IPSEC IKEv2 with EAP-MSCHAPv2 Not working. Could use some help.
-
I followed this guide link and I for the life of me cannot successfully get IPSEC to authenticate or connect properly with Windows 10.
I am using the correct certificate from the certificate authority on the client.
Here's some screenshots of my configuration with a blacked-out WAN IP address
Certificate Authority:
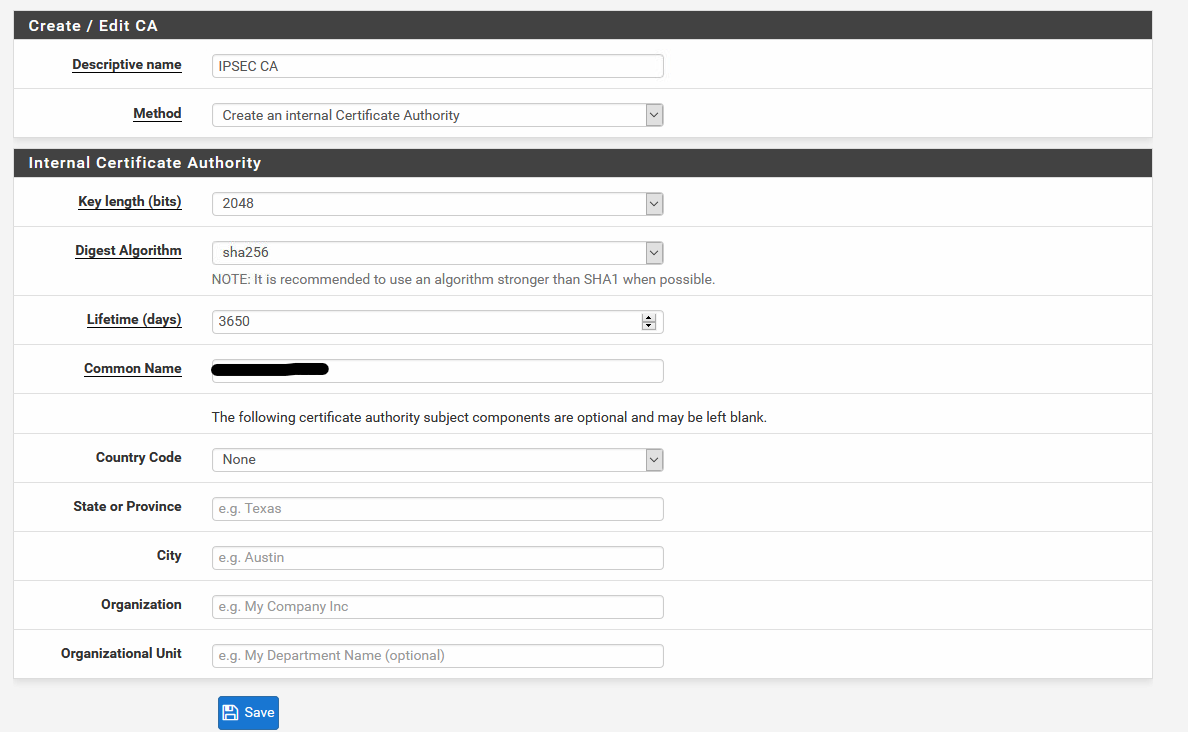
Server Certificate:
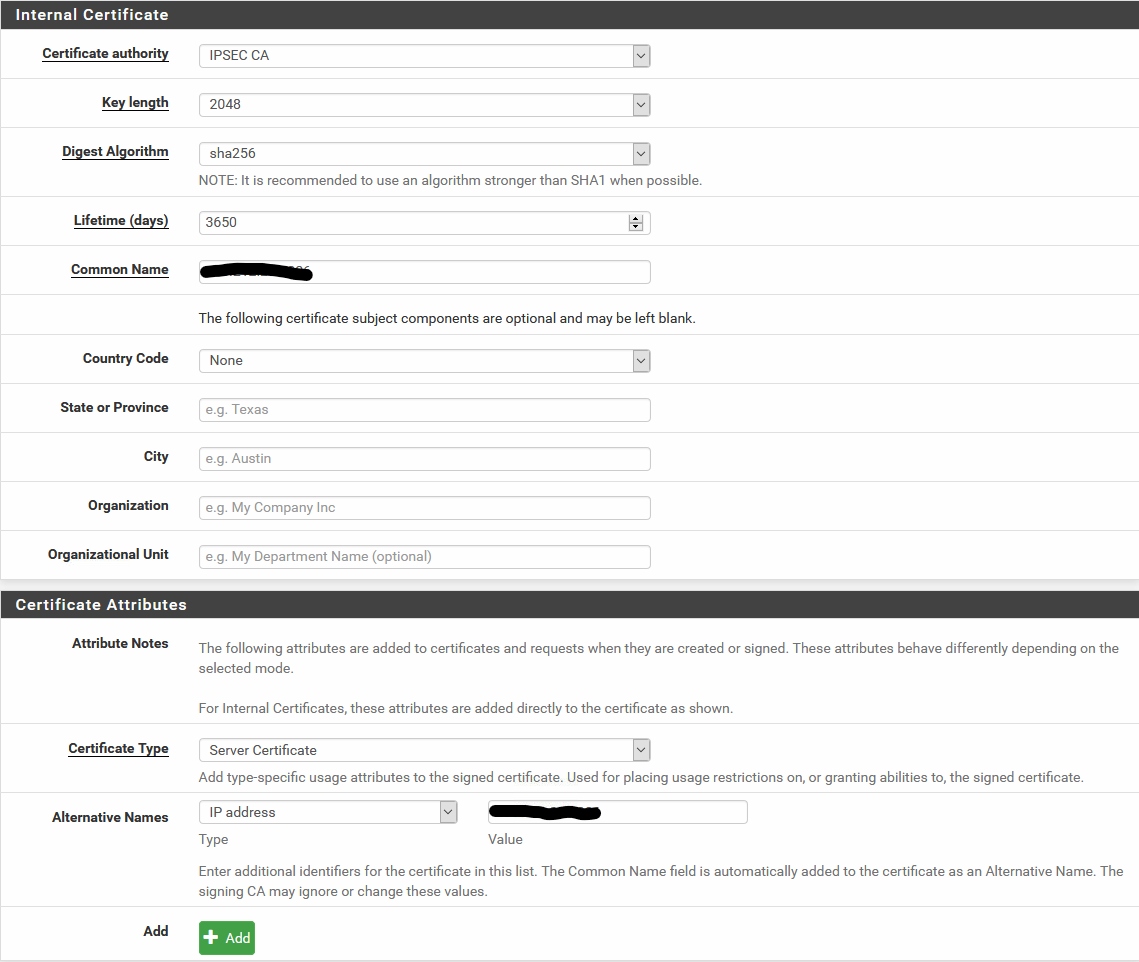
