pfBlockerNG-Devel blocking on mobile devices but not laptop
-
Hello,
I just setup pfSense for the first time on Friday (6/26/2020) and I was able to configure the initial setup successfully. I installed the Snort package and the pfBlockerNG-Devel package. I am still fine tuning the Snort service but the pfBlocker was not working initially. It took me almost two days to realize that I had to setup pfSense IP address as the DNS server on the DHCP service. Now I can see that the DNSBL is actually blocking.
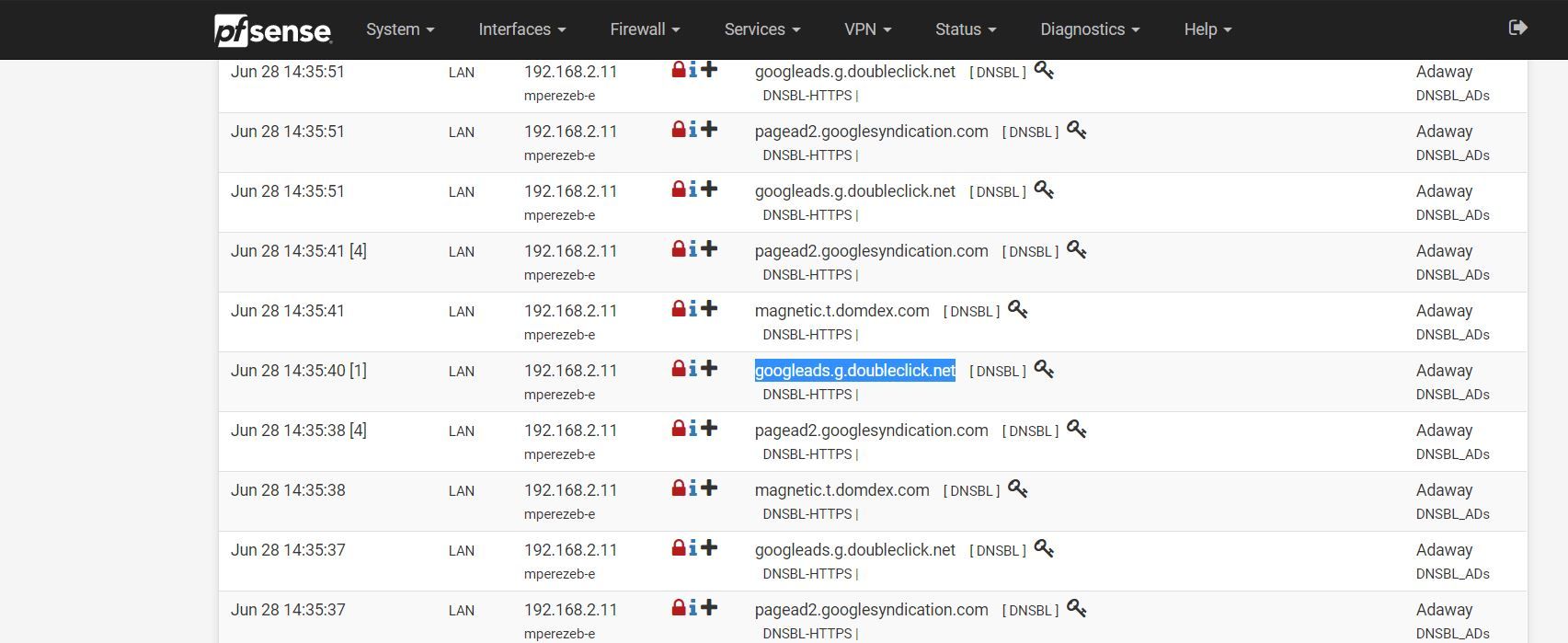
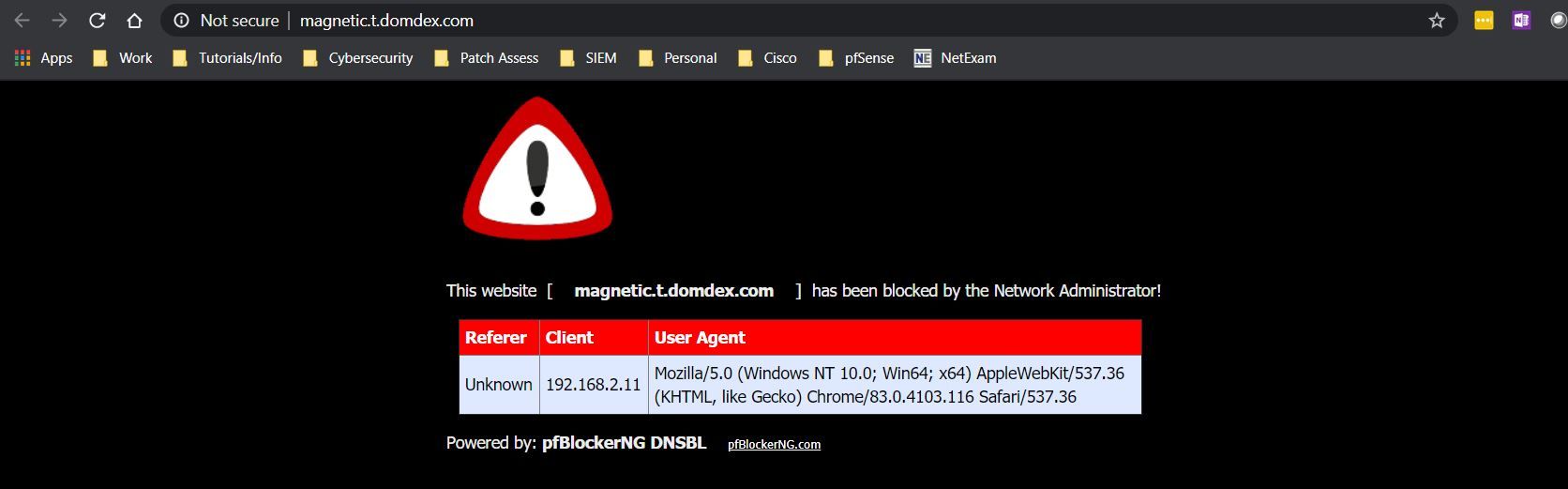
The problems is that I still see countless of ads when I navigate to a website that I know has ads. This is only happening on my laptop. If I use my iPhone, wifes iphone, sons tablets, the ads are being block for that website. If I navigate to Firewall/pfBlockerNg/Alerts and filter for alerts from my laptop I can see that it detected the domains but if I copy the link and navigate to that link pfBlocker will not deny the traffic. I tried many of the links and I did find one that was being blocked.
If I try one of the google ad links that show up on the report I am able to navigate to the site.
Why is this happening? Could it be something on my local device or a setting on pfSense?

-
@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
It took me almost two days to realize that I had to setup pfSense IP address as the DNS server on the DHCP service.
You just proved this :
to be true ;)
Your devices should use pfSense (== unbound, the resolver) to handle the DNS requests.
@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
The problems is that I still see countless of ads when I navigate to a website that I know has ads. This is only happening on my laptop
The domains/IP's used as add server isn't necessarily some other server.
It is very possible that the web site you visit generate itself the add blocks. You cant' block them, as you would block the entire site.Also : what DNS is your laptop using ? It should be using DHCP so it should be using pfSense/unbound.
