Child-SA only one-way
-
Hi all
My first topic here, tell me if this is the wrong place or format.
I'm having a strange issue with a newly created IPsec tunnel. My pfSense Version is 2.4.5, the foreign endpoint is a Cisco Firewall.
I read up on https://docs.netgate.com/pfsense/en/latest/book/ipsec/ipsec-troubleshooting.html#tunnel-establishes-when-initiating-but-not-when-responding, but I couldn't figure out the misconfiguration yet. The configuration seems to match, see cisco config: config.txt
It goes as follows.
- status before bringing the connection up
# ipsec status Shunted Connections: bypasslan: 172.16.14.0/24|/0 === 172.16.14.0/24|/0 PASS Routed Connections: con3000{963}: ROUTED, TUNNEL, reqid 11 con3000{963}: 172.16.14.34/32|/0 172.16.14.35/32|/0 172.16.14.36/32|/0 172.16.14.37/32|/0 === 10.153.64.0/20|/0 Security Associations (0 up, 0 connecting): none- bringing the connection up, IKE_SA succeeds, CHILD_SA fails with TS_UNACCEPTABLE
# ipsec up con3000 initiating IKE_SA con3000[92] to 46.14.34.14 generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] sending packet: from 95.128.34.75[500] to 46.14.34.14[500] (464 bytes) received packet: from 46.14.34.14[500] to 95.128.34.75[500] (574 bytes) parsed IKE_SA_INIT response 0 [ SA KE No V V N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) V ] received Cisco Delete Reason vendor ID received Cisco Copyright (c) 2009 vendor ID received FRAGMENTATION vendor ID selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 authentication of '95.128.34.75' (myself) with pre-shared key establishing CHILD_SA con3000{965} generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] sending packet: from 95.128.34.75[500] to 46.14.34.14[500] (400 bytes) received packet: from 46.14.34.14[500] to 95.128.34.75[500] (160 bytes) parsed IKE_AUTH response 1 [ V IDr AUTH N(TS_UNACCEPT) ] authentication of '46.14.34.14' with pre-shared key successful IKE_SA con3000[92] established between 95.128.34.75[95.128.34.75]...46.14.34.14[46.14.34.14] scheduling reauthentication in 2525s maximum IKE_SA lifetime 3065s received TS_UNACCEPTABLE notify, no CHILD_SA built failed to establish CHILD_SA, keeping IKE_SA establishing connection 'con3000' failed- status after bringing the connection up
# ipsec status Shunted Connections: bypasslan: 172.16.14.0/24|/0 === 172.16.14.0/24|/0 PASS Routed Connections: con3000{963}: ROUTED, TUNNEL, reqid 11 con3000{963}: 172.16.14.34/32|/0 172.16.14.35/32|/0 172.16.14.36/32|/0 172.16.14.37/32|/0 === 10.153.64.0/20|/0 Security Associations (1 up, 0 connecting): con3000[92]: ESTABLISHED 2 minutes ago, 95.128.34.75[95.128.34.75]...46.14.34.14[46.14.34.14]- after a ping is initiated from the other endpoint to 172.16.14.34 the CHILD_SA gets created (clog /var/log/ipsec.log)
Jun 8 11:27:12 fw-tbabs-01 charon: 05[NET] <con3000|92> received packet: from 46.14.34.14[500] to 95.128.34.75[500] (592 bytes) Jun 8 11:27:12 fw-tbabs-01 charon: 05[ENC] <con3000|92> parsed CREATE_CHILD_SA request 0 [ SA No KE TSi TSr ] Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> looking for a child config for 172.16.14.34/32|/0 === 10.153.64.240/32|/0 10.153.64.0/20|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> proposing traffic selectors for us: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> 172.16.14.34/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> 172.16.14.35/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> 172.16.14.36/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> 172.16.14.37/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> proposing traffic selectors for other: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> 10.153.64.0/20|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> candidate "con3000" with prio 5+7 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> found matching child config "con3000" with prio 12 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting proposal: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> no acceptable ENCRYPTION_ALGORITHM found Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting proposal: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> proposal matches Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> received proposals: ESP:AES_GCM_16_256/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/AES_CBC_192/AES_CBC_128/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_GCM_16_256/MODP_2048/NO_EXT_SEQ, ESP:AES_GCM_12_256/MODP_2048/NO_EXT_SEQ, ESP:AES_GCM_8_256/MODP_2048/NO_EXT_SEQ Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting traffic selectors for us: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 