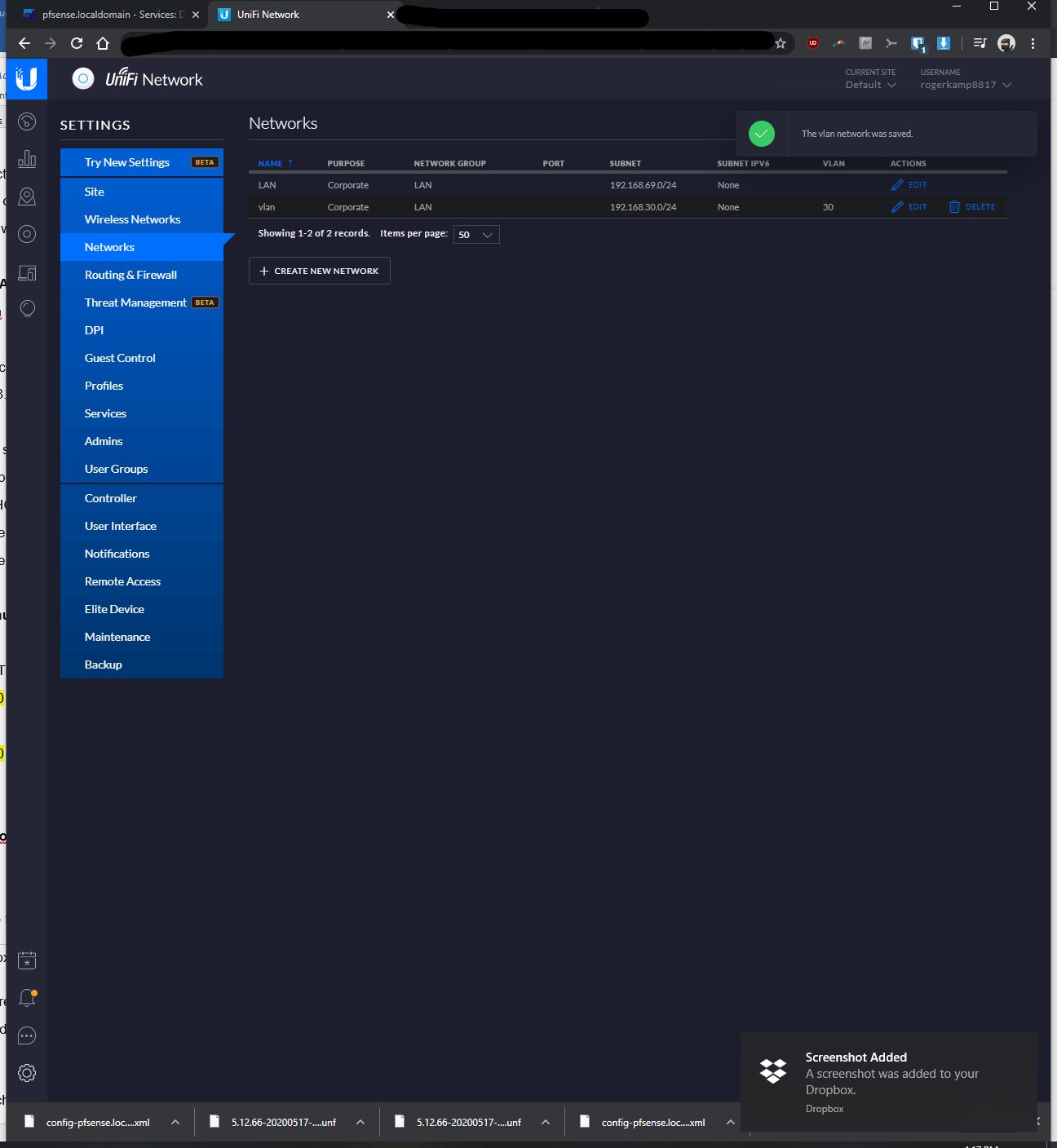
-I'd like the pfsense to assign IP's and not the Unifi switch 8In pfsense, I've setup a vlan as follows:
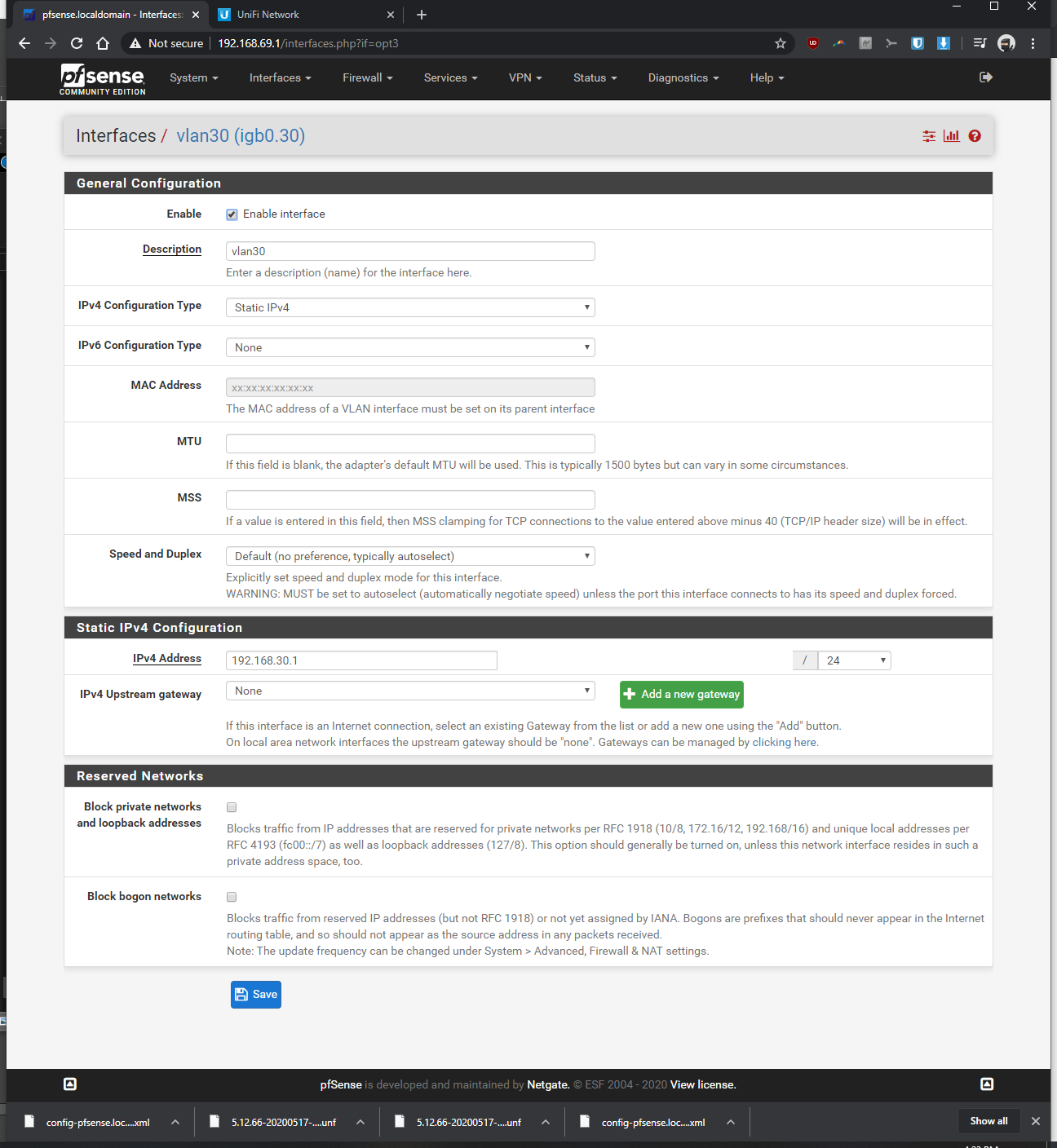
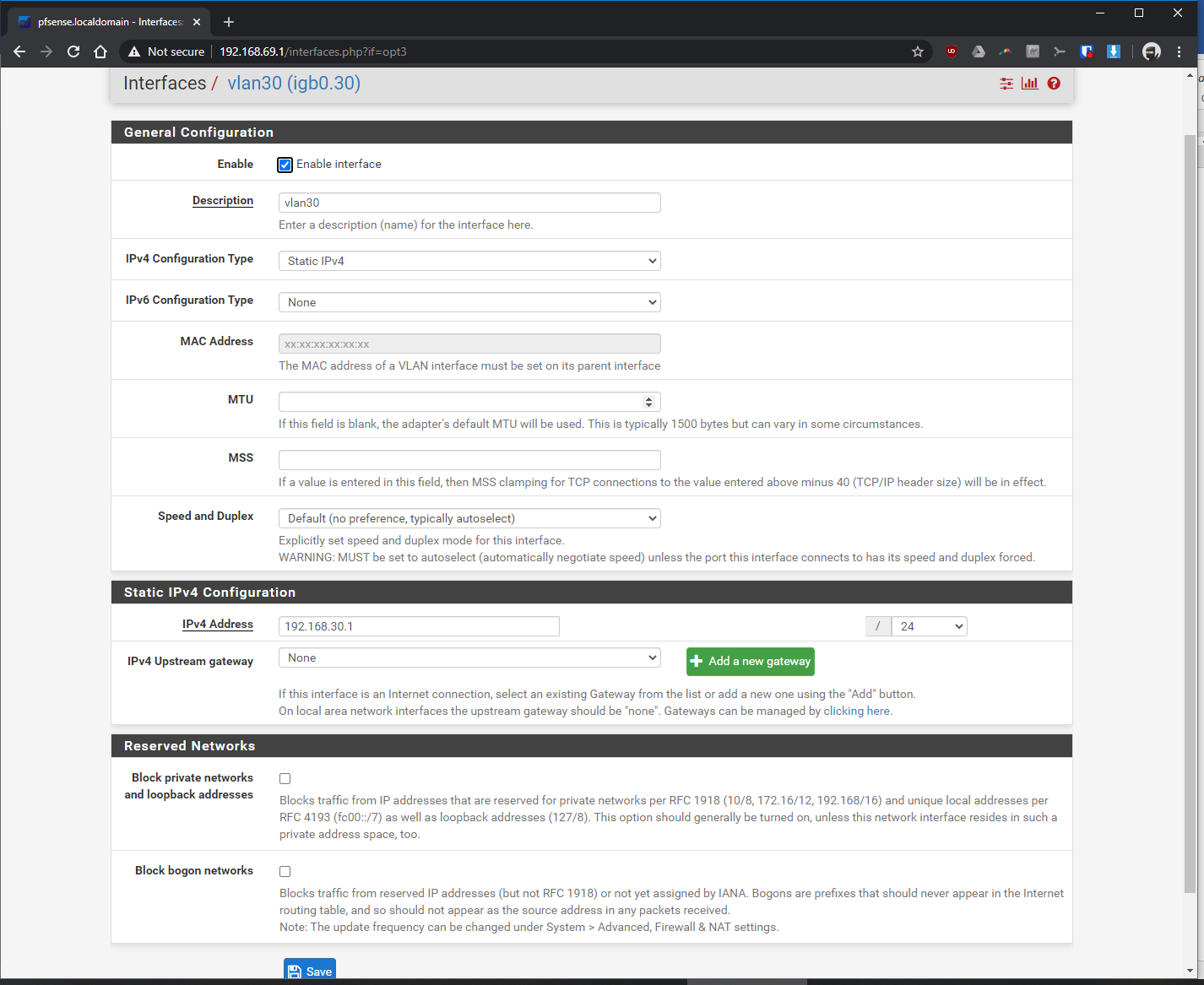
-Interfaces > interface assignments > vlans > vlan config: parent interface igb0 (same port unifi switch is plugged into), vlan tag: 30, vlan priority 0 (default), description: vlan30 > saved
-Interfaces > assignments > assigned VLAN30 to new OPT and renamed it, enabled it, static ipv4 of 192.168.30.1 / 24, saved
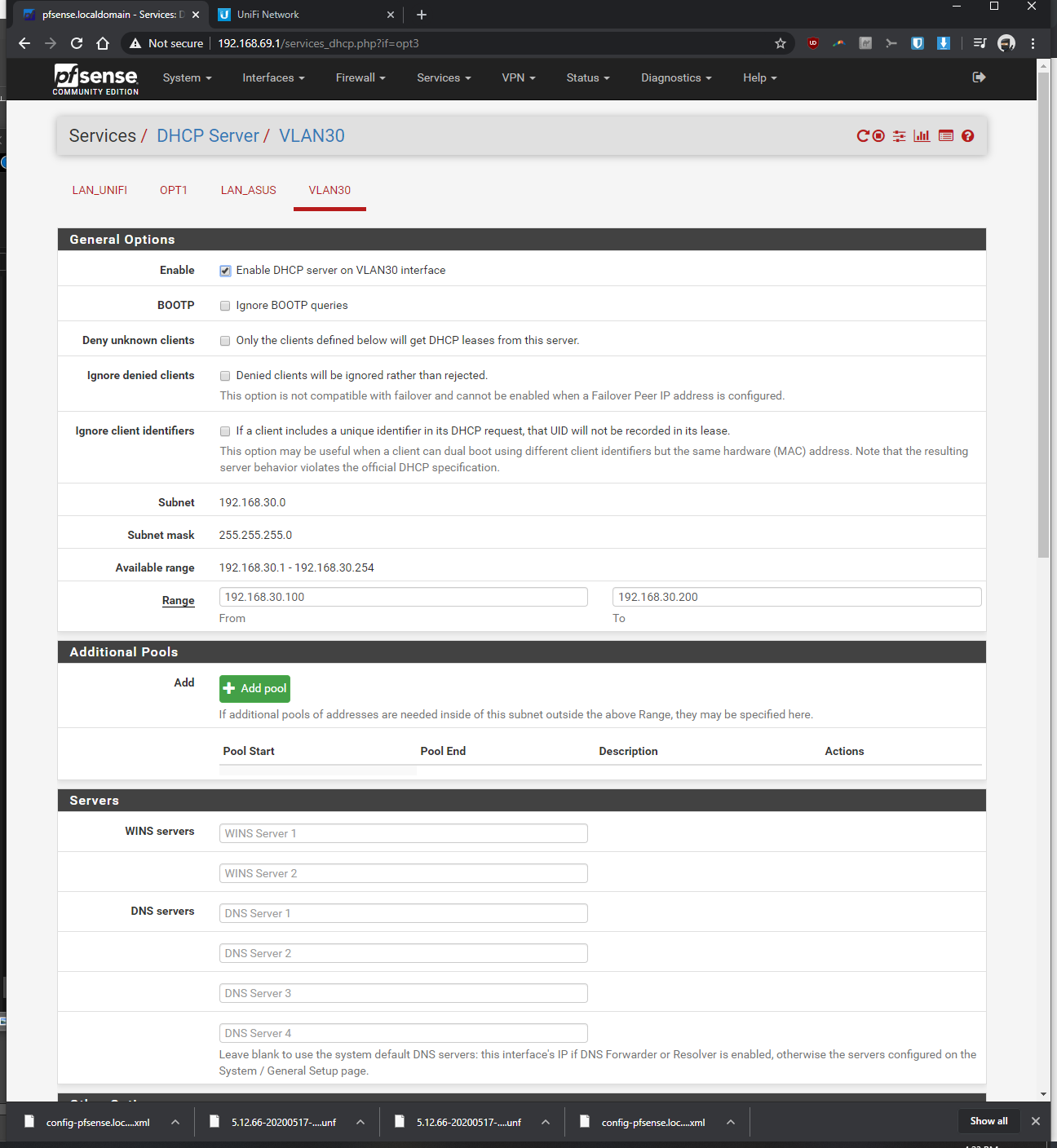
-Services > DHCP server > VLAN30 > enabled yes > range from 192.168.30.100 to 192.168.30.200, saved
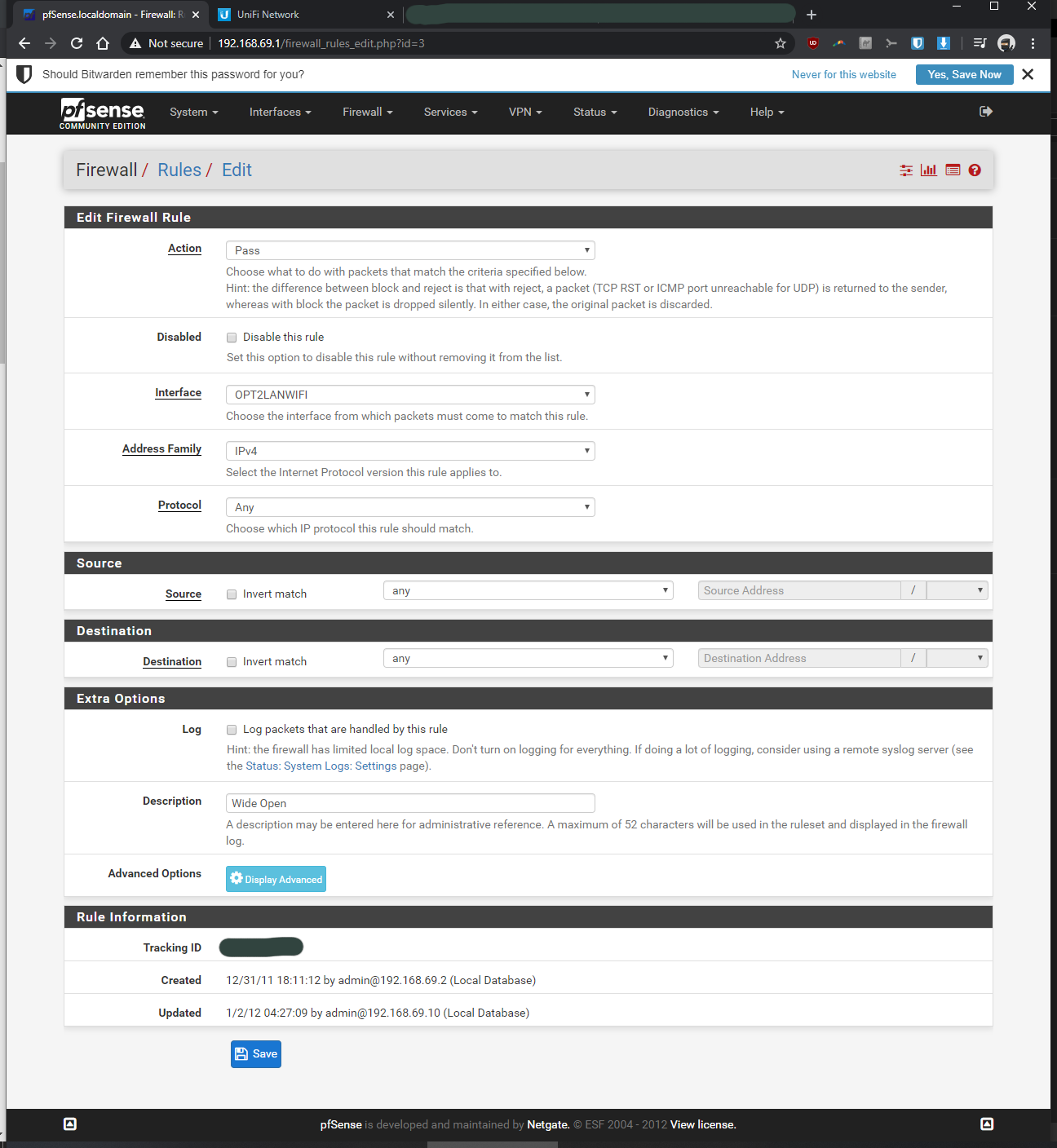
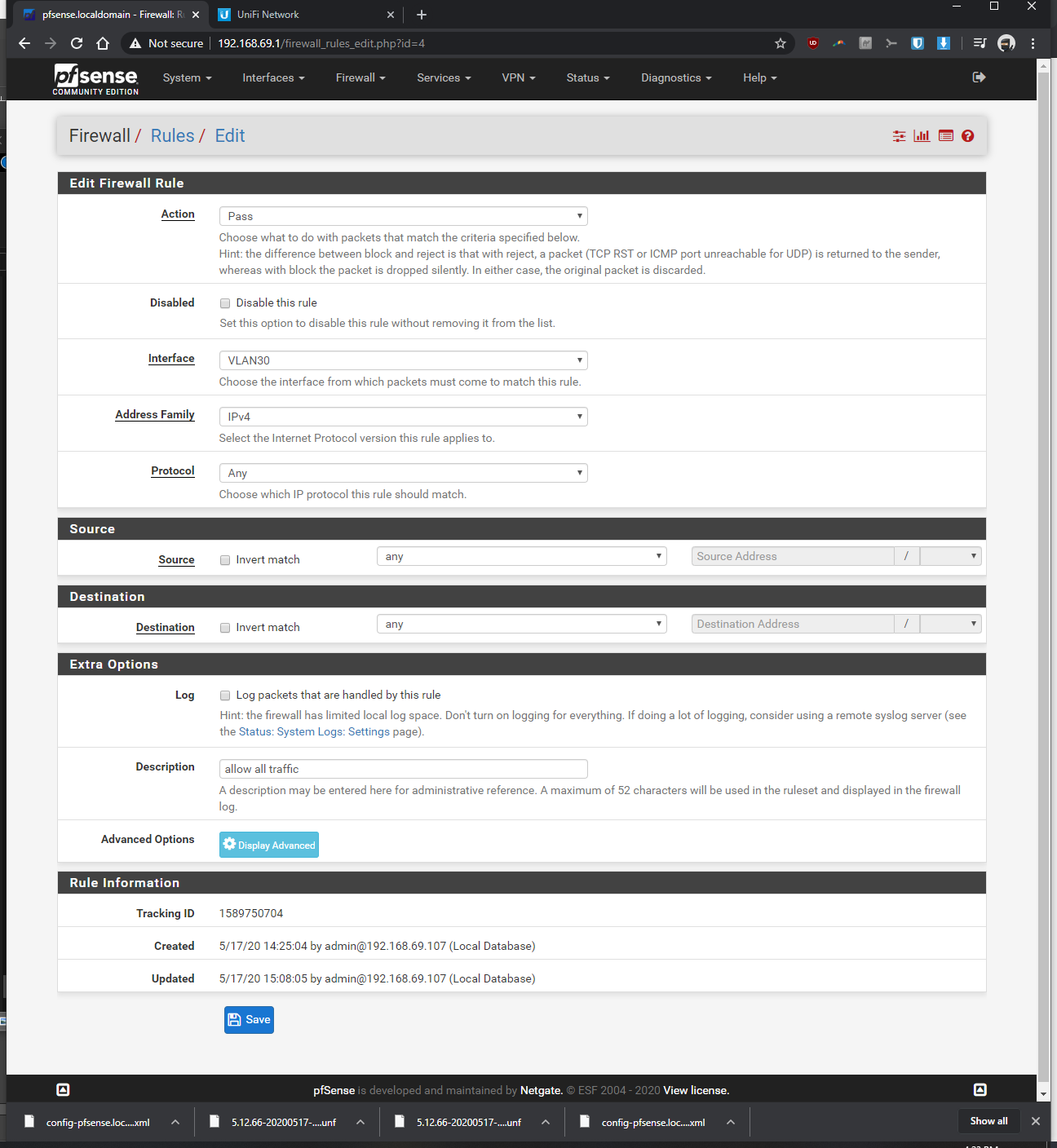
