Easylist update fails. Expired Cert
-
@johnpoz Yeah. Packages are not an issue any more. The easylist downloads still fail with an expired cert. Not sure why that would be the case. Maybe more than one intermediate cert expired today?
Edited to add - This is from the log just a few minutes ago:
[ EasyList ] Downloading update . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... .. unknown http status code | 0 [ DNSBL_EasyList - EasyList ] Download FAIL [ 05/30/20 19:00:59 ] Firewall and/or IDS (Legacy mode only) are not blocking download. [ EasyList_Adware ] Downloading update . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... .. unknown http status code | 0 [ DNSBL_EasyList - EasyList_Adware ] Download FAIL [ 05/30/20 19:01:15 ] Firewall and/or IDS (Legacy mode only) are not blocking download. [ EasyPrivacy ] Downloading update . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... . cURL Error: 60 SSL certificate problem: certificate has expired Retry in 5 seconds... .. unknown http status code | 0 [ DNSBL_EasyList - EasyPrivacy ] Download FAIL [ 05/30/20 19:01:31 ] Firewall and/or IDS (Legacy mode only) are not blocking download. Saving DNSBL database... completed -
You could change the State of the URL to Flex until the cert issue is fixed.
-
Please explain how downloading EasyList has anything to do with any of Netgate's servers?
Perhaps the download site is suffering something similar?
What are the specific URLs those lists are downloaded from?
-
curl https://easylist-downloads.adblockplus.org/easyprivacy.txt curl: (60) SSL certificate problem: certificate has expired More details here: https://curl.haxx.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the web page mentioned above. -
That is nothing Netgate can fix.
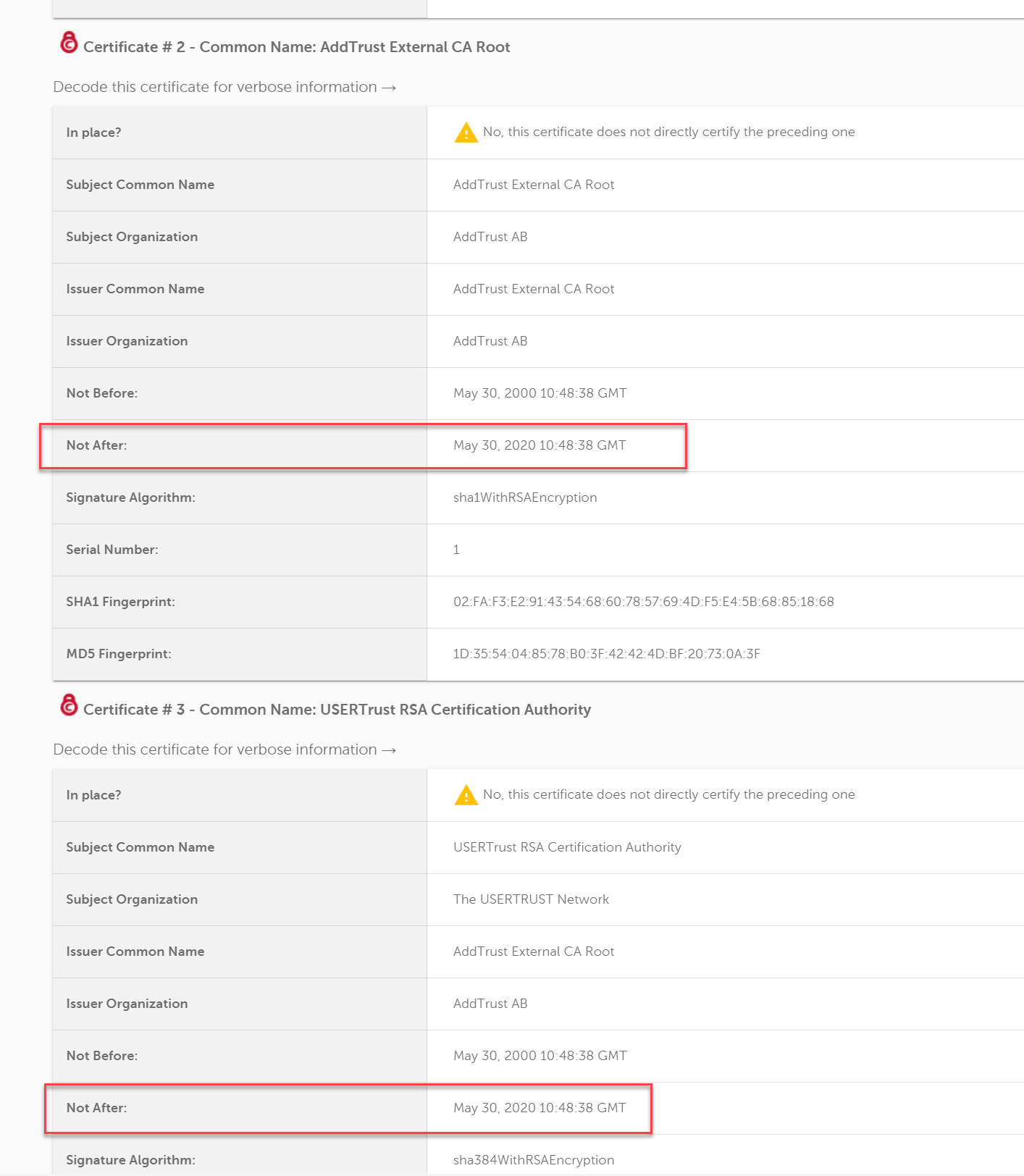
They need to remove the AddTrust certificate and the one linking USERTrust RSA Certification Authority to that from the chain being served by the server.