172.16.14.34/32|/0, received: 172.16.14.34/32|/0 => match: 172.16.14.34/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 172.16.14.35/32|/0, received: 172.16.14.34/32|/0 => no match Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 172.16.14.36/32|/0, received: 172.16.14.34/32|/0 => no match Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 172.16.14.37/32|/0, received: 172.16.14.34/32|/0 => no match Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting traffic selectors for other: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 10.153.64.0/20|/0, received: 10.153.64.240/32|/0 => match: 10.153.64.240/32|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> config: 10.153.64.0/20|/0, received: 10.153.64.0/20|/0 => match: 10.153.64.0/20|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> CHILD_SA con3000{966} state change: CREATED => INSTALLING Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> using AES_CBC for encryption Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> using HMAC_SHA2_256_128 for integrity Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> adding inbound ESP SA Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> SPI 0xc48473c5, src 46.14.34.14 dst 95.128.34.75 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> adding outbound ESP SA Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> SPI 0xc2c8931a, src 95.128.34.75 dst 46.14.34.14 Jun 8 11:27:12 fw-tbabs-01 charon: 05[IKE] <con3000|92> CHILD_SA con3000{966} established with SPIs c48473c5_i c2c8931a_o and TS 172.16.14.34/32|/0 === 10.153.64.0/20|/0 Jun 8 11:27:12 fw-tbabs-01 charon: 05[CHD] <con3000|92> CHILD_SA con3000{966} state change: INSTALLING => INSTALLED Jun 8 11:27:12 fw-tbabs-01 charon: 05[ENC] <con3000|92> generating CREATE_CHILD_SA response 0 [ N(ESP_TFC_PAD_N) SA No KE TSi TSr ] Jun 8 11:27:12 fw-tbabs-01 charon: 05[NET] <con3000|92> sending packet: from 95.128.34.75[500] to 46.14.34.14[500] (480 bytes)- status after creation
ipsec status Shunted Connections: bypasslan: 172.16.14.0/24|/0 === 172.16.14.0/24|/0 PASS Routed Connections: con3000{1}: ROUTED, TUNNEL, reqid 1 con3000{1}: 172.16.14.34/32|/0 172.16.14.35/32|/0 172.16.14.36/32|/0 172.16.14.37/32|/0 === 10.153.64.0/20|/0 Security Associations (1 up, 0 connecting): con3000[2]: ESTABLISHED 12 minutes ago, 95.128.34.75[95.128.34.75]...46.14.34.14[46.14.34.14] con3000{5}: INSTALLED, TUNNEL, reqid 2, ESP SPIs: cf2e3af4_i cd44d223_o con3000{5}: 172.16.14.34/32|/0 === 10.153.64.0/20|/0In conclusion, the CHILD_SA only gets created after a ping from the other endpoint, not if initiated from my end.
- A ping to one of the foreign IP's (a.e. 10.153.64.1) before the established tunnel does not work, only after establishing the tunnel.
- There is no route before nor after creating the CHILD_SA, see netstat below. As I understand this is some IPsec magic in the background that does routing
- Without established CHILD_SA, traffic from 172.16.14.34 does not pass enc0 interface and times out
Any idea what went wrong here? I see following proposal error when the remote gateway establishes, but then it matches anyway, so not sure thats the issue.
Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting proposal: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> no acceptable ENCRYPTION_ALGORITHM found Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> selecting proposal: Jun 8 11:27:12 fw-tbabs-01 charon: 05[CFG] <con3000|92> proposal matchesifconfig
em0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=209b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC> ether 00:1a:4a:02:02:45 hwaddr 00:1a:4a:02:02:45 inet6 fe80::21a:4aff:fe02:245%em0 prefixlen 64 scopeid 0x1 inet 95.128.34.75 netmask 0xffffffe0 broadcast 95.128.34.95 inet 95.128.34.77 netmask 0xffffffff broadcast 95.128.34.77 inet 95.128.34.79 netmask 0xffffffff broadcast 95.128.34.79 inet 95.128.34.84 netmask 0xffffffff broadcast 95.128.34.84 inet 95.128.34.85 netmask 0xffffffff broadcast 95.128.34.85 inet 95.128.34.66 netmask 0xffffffff broadcast 95.128.34.66 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active em1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=209b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC> ether 00:1a:4a:02:02:46 hwaddr 00:1a:4a:02:02:46 inet6 fe80::21a:4aff:fe02:246%em1 prefixlen 64 scopeid 0x2 inet 172.16.14.1 netmask 0xffffff00 broadcast 172.16.14.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active em2: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=209b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC> ether 00:1a:4a:02:02:48 hwaddr 00:1a:4a:02:02:48 inet6 fe80::21a:4aff:fe02:248%em2 prefixlen 64 scopeid 0x3 inet 192.168.0.1 netmask 0xffffff00 broadcast 192.168.0.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active enc0: flags=41<UP,RUNNING> metric 0 mtu 1536 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: enc lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x5 inet 127.0.0.1 netmask 0xff000000 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: lo pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync ovpns1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::21a:4aff:fe02:245%ovpns1 prefixlen 64 scopeid 0x8 inet 10.0.0.1 --> 10.0.0.2 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 24930netstat -r -n