Mobile Client Setup:
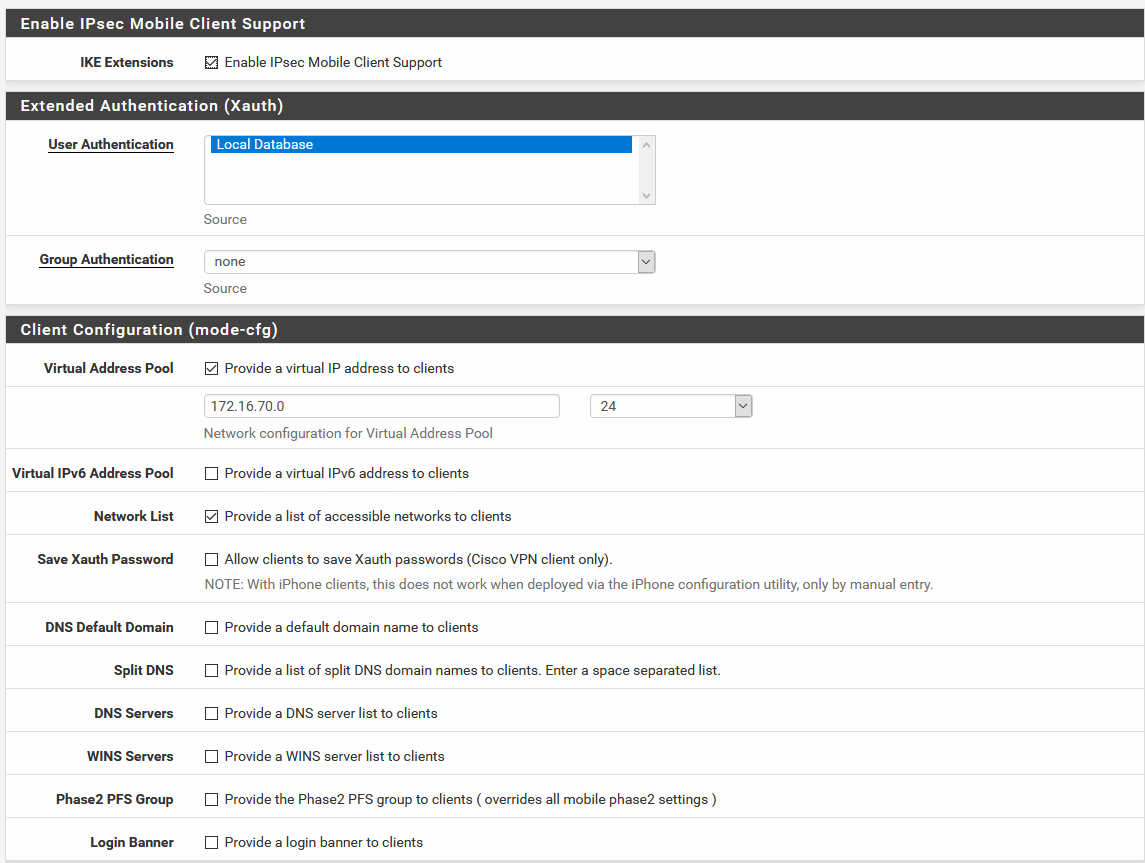
Phase 1 Setup:
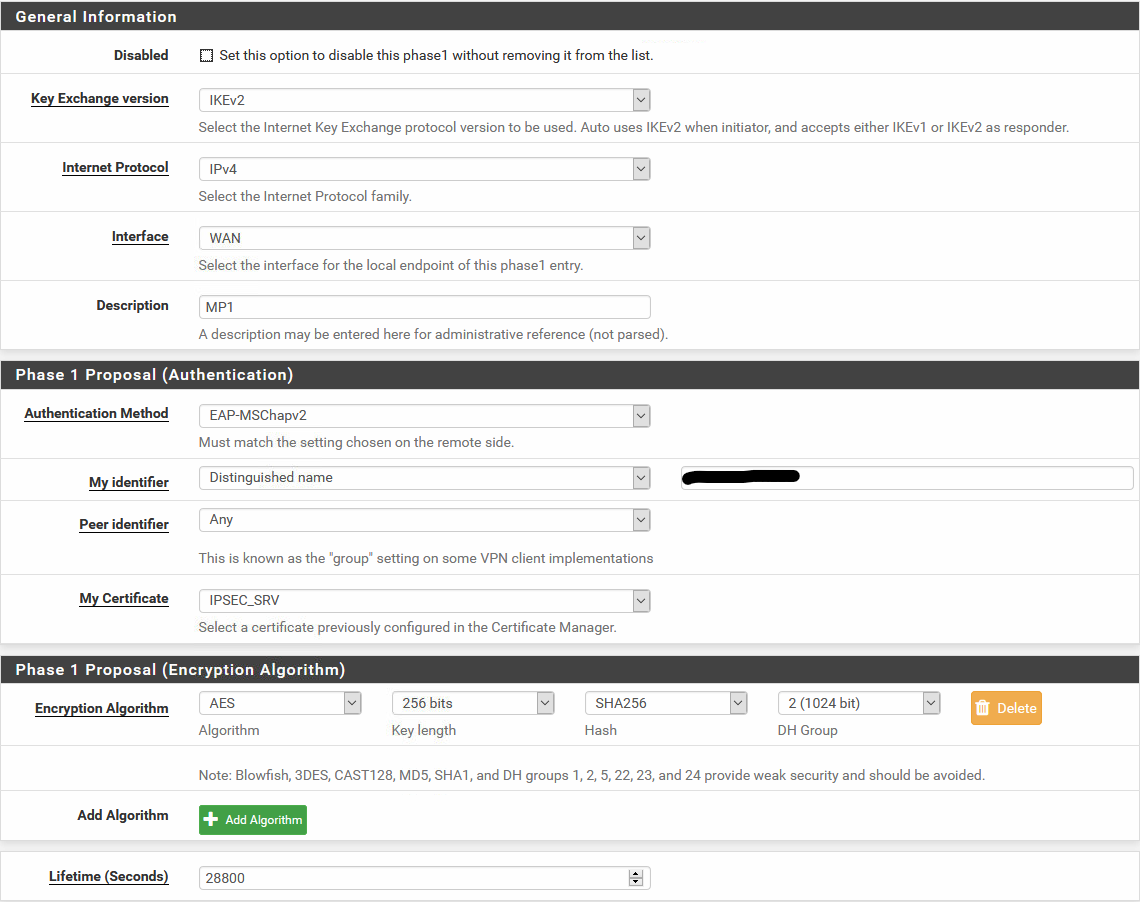

Phase 2 Setup:
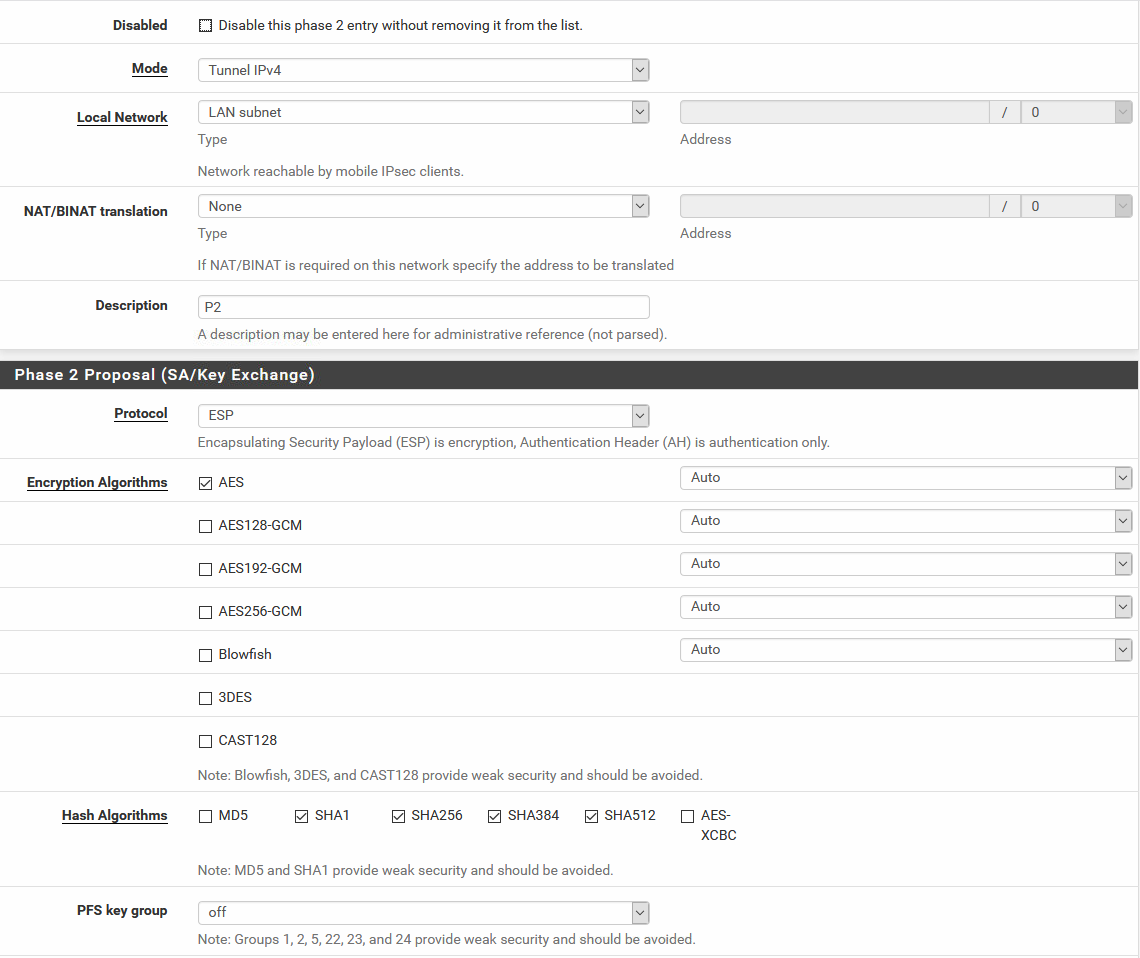
Pre-Shared Keys:
When I attempt to connect via Windows 10 I get error 87 the parameter is incorrect:
When I attempt to connect via Android with strongSwan:
I tried my best to look at existing documentation and other user forum posts but from my configuration, I cannot for the life of me determine what is wrong. Any and all help is appreciated, thank you!
-
I run my Win 10 without problem:
P1:
AES256
SHA256
DH14
Responder Only
Mobike enableP2:
ESP
AES256
SHA256
PFS 14Your DH Group is 2 and very weak.
On Win 10 Side, i use Powershell to setup the VPN Client Profile.
Add-VpnConnection -Name "pfSense" -ServerAddress "WAN-IP" -TunnelType IKEv2 -EncryptionLevel Required -AuthenticationMethod EAP -AllUserConnection
Set-VpnConnectionIPsecConfiguration -ConnectionName "pfSense" -AuthenticationTransformConstants GCMAES256 -CipherTransformConstants GCMAES256 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -DHGroup Group14 -PfsGroup PFS2048 -PassThru
-
Thanks @NOCling I'm now able to connect via strongSwan on Android. I think the reason why I didn't originally use DH 14 is that the default Windows client is not configured for that but using your Powershell alongside updating Phase 1 got me further however I still cannot connect on Windows 10.