openssl s_client -connect easylist-downloads.adblockplus.org:443 -showcerts CONNECTED(00000003) depth=3 C = SE, O = AddTrust AB, OU = AddTrust External TTP Network, CN = AddTrust External CA Root verify error:num=10:certificate has expired notAfter=May 30 10:48:38 2020 GMT --- Certificate chain 0 s:/serialNumber=HRB 73508/jurisdictionC=DE/businessCategory=Private Organization/C=DE/postalCode=50825/ST=Nordrhein-Westfalen/L=K\xC3\xB6ln/street=Lichtstr. 25/O=Eyeo GmbH/OU=COMODO EV Multi-Domain SSL/CN=easylist-downloads.adblockplus.org i:/C=GB/ST=Greater Manchester/L=Salford/O=Sectigo Limited/CN=Sectigo RSA Extended Validation Secure Server CA -----BEGIN CERTIFICATE----- MIIIzDCCB7SgAwIBAgIQKT5prsOsgb2urn0sCoK5qjANBgkqhkiG9w0BAQsFADCB kTELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4G A1UEBxMHU2FsZm9yZDEYMBYGA1UEChMPU2VjdGlnbyBMaW1pdGVkMTkwNwYDVQQD EzBTZWN0aWdvIFJTQSBFeHRlbmRlZCBWYWxpZGF0aW9uIFNlY3VyZSBTZXJ2ZXIg Q0EwHhcNMTkwMzI3MDAwMDAwWhcNMjEwMzI2MjM1OTU5WjCCARAxEjAQBgNVBAUT CUhSQiA3MzUwODETMBEGCysGAQQBgjc8AgEDEwJERTEdMBsGA1UEDxMUUHJpdmF0 ZSBPcmdhbml6YXRpb24xCzAJBgNVBAYTAkRFMQ4wDAYDVQQREwU1MDgyNTEcMBoG A1UECBMTTm9yZHJoZWluLVdlc3RmYWxlbjEOMAwGA1UEBwwFS8O2bG4xFTATBgNV BAkTDExpY2h0c3RyLiAyNTESMBAGA1UEChMJRXllbyBHbWJIMSMwIQYDVQQLExpD T01PRE8gRVYgTXVsdGktRG9tYWluIFNTTDErMCkGA1UEAxMiZWFzeWxpc3QtZG93 bmxvYWRzLmFkYmxvY2twbHVzLm9yZzCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCC AgoCggIBALqVP6XzqkvRCzTzkxPyo4OFhF38xBUjHz8fVnMRbeV/v1iJNuRlnEuK GlHEkUW13+fJcrotdcq4VxK2qYkxED+ZGG+LEiECbdWp102NNd6ZyzFWqJfrHzOk xScMche89wVV0HZzif2Ovv9Gp4fg93XbcYE6WFJVhMbnDVqxE7YZuta2Y2nmw/Py YITCK9aR3Bs+KJtcoQIQR42DrObDHv5c4v0WKDxU7IbvxgXOFouK9hqny9+Aerbr w4ldHe+a6KwS+sj8T59xj06eEAvfIrWqF9wlZzToTWbb/DrFRpPPiJTLesJBvs/m IYs0v36yS90TzAP4w/QRDDyU4dIHPuLWG6q56XkoVd1/smJcDnobtqtc5g9vvRNt dud3MSpQqaefNdUO60pxtNyLneZDPnRzr7ODqWG08hZ2r5G2hdm26jHzCJH1DRnB JeThfC+F+hQt3BUVLf3pwgQaQ8Apod4wQeoBC62+nkMFhB+wjpDBG5Wxe08tlq1I MlLchr3lySJo8Uxbn49hTiVds685llLye6PdB5O6sWwRT9GDWnl0Z1I7SmT89Jj9 YgEJ0An1PmP08q+iWxTeeDivnrMThlAsFxKk9ZanPQ+nOkl1sm7Q4VDNd0w1NzFe