Routing tables Internet: Destination Gateway Flags Netif Expire default 95.128.34.65 UGS em0 10.0.0.0/24 10.0.0.2 UGS ovpns1 10.0.0.1 link#8 UHS lo0 10.0.0.2 link#8 UH ovpns1 46.14.34.14 95.128.34.65 UGHS em0 95.128.34.64/27 link#1 U em0 95.128.34.66 link#1 UHS lo0 95.128.34.66/32 link#1 U em0 95.128.34.75 link#1 UHS lo0 95.128.34.77 link#1 UHS lo0 95.128.34.77/32 link#1 U em0 95.128.34.79 link#1 UHS lo0 95.128.34.79/32 link#1 U em0 95.128.34.84 link#1 UHS lo0 95.128.34.84/32 link#1 U em0 95.128.34.85 link#1 UHS lo0 95.128.34.85/32 link#1 U em0 127.0.0.1 link#5 UH lo0 172.16.14.0/24 link#2 U em1 172.16.14.1 link#2 UHS lo0 192.168.0.0/24 link#3 U em2 192.168.0.1 link#3 UHS lo0/var/etc/ipsec/ipsec.conf
# This file is automatically generated. Do not edit config setup uniqueids = yes conn bypasslan leftsubnet = 172.16.14.0/24 rightsubnet = 172.16.14.0/24 authby = never type = passthrough auto = route conn con3000 fragmentation = yes keyexchange = ikev2 reauth = yes forceencaps = no mobike = no rekey = yes installpolicy = yes type = tunnel dpdaction = restart dpddelay = 2s dpdtimeout = 12s closeaction = restart auto = route left = 95.128.34.75 right = 46.14.34.14 leftid = 95.128.34.75 ikelifetime = 3600s lifetime = 3600s ike = aes256-sha256-modp2048! esp = aes256-sha256-modp2048,aes256gcm128-sha256-modp2048,aes256gcm96-sha256-modp2048,aes256gcm64-sha256-modp2048! leftauth = psk rightauth = psk rightid = 46.14.34.14 rightsubnet = 10.153.64.0/20 leftsubnet = 172.16.14.34,172.16.14.35,172.16.14.36,172.16.14.37/var/etc/ipsec/strongswan.conf
# Automatically generated config file - DO NOT MODIFY. Changes will be overwritten. starter { load_warning = no config_file = /var/etc/ipsec/ipsec.conf } charon { # number of worker threads in charon threads = 16 ikesa_table_size = 32 ikesa_table_segments = 4 init_limit_half_open = 1000 install_routes = no load_modular = yes ignore_acquire_ts = yes cisco_unity = no syslog { identifier = charon # log everything under daemon since it ends up in the same place regardless with our syslog.conf daemon { ike_name = yes dmn = 1 mgr = 1 ike = 2 chd = 2 job = 1 cfg = 2 knl = 1 net = 1 asn = 1 enc = 1 imc = 1 imv = 1 pts = 1 tls = 1 esp = 1 lib = 1 } # disable logging under auth so logs aren't duplicated auth { default = -1 } } plugins { # Load defaults include /var/etc/ipsec/strongswan.d/charon/*.conf stroke { secrets_file = /var/etc/ipsec/ipsec.secrets } unity { load = no } curve25519 { load = yes } } } -
@oli
Hi
Try setting up phase-2 on both sides of the tunnel like this ( PFSense side)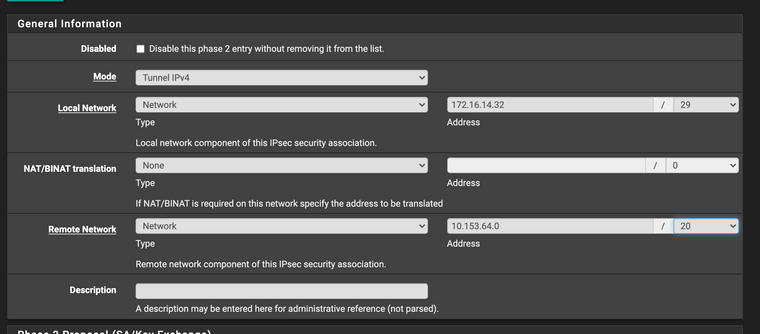
-
@Konstanti
Thanks for the reply, will do. But why would this work? -
@oli
Because only one SA will be created on both sides of the tunnel, and the system will set a trap (TS 172.16.14.32/29|/0 === 10.153.64.0/20|/0 ) that will get traffic from 172.16.14.34,172.16.14.35,172.16.14.36,172.16.14.37 to 10.153.64.0/20, and that traffic will go into the tunnel
-
@Konstanti
Ok, I'm curious if this will also fix the issue that I can not initiate. I'll keep you posted, thanks for the clarification. -
@oli
I see that when I connect , Cisco sends an error message
received TS_UNACCEPTABLE notify, no CHILD_SA builtThat's why I suggest creating one phase-2 instead of 4.
-
@Konstanti
Worked like a charm, thank you very much!
Do single adresses generally not work or just in this specific case?
How can i extend the official documentation with this? I found a couple of threads in the wild with the same error message but no working solutions as far as i can tell. -
@oli said in Child-SA only one-way:
Worked like a charm, thank you very much!
Do single adresses generally not work or just in this specific case?
How can i extend the official documentation with this? I found a couple of threads in the wild with the same error message but no working solutions as far as i can tell.I think there is a problem with the IPSec phase-2 settings on the Cisco side
If you can , show me the Cisco settings -
@Konstanti
I'll see what I can do.