Rules for DNS traffic
-
Another trick instead of firewall rules, should be to portforward 53 & 853 to pfsense-ip 53 & 853
I haven't tried that , but i think it's in the "Book" , en excellent read (thnx Netgate) -
Thank you VERY much for your responses. Quick follow-up question though...
Why would I port forward to the IP of the pfSense itself, instead of the IP of the DNS server?
-
@StarsAndBars said in Rules for DNS traffic:
DNS server is 192.168.1.250 and I want any and all traffic to be directed to it for upstream resolution
So you have this NS forwarding where? Or resolving?
Normally you would point your client there, then have it forward to pfsense - which would resolve.
So pfsense would only point to itself, loopback 127.0.0.1. You would setup a domain override for your domain.tld so pfsense knows to go ask 192.168.1.250 for any of your domains and the reverse zones.
As to any other external, you could ether block that or redirect it to pfsense loopback.
-
Do you have a quick example of a domain override ??
I'm lazy ..I assume we're talking about Unbound
/Bingo
-
here
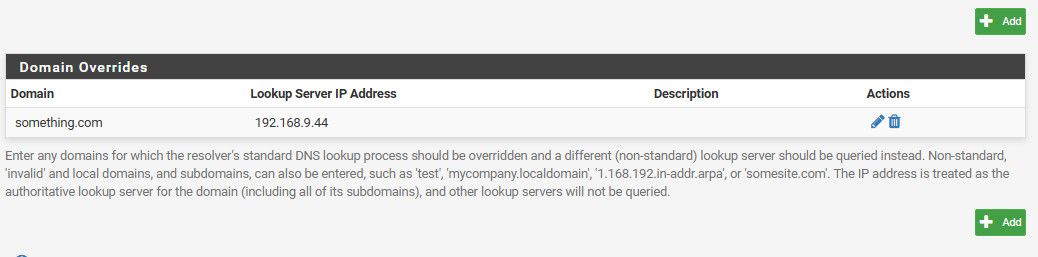
Scroll down in the unbound settings gui..
-
@StarsAndBars said in Rules for DNS traffic:
Thank you VERY much for your responses. Quick follow-up question though...
Why would I port forward to the IP of the pfSense itself, instead of the IP of the DNS server?
That would just seem more logic to me.
If possible don't even allow your clients to go to the DNS server.
Have them use the firewall, as it can protect it self.
I do that for both DHCP (dhcp relay) & DNS.I had an existing Linux DHCP & DNS structure before using pfSense.
@homeI must admit that ISC-DHCP is powerfull , but pfSense DHCP is so easy to setup.
@work
I Use pfSense for DNS & DHCP
And prays that someone would make a fix for unbound to allow it to record DHCP entries wo. having to restart , and cause a looooooonnng DNS outage (well enough to make the system feel unresponsive). So i don't use that function.
-
@johnpoz said in Rules for DNS traffic:
here

Scroll down in the unbound settings gui..
Arrghh .... That was easy
I did all that transparent stuff etc ....@OP
Use Johns tip , that's elegant -
@johnpoz The host on my LAN is a DNS server (pi-hole ad blocker, actually). It currently forwards upstream to Google DNS for now.
I want all DNS resolution requests from the LAN, regardless of the host/origin to be forced through the pi-hole so that ads and analytics requests can be blocked. I specifically do not want the pfSense device to do any resolution on its own for LAN clients (but what it does for its own purposes internally is ok). I am particularly interested in forcing devices with hard-coded DNS through the pi-hole for obvious reasons.
Thanks, I hope that clarifies what I am looking to do, so if you could help me tailor my config there, I would appreciate it. I am building a second DNS server for the LAN (192.168.1.251) in the same configuration as a backup/failover. So I would eventually want the rules to reflect that and cascade accordingly.
Thanks again for any insight you can provide.