FFJCaNUGg5UYewGYHX5BEbCwhiJBkJof2fTW2Tns8+W5VOzkMippAgMBAAGjggOc MIIDmDAfBgNVHSMEGDAWgBQsaf+AyYeQrjThtOdMk4WZQOmnsjAdBgNVHQ4EFgQU 7/DOijd/dBoSIldx6KR7244PCG0wDgYDVR0PAQH/BAQDAgWgMAwGA1UdEwEB/wQC MAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMEkGA1UdIARCMEAwNQYM KwYBBAGyMQECAQUBMCUwIwYIKwYBBQUHAgEWF2h0dHBzOi8vc2VjdGlnby5jb20v Q1BTMAcGBWeBDAEBMFYGA1UdHwRPME0wS6BJoEeGRWh0dHA6Ly9jcmwuc2VjdGln by5jb20vU2VjdGlnb1JTQUV4dGVuZGVkVmFsaWRhdGlvblNlY3VyZVNlcnZlckNB LmNybDCBhgYIKwYBBQUHAQEEejB4MFEGCCsGAQUFBzAChkVodHRwOi8vY3J0LnNl Y3RpZ28uY29tL1NlY3RpZ29SU0FFeHRlbmRlZFZhbGlkYXRpb25TZWN1cmVTZXJ2 ZXJDQS5jcnQwIwYIKwYBBQUHMAGGF2h0dHA6Ly9vY3NwLnNlY3RpZ28uY29tMGoG A1UdEQRjMGGCImVhc3lsaXN0LWRvd25sb2Fkcy5hZGJsb2NrcGx1cy5vcmeCHWVh c3lsaXN0LW1zaWUuYWRibG9ja3BsdXMub3Jnghxub3RpZmljYXRpb24uYWRibG9j a3BsdXMub3JnMIIBfwYKKwYBBAHWeQIEAgSCAW8EggFrAWkAdwDuS723dc5guuFC aR+r4Z5mow9+X7By2IMAxHuJeqj9ywAAAWnALndGAAAEAwBIMEYCIQCOd1XS5dul B7DB79z5xhiPH4LfvnV8sT41EaCy+lzXxwIhAKHkQriy3c2nY3jF14BY8OFLO1BC W/Ha2RLP7SENXFNRAHYAb1N2rDHwMRnYmQCkURX/dxUcEdkCwQApBo2yCJo32RMA AAFpwC535QAABAMARzBFAiEAr4TwleTsdE3/oDK3LFEs2RRVx/IRonoAiCnkukD+ ucMCIGn4XZiITZLr0a3qPTG6sf6VExqJiW+gYSVRadQl6+IZAHYAu9nfvB+KcbWT lCOXqpJ7RzhXlQqrUugakJZkNo4e0YUAAAFpwC53TAAABAMARzBFAiAWmd8O1Xtr 5li+rgRGASbp+fyRkBw7typDgkpTAqE1KAIhALPNRkFRpuH3Gi/hP5vikcBXvOvj bkTM9Kq8+BZnVIWmMA0GCSqGSIb3DQEBCwUAA4IBAQB0L4VlVSggmO/v2AClaqgJ KB1R7mhb4nglaZ/QPPmdsuX8L9szOLpe62HR/j9Ov4JChRrLSW4kpglaDO5PYSdf JwrdbqkKtloCdJxPK56I4JDAl+Bl8PPTZhRMBPPUbJUxwn0Ilsv3JCQw6Uye6up5 +3/RK2WS01dLXMbG0KmYaxq1tToySTSNU65rG66g7l11l4AwWCKlznbLmB7uTbDv tWH9FqFHjVpLAJ5AIIxnkBGvAYHjU3+/43VCqytJMVljbGAtmQOsb4A/bH1CxpSt NmcV9lm4kab9rh8kan8vs3LZxLofPWLNVIgZ+d0NSuk3Qc8PyFOMBqS5rFGBakDH -----END CERTIFICATE----- 1 s:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root -----BEGIN CERTIFICATE----- MIIENjCCAx6gAwIBAgIBATANBgkqhkiG9w0BAQUFADBvMQswCQYDVQQGEwJTRTEU MBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFkZFRydXN0IEV4dGVybmFs IFRUUCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBFeHRlcm5hbCBDQSBSb290 MB4XDTAwMDUzMDEwNDgzOFoXDTIwMDUzMDEwNDgzOFowbzELMAkGA1UEBhMCU0Ux FDASBgNVBAoTC0FkZFRydXN0IEFCMSYwJAYDVQQLEx1BZGRUcnVzdCBFeHRlcm5h bCBUVFAgTmV0d29yazEiMCAGA1UEAxMZQWRkVHJ1c3QgRXh0ZXJuYWwgQ0EgUm9v dDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALf3GjPm8gAELTngTlvt H7xsD821+iO2zt6bETOXpClMfZOfvUq8k+0DGuOPz+VtUFrWlymUWoCwSXrbLpX9 uMq/NzgtHj6RQa1wVsfwTz/oMp50ysiQVOnGXw94nZpAPA6sYapeFI+eh6FqUNzX mk6vBbOmcZSccbNQYArHE504B4YCqOmoaSYYkKtMsE8jqzpPhNjfzp/haW+710LX a0Tkx63ubUFfclpxCDezeWWkWaCUN/cALw3CknLa0Dhy2xSoRcRdKn23tNbE7qzN E0S3ySvdQwAl+mG5aWpYIxG3pzOPVnVZ9c0p10a3CitlttNCbxWyuHv77+ldU9U0 WicCAwEAAaOB3DCB2TAdBgNVHQ4EFgQUrb2YejS0Jvf6xCZU7wO94CTLVBowCwYD VR0PBAQDAgEGMA8GA1UdEwEB/wQFMAMBAf8wgZkGA1UdIwSBkTCBjoAUrb2YejS0 Jvf6xCZU7wO94CTLVBqhc6RxMG8xCzAJBgNVBAYTAlNFMRQwEgYDVQQKEwtBZGRU cnVzdCBBQjEmMCQGA1UECxMdQWRkVHJ1c3QgRXh0ZXJuYWwgVFRQIE5ldHdvcmsx IjAgBgNVBAMTGUFkZFRydXN0IEV4dGVybmFsIENBIFJvb3SCAQEwDQYJKoZIhvcN AQEFBQADggEBALCb4IUlwtYj4g+WBpKdQZic2YR5gdkeWxQHIzZlj7DYd7usQWxH YINRsPkyPef89iYTx4AWpb9a/IfPeHmJIZriTAcKhjW88t5RxNKWt9x+Tu5w/Rw5 6wwCURQtjr0W4MHfRnXnJK3s9EK0hZNwEGe6nQY1ShjTK3rMUUKhemPR5ruhxSvC Nr4TDea9Y355e6cJDUCrat2PisP29owaQgVR1EX1n6diIWgVIEM8med8vSTYqZEX c4g/VhsxOBi0cQ+azcgOno4uG+GMmIPLHzHxREzGBHNJdmAPx/i9F4BrLunMTA5a mnkPIAou1Z5jJh5VkpTYghdae9C8x49OhgQ= -----END CERTIFICATE----- 2 s:/C=US/ST=New Jersey/L=Jersey City/O=The USERTRUST Network/CN=USERTrust RSA Certification Authority i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root -----BEGIN CERTIFICATE----- MIIFdzCCBF+gAwIBAgIQE+oocFv07O0MNmMJgGFDNjANBgkqhkiG9w0BAQwFADBv MQswCQYDVQQGEwJTRTEUMBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFk ZFRydXN0IEV4dGVybmFsIFRUUCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBF eHRlcm5hbCBDQSBSb290MB4XDTAwMDUzMDEwNDgzOFoXDTIwMDUzMDEwNDgzOFow gYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpOZXcgSmVyc2V5MRQwEgYDVQQHEwtK ZXJzZXkgQ2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMS4wLAYD