-Firewall > Rules > VLAN30> pass, interface vlan30, any, any, anyIn the Rpi4b Unifi Controller (192.168.69.2 static)
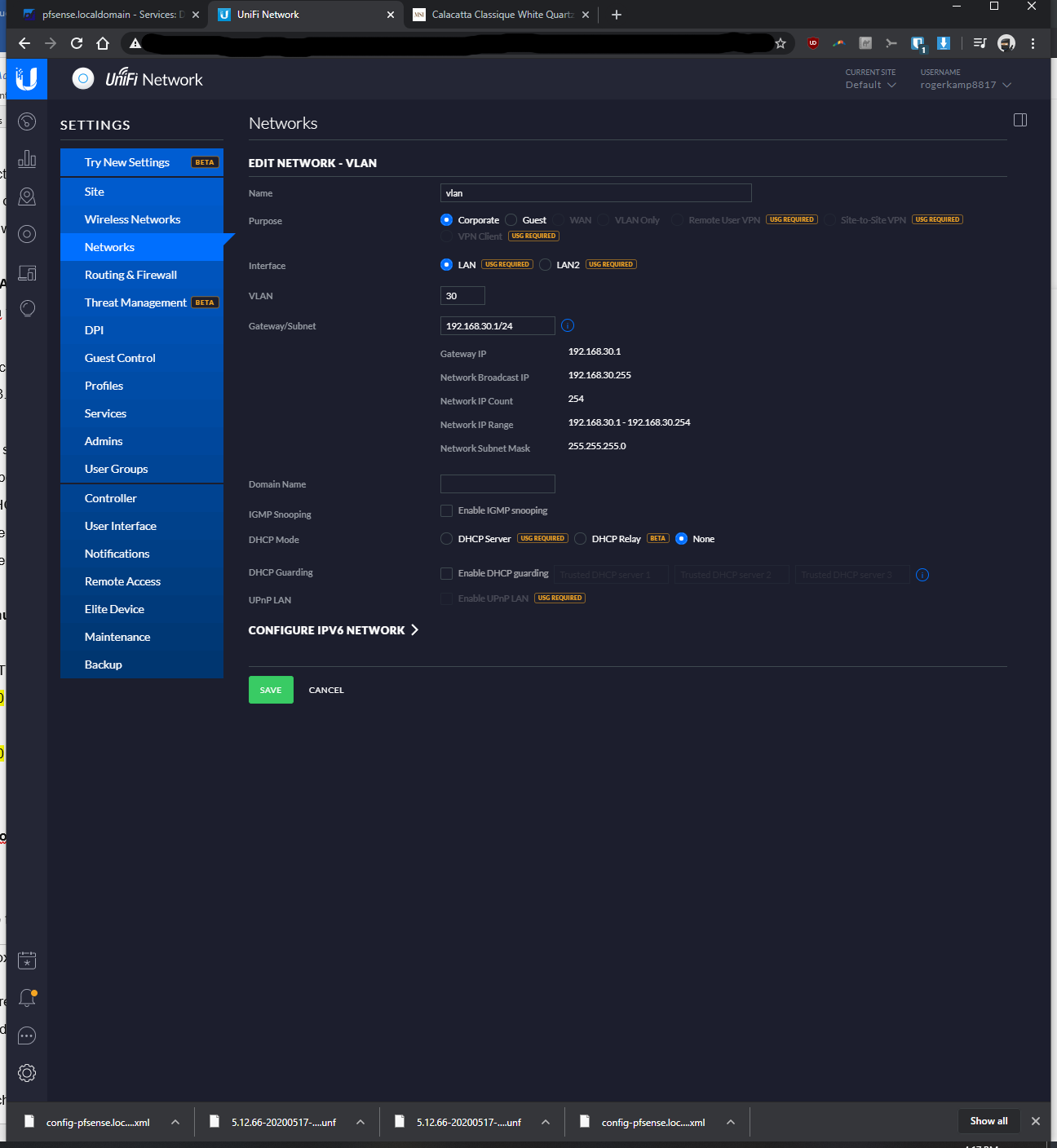
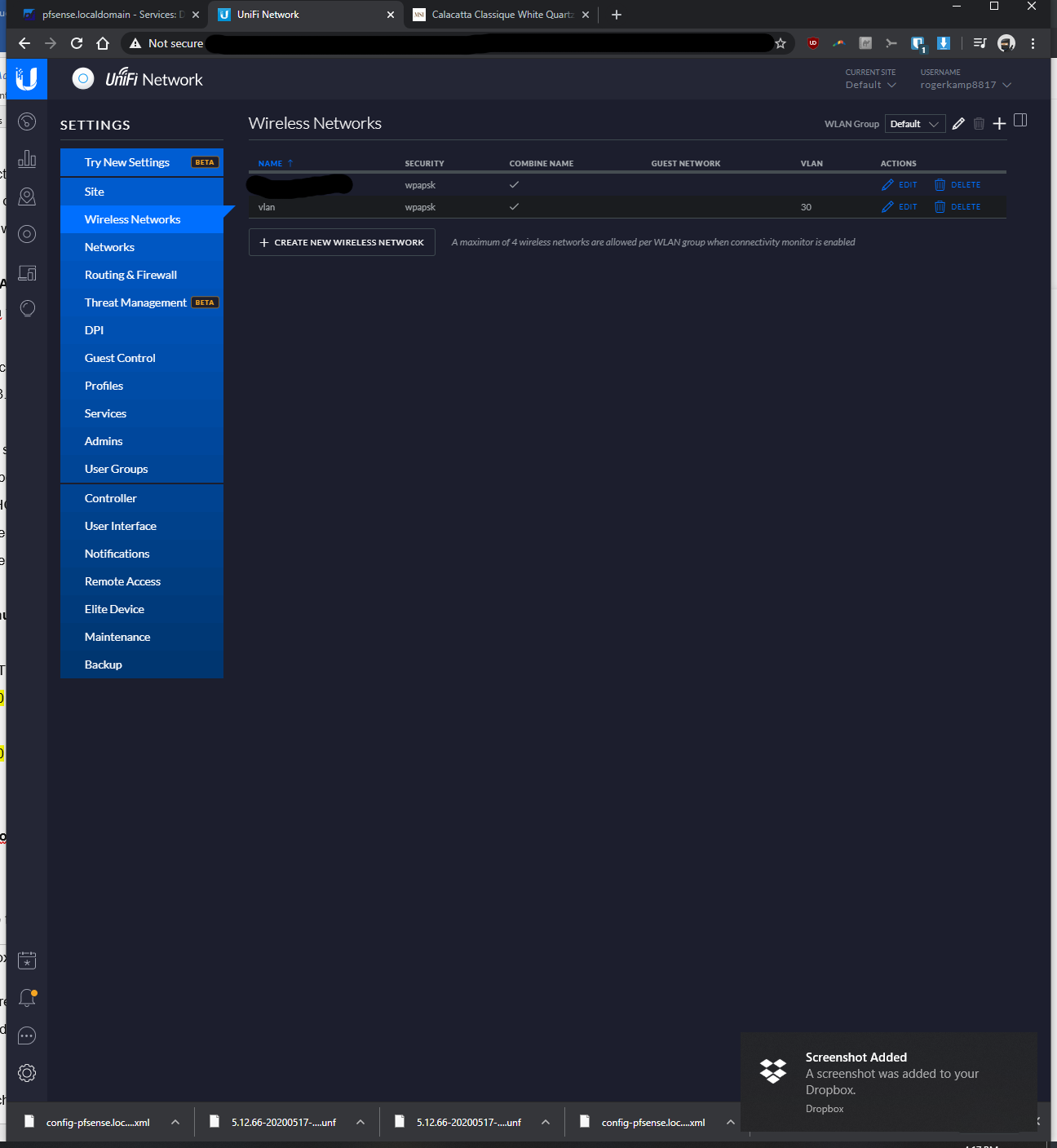
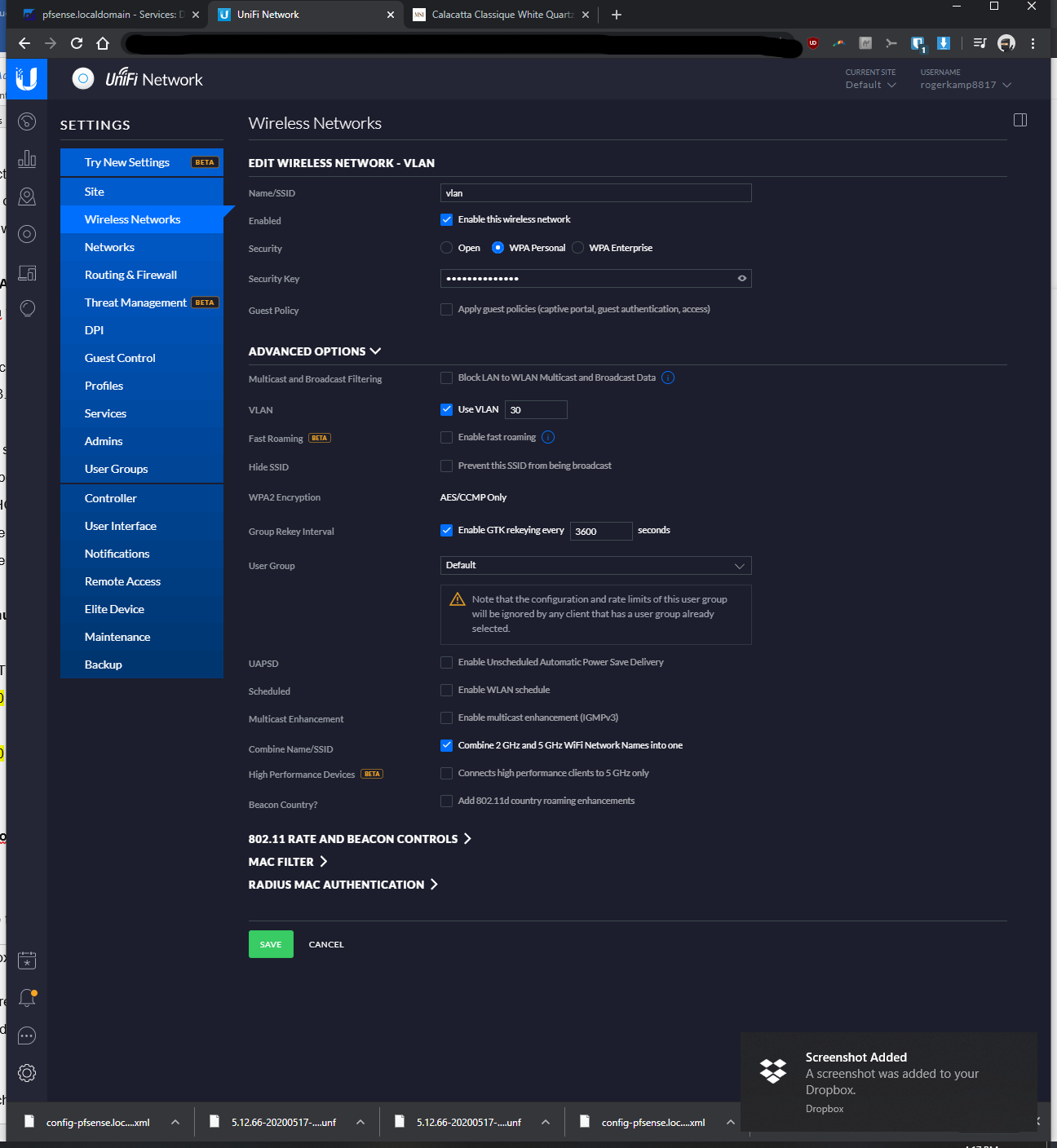
-At first, I initially only went to Settings > Wifi Networks > Create New Wireless Network >Named the SSD, entered password, and assigned vlan 30; however wifi devices connected to vlan 30 wasn't getting assigned a proper IP. From the tutorials I was watching, I think this should have worked, but it didn't seem to.
-In addition to doing the above bullet, I went to Settings > Wifi Networks > Networks > Named it vlan 30, kept corporate bubble filled, entered vlan ID of 30... After taking this additional step, then it started to assign proper IP's to the vlan connected device.When I ping from the RPi Unifi controller to my WLAN clients (not VLAN clients), it'd ping fine.
