stop pfsense showing as route
-
would it be this?
https://phil.lavin.me.uk/2013/04/how-to-disable-icmp-redirects-in-pfsense/
-
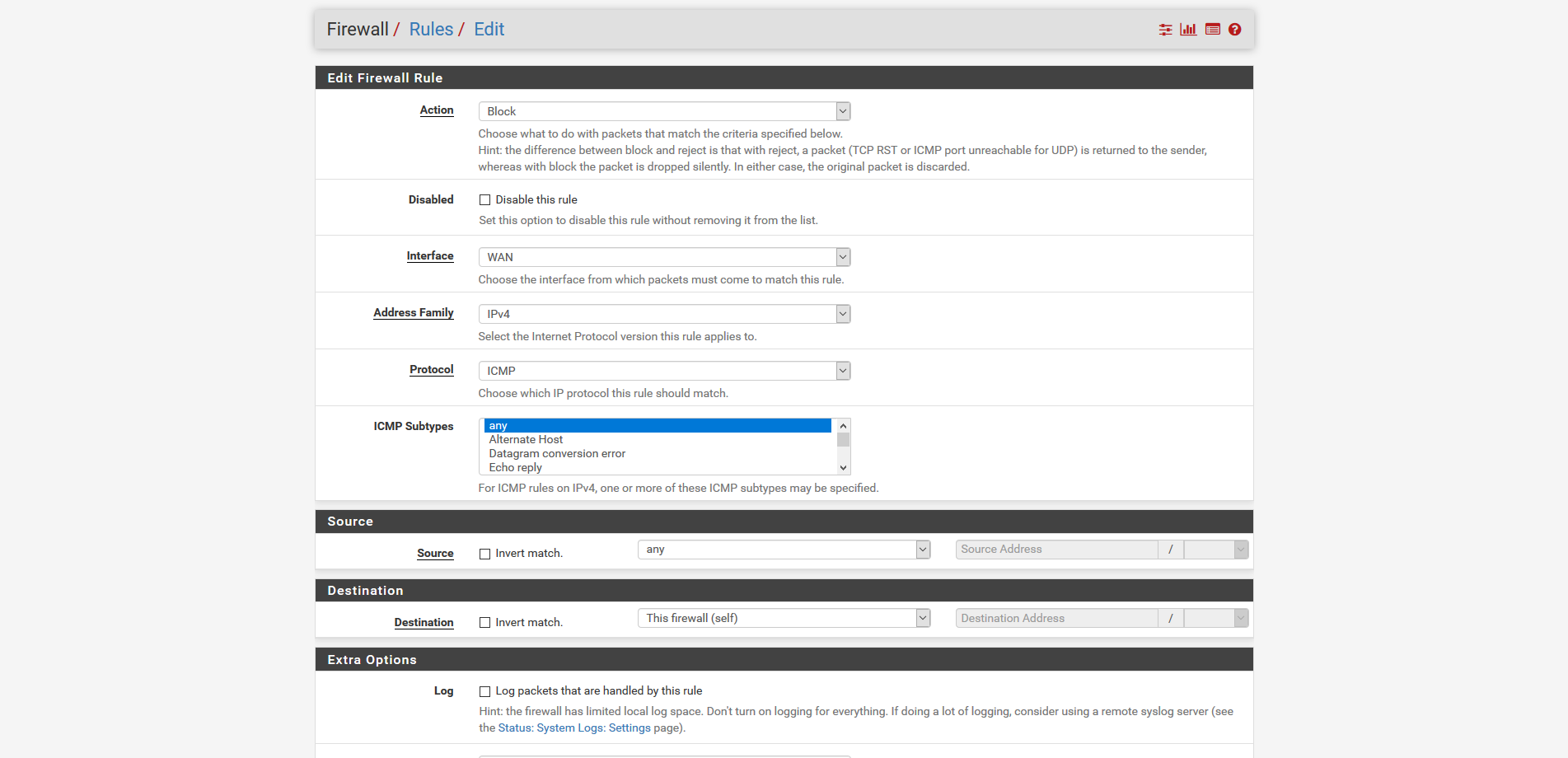
Your ICMP block rule is at the top isn't it ?