VQQDEyVVU0VSVHJ1c3QgUlNBIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MIICIjAN BgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAgBJlFzYOw9sIs9CsVw127c0n00yt UINh4qogTQktZAnczomfzD2p7PbPwdzx07HWezcoEStH2jnGvDoZtF+mvX2do2NC tnbyqTsrkfjib9DsFiCQCT7i6HTJGLSR1GJk23+jBvGIGGqQIjy8/hPwhxR79uQf jtTkUcYRZ0YIUcuGFFQ/vDP+fmyc/xadGL1RjjWmp2bIcmfbIWax1Jt4A8BQOujM 8Ny8nkz+rwWWNR9XWrf/zvk9tyy29lTdyOcSOk2uTIq3XJq0tyA9yn8iNK5+O2hm AUTnAU5GU5szYPeUvlM3kHND8zLDU+/bqv50TmnHa4xgk97Exwzf4TKuzJM7UXiV Z4vuPVb+DNBpDxsP8yUmazNt925H+nND5X4OpWaxKXwyhGNVicQNwZNUMBkTrNN9 N6frXTpsNVzbQdcS2qlJC9/YgIoJk2KOtWbPJYjNhLixP6Q5D9kCnusSTJV882sF qV4Wg8y4Z+LoE53MW4LTTLPtW//e5XOsIzstAL81VXQJSdhJWBp/kjbmUZIO8yZ9 HE0XvMnsQybQv0FfQKlERPSZ51eHnlAfV1SoPv10Yy+xUGUJ5lhCLkMaTLTwJUdZ +gQek9QmRkpQgbLevni3/GcV4clXhB4PY9bpYrrWX1Uu6lzGKAgEJTm4Diup8kyX HAc/DVL17e8vgg8CAwEAAaOB9DCB8TAfBgNVHSMEGDAWgBStvZh6NLQm9/rEJlTv A73gJMtUGjAdBgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rIDZsswDgYDVR0PAQH/ BAQDAgGGMA8GA1UdEwEB/wQFMAMBAf8wEQYDVR0gBAowCDAGBgRVHSAAMEQGA1Ud HwQ9MDswOaA3oDWGM2h0dHA6Ly9jcmwudXNlcnRydXN0LmNvbS9BZGRUcnVzdEV4 dGVybmFsQ0FSb290LmNybDA1BggrBgEFBQcBAQQpMCcwJQYIKwYBBQUHMAGGGWh0 dHA6Ly9vY3NwLnVzZXJ0cnVzdC5jb20wDQYJKoZIhvcNAQEMBQADggEBAJNl9jeD lQ9ew4IcH9Z35zyKwKoJ8OkLJvHgwmp1ocd5yblSYMgpEg7wrQPWCcR23+WmgZWn RtqCV6mVksW2jwMibDN3wXsyF24HzloUQToFJBv2FAY7qCUkDrvMKnXduXBBP3zQ YzYhBx9G/2CkkeFnvN4ffhkUyWNnkepnB2u0j4vAbkN9w6GAbLIevFOFfdyQoaS8 Le9Gclc1Bb+7RrtubTeZtv8jkpHGbkD4jylW6l/VXxRTrPBPYer3IsynVgviuDQf Jtl7GQVoP7o81DgGotPmjw7jtHFtQELFhLRAlSv0ZaBIefYdgWOWnU914Ph85I6p 0fKtirOMxyHNwu8= -----END CERTIFICATE----- 3 s:/C=GB/ST=Greater Manchester/L=Salford/O=Sectigo Limited/CN=Sectigo RSA Extended Validation Secure Server CA i:/C=US/ST=New Jersey/L=Jersey City/O=The USERTRUST Network/CN=USERTrust RSA Certification Authority -----BEGIN CERTIFICATE----- MIIGNDCCBBygAwIBAgIQKE45wUs4bYiccpnljNBaVzANBgkqhkiG9w0BAQwFADCB iDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0pl