When I ping from the RPi Unifi controller or ping from other WLAN clients to VLAN clients, there is no connection
I would like to see that the VLAN network pings (transfers data) with other networks, before I setup additional firewall rules to prevent transfer (i.e., IoT devices).
-
What rules do you have on the interfaces... Showing us the specific 1 rule doesn't help... For all we know you have block rfc1918 enabled on that interface..
Keep in mind local devices firewalls as well... Just because pfsense allows traffic from 1 vlan to the other, doesn't mean the other devices firewall allows you to ping from that remote network.
-
Thanks for chiming in.
The tutorials I was following, it didn't mention anything about RFC 1918 (I left it as default/untouched). As you eluded to, it might be doing something that's preventing my vlan from communicating to non-vlan devices? What should I be changing with my settings to make the vlan devices ping with the non-vlan devices, without opening up my network to the entire internet by mistake? Should I be unchecking one or both of the resrved network check boxes within my WAN?
If you need to see any other screenshots, please let me know.
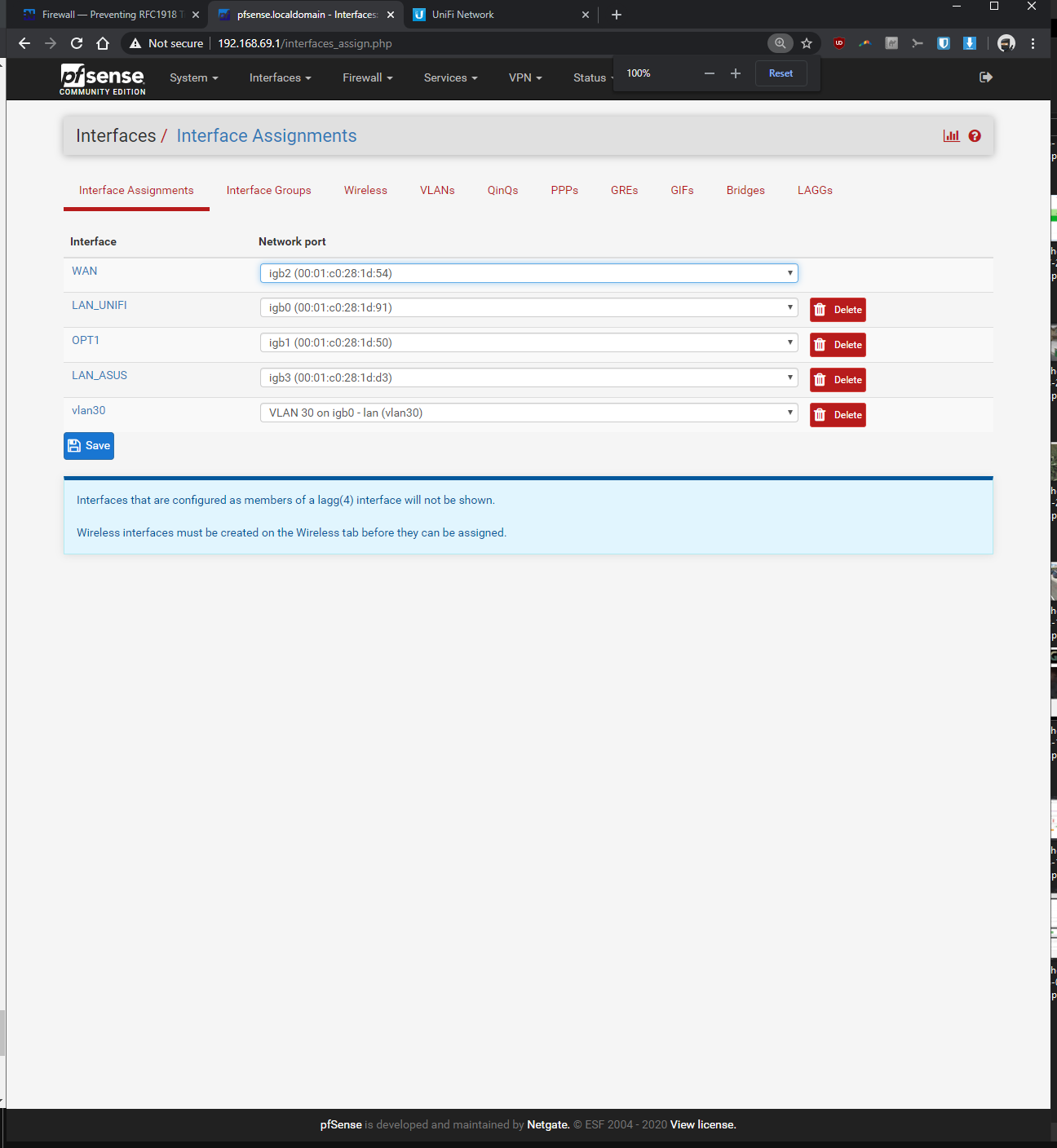
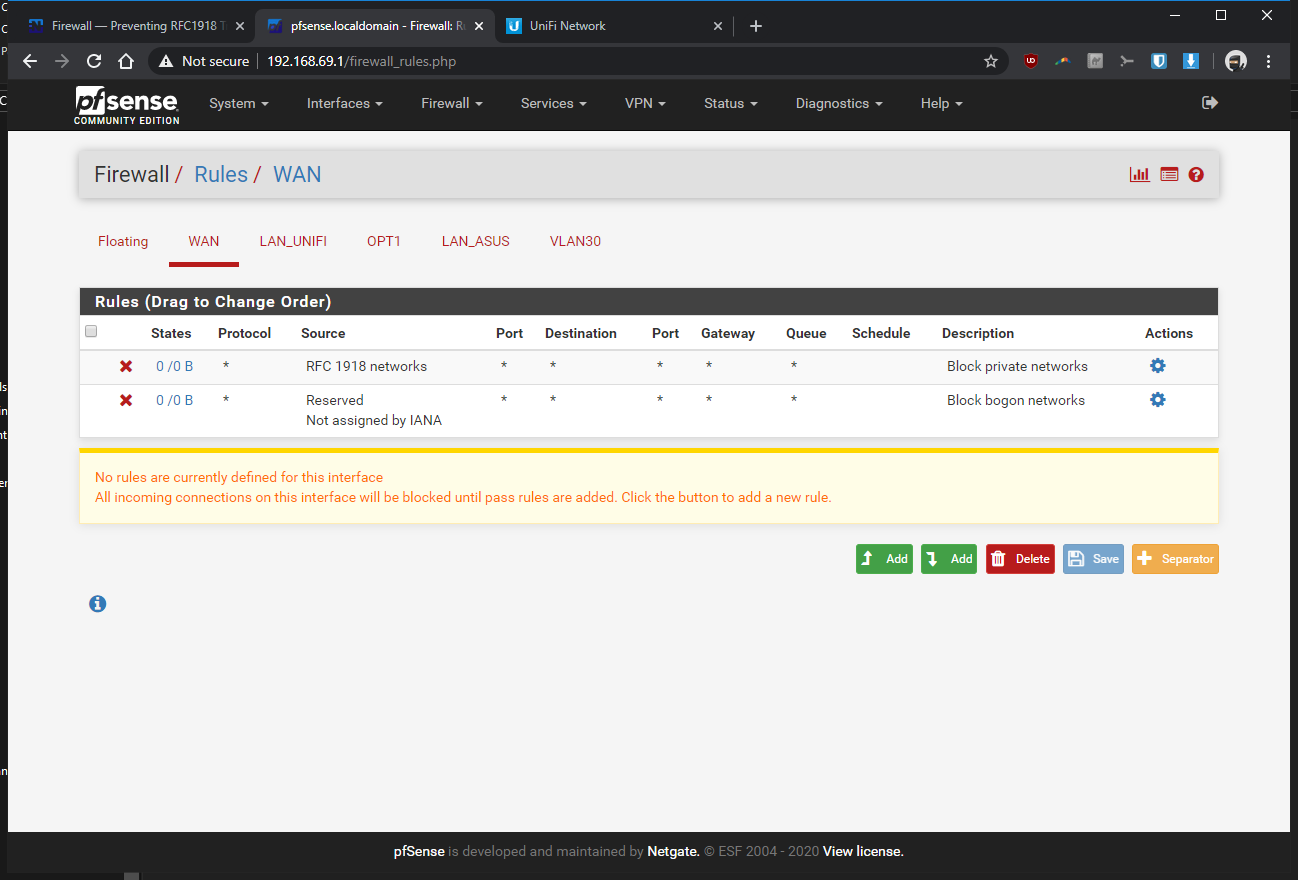
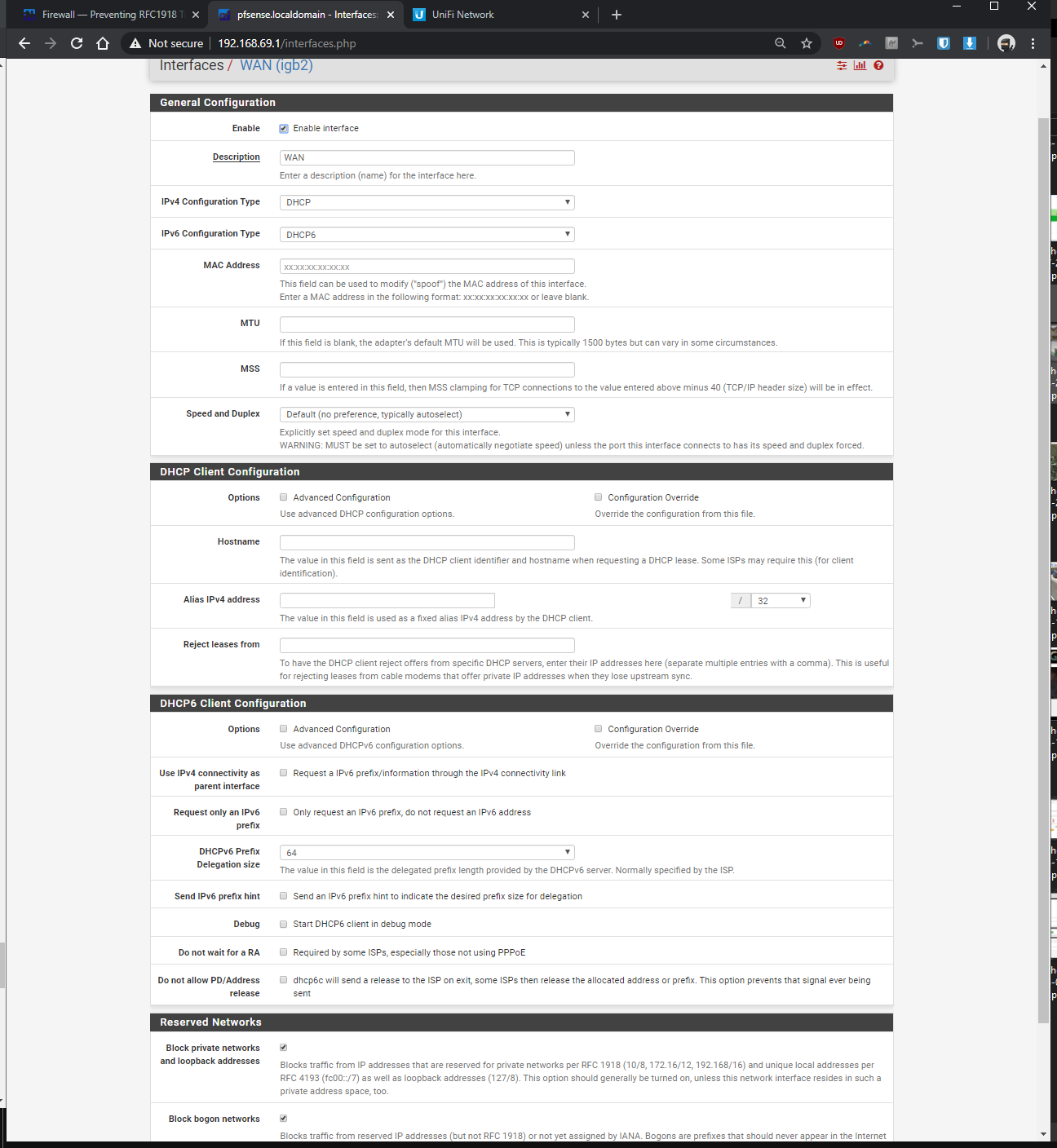
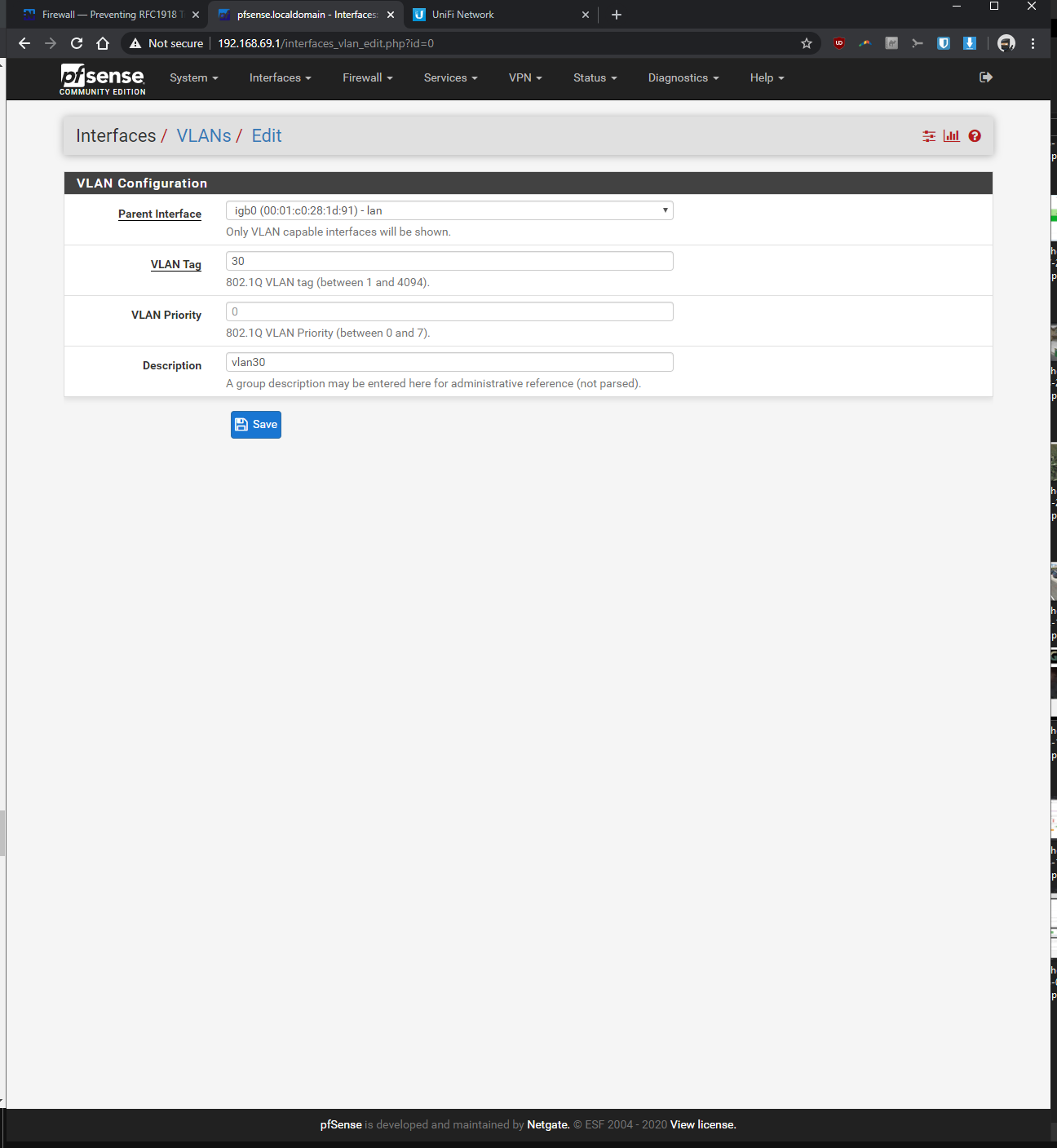
-
@rogerkamp8817 said in Help with my pfsense + unifi AP setup:
If you need to see any other screenshots, please let me know.