I still get the same error on the client side of windows with "87 The parameter is incorrect"I've updated my phase 1 to this:
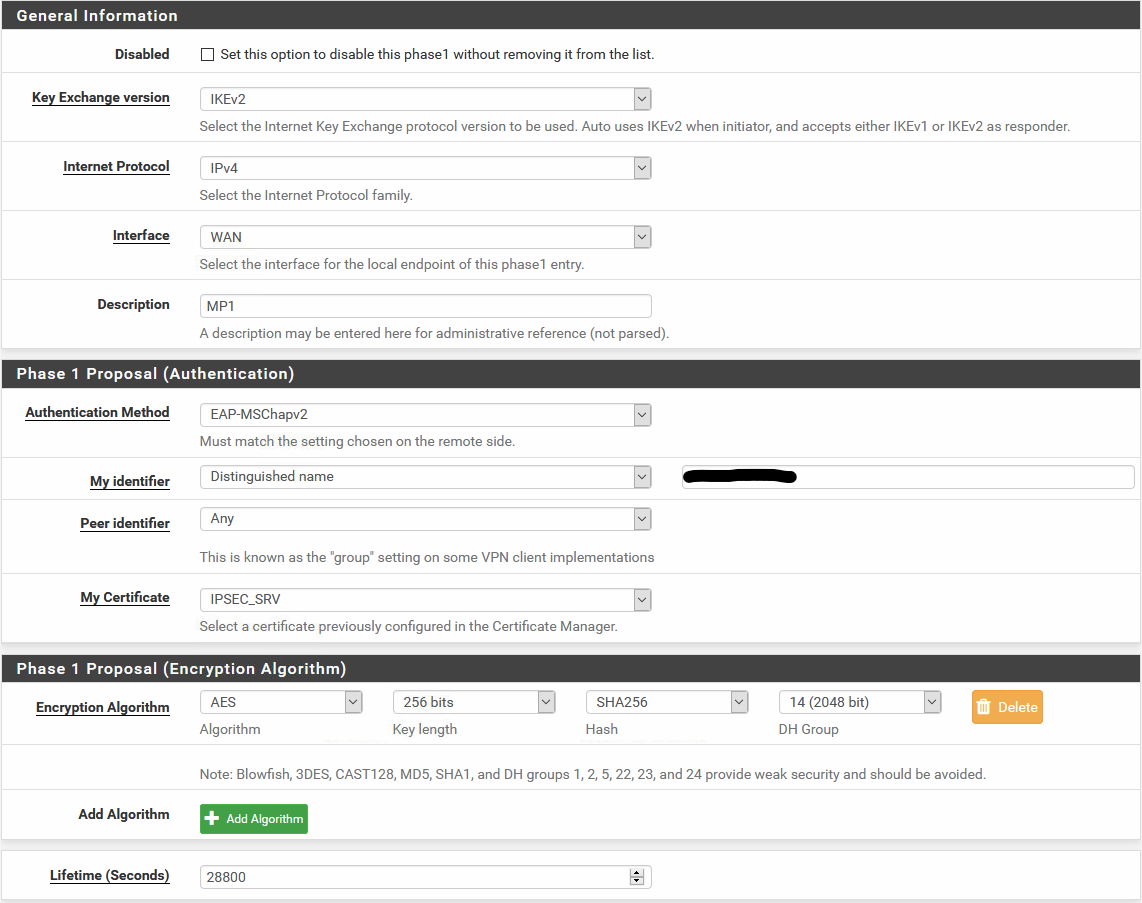