cnNleSBDaXR5MR4wHAYDVQQKExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNV BAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTgx MTAyMDAwMDAwWhcNMzAxMjMxMjM1OTU5WjCBkTELMAkGA1UEBhMCR0IxGzAZBgNV BAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UEBxMHU2FsZm9yZDEYMBYGA1UE ChMPU2VjdGlnbyBMaW1pdGVkMTkwNwYDVQQDEzBTZWN0aWdvIFJTQSBFeHRlbmRl ZCBWYWxpZGF0aW9uIFNlY3VyZSBTZXJ2ZXIgQ0EwggEiMA0GCSqGSIb3DQEBAQUA A4IBDwAwggEKAoIBAQCaoslYBiqFev0Yc4TXPa0s9oliMcn9VaENfTUK4GVT7niB QXxC6Mt8kTtvyr5lU92hDQDh2WDPQsZ7oibh75t2kowT3z1S+Sy1GsUDM4NbdOde orcmzFm/b4bwD4G/G+pB4EX1HSfjN9eT0Hje+AGvCrd2MmnxJ+Yymv9BH9OB65jK rUO9Na4iHr48XWBDFvzsPCJ11Uioof6dRBVp+Lauj88Z7k2X8d606HeXn43h6acp LLURWyqXM0CrzedVWBzuXKuBEaqD6w/1VpLJvSU+wl3ScvXSLFp82DSRJVJONXWl dp9gjJioPGRByeZw11k3galbbF5gFK9xSnbDx29LAgMBAAGjggGNMIIBiTAfBgNV HSMEGDAWgBRTeb9aqitKz1SA4dibwJ3ysgNmyzAdBgNVHQ4EFgQULGn/gMmHkK40 4bTnTJOFmUDpp7IwDgYDVR0PAQH/BAQDAgGGMBIGA1UdEwEB/wQIMAYBAf8CAQAw HQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMDoGA1UdIAQzMDEwLwYEVR0g ADAnMCUGCCsGAQUFBwIBFhlodHRwczovL2Nwcy51c2VydHJ1c3QuY29tMFAGA1Ud HwRJMEcwRaBDoEGGP2h0dHA6Ly9jcmwudXNlcnRydXN0LmNvbS9VU0VSVHJ1c3RS U0FDZXJ0aWZpY2F0aW9uQXV0aG9yaXR5LmNybDB2BggrBgEFBQcBAQRqMGgwPwYI KwYBBQUHMAKGM2h0dHA6Ly9jcnQudXNlcnRydXN0LmNvbS9VU0VSVHJ1c3RSU0FB ZGRUcnVzdENBLmNydDAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AudXNlcnRydXN0 LmNvbTANBgkqhkiG9w0BAQwFAAOCAgEAQ4AzPxVypLyy3IjUUmVl7FaxrHsXQq2z Zt2gKnHQShuA+5xpRPNndjvhHk4D08PZXUe6Im7E5knqxtyl5aYdldb+HI/7f+zd W/1ub2N4Vq4ZYUjcZ1ECOFK7Z2zoNicDmU+Fe/TreXPuPsDicTG/tMcWEVM558OQ TJkB2LK3ZhGukWM/RTMRcRdXaXOX8Lh0ylzRO1O0ObXytvOFpkkkD92HGsfS06i7 NLDPJEeZXqzHE5Tqj7VSAj+2luwfaXaPLD8lQEVci8xmsPGOn0mXE1ZzsChEPhVq FYQUsbiRJRhidKauhd+G2CkRTcR5fpsuz+iStB9s5Fks9lKoXnn0hv78VYjvR78C Cvj5FW/ounHjWTWMb3il9S5ngbFGcelB1l/MQkR63+1ybdi2OpjNWJCftxOWUpkC xaRdnOnSj7GQY0NLn8Gtq9FcSZydtkVgXpouSFZkXNS/MYwbcCCcRKBbrk8ss0SI Xg1gTURjh9VP1OHm0OktYcUw9e90wHIDn7h0qA+bWOsZquSRzT4s2crF3ZSA3tuV /UJ33mjdVO8wBD8aI5y10QreSPJvZHHNDyCmoyjXvNhR+u3arXUoHWxO+MZBeXbi iF7Nwn/IEmQvWBW8l6D26CXIavcY1kAJcfyzHkrPbLo+fAOa/KFl3lIU+0biEVNk Q9zXE6hC6X4= -----END CERTIFICATE----- --- Server certificate subject=/serialNumber=HRB 73508/jurisdictionC=DE/businessCategory=Private Organization/C=DE/postalCode=50825/ST=Nordrhein-Westfalen/L=K\xC3\xB6ln/street=Lichtstr. 