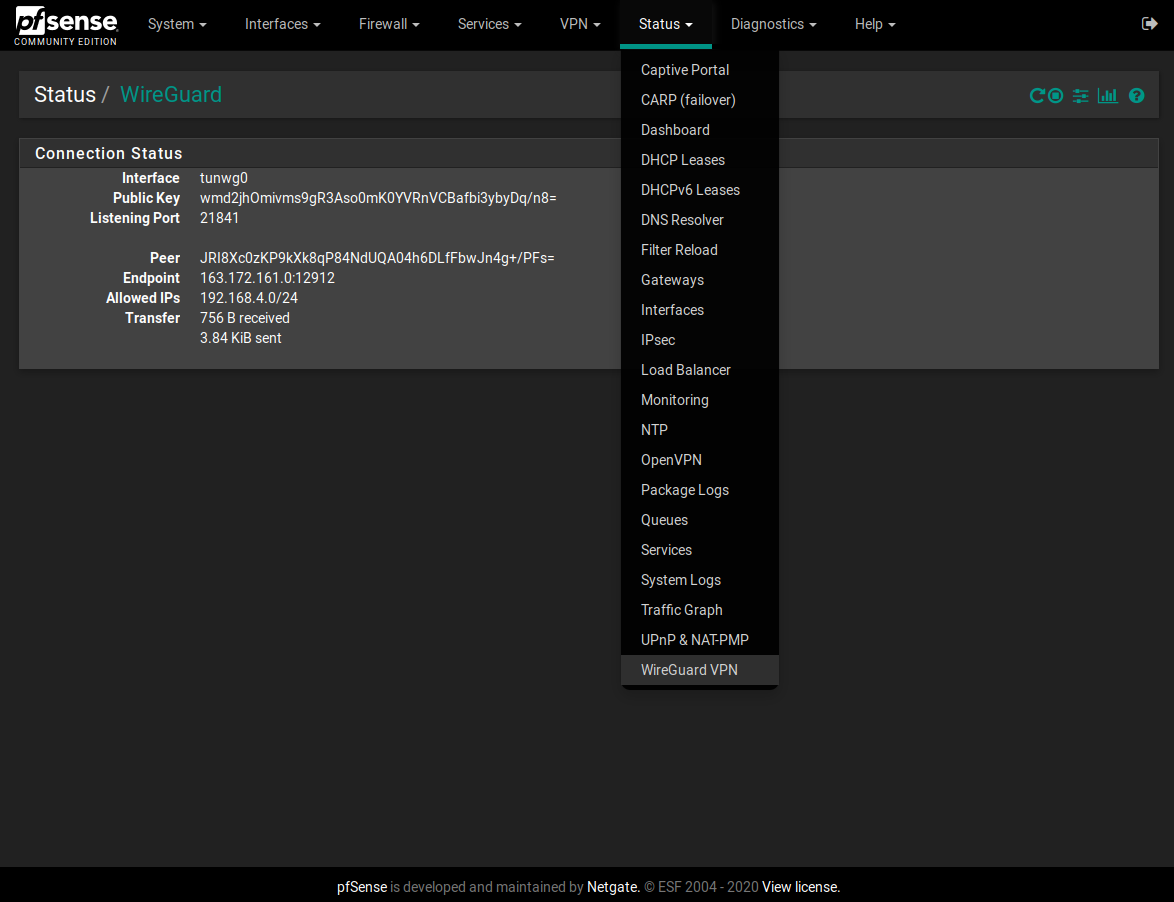
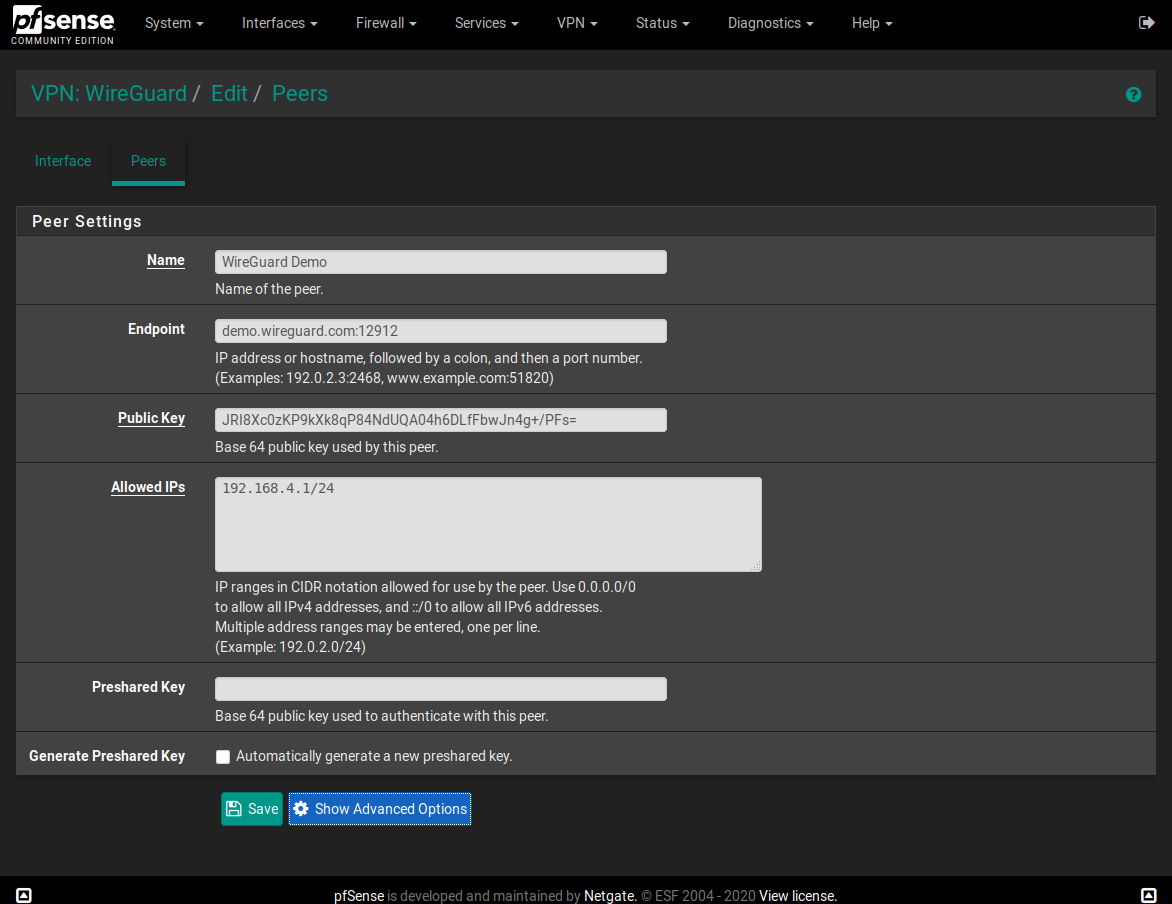
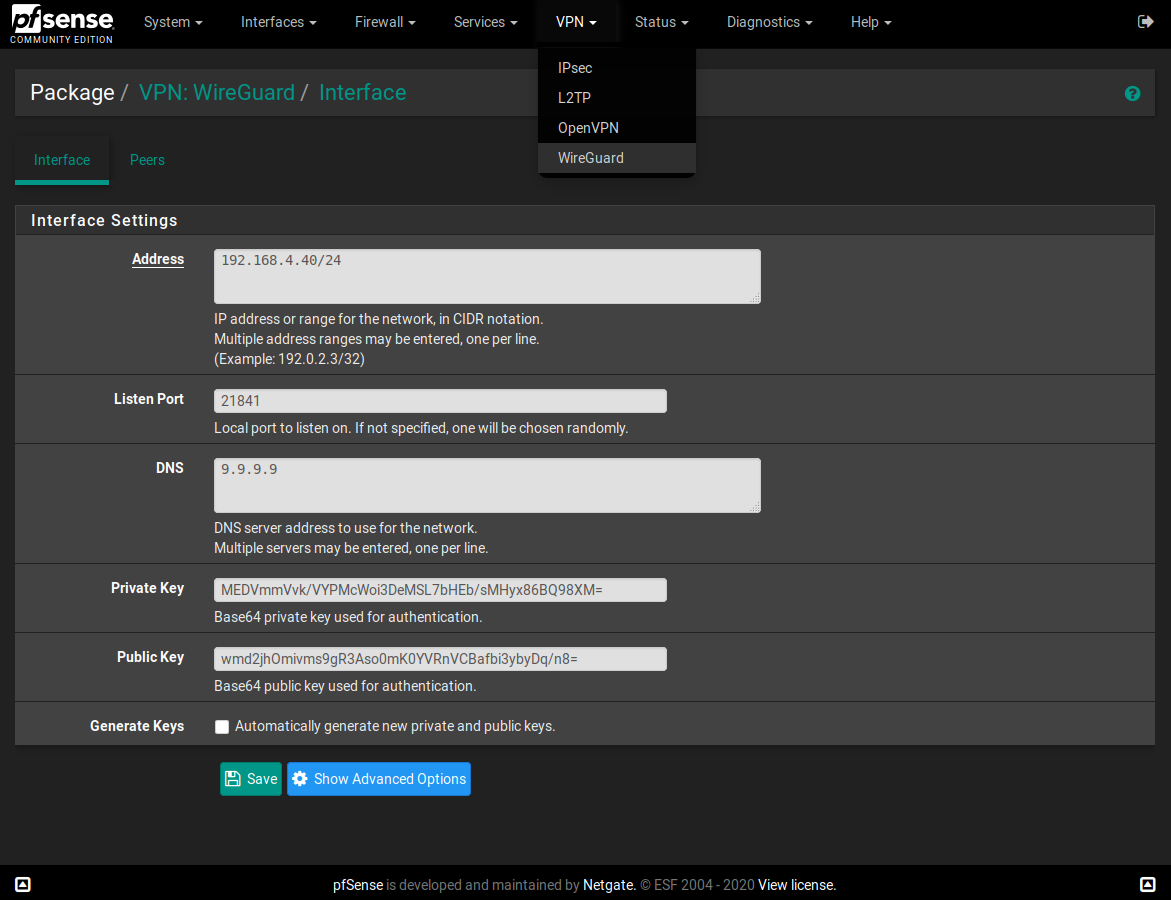
I made a WireGuard package for pfSense
-
@Ashus thank you. I saw that and configuring by xml-files is ok for me, but since I could not generate new keys easily I didn't manage to set up a second tunnel. Now I will give it another try.
I still have a problem with gateway/ip though.
I get an IP from mullvad. Let say it is 10.11.12.13/32
Where should I configure it besides the obvious wireguard peer section?Should I configure it in the Interfaces section as IPv4 static?