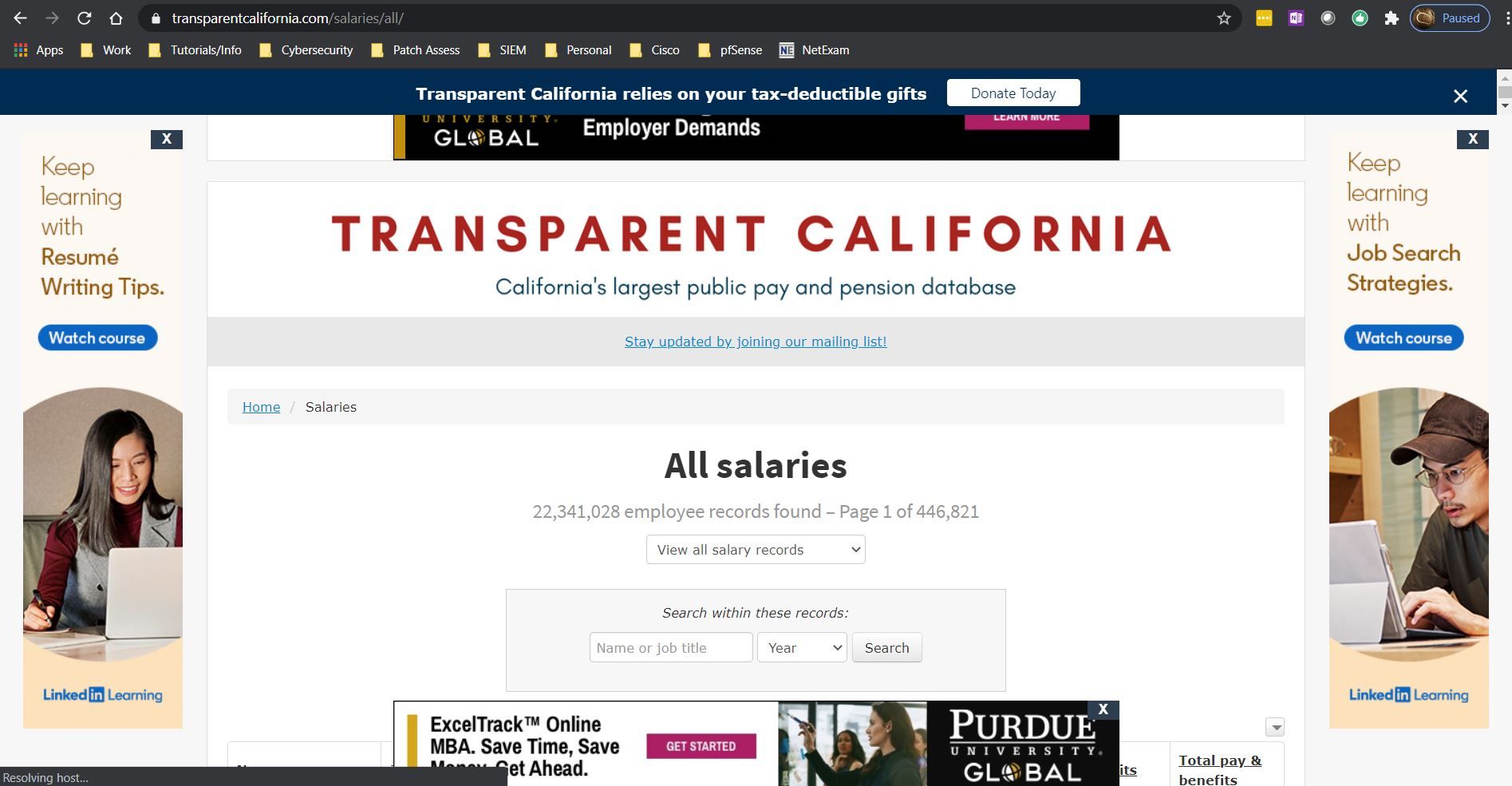
When I visit that https://transparentcalifornia.com/salaries/all/ website, I see no adds :
-
@Gertjan
Thanks for the suggestionsMy laptop is using DHCP to get the IP address and DNS settings. The IP address of my pfSense is 192.168.2.1.
I do have DNS resolver enable. Should I enable SSL/TLS service? Also, I want to reiterate, on my mobile devices the ads are being block for the Transparent California website. The only device that is not blocking most of them is my laptop. I say most of them because it is blocking a few of them but many are still showing.