25/O=Eyeo GmbH/OU=COMODO EV Multi-Domain SSL/CN=easylist-downloads.adblockplus.org issuer=/C=GB/ST=Greater Manchester/L=Salford/O=Sectigo Limited/CN=Sectigo RSA Extended Validation Secure Server CA --- No client certificate CA names sent Peer signing digest: SHA512 Server Temp Key: ECDH, P-256, 256 bits --- SSL handshake has read 7273 bytes and written 433 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 4096 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: CE47B9842B7DC1A7151565CF410CF16D442DC368E08EC3FF156D43E1E068E963 Session-ID-ctx: Master-Key: 9512999008F57A6F33F75F824A4C3AD0562E066114AA6D7923DB4F4E587EA0BFD81C0D7EBFE30FEC6B93B66134EB7669 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 300 (seconds) TLS session ticket: 0000 - a0 af 7f a9 e6 37 0b 1c-0c dc a3 0d 6d 91 2e 05 .....7......m... 0010 - c3 fc 7e 6e b8 8e 4f 79-d4 c8 3f 37 92 0c 8c 46 ..~n..Oy..?7...F 0020 - 9f 02 9b 2f 9f b8 6d af-12 55 f2 4b 60 5d f4 72 .../..m..U.K`].r 0030 - 9d a9 e7 a4 bf 14 10 a8-85 d8 b0 54 cd 81 df d6 ...........T.... 0040 - 56 ca ab 6e ca 69 f0 7e-c9 82 7f 81 91 07 5e 84 V..n.i.~......^. 0050 - 01 65 c5 5e fe de 8e d9-d5 eb 98 fc a7 07 6e 40 .e.^..........n@ 0060 - f1 33 0c 0e 5a 2b 3e 3b-d3 4e 23 3f d7 9a 63 5f .3..Z+>;.N#?..c_ 0070 - 53 73 cb e2 81 35 7c dd-91 f7 0a 17 3f 85 e6 65 Ss...5|.....?..e 0080 - c4 25 cc 7e 58 7f 71 9f-e1 06 62 36 50 15 94 0b .%.~X.q...b6P... 0090 - 90 ee 85 e4 be 78 50 e5-15 dd 5b 46 74 83 d7 93 .....xP...[Ft... 00a0 - 60 28 06 55 52 ec a4 53-38 4e a7 a3 0c d9 02 40 `(.UR..S8N.....@ Start Time: 1590883108 Timeout : 300 (sec) Verify return code: 10 (certificate has expired) --- -
@RonpfS how come I don’t get a similar error when navigating to the list via my browser?