Should I manually set it as gateway IP?The only time I have gotten it to work I statically set it as gateway IP, but I think the intention is to only set it in the wireguard section.
-
@Talisker Yes, by my side, I used Mullvad/32 ip both in the following fields:
- Package -> VPN: WireGuard -> Interface -> Address;
- System -> Routing -> Gateways -> Gateway IP;
-
@dubatech but, you dont set it as static IPv4 address in Interfaces / Wireguard
Static IPv4
IPv4 address = MullvadI wonder if it is some kind of routing issue since I have OpenVPN. When I upgraded to version 2.5 I could not longer have two OpenVPN connections to mullvad, since the service died because of some kind of routing-problem. I will try to set up a static route to the IP I am pinging.
-
@Talisker No, I didn't set it on Interfaces / tunwg0:
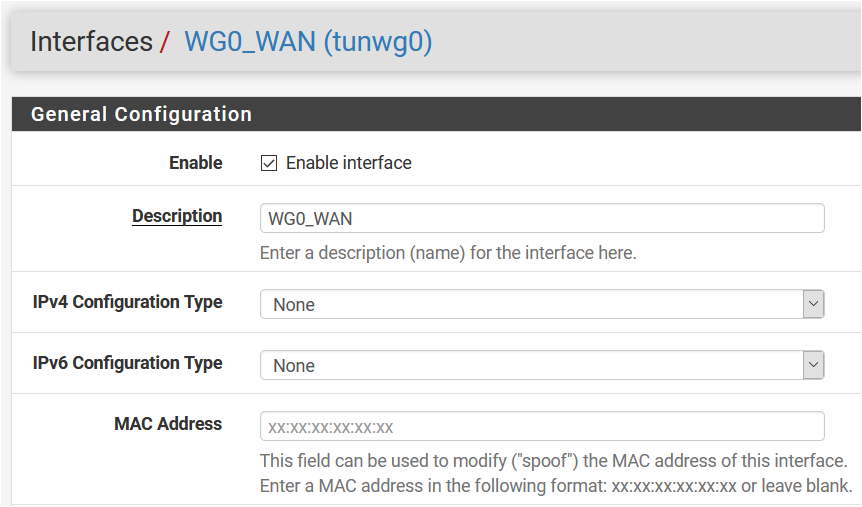
Nat Outbound rule is setup correctly?
I've OpenVPN and also WG with Mullvad and it works correctly with Manual Outbound NAT rule generation. -
@dubatech the problem is that the gateway is considered down. The NAT and Rules are correct. I had I working before, but not any more.
-
@Talisker The same for me, everytime I reboot.
In that case I disable and then enable again gateway.