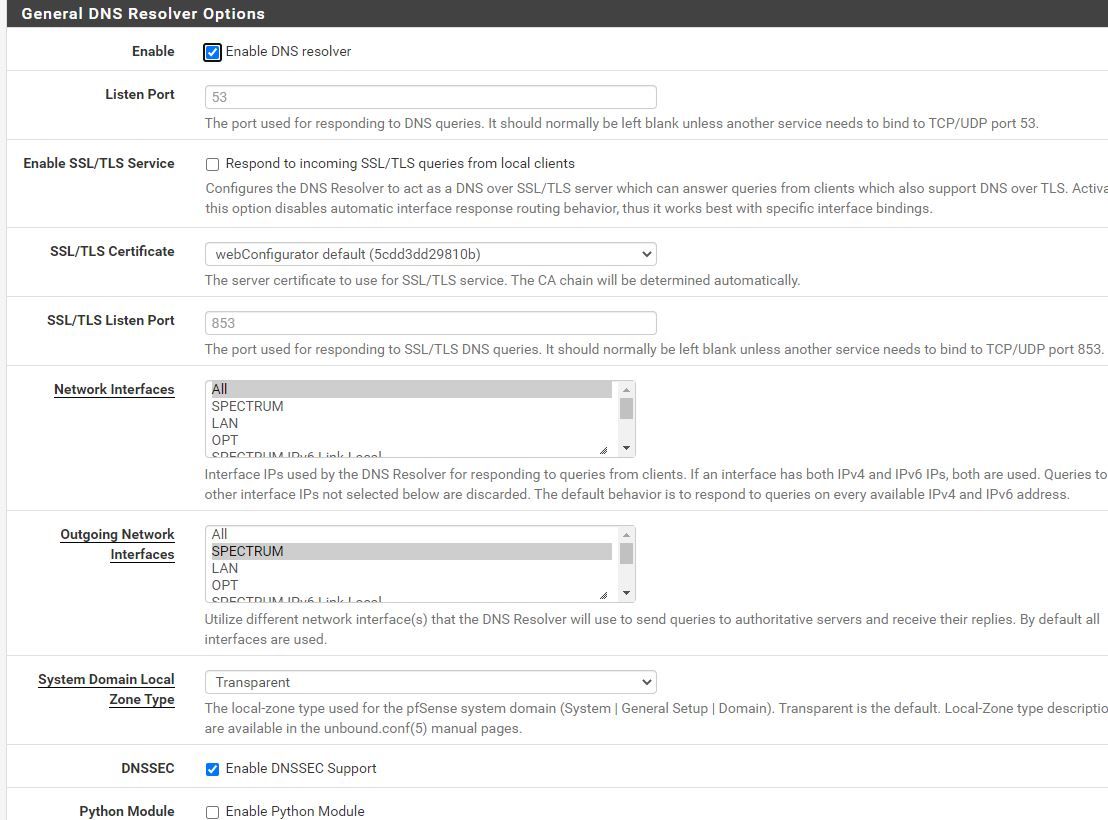
-

Ok, but your question is about DNS : what is the DNS ?
If it's, for example, 8.8.8.8, everything is explained as you are not using the resolver, so not using pfBlockerNG.@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
Should I enable SSL/TLS service?
If you do not trust your LAN network(s). And if your clients (PC's, phones, etc) support this mode.
It just adds a new level of complexity.
@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
on my mobile devices the ads are being block for the Transparent California website.
They are on the same LAN work as de PC, 192.168.2.0/24 ?
@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
The only device that is not blocking most of them is my laptop. I say most of them because it is blocking a few of them but many are still showing.
Visit the DNS and DHCP forum .... and read the very first pinned thread : HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox
If your browser uses such a DNS mode, then it bypasses the Resolver, so pfBlockerNG is bypassed. -
@Gertjan said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
Ok, but your question is about DNS : what is the DNS ?
