Windows Server DNS Server can't forward to pfSense
-
@netblues Yeah everything is allowed at the moment so it's fine

-
@Hekmil Is dns resolver service running on pf? is it listening on lan interface?
-
@netblues yes it's running, I can resolve any domain from the pfSense.
The configuration is the default one, listening on all interfaces.
It's like the Windows machine can't forward the DNS request to the pfSense.
-
@Hekmil No. You run nslookup
What is the lan ip of pf sense?
Try running nslookup from pf cli
pf sense it self can resolve without a local resolver if configured to use wan connection dns for example. -
@netblues Yes I was talking about running a nslookup from the pfSense CLI, sorry if it wasn't clear. From the CLI it manage to resolve.
My LAN ip of my pfSense is 172.16.1.2
Yes the pfSense does use the WAN connection when resolving
-
@Hekmil not much left to do.
can you ping pfsense lan from windows server? -
@netblues Yeah that's why i'm asking here, because I'm out of option
Yes all my machines can ping together. But only pfSense can ping outside the NAT (for example 8.8.8.8).
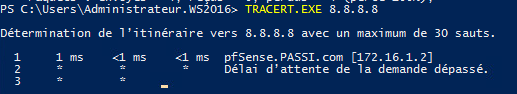
Here is a tracert command to 8.8.8.8 which timeout after reaching pfSense LAN interface. The firewall log :