-
Yes very top
-
Where are you trying to block traceroutes from, if its your local network out the rule needs to be on the LAN interface.
-
Its WAN, its a public firewall for public IP's so has a WAN IP
-
I saw 'somewhere' that trace route could be ICMP based.
Normally, it's UDP based.@chrisjmuk : you want to hide your router from LAN based clients ?

You can not fear attacks from the inside. Unless you created that situation.
Only trusted clients should be connected to the LAN interface.
Everybody else goes on a another LAN network, called OPTx where x is a number.
These guys shouldn't be able to connect to pfSense, the GUI (port 443 or 80). They can just use '53', '67', '68' and '123' (if you want).
Attacks from the outside isn't possible. pfSense, out of the box, is rock solid. -
https://superuser.com/questions/355486/what-is-the-range-of-ports-that-is-usually-used-in-the-traceroute-command
Forgot it could use UDP.
-
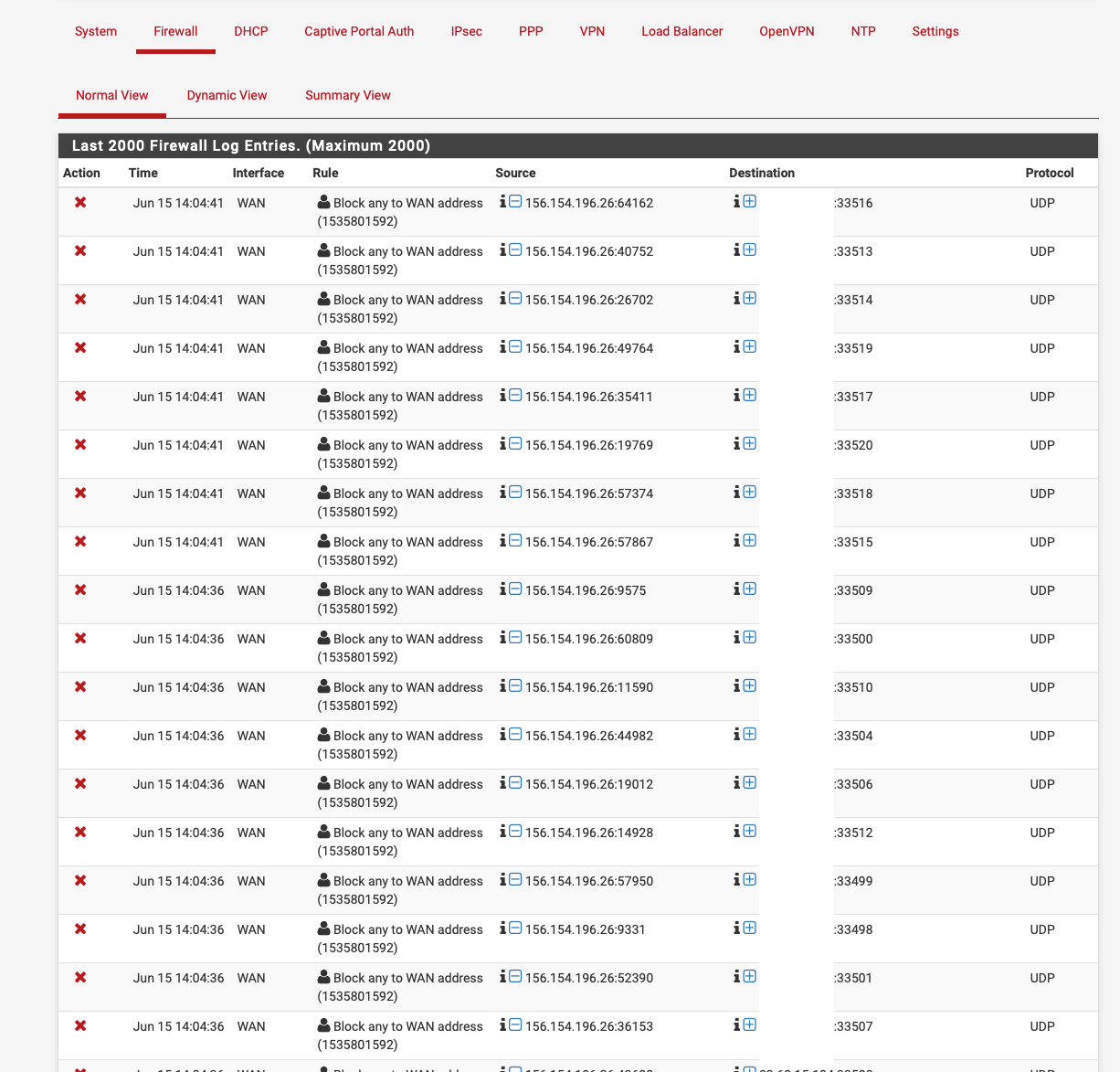
Thank, but that doesnt really help me blocking the trace, i set to udp and ports 33434 to 33534 and no luck, someone must of solved this issue before. surely
-
Do you have any floating rules, by default everything is blocked into the WAN interface.
-
https://www.ultratools.com/tools/traceRoute
-
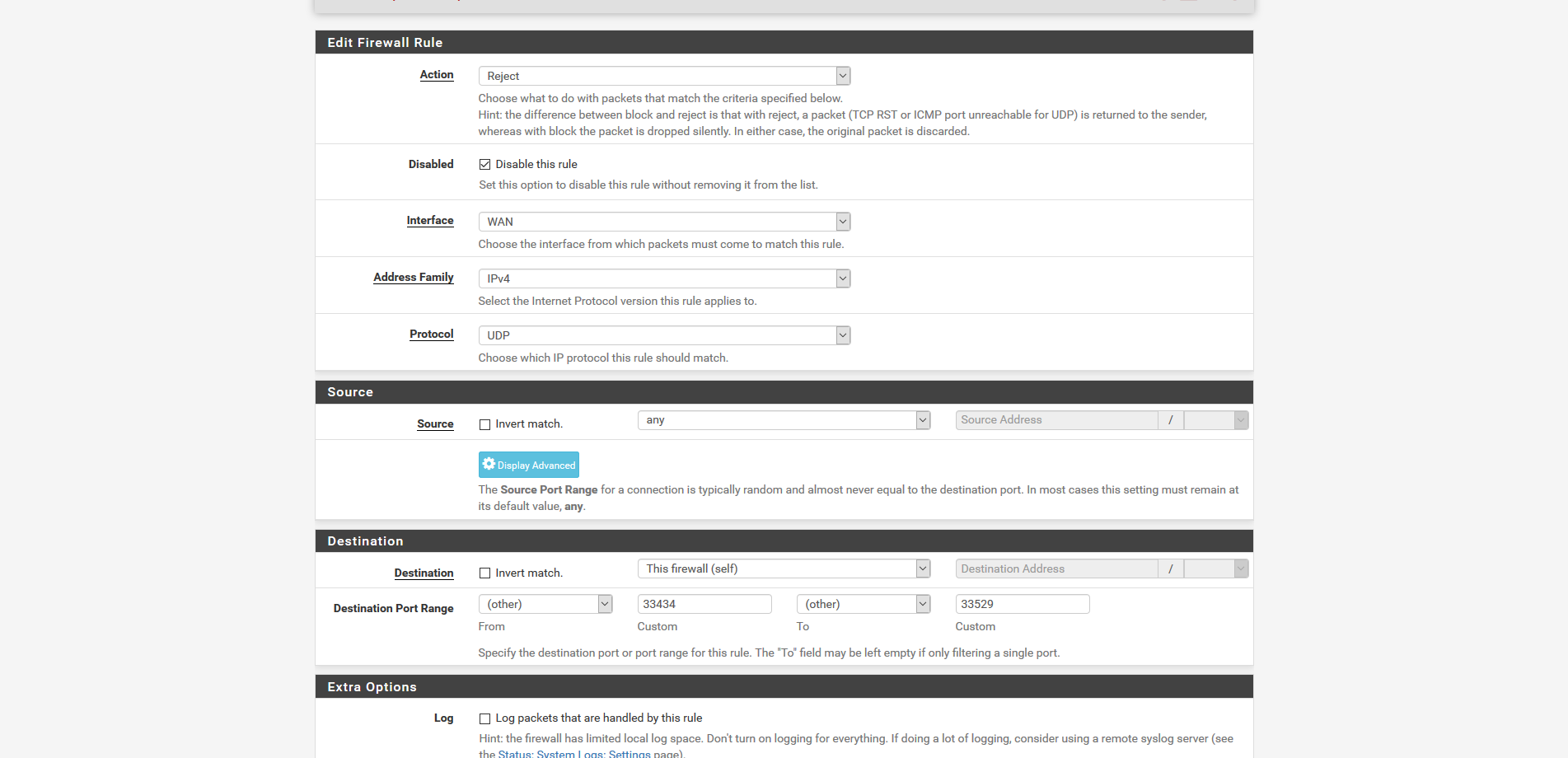