-Rob
-
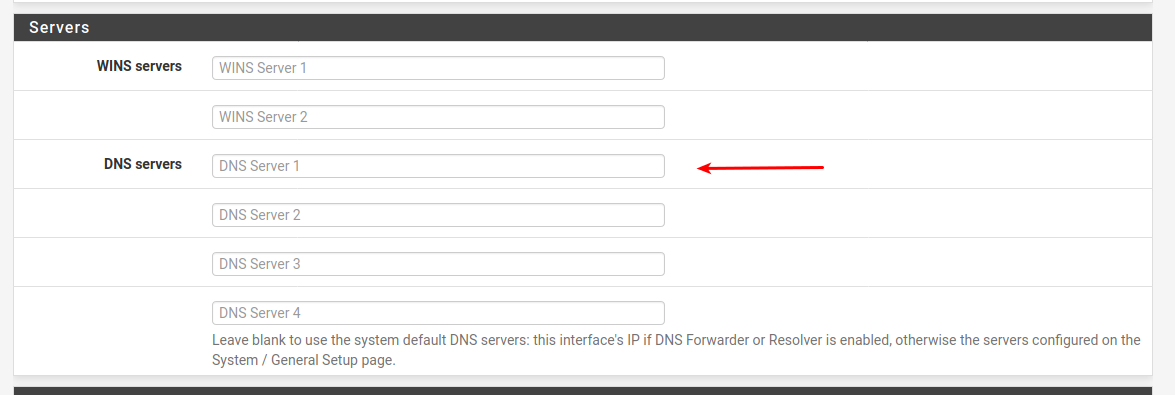
You might just hand out the ip addy of the pihole in the DHCP server definitions of the LAN.
Then on the LAN interface add an allow rule for pihole UDP 53
And Deny UDP 53 & 853 to any after the allow.That would cause your LAN to use just the pihole (as given out by dhcp)
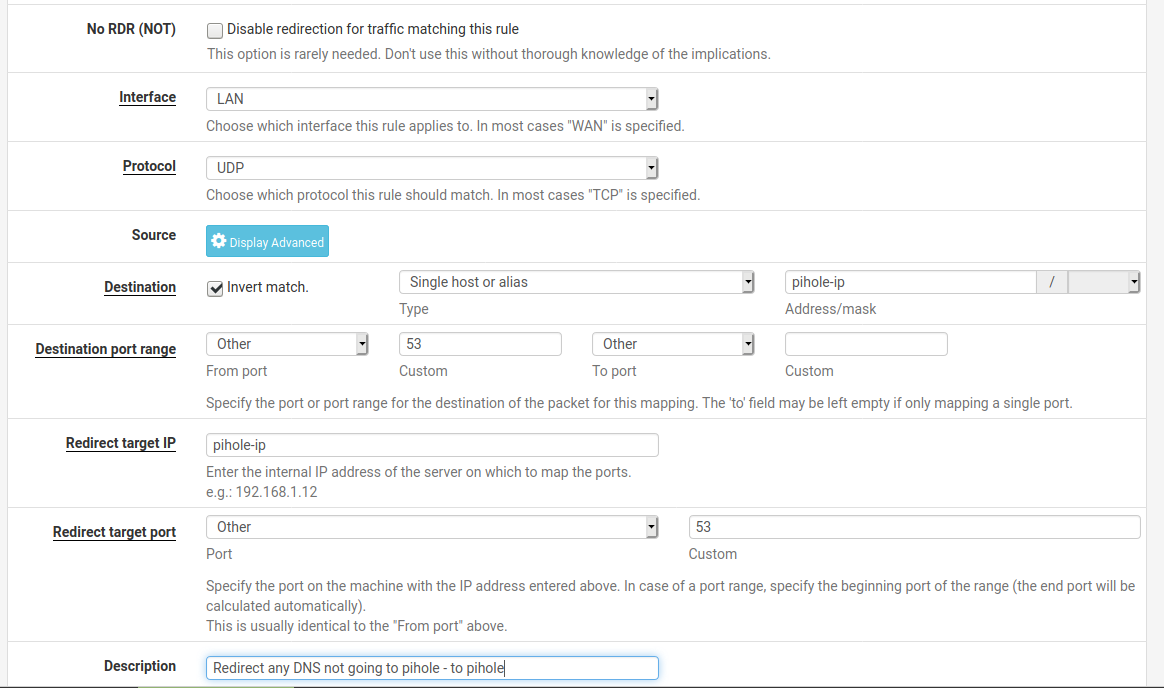
The force part usually solves it self (i use pihole too) , it trued a few times on 8.8.8.8 , gives up.
And uses the DHCP given server (pihole) -
Or do the portforward trick along with the DHCP handing out pihole as DNS
https://docs.netgate.com/pfsense/en/latest/dns/redirecting-all-dns-requests-to-pfsense.html
Just substitute 127.0.0.1 with the pihole ip
Something like this