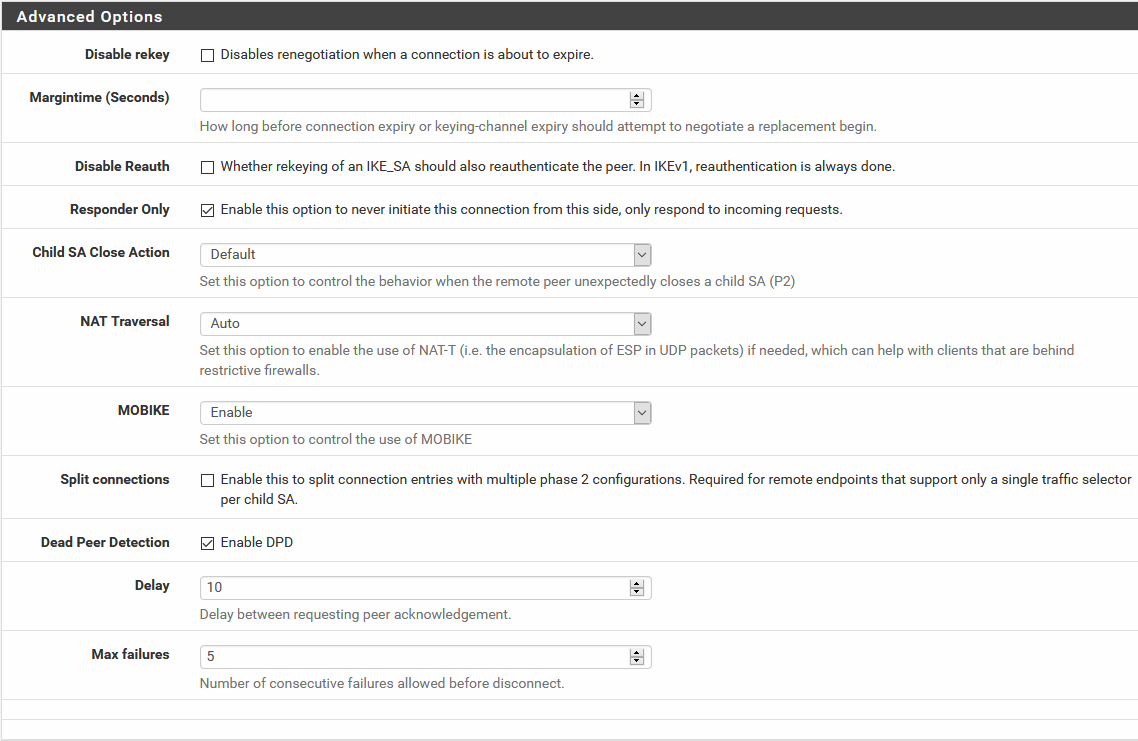
I've updated my phase 2 to this:
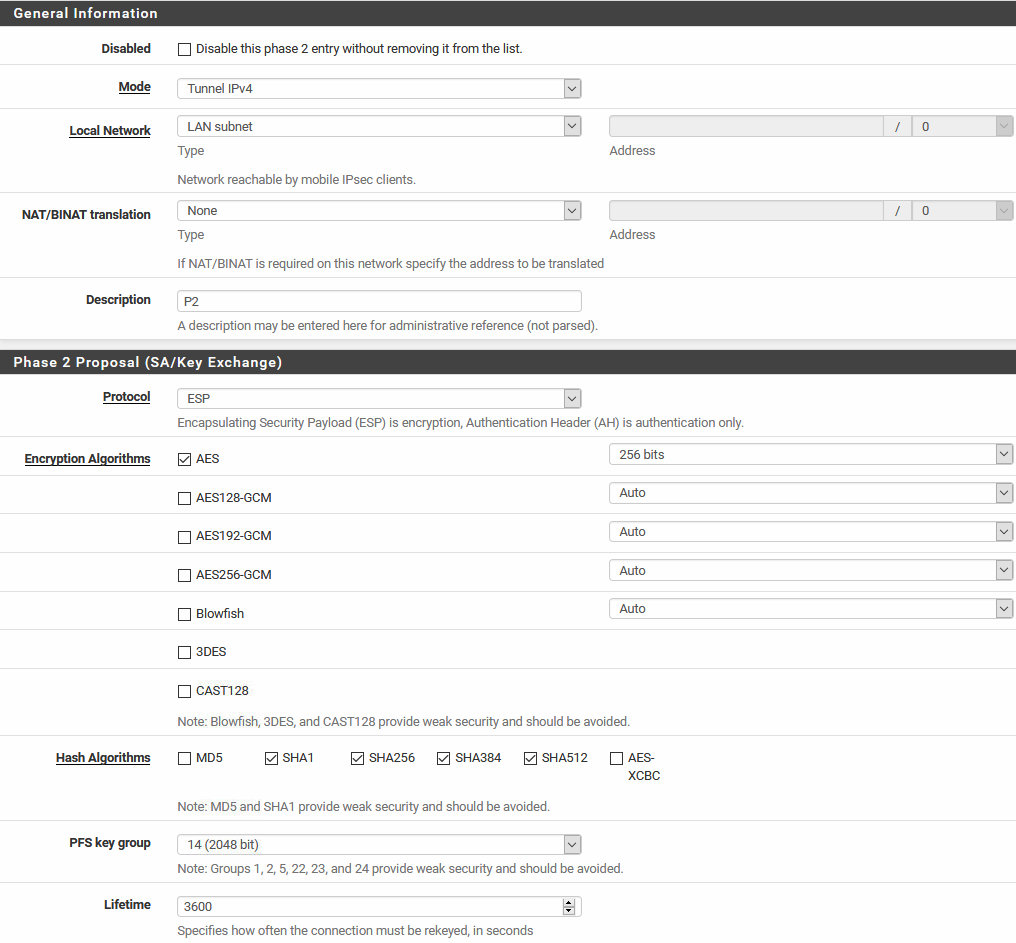
Did I miss something from your advice to finish the connection for Windows 10?