I uploaded the wrong screenshot the first time. The DNS server is my pfSense.
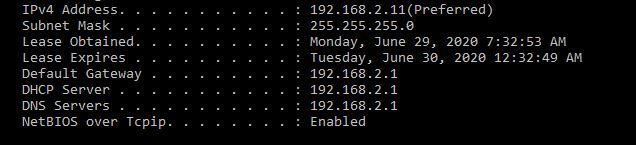
-
@Gertjan said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
If you do not trust your LAN network(s). And if your clients (PC's, phones, etc) support this mode.
It just adds a new level of complexity.I will not enable it.
I also noticed that the firewall rule that was created automatically by pfBlocker doesn't have any hits. Is this normal?
There are some ICMP because I was pinging the virtual ip address.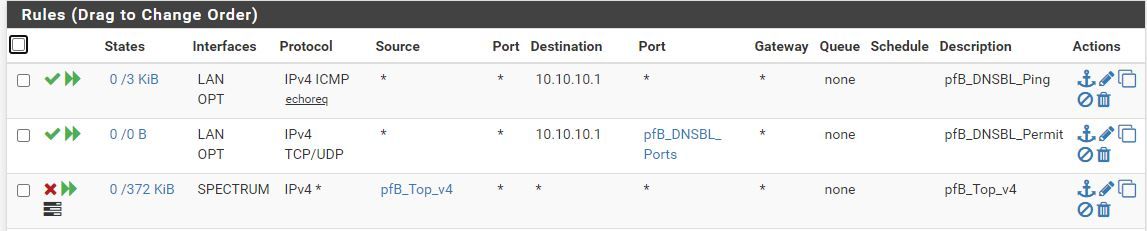
-
@Gertjan said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
Visit the DNS and DHCP forum .... and read the very first pinned thread : HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox
If your browser uses such a DNS mode, then it bypasses the Resolver, so pfBlockerNG is bypassed.It appears that it only applies to Firefox. I found the following for Google Chrome, I will go ahead and try it.
https://www.blackfog.com/knowledge-base/disable-async-dns-on-google-chrome-for-windows/#:~:text=Recent%20versions%20of%20Google%20Chrome,and%20uses%20the%20browser%20directly.
-
You found it :
Recent versions of Google Chrome employ a feature called Async DNS. This feature bypasses the normal operating system mechanisms for resolving domain names and uses the browser directly. In this mode, DNS requests will uses SSL to communicate directly with Googles own DNS servers and some third party providers. As a result you may see some Ads leak through the browser.
If it's active, your have your explanation.
You can test your PC device with another browser that is not using such a functionality, like the good olf IE11 - or, as described in the forum post, a well defined method to turn it of if you can find it (Firefox case).. -
@Gertjan
It didn't work. I disabled it on Firefox and Chrome. I will try IE11
I did a Wireshark capture and I saw some interesting stuff.
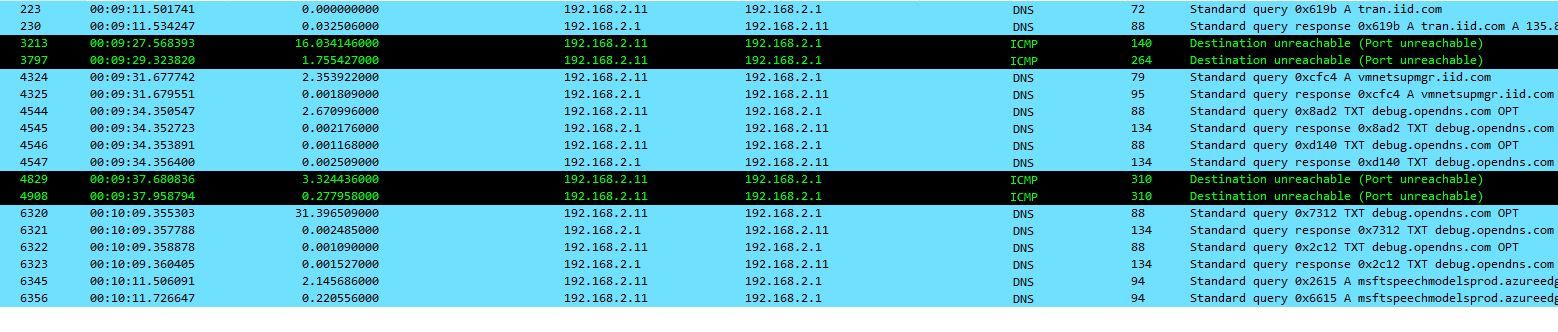
I don't know why its querying other DNS servers. Should I remove the OpenDNS server from my configuration?
