NAT rule enabled on another interface than specified
-
Hello,
I've configured a Port forward NAT on an internal interface "CLIENTS" (192.168.0.0/24) but it's also NATting on my "OpenVPN" (192.168.99.0/24) interface.Is that a normal behavior? I would have expected the NAT to be performed only on "CLIENTS".
"CLIENTS" is a virtual interface (VLAN)
Thanks!
Here's the NAT rule details:
Interface CLIENTS Protocol TCP Source NONE Single host or alias Type 10.10.10.6 Destination port range MS DS Redirect target IP 10.10.10.2 Redirect target port MS DS NAT reflection Use system default Filter rule association None -
Check if NAT reflection is enabled in System > Advanced > Firewall & NAT or try to disable it in this NAT rule.
-
What would be the point of this? Why would you not just hit 10.2 in the first place?
Why would a client on 192.168.0.X try and go to 10.10.10.6 vs just going to 10.2 directly?
And even if you did redirect it, why would 192.168.0.x accept an answer from .2 vs .6? When he was trying to talk to .6
Just confused at what your wanting to accomplish here..
-
@johnpoz for migration purposes. I have a new server with a new IP and we need time to change the IP on every machines, so we translate the server's old IP to the new one until configurations are changed everywhere.
And even if you did redirect it, why would 192.168.0.x accept an answer from .2 vs .6? When he was trying to talk to .6
huh, isn't NAT done on both directions (stateful)?
-
@viragomann said in NAT rule enabled on another interface than specified:
Check if NAT reflection is enabled in System > Advanced > Firewall & NAT or try to disable it in this NAT rule.
This is the good answer! Thanks!
-
@echo4201 said in NAT rule enabled on another interface than specified:
huh, isn't NAT done on both directions (stateful)?
So some IP on the internet 1.2.3.4 - hits your wan 4.5.6.7 which you forward to 192.168.1.100... What IP does .100 see that traffic from for source? The 1.2.3.4 address.. You would have to do source natting if you want it to see say your 192.168.1.1 (pfsense IP in your 192.168.1 network) On the server..
Oh - your saying that pfsense will send that traffic back via state to as though it came from .6 -- hmmm... Can test that real quick.. You might be right since your on 2 different networks, and not a asymmetrical routing problem when you forward to client that has access to the source..
As to your migration problem? So you have IPs hard coded.. Why would you not have just hit host.domain.tld which you could then just point to whatever IP that service is running on..
If I were you, I would be changing to using a fqdn, so you don't run into such an issue in the future.
edit: Ok just tested.. My bad I was thinking the destination IP was same network as client - which would asymmetrical and client would see traffic from .2 vs .6
But in your scenario it will look like traffic came back from .6
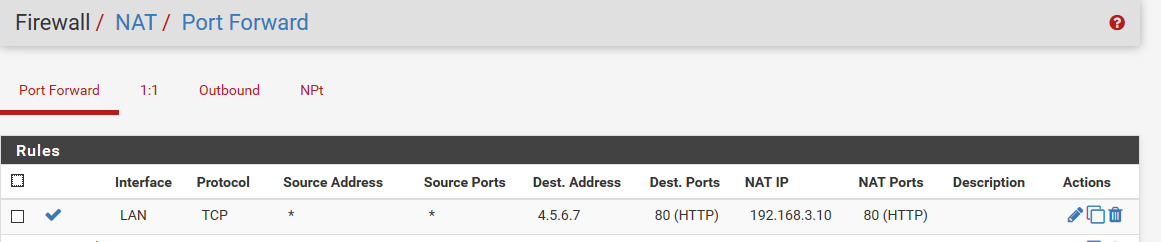
I did simple test of port forwarding 80 to 4.5.6.7 to IP on different vlan
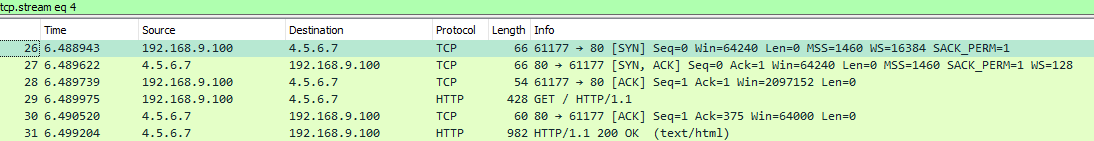
Ok so what your doing should work - but again would be simpler if you would of just used fqdn for when migrating services to new IPs.
But if you only did port forward on interface X, it wouldn't do that for interface Y.
-
Oh - your saying that pfsense will send that traffic back via state to as though it came from .6 -- hmmm... Can test that real quick.. You might be right since your on 2 different networks, and not a asymmetrical routing problem when you forward to client that has access to the source..
Yup.
As to your migration problem? So you have IPs hard coded.. Why would you not have just hit host.domain.tld which you could then just point to whatever IP that service is running on..
I agree.
-
See my edit - just tested
-
@johnpoz
yup thanks, that's what I was expecting.as for :
But if you only did port forward on interface X, it wouldn't do that for interface Y.
as viragomann said, it was the NAT reflection that was causing it
-
Hmmm, what was system default set too? Mine is disabled - but it defaults to what pure nat or nat+proxy?
I really don't see how that would of come into play on a different interface.. Can try and duplicate it - what setting did you have in system, and can set mine to that and then look at the exact rules being created..