How about the firewall rules on the interfaces.. You know the ones I specifically asked for ;)
What rules do you have on the interfaces.
-
here you go! let me know if i'm still missing something...
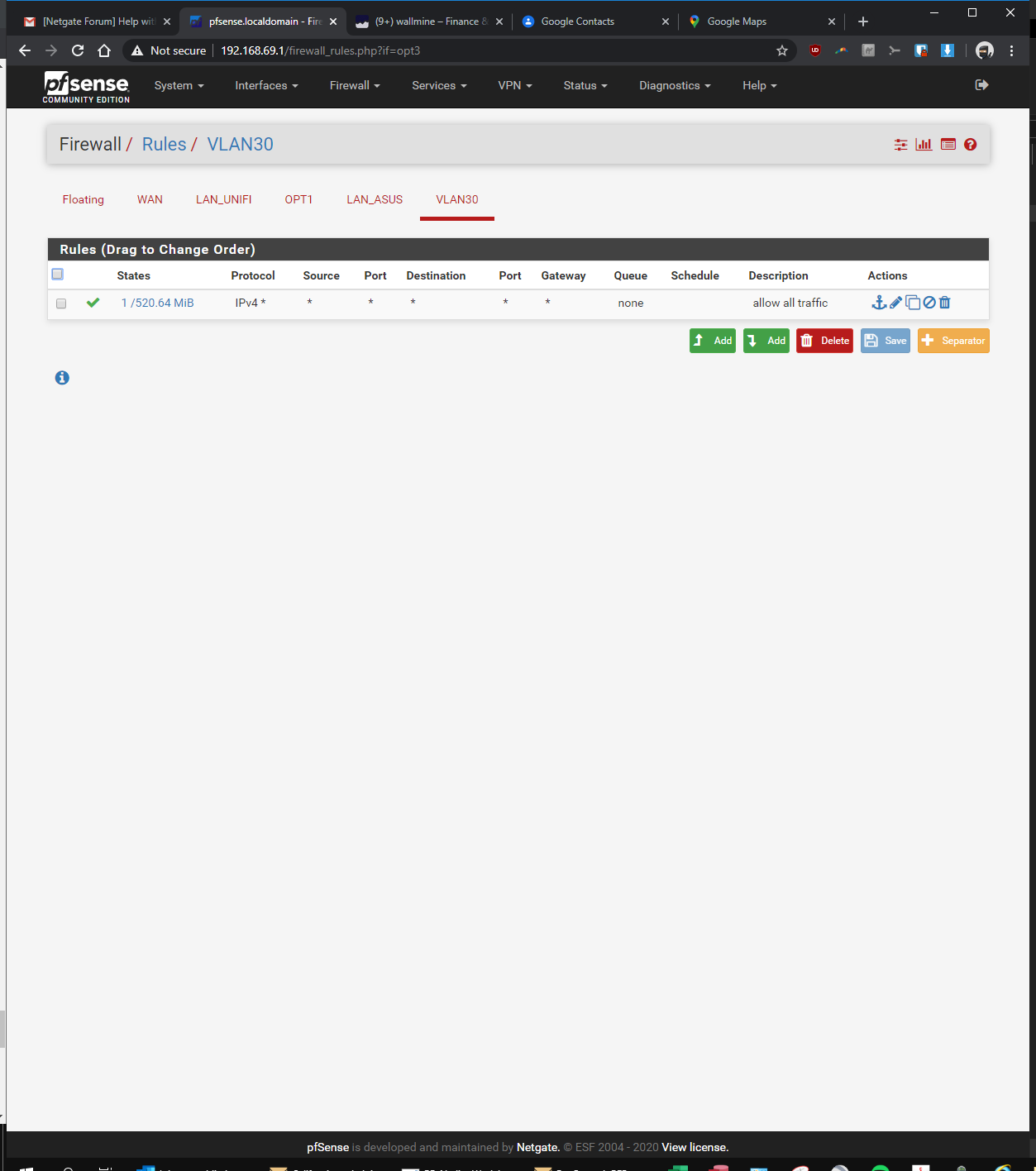
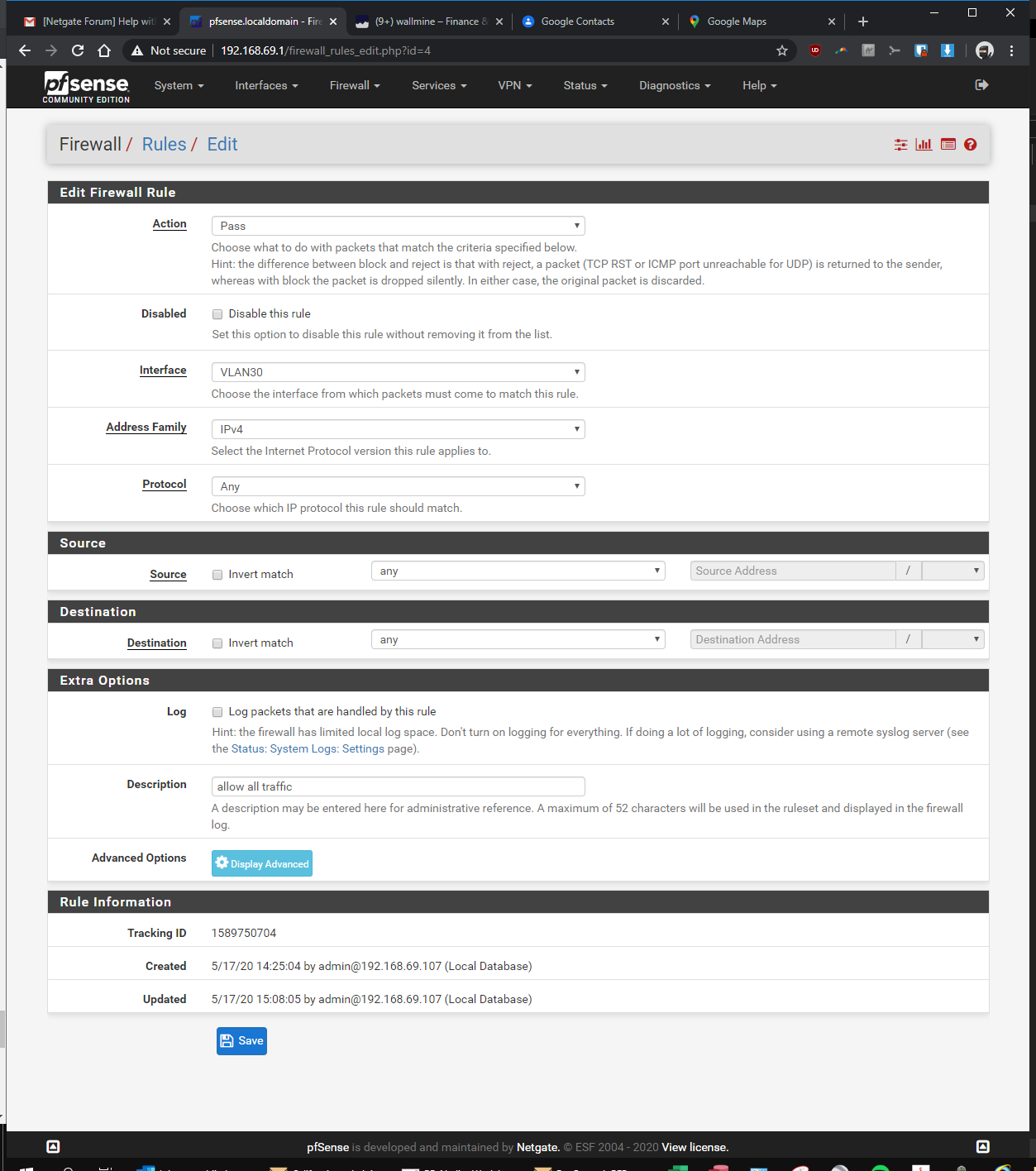
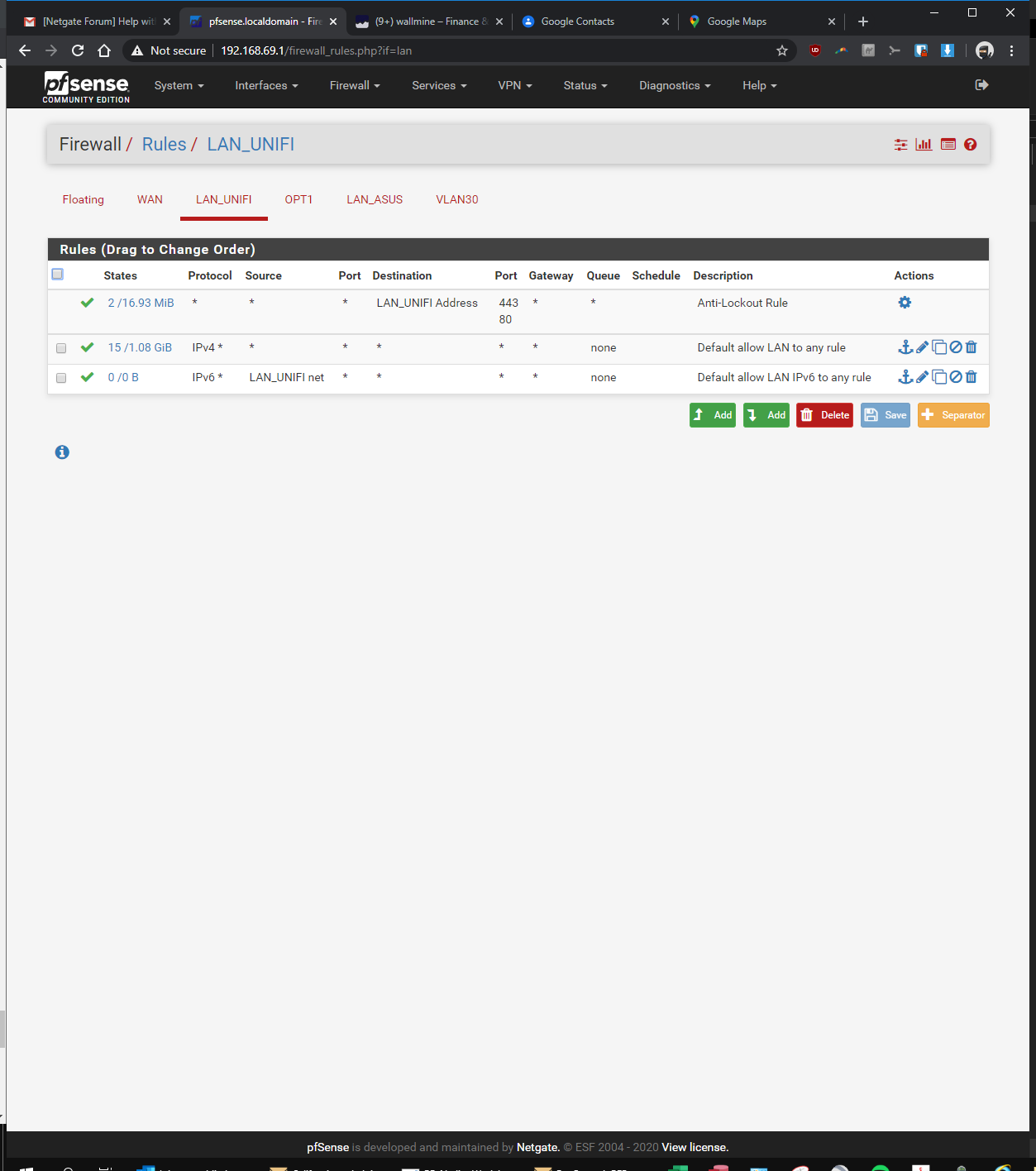

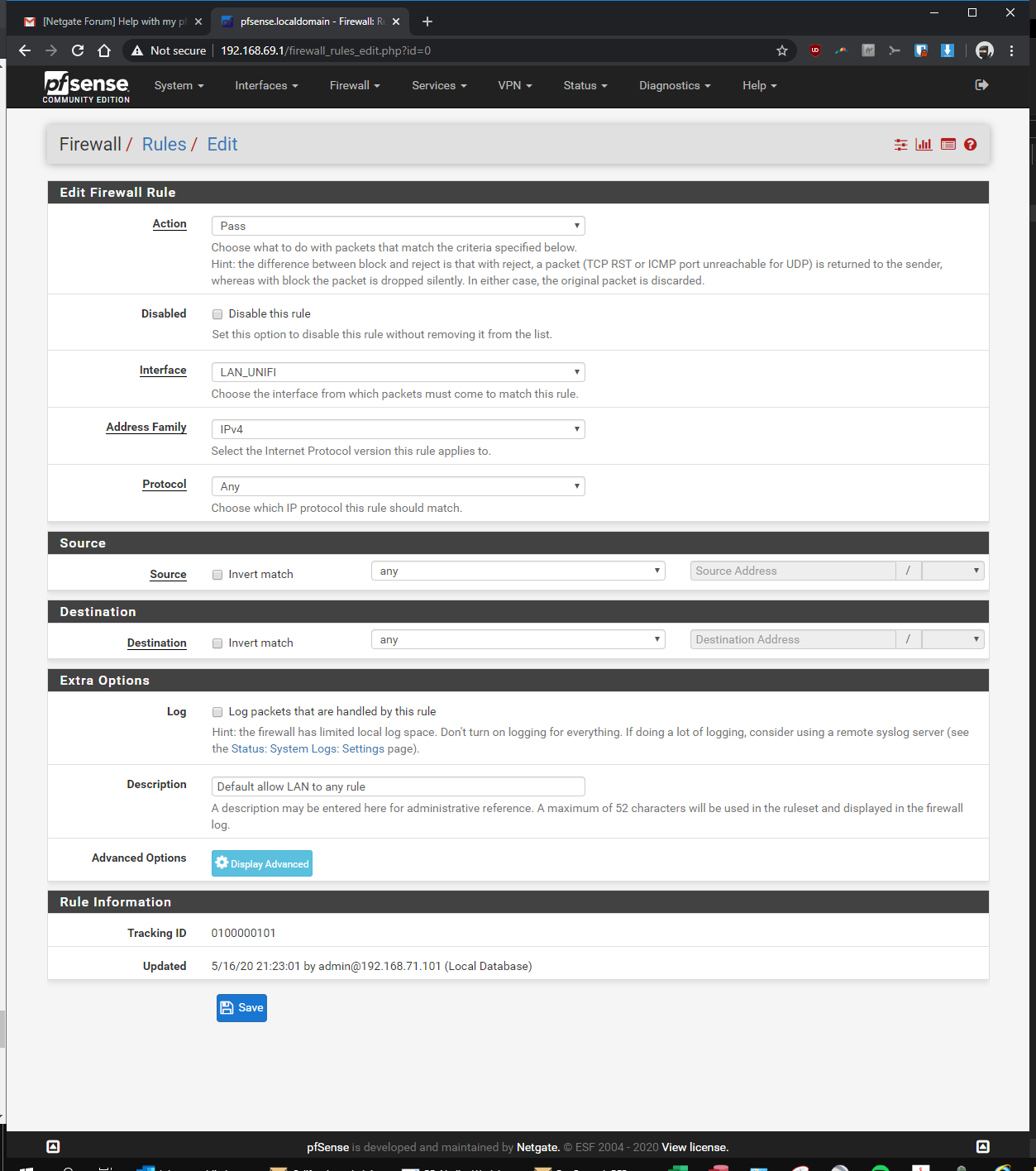
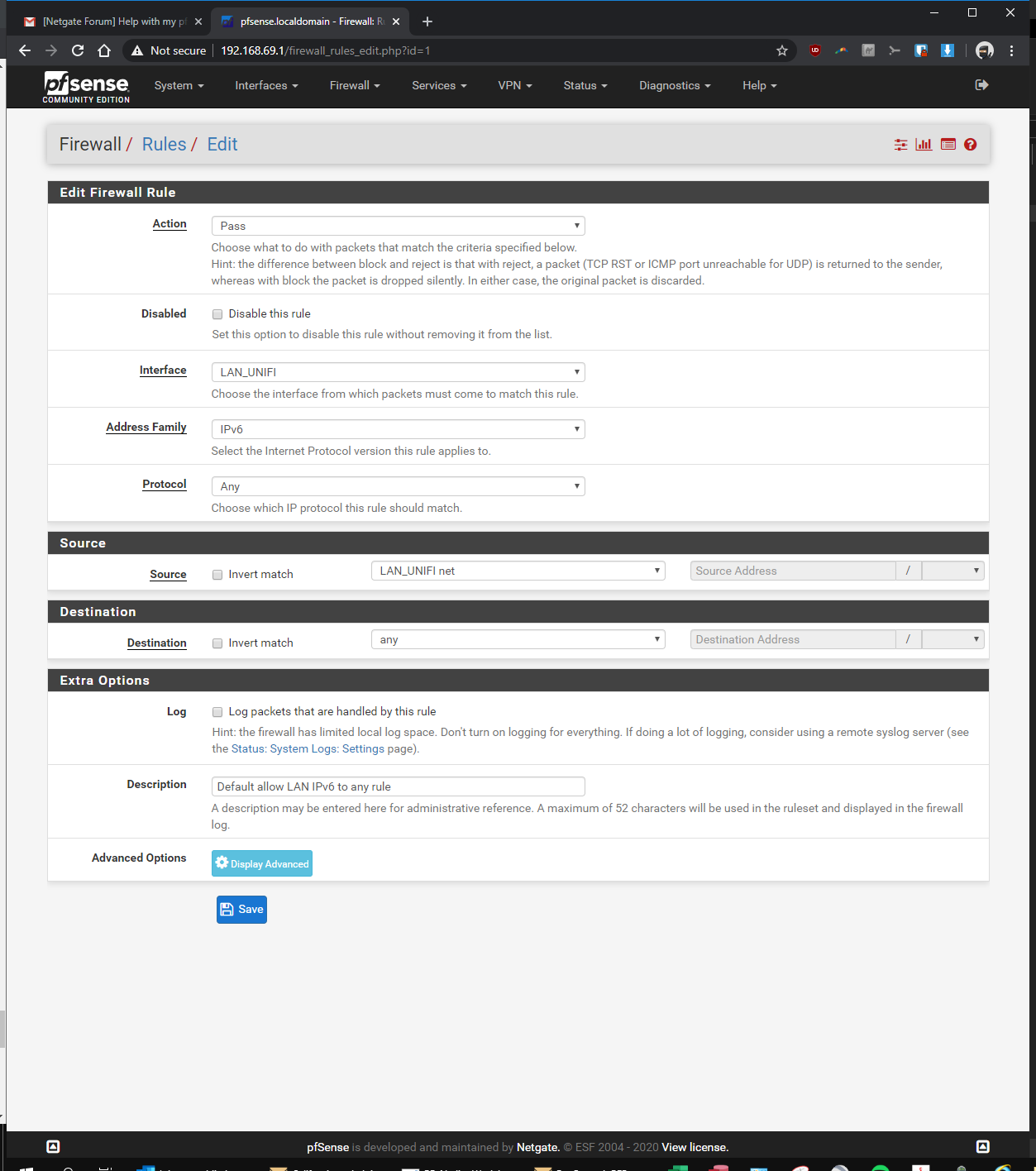
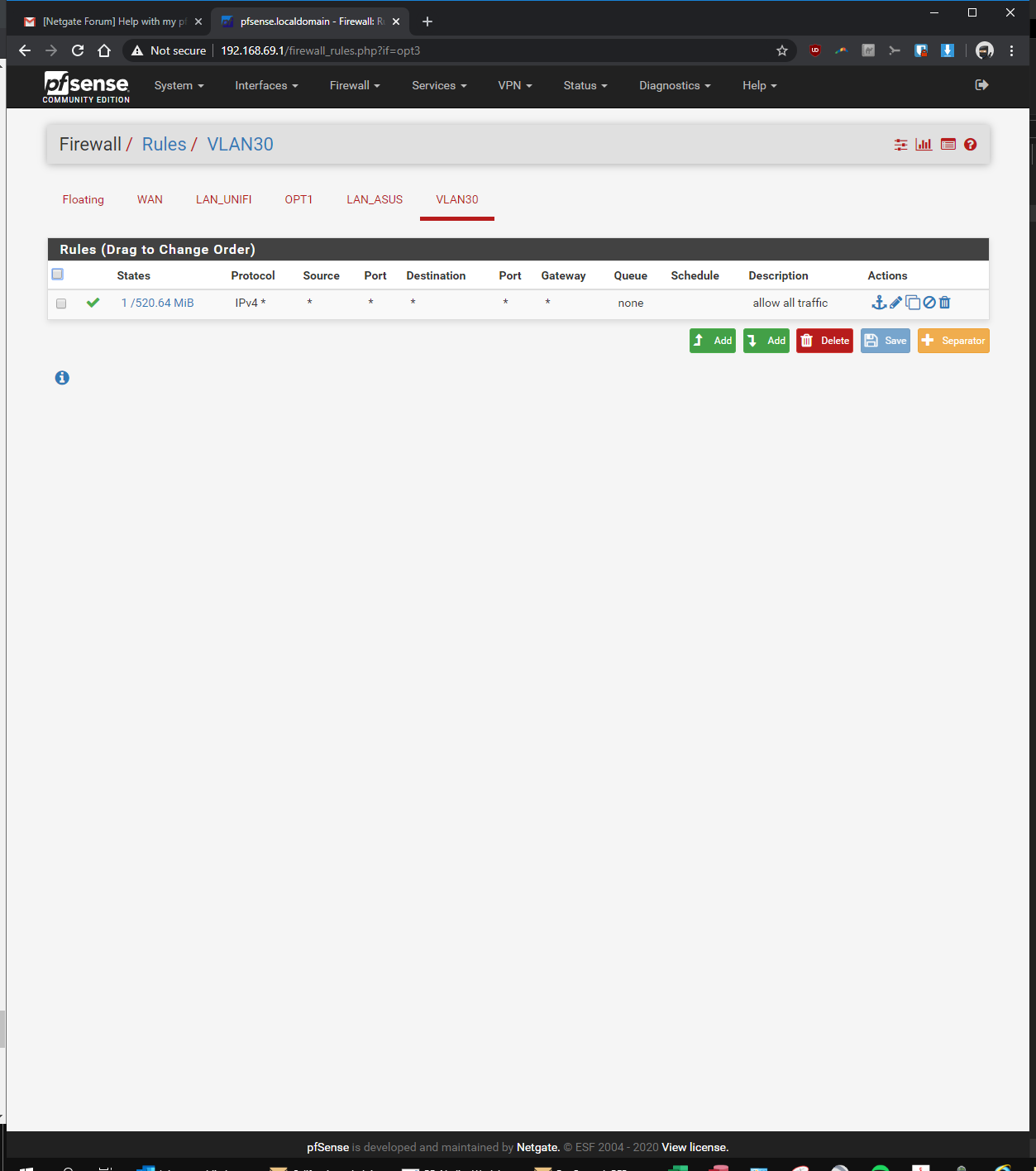
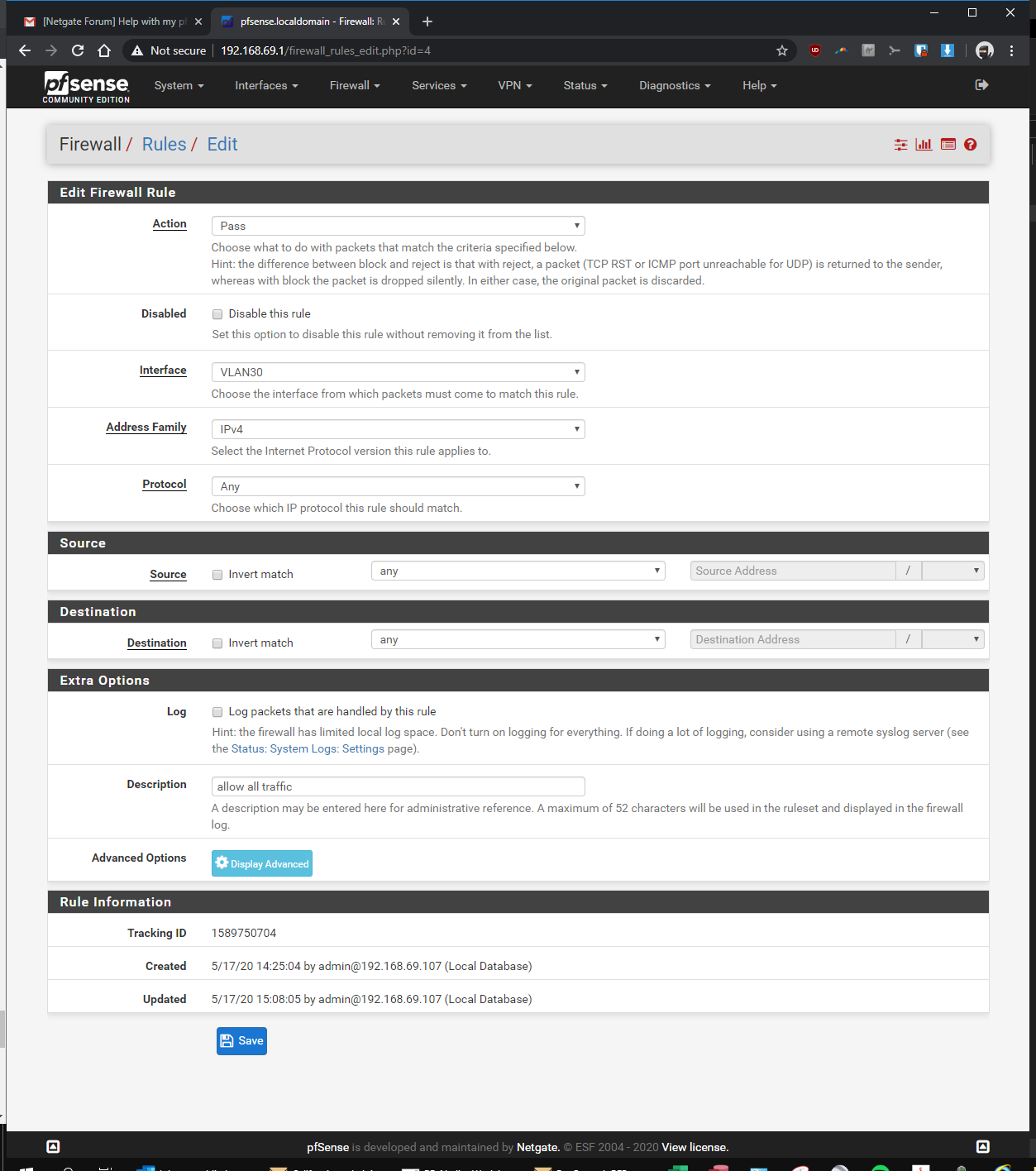
-
OMG!!! dude post up the rules so we can see their order
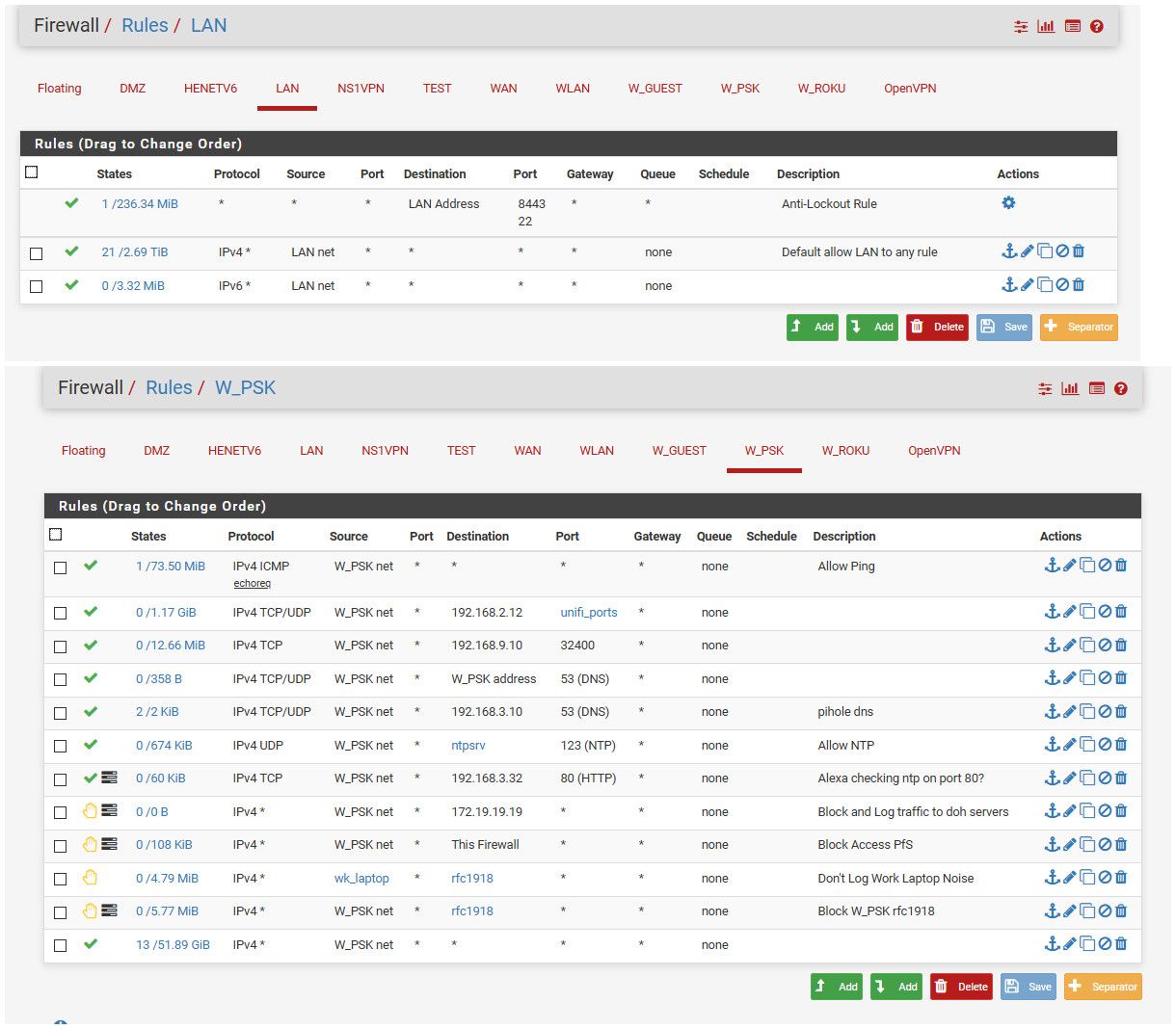
I shouldn't have to scroll through a hundred pages to see the info needed ;)
So your vlan rule is any any.. So if you can not ping some device in your lan - it would SCREAM that devices firewall.. Can you ping the pfsense lan IP from your vlan?
Simple test sniff on your lan interface while you say try and ping something in the lan from you vlan.. Do you see the traffic go out to the device from pfsense.. If so - if there is no answer, then its firewall on the device your trying to talk too.
-
Turns out I couldn't ping from one network to the next due to my client's firewall blocking it. Temporarily turning off windows 10 firewall allowed it to ping from 192.169.69.XX to 192.169.30.XX.
Over the past couple weeks, I've been trying to get my PIA VPN setup but I am running into significant slow down issues when the VPN is turned on. I've tried MANY different combinations and followed 5-6 different tutorials from scratch and still not finding a VPN config that gets me more reasonable VPN speeds.