-
And you cant nslookup from everywhere else with pfsense lan ip but you can from pfsense cli using lan ip.
Anything on floating rules? -
@netblues Wait I was only trying to do
nslookup cnn.comon the cli not using lan IP. If I do that it doesn't work of course sorry. It's like the resolving DNS service was not enabled for all interfaces except it is.Floating rules are empty.
-
@Hekmil please post services resolver settings.
Have you tried restarting resolver service? -
@netblues Here are my setting of my resolver :
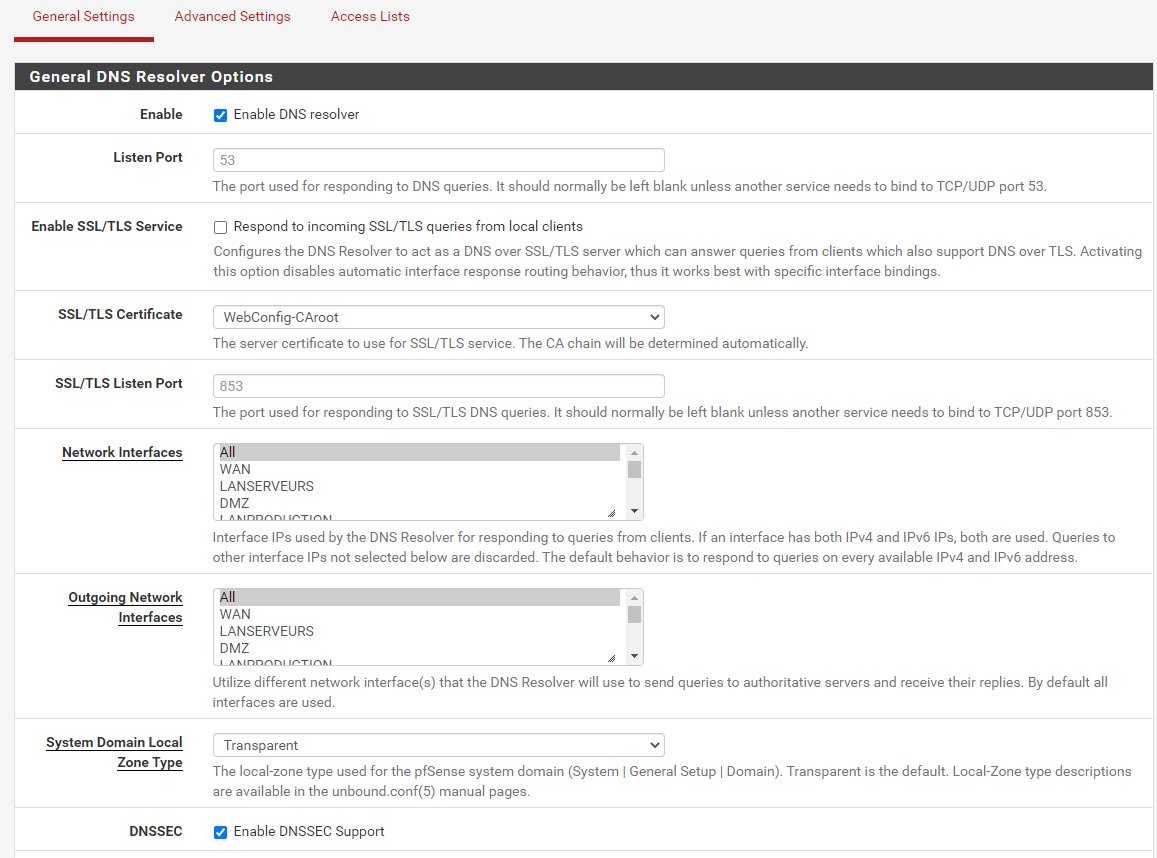
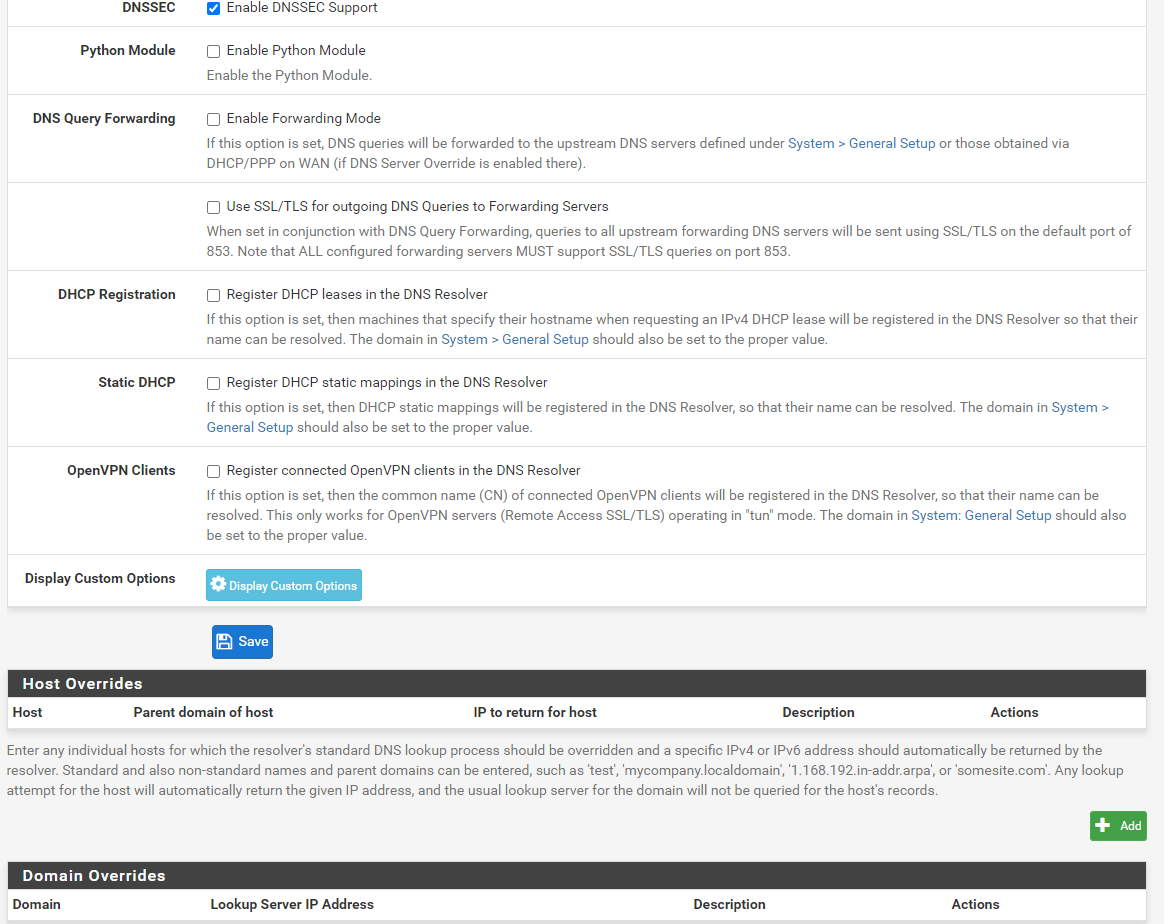
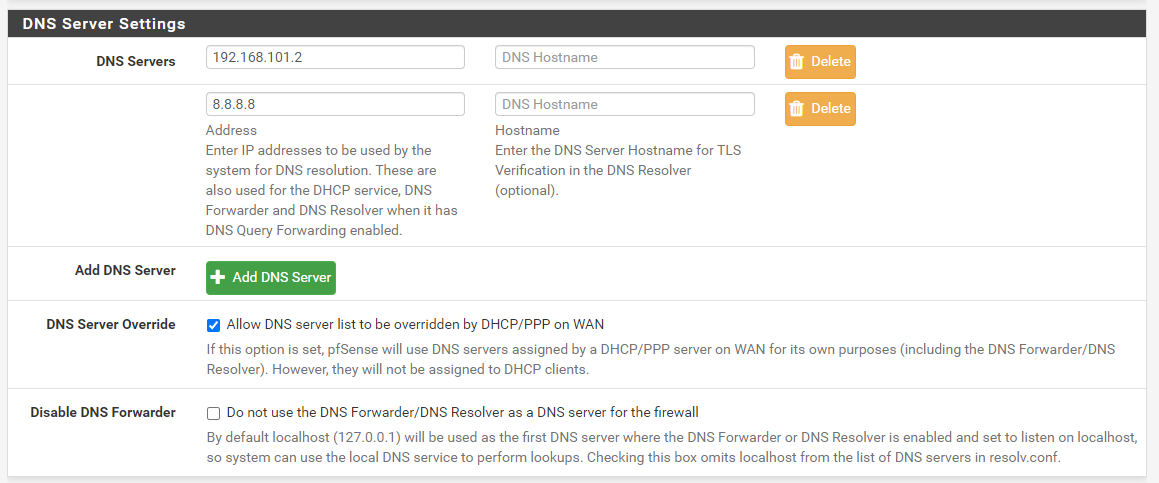
192.168.101.2 = NAT GatewayYes the service and even the machine has been restarted trying fixing the issue
-
@Hekmil you dont really need any dns servers if pf can reach the internet..
However this is irrelevant.
Dns resolver should be listening on lan anyway.
Do restart the srrvice and look at status system logs resolver logs for anything strange. -
@netblues True that
Nothing really usefull from the logs :
-
@Hekmil output of sockstat -l please
-