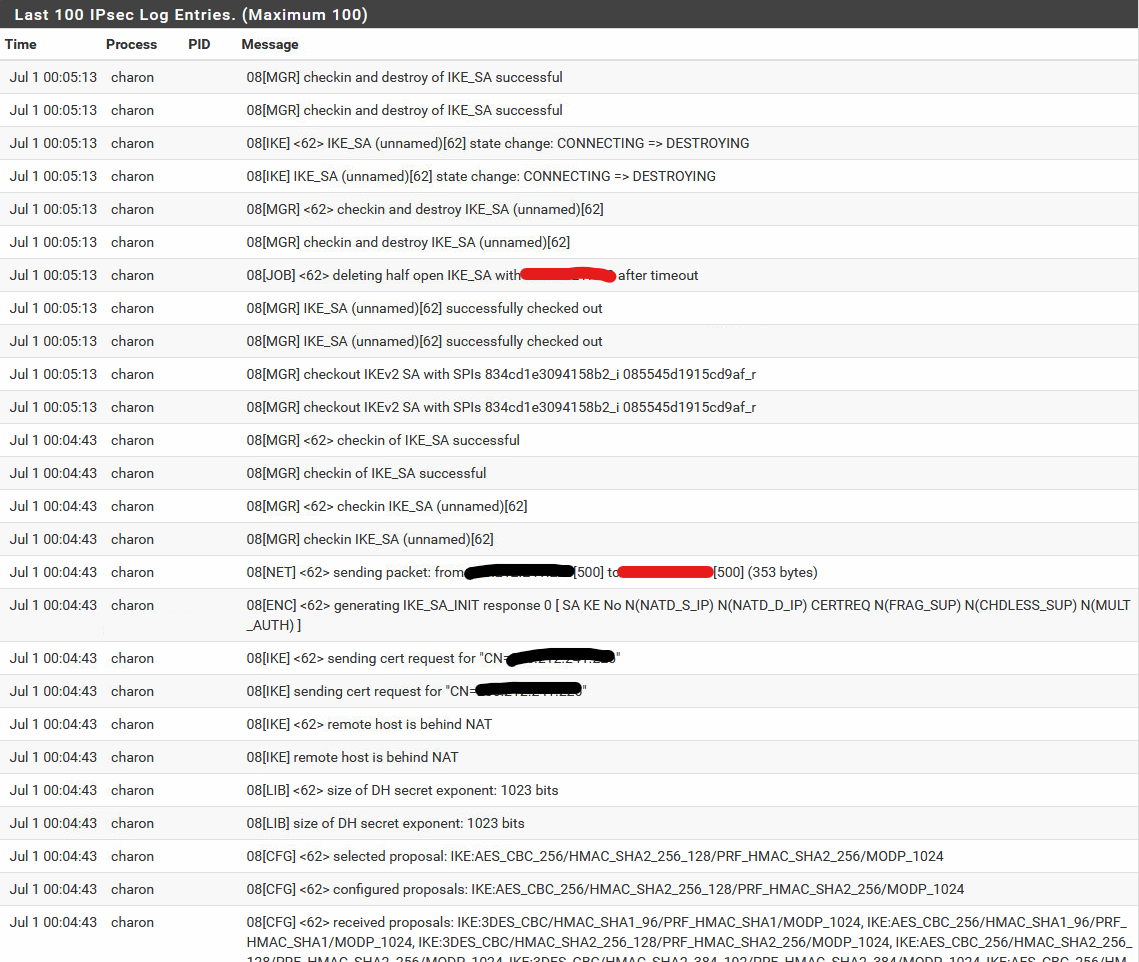
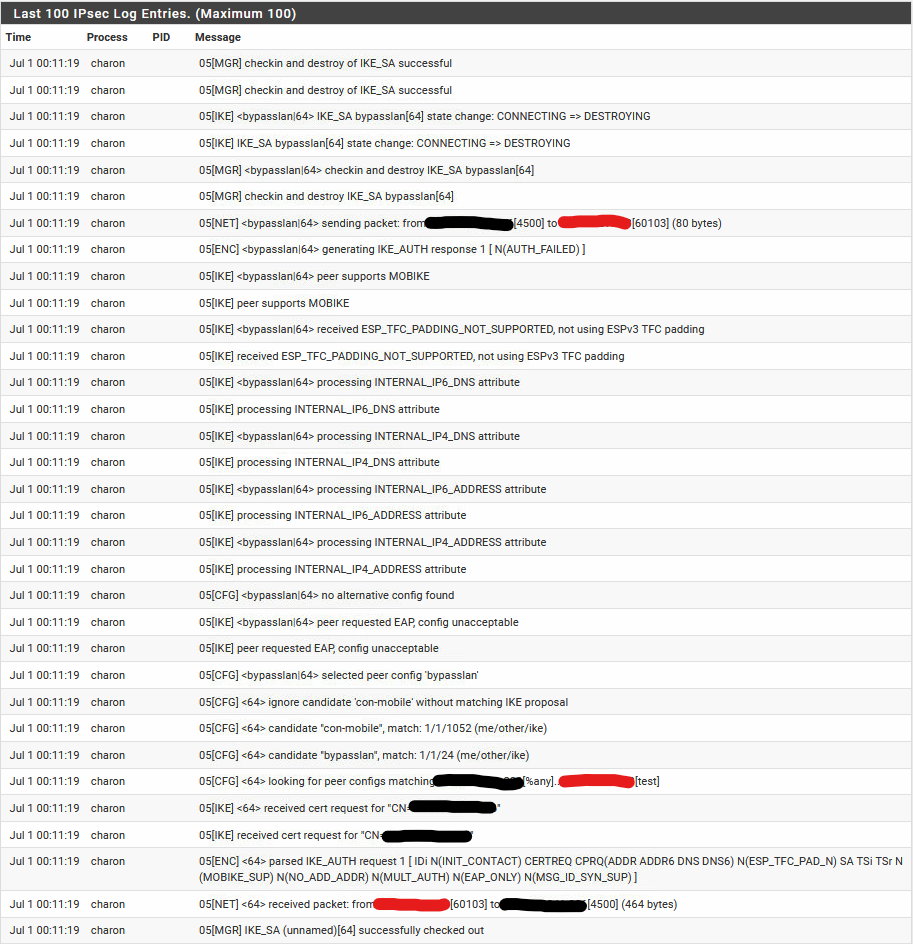
Here's the logs for the connection attempt:
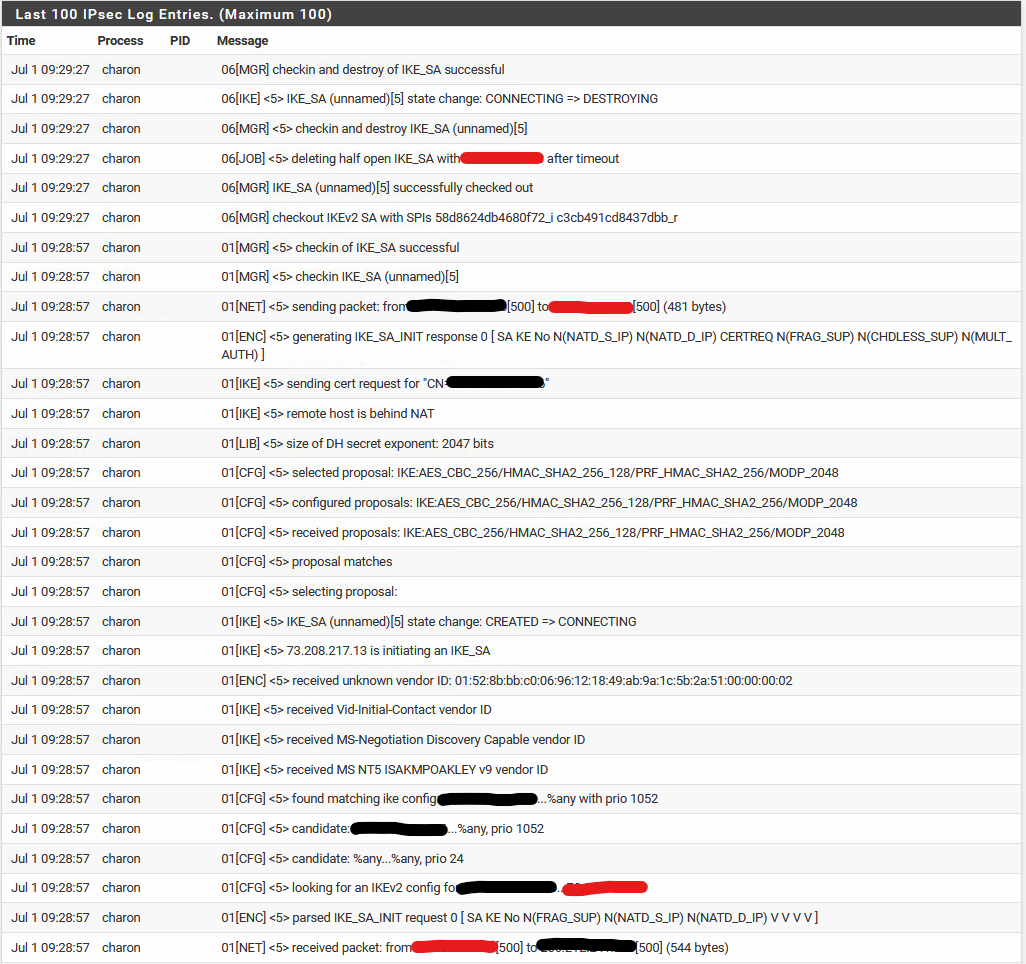
-
Bump. Here's the current pastebin of what happens when I attempt to connect using Windows 10 (https://pastebin.com/ndeHZm9W). Note, my android phone is able to connect with strong swan
-
Sorry got the wrong Line:
Set-VpnConnectionIPsecConfiguration -ConnectionName "pfSense" -AuthenticationTransformConstants SHA256128 -CipherTransformConstants AES256 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -DHGroup Group14 -PfsGroup PFS2048 -PassThru
AES 256 is right, but gave you GCMAES256 before.
-
Still getting issues: https://pastebin.com/wpWqPEYZ