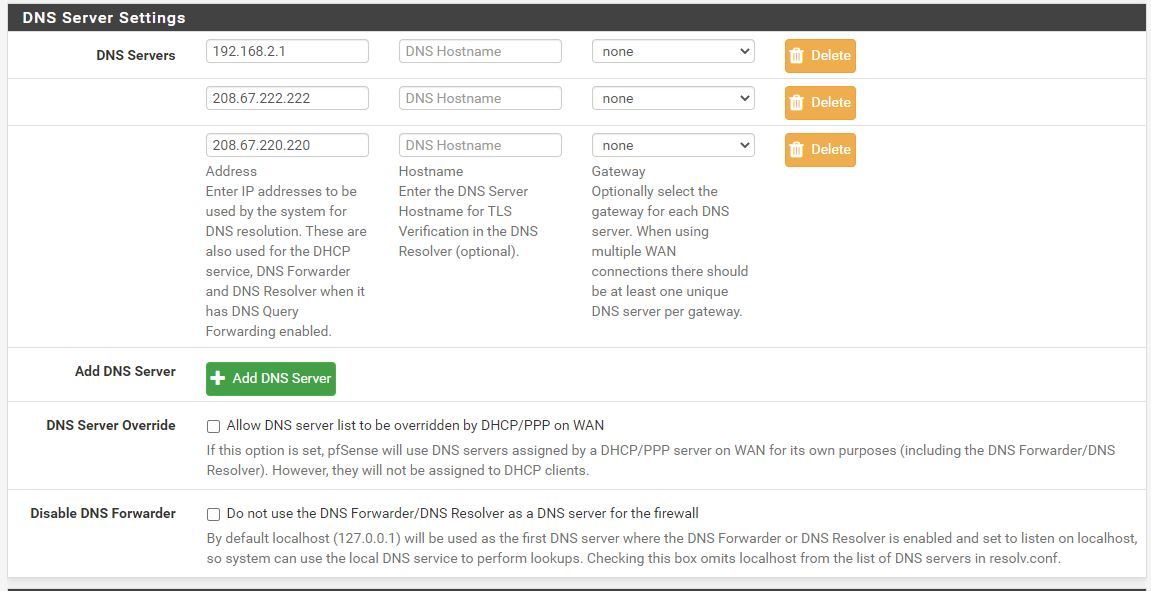
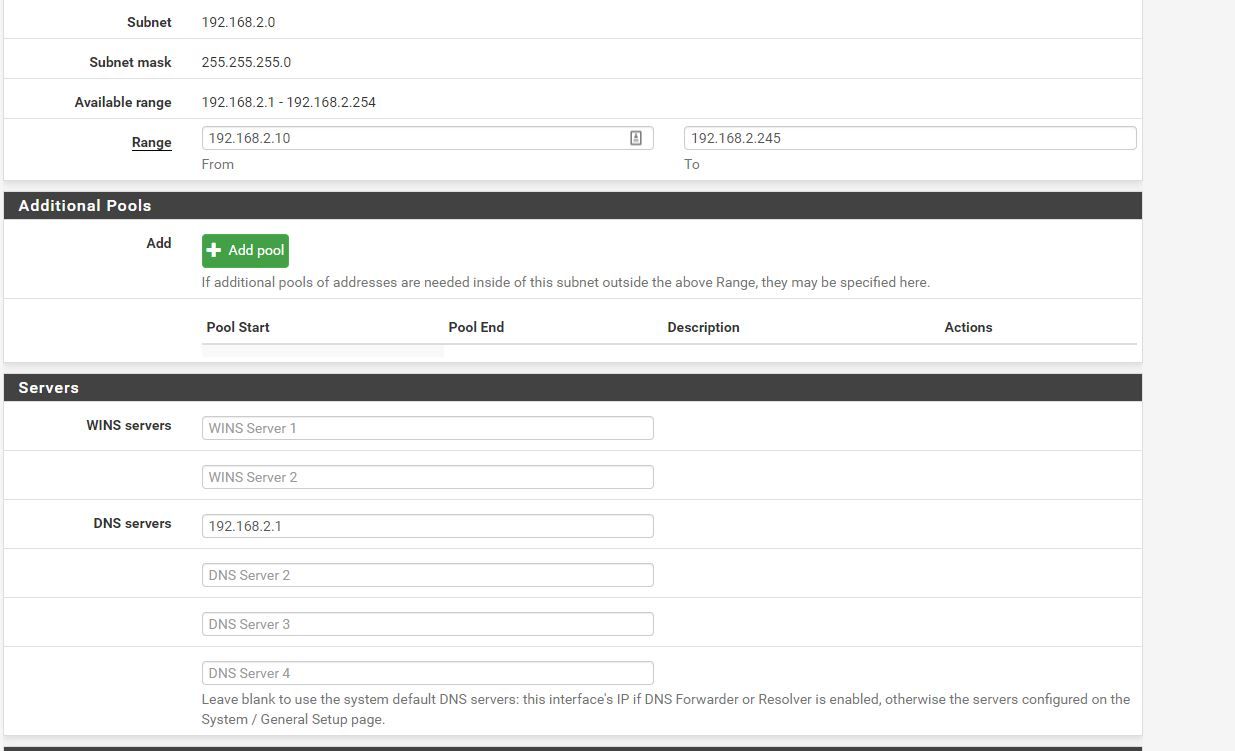
-
How can you ask :
@mperez0000 said in pfBlockerNG-Devel blocking on mobile devices but not laptop:
I don't know why its querying other DNS servers.
and then showing this image :
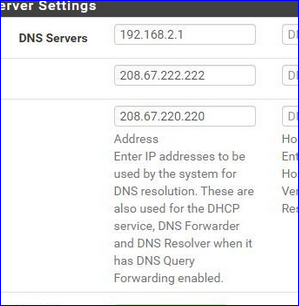
without seeing the relation between your question and your => answer<= to it.
Read the description text.You don't need the first, as DHCP will hand out the IP of pfSense as the 'local DNS cache resolver'. So network (DHCP) clients know to who they have to ask for DNS requests.
See also the DNS servers fields description of the DHCP server setting page.The other two IPs : so you list two other IP,'s which are also used by DHCP = communicated to your network DHCP clients ..... which means they could use OpenDNS instead of the pfSense Resolver ... which uses pfBlocker ....
So, you set up the opportunity to bypass pfBlockerNG - and ask why it's bypassed ...

Really, consider this : the default settings were just perfect ;)
If you want to add something there add :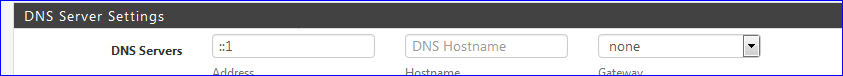
Note : your 'wireshark' also showed something else : your LAN doesn't reply on ICMP (ping) ? Why ? (can't see if it's the source or destination - your PC is in "undercover" mode ?)
Tip of the day : use the default LAN rule as proposed by Netgate.