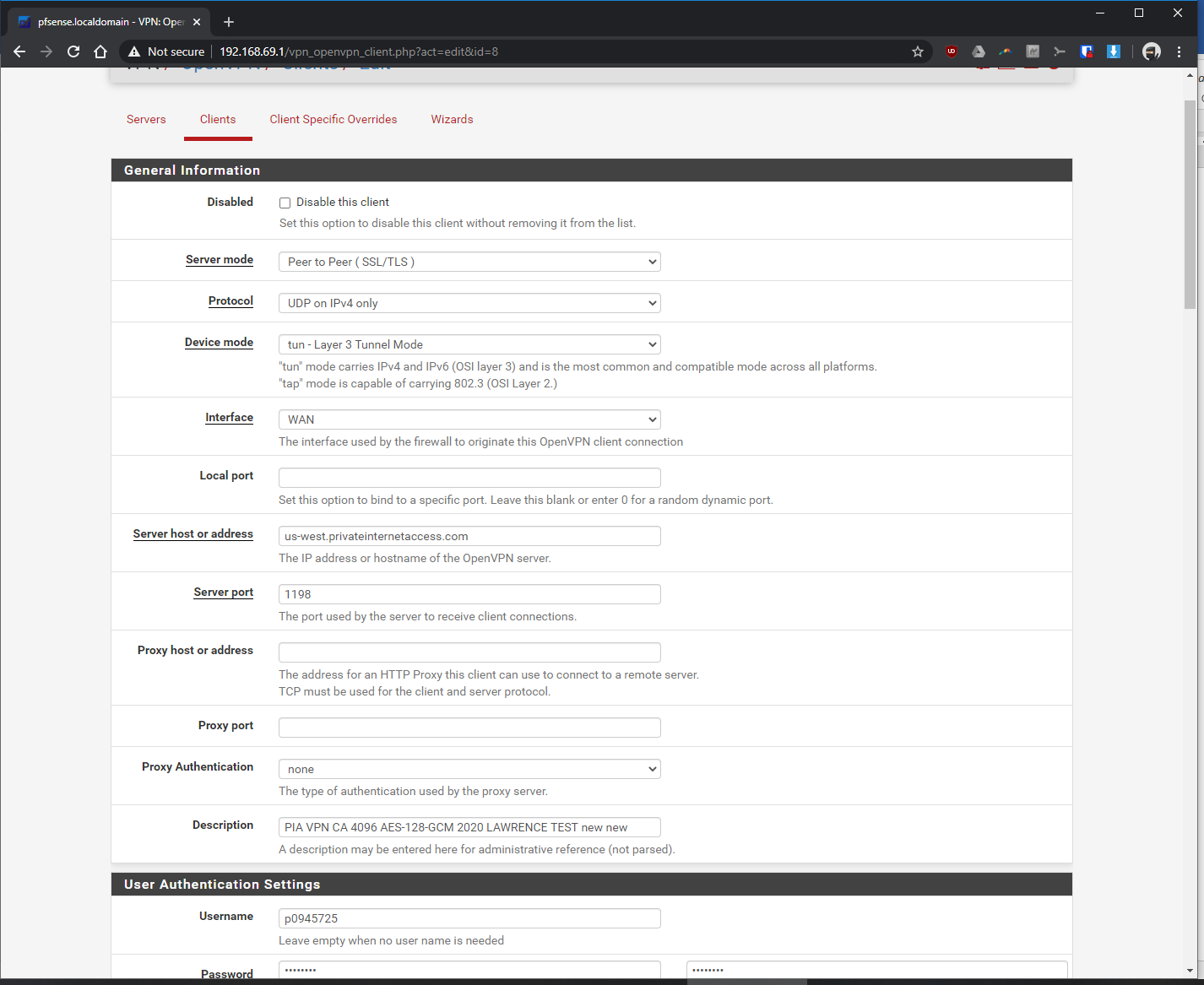
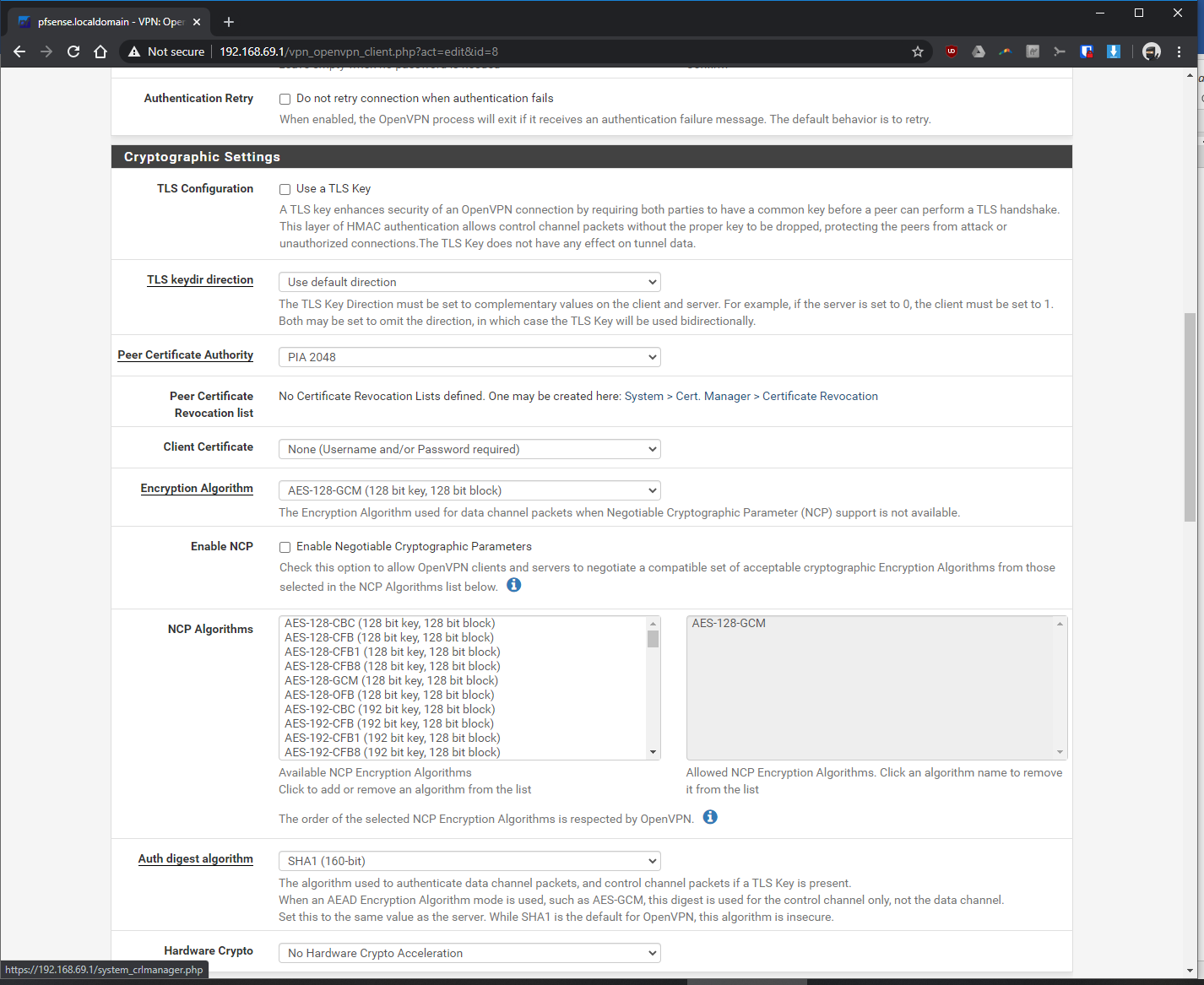
My internet is 1gig down and 36mpbs up. The up seems okay, but when the VPN is turned on, the down speed drops to anywhere from 10mpbs to ~80 mpbs at best. This is on a hardwared lan connection and running a fitlet2 minipc w/ Celeron J3455, 4gb of ram, and 32gb of SSD. It seems I can get it to work closer to 80 mpbs down when I mess with the encryption settings but 80 mpbs is way too slow for what I think this CPU was capable of. The upload speed seems fine.
I've tried different settings, ranging from AES-128-CBC, GSM, diff hardware cryptos (BSD crypto... & IntelRDAND), different VPN servers, different ports...
Can anyone provide some feedback on what I might be doing wrong?
Thanks in advance!! Sorry for all the screenshots.
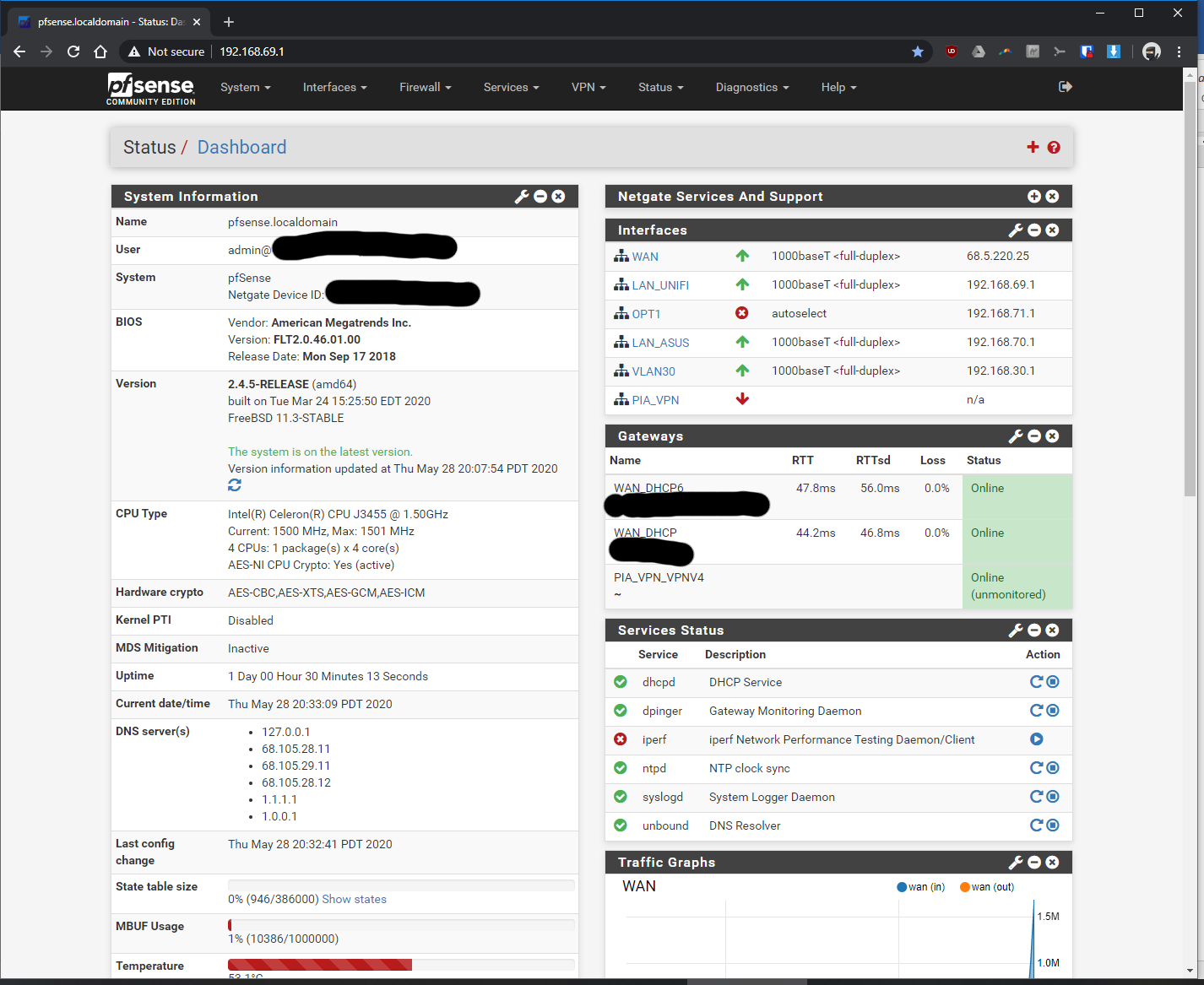
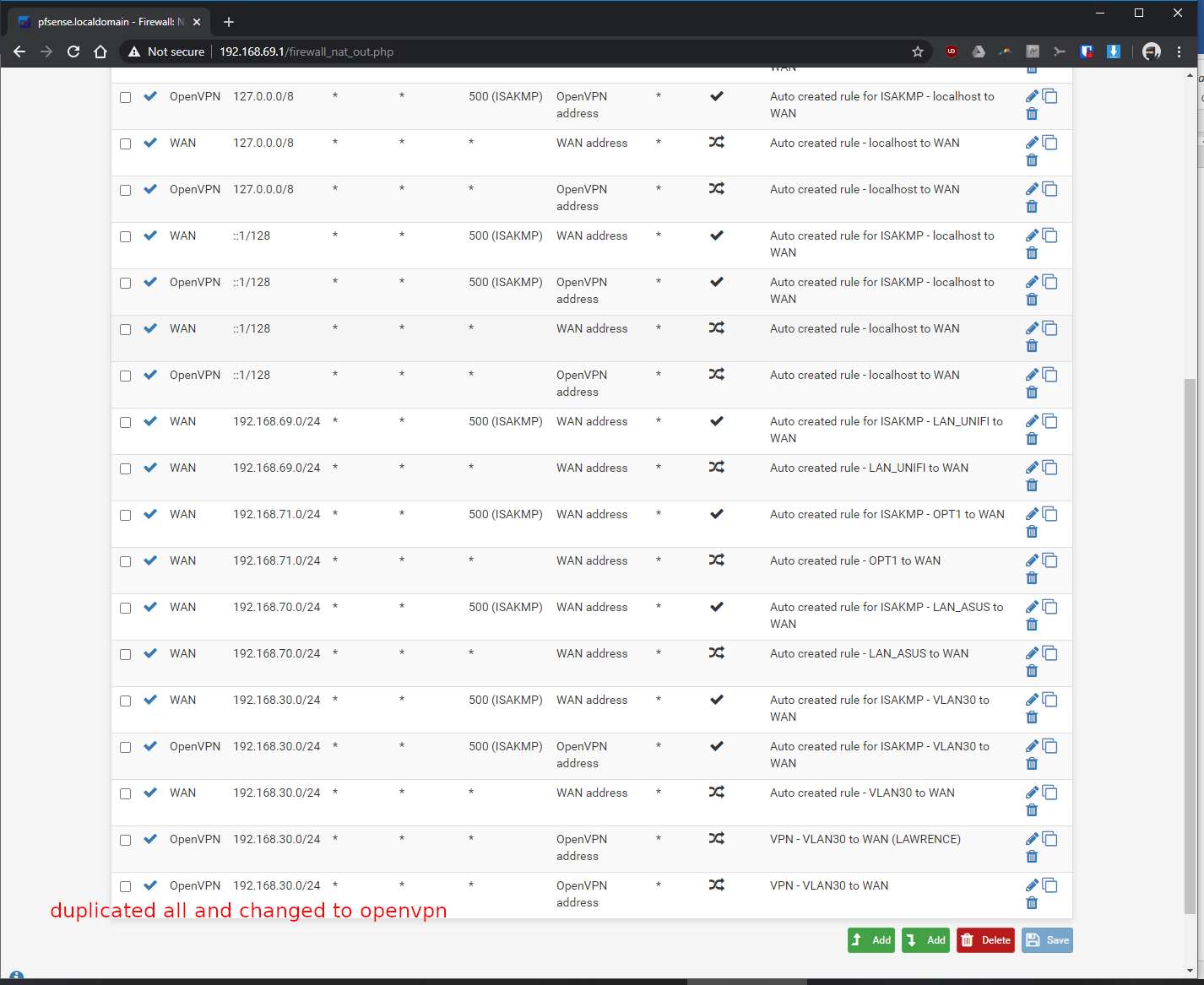
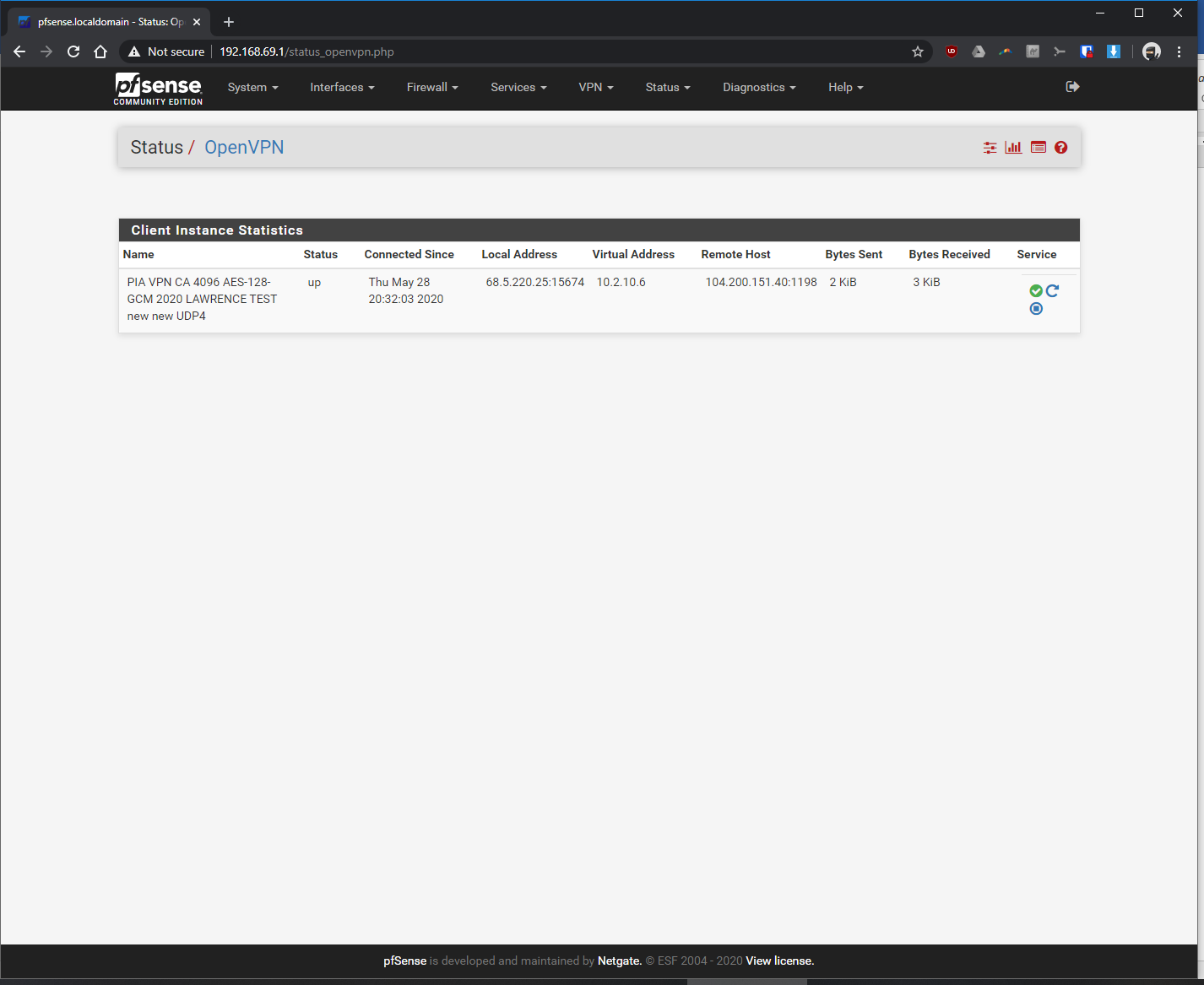
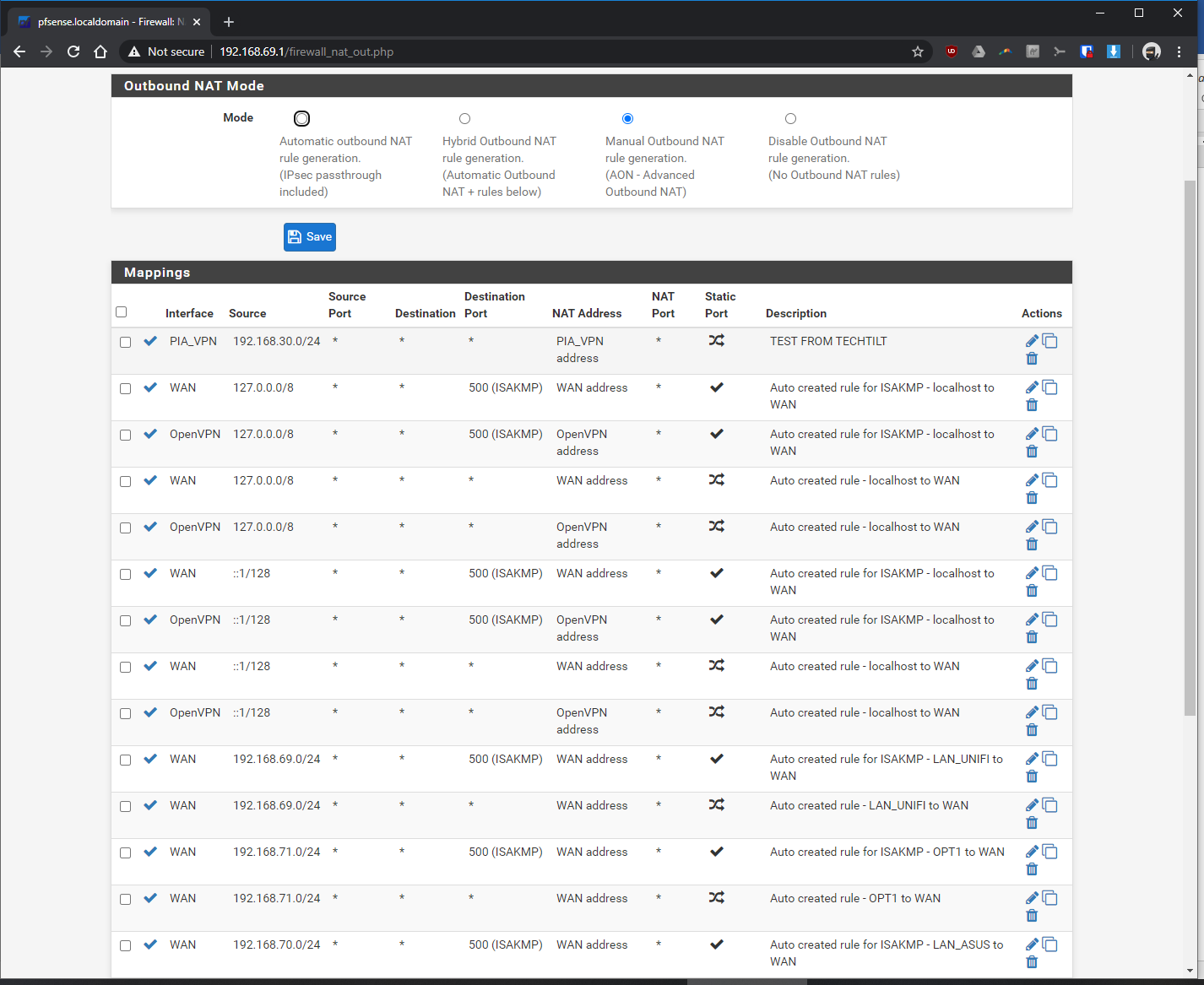
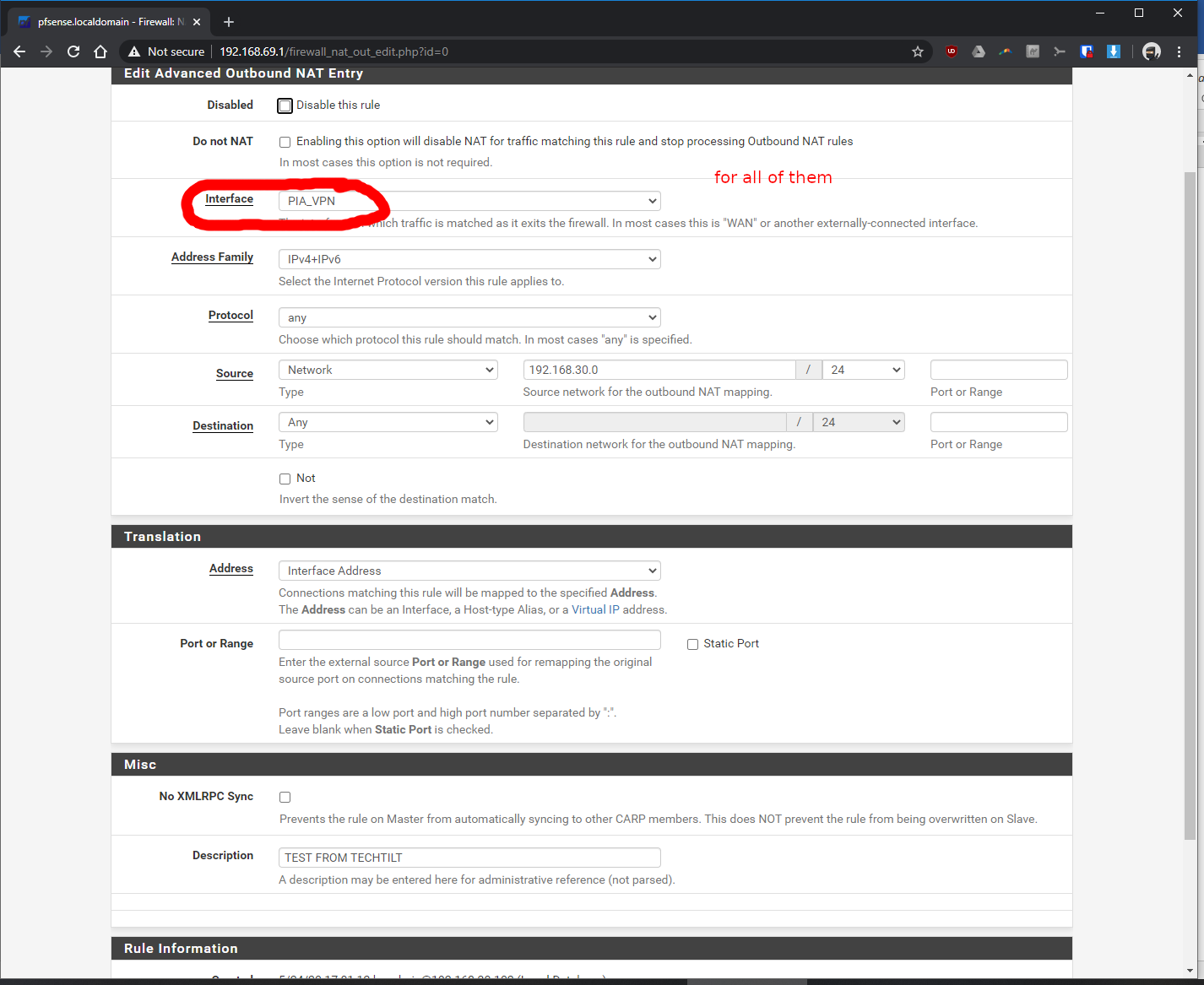
-