USER COMMAND PID FD PROTO LOCAL ADDRESS FOREIGN ADDRESS root sockstat 96752 13 stream /var/run/php-fpm.socket unbound unbound 52451 3 udp6 *:53 *:* unbound unbound 52451 4 tcp6 *:53 *:* unbound unbound 52451 5 udp4 *:53 *:* unbound unbound 52451 6 tcp4 *:53 *:* unbound unbound 52451 7 tcp4 127.0.0.1:953 *:* unbound unbound 52451 12 stream /var/run/php-fpm.socket unbound unbound 52451 13 stream /var/run/php-fpm.socket unbound unbound 52451 14 udp4 *:52518 *:* root syslogd 45622 6 dgram /var/dhcpd/var/run/log root syslogd 45622 7 udp6 *:514 *:* root syslogd 45622 8 udp4 *:514 *:* root syslogd 45622 9 dgram /var/run/log root syslogd 45622 10 dgram /var/run/logpriv root syslogd 45622 12 stream /var/run/php-fpm.socket root syslogd 45622 13 stream /var/run/php-fpm.socket root php-fpm 17426 3 dgram (not connected) root php-fpm 17426 4 udp4 *:* *:* root php-fpm 17426 5 udp6 *:* *:* root php-fpm 17426 13 stream /var/run/php-fpm.socket root ntpd 37361 20 udp6 fe80::20c:29ff:fe82:c819%em0:123 *:* root ntpd 37361 21 udp4 192.168.101.40:123 *:* root ntpd 37361 22 udp6 fe80::20c:29ff:fe82:c823%em1:123 *:* root ntpd 37361 23 udp4 172.16.1.2:123 *:* root ntpd 37361 24 udp6 fe80::20c:29ff:fe82:c82d%em2:123 *:* root ntpd 37361 25 udp4 172.16.101.2:123 *:* root ntpd 37361 26 udp6 fe80::20c:29ff:fe82:c837%em3:123 *:* root ntpd 37361 27 udp4 172.16.4.2:123