whats the entire port range you have? i have this as i said (i know rule is currently disabled in the screenshot but doesnt work enabled)
-
Post a screenshot of your WAN rules, as I said by default everything is blocked inbound on the WAN.
-
yep just posted, because its all public IP's it cant work as like that, if i block ICMP on everything in WAN the public IP's will no longer ping, so just setting to the firewall ip itself.
-
@chrisjmuk said in stop pfsense showing as route:
yep just posted, because its all public IP's it cant work as like that, if i block ICMP on everything in WAN the public IP's will no longer ping, so just setting to the firewall ip itself.
All your WAN rules.
-
i cant because of sensitive information. in the firewall and with ip's
-
Following this is the only thing I can suggest:-
https://docs.netgate.com/pfsense/en/latest/book/firewall/troubleshooting-firewall-rules.html
-
No luck, just blocked all UDP on the firewall ip and still traces.
-
Still don't know what trace-route you want to block.
From the inside, LAN, to, the outside ?
The other way around ? -
so tracing from outside of our network into a public ip in our DC so for example on the route
BGP Router
CORE Switch
pfSense Firewall ( Public IP)
Server (Public IP)trying to block the pfSense public ip from being traced, i can stop the normal icmp ping protocal but not the trace or an MTR
pfSense on WAN needs to be a public IP and our core switch ip routes to it to get route outwards to our BGP switch to know where its going as its in the BGP config, would not work as an internal ip because it has no route to the world.
-
@chrisjmuk said in stop pfsense showing as route:
trying to block the pfSense public ip from being traced,
That public IP is assigned to you - and known (to the public).
You can't hide an IP.
You can make it look like a black hole, by not answering to any out of state requests, which is what pfSense does when you install, it.The last router in front of pfSense knows what IP - the one used by you - is on what interface. If that one - yours - isn't replying when using trace route, they - the one that traces - still knows the path to you system up until the last router.
If you asked the organisation that gave you your IP's to remove them - that is : remove them from their routing tables, then your IP would vanish from the net, that's for sure. As will your entire connection to the net.
Btw : the trace route will end with your WAN IP, because the upstream router was telling so. It will not go beyond pfSense, because it also works as a firewall.
This (should be valid) if the IP's are RFC1918 - or public ones.