Using AES-128-GCM with hardware crypto set to none should be fastest there as long as the other end supports it and it looks like they do.
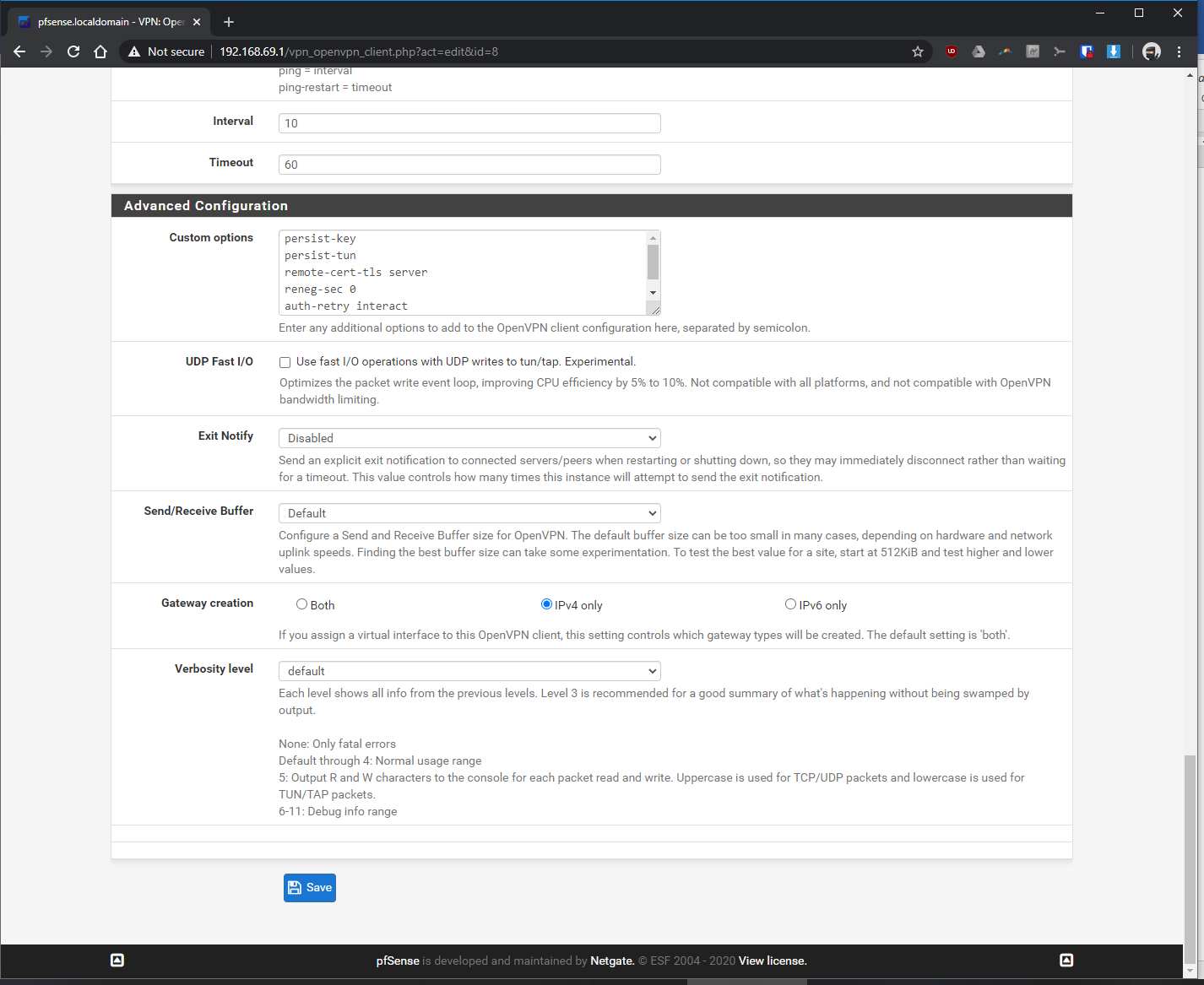
You should enable FastIO and set Send/Recv buffers to 512K which will probably be faster.You CPU is showing a maximum frequency of 1501MHz which indicates 'turbo mode', is that actually enabled though? You could try enabling powerd which is required for some CPUs to see full speed.
You need to run at the command line
top -aSHwhilst you're testing to see how the CPU is loaded. If it's hitting 100% on one core that's all you can get.Steve
-
i started from scratch with the fitlet2 and an old dell optiplex w/ 4 port intel NIC, using the same vpn settinsg. the dell optiplex is having no issues with VPN on. I think its either the fitlet2 j3455 cpu not liking the encryption or perhaps one of the settings you mentioned will fix it...
-
The J3455 is not powerful CPU but I would expect it to push more then 100Mbps of OpenVPN given a reasonable connection to the server.
You have to checktop -aSHthough to know what's limiting it.Steve