-
Because different libraries treat things differently.
Based on what I saw today, some libraries will ignore CA's presented by the server in the chain and use the CAs in their trusted store instead if they have a match. Those will continue to work because they do not follow the validation chain to the expired AddTrust External CA Root CA.
The way pfSense's library apparently works is it will use the CAs as presented by the server.
The bottom line is the server is misconfigured and is sending an expired CA in its certificate chain.
-
@Derelict OK. Easylist needs to update their certs. Good to know were the fault is. That's helpful.
The aggressive posture is, however, not helpful. If I could explain how downloading easylists has anything to do with Netgate's servers I would not have posted the question.
-
The list downloaded with Flex State :
[ EasyList_Adware ] Downloading update . cURL Error: 60 [ ! ] Downgrading SSL settings (Flex) . 200 OK. ---------------------------------------------------------------------- Orig. Unique # Dups # White # TOP1M Final ---------------------------------------------------------------------- 100 100 1 0 0 99 ---------------------------------------------------------------------- -
@jwj Aggressive? Man. How about pointed and factual. I was asking because I personally have no idea how Easylist works or how you have your node/Aliases/pfBlocker configured.
-
@Derelict Yup. And sarcastic. How about: "That's all server side, nothing you or we can do from this end." That would be pointed and factual. You asked because you knew damn well it had nothing to do with Netgate servers. Sorry if you found the question too stupid to answer as an adult. My bad for expecting an adult reply.
-
I didn't know what servers were in question until @RonpfS answered with specifics. I had a pretty good idea it wasn't going to be a netgate server but I did not know for sure. Sorry I offended your delicate sensibilities by providing an immediate, factual diagnosis of the exact problem you were asking about. Please forgive me for asking for additional, specific details.
-
@jwj Here's an easy way to see the issues with the EasyList SSL Cert chain: Just navigate to this site:
This is NOT a Netgate issue, but a problem with server hosting the EasyList txt files. EasyList cert has two CAs that expired today.
-
@RonpfS said in Easylist update fails. Expired Cert:
You could change the State of the URL to Flex until the cert issue is fixed.
Could you explain what a switch from ON to FLEX does? I could not find documentation on this. Thank you.
-
I am puzzled. When I go to https://easylist-downloads.adblockplus.org/easyprivacy.txt with my browser and then check the cert, I get an expiration date of 3/26/21, which is well into the future. Not sure why pfBlockerNG reports an expired certificate. Does the URL access by pfBlockerNG differ from the above?
-
@revengineer Did you click on the
Flex: Downgrade the SSL Connection (Not Recommended)
-
@RonpfS said in Easylist update fails. Expired Cert:
@revengineer Did you click on the
Flex: Downgrade the SSL Connection (Not Recommended)
Thanks for the explanation.
Fortunately, a forced reload seems to have fixed the issue now.EDIT: Not sure what led be to believe this is fixed. It is not, the issue remains. I understand nothing the pfsense team or package developer can do about.
-
@costanzo I tried emailing and contacting them via twitter about their cert issue.
Haven't heard back... Does anyone know how to reach them?
For twitter I used: @AdblockPlus
For email I used: info@eyeo.com -
Hi All,
First time user, so please be gentle with me!I think this article describes the problem quite well - especially the
Cross-signingsectionSo, to fix it, I deleted the old CA from the
/usr/local/share/certs/ca-root-nss.crtfile (lines 423-512 in my version), as described in theWhat to do?section in that link aboveHTH
-
@jimmythedog said in Easylist update fails. Expired Cert:
Hi All,
First time user, so please be gentle with me!I think this article describes the problem quite well - especially the
Cross-signingsectionSo, to fix it, I deleted the old CA from the
/usr/local/share/certs/ca-root-nss.crtfile (lines 423-512 in my version), as described in theWhat to do?section in that link aboveHTH
I have done what you purpose and I can confirm that it works!
Thanks,
fireodo