Attaching /24 public IPs to make them usable by hosts behind firewall
-
Hi guys,
I've got the latest version of PFsense installed on XG-1537.
I've got it configured to use the transport IP provided to us by our datacenter (/29), but I also want to attach a separate /24 block of public IPs they gave us. The /24 block would be used by machines to host web sites and various services, so they must be accessible from the public internet.
I added them as "Virtual IP Address" under Firewall => Virtual IPs. I had to select "Other" because IP alias didn't work.
Is this the right way to attach these extra /24 IPs to the router or am I doing this wrong?
Thanks!
Luca -
It depends on whether they are routed to you on your address on the /29 (the right way) or if they are a secondary interfaces subnet on the WAN interface (the wrong, stupid way). Based on what you have said, it sounds like they are routed, which is good.
If they are routed to you you can do whatever you want with them.
You can number an inside interface with the /24 (or a subnet of it) and just place the servers on that inside network with public IP addresses on them.
You will want to exclude that inside network from NAT if you choose to go that way.
-
^ exactly... If was me.. I would subnet that /24 down to sizes you need for different vlans you put behind pfsense.. Reserving at least a small subnet say a /29 or /28 for use as vips, etc.
If you use routed subnets, no need to worry about port forwarding - you just allow whatever traffic you need via straight up firewall rules.
But if they are using a /29 transit already - you could prob just the remaining of that /29 for vips.
-
Thanks guys!
So here is the other twist.... I'm doing BGP peering with my datacenter and the /24 IPs are being announced by me to the peer, and by the peer out to the internet.
Does the above change how it's routed? (the stupid way vs smart way).
Also, I'm very new to pfsense so please excuse the stupidity of this question (switching from Juniper/Cisco)... What do you mean by "You can number an inside interface with the /24 (or a subnet of it) and just place the servers on that inside network with public IP addresses on them."? I've searched around on the interfaces section and don't see that as an obvious option.
Thanks!
Luca -
As long as the routes are advertised wouldn't actually matter if you or the isp does the advertising..
You just set the public IPs on the networks.. Lets say your network is 1.2.3.0/24
And you want a 2nd half /25 inside..
Just set 1.2.3.129/25 on some lan side interface... Make sure your not natting this network in your outbound nat settings.. You could do full manual, or just do hybrid, set the network you don't want to nat and click the do not nat checkbox
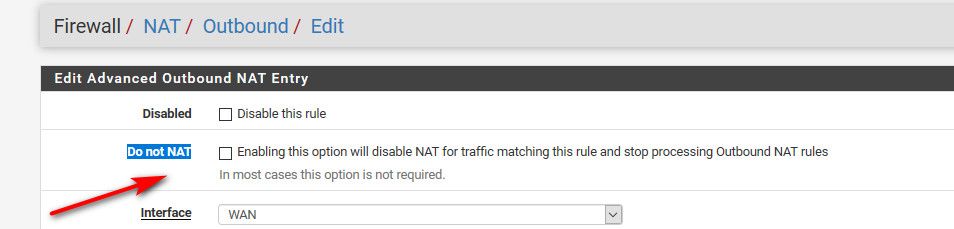
Then whatever traffic you want to allow into those IPs, just setup firewall rule on your wan to allow the traffic to whatever inside IP and or ports, etc. etc..
-
@johnpoz said in Attaching /24 public IPs to make them usable by hosts behind firewall:
As long as the routes are advertised wouldn't actually matter if you or the isp does the advertising..
You just set the public IPs on the networks.. Lets say your network is 1.2.3.0/24
And you want a 2nd half /25 inside..
Just set 1.2.3.129/25 on some lan side interface... Make sure your not natting this network in your outbound nat settings.. You could do full manual, or just do hybrid, set the network you don't want to nat and click the do not nat checkbox

Then whatever traffic you want to allow into those IPs, just setup firewall rule on your wan to allow the traffic to whatever inside IP and or ports, etc. etc..
Awesome. Thanks for the screenshot!
So I already have 192.168.1.1 as my lan gateway IP and DHCP running on the lan port. Can I still set the /24 here like you said or do I need to get rid of the DHCP+192.168.1.1 IP... Assuming I don't have to get rid of that DHCP address, WHERE do I go to set "Just set 1.2.3.129/25 on some lan side interface"?
Thanks!
-
You wouldn't want to run multiple layer 3s on the same layer 2... You would either change this network to be your public range you want, or setup a different network/vlan to be this public range.
-
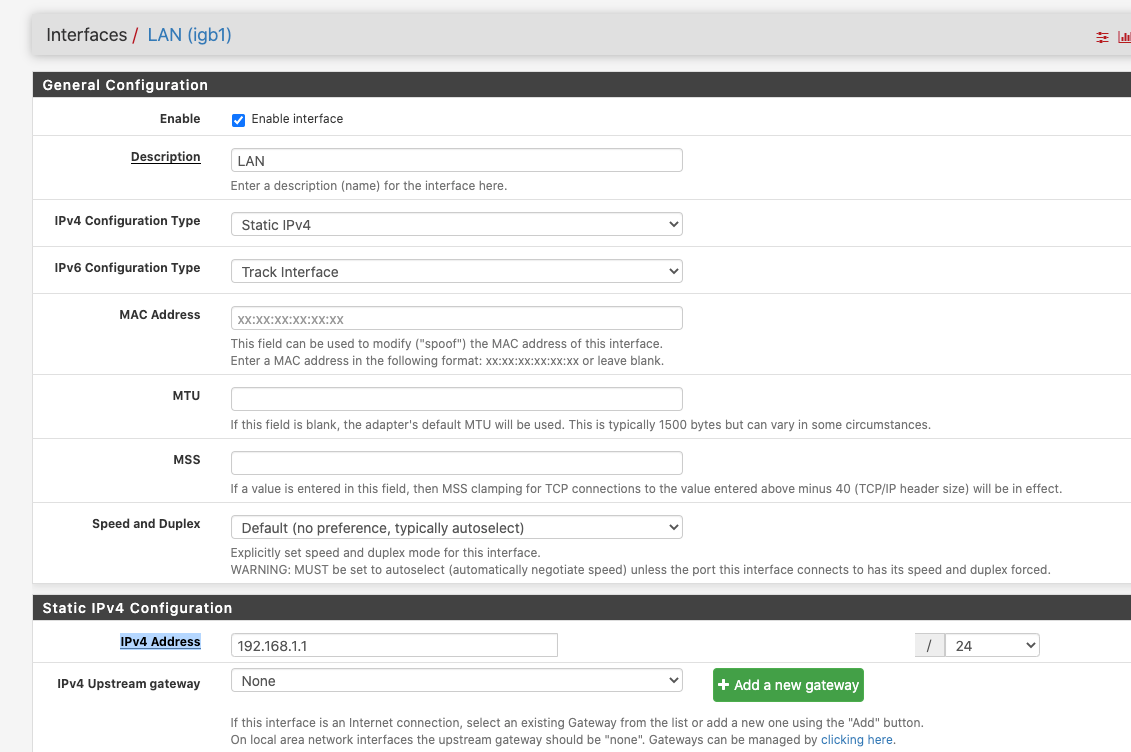
John,Ok. Great. So things are starting to make sense now.
Just so that I'm clear on what you just said...
#1. Change my current 192.168.1.1 Static LAN IPv4 Address to a x.x.x.1 from the /24 block as per screenshot.
#2. Setup a separate VLAN to handle DHCP using the old 192.168.1.1 subnet.Thanks!
-
Doesn't matter which way you do it.. Be it your routed is native or a vlan.. Or if you change this one or add the routed space.