On monitor IP I've Mullvad DNS 10.64.0.1 because using Mullvad/32 ip as monitor IP doesn't work. -
I can see that work has been done, but no compiled package is available for download. Unfortunately I have not compiled any package before and I don't really have time to do read up upon it for the moment. (Though I could set up a freebsd in my VMware, so in theory it could be done).
I upgraded my hardware PFSense to 2.5, but got packet loss in OpenVPN which is not ok. Since I cannot easily reach the firewall physically I decided to boot up my virtual 2.4.5 and run them in parallell. (And I have a Clavister firewall as well, since I can get several IPs from my ISP). Anyway, this gives me plenty of opportunity to try things when I have more time:)
So as soon as someone could put up a new package made on the merged project I am happy to try.
Edit: I found it, but only for version 2.4.
pkg add https://github.com/lucasnz/pfSense-pkg-wireguard/releases/download/v1.0.1/pfSense-pkg-wireguard-1.0.1-freebsd11-amd64.txzLucasnz version is working. It has removed the bug with key generation and I am able to set up the tunnel as intended. Still with the "issue" that I have to set gateway IP manually in the xml-file since I otherwise get an error trying to configure a gateway IP on an interface with dynamic IP address.
-
Anyone made any benchmark comparing this package to openvpn on the same connection? ie throughput. Care to share?
-
I'm trying to get a basic wireguard link set up between pfSense and a remote server, and running into a strange issue. Both sides of the tunnel show it as active, and keepalive packets are flowing, but I can't ping one side from the other. I'm speculating this basic issue is what's preventing my source-based routing (explained in a different thread on here) from working properly.
The server's wireguard endpoint is 192.168.16.0/31, and the pfSense endpoint is set as 192.168.16.1/31. From pfSense, I can't ping 192.168.16.0, and additionally when I ping the local 192.168.16.1 address it actually goes through the wireguard tunnel and back again before replying which is even more confusing. That definitely doesn't seem right.
When I run an ifconfig from the console, this is what I get for the wireguard interface:
tunwg0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1420 options=80000<LINKSTATE> inet 192.168.16.1 --> 192.168.16.1 netmask 0xfffffffe nd6 options=101<PERFORMNUD,NO_DAD> groups: tun Opened by PID 52527Which seems to imply that the address does exist locally on the router. However, like I said above I can't ping it locally, or from the other side of the tunnel.
-
@papkee don't know how it works in PFSense l, but it could be considered that. 1 is a broadcast address and .0 is the network address. Why not a slightly bigger network and not using the first and the last IP to rule that out? Like using. 1 and .2 in a /30 network.
-
OK, finally did a comparision....... I know WG is not in kernel on freebsd/pfsense yet!
Server Xeon E5-2667v2 (8x3.3Ghz turbo 4.0Ghz) pfsense running in VM on ESXi with 2 cores.
Pfsense openvpn 650Mbit (cpu 60%)
Pfsense Wireguard 650Mbit (cpu 80%)
Vyos Wireguard 900Mbit (cpu 65%)Symmetrical 1Gbit FIber Internet.
-
-
Thanks for the suggestions everyone, I'll give them a try and report back.
Edit
No dice.
I tried with the /30 and 192.168.16.1 & 16.2, and it got me the same result as the /31. Couldn't ping either endpoint from the other, and on the pfsense box pinging its own tunnel address went through the tunnel and back again.
Tried the /32s with the same addresses above and that didn't even allow the pfSense box to ping itself. Something is still strange with this setup.
Although as a sidenote, I just went and checked some of the other debian -> debian wireguard links I have set up the same way, and I actually can't ping their endpoint IPs directly either. But, those tunnels are still routing my subnet just fine so I'm thinking that might not be the root cause of my routing issues.
-
@xayide I have an older VMware installation and get the following.
OpenVPN 130 MBps
Wireguard 205 MbpsPFSense isn't my primary firewall, but I use it when I want to be anonymous. (Load balanced between OpenVPN/Wireguard on the VMware and hardware PFSense.) A little weird setup, but I need some projects...
-
So does anyone else use wireguard as a gateway in pfSense for policy-based routing?
I believe my testing so far has concluded that this is not possible. pfSense just ignores any firewall rules that specify the wireguard interface as the gateway.
-
@papkee As I mentioned earlier in this thread. I need to specify the IP adress for Wireguard as IP address on the gateway. It is dynamic as default and cannot be changed in the UI. I opened the configuration in text-mode and changed IP to the /32-address and it works.
-
@papkee I'm using exactly as a gateway since weeks, without problems.
You can create a new gw on System \ Routing \ Gateways and use the ip address you get from your wg provider as gateway ip.
