stop pfsense showing as route
-
https://www.ultratools.com/tools/traceRoute
-
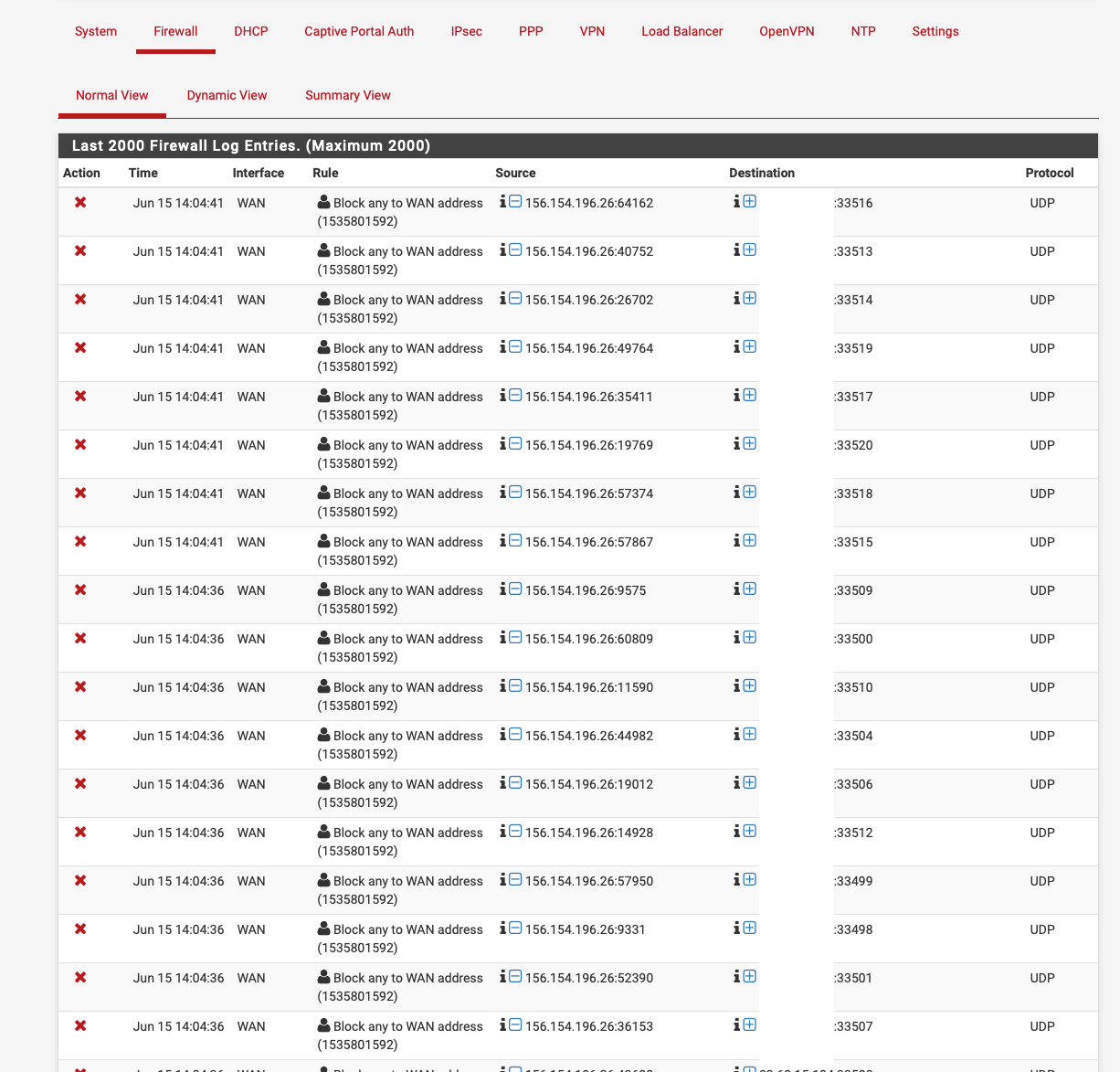
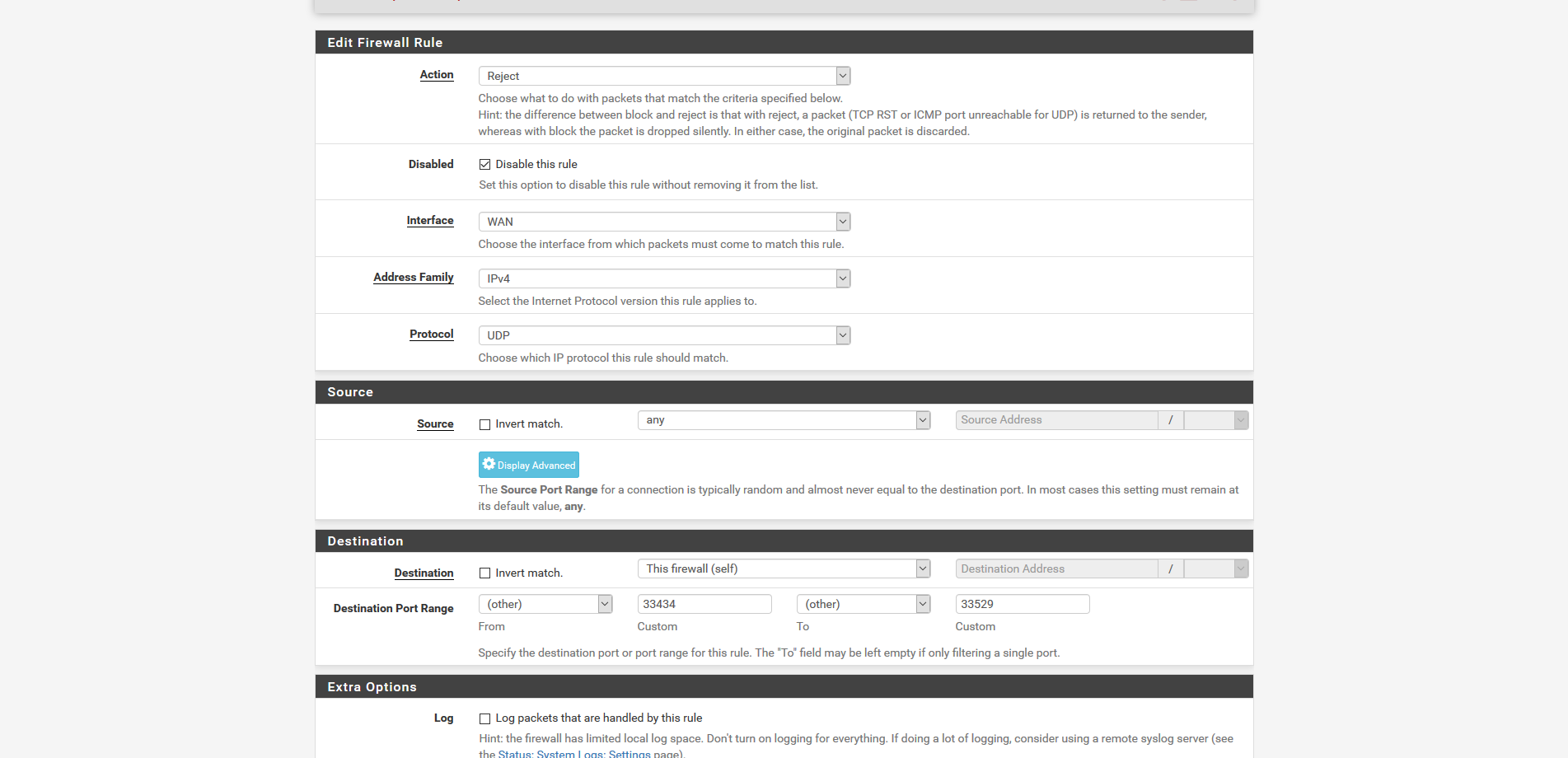
whats the entire port range you have? i have this as i said (i know rule is currently disabled in the screenshot but doesnt work enabled)
-
Post a screenshot of your WAN rules, as I said by default everything is blocked inbound on the WAN.
-
yep just posted, because its all public IP's it cant work as like that, if i block ICMP on everything in WAN the public IP's will no longer ping, so just setting to the firewall ip itself.
-
@chrisjmuk said in stop pfsense showing as route:
yep just posted, because its all public IP's it cant work as like that, if i block ICMP on everything in WAN the public IP's will no longer ping, so just setting to the firewall ip itself.
All your WAN rules.
-
i cant because of sensitive information. in the firewall and with ip's
-
Following this is the only thing I can suggest:-
https://docs.netgate.com/pfsense/en/latest/book/firewall/troubleshooting-firewall-rules.html
-
No luck, just blocked all UDP on the firewall ip and still traces.
-
Still don't know what trace-route you want to block.
From the inside, LAN, to, the outside ?
The other way around ? -
so tracing from outside of our network into a public ip in our DC so for example on the route
BGP Router
CORE Switch
pfSense Firewall ( Public IP)
Server (Public IP)trying to block the pfSense public ip from being traced, i can stop the normal icmp ping protocal but not the trace or an MTR
pfSense on WAN needs to be a public IP and our core switch ip routes to it to get route outwards to our BGP switch to know where its going as its in the BGP config, would not work as an internal ip because it has no route to the world.
-
@chrisjmuk said in stop pfsense showing as route:
trying to block the pfSense public ip from being traced,
That public IP is assigned to you - and known (to the public).
You can't hide an IP.
You can make it look like a black hole, by not answering to any out of state requests, which is what pfSense does when you install, it.The last router in front of pfSense knows what IP - the one used by you - is on what interface. If that one - yours - isn't replying when using trace route, they - the one that traces - still knows the path to you system up until the last router.
If you asked the organisation that gave you your IP's to remove them - that is : remove them from their routing tables, then your IP would vanish from the net, that's for sure. As will your entire connection to the net.
Btw : the trace route will end with your WAN IP, because the upstream router was telling so. It will not go beyond pfSense, because it also works as a firewall.
This (should be valid) if the IP's are RFC1918 - or public ones. -
Just thinking we can blackhole the pfsense ip on incomming connections on our BGP configs, that way it wont be hit from outside but allowed on inside our network.
-
Or, as you stated earlier : what about using RFC1918 instead of using a public IP ?
If the network doesn't need to be accessible from the outside, hiding it from the outside would because easier.