-
@dubatech anyone have a guide how to set up a working "compiling environment"? I would like to be able to compile packages for FreeBSD 12.1, but I fail to do that. My idea was to set up a working environment for that and then produce a package for PFSense 2.5 ...
-
@Talisker I'm sorry, I really don't know if there is a guide for doing that.
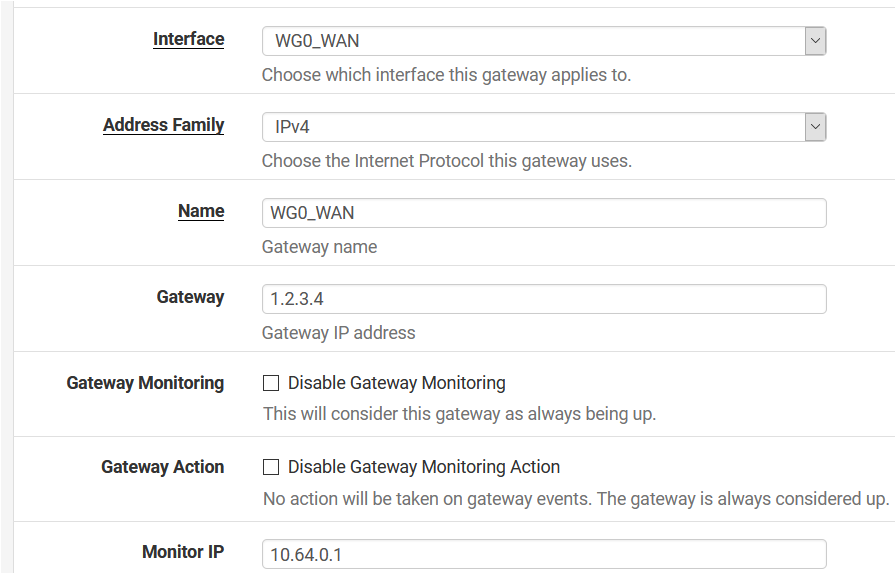
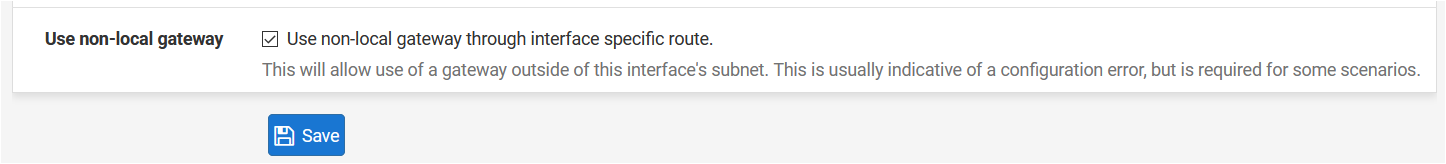
Anyway, I don't know if you've tried but I set up the wireguard gateway using the Advanced option "Use non-local gateway".This gave me the ability to avoid using IP/32 received from Mullvad.
This is the gateway configuration:
Advanced gateway options:
Now, on VPN: WireGuard / Edit / Peers put the following in the "Allowed IPs":

It's working great, without the need to edit config files, setting up the IP/32 obtained by the WireGuard VPN provider, etc...
Really thanks to @Ashus, who helped me with the manual configuration of the tunwg config files to set up multiple wireguard interfaces!
-
@Talisker
Dear @Talisker,
Hello and I hope that you are safe and well. I compiled and built Lucasnz pfSense-pkg-wireguard-1.0.1 For 2.5.0. With all due respect to Ascrod and Ashus, I found Lucasnz to work perfectly on pfSense 2.5.0. For you to get a basic idea as to how to setup a FreeBSD 12 Build Server - see my old tutorial here :https://forum.netgate.com/topic/130832/solution-posted-dns-tls-getdns-stubby-from-pfsense-freebsd-ports
I am attaching a text file with with detailed instructions as how to build Lucasnz pfSense-pkg-wireguard from github for pfsense 2.5.0. - There is also an extra added gift for those who are looking to setup Lucasnz pfSense-pkg-wireguard package on pfSense 2.5.0 Firewall. The reason that I chose Lucasnz to compile on a FreeBSD Build Server ( special thanks to @Talisker for suggestion that it " works " ) is just that. Lucasnz WireGuard for pfsense survives reboots, upgrades - and has no issues with DNS or any such other related problems. I have been running this for a few weeks with no issues. Good Luck - Hope this helps
Lucasnz pfSense-pkg-wireguard-1.0.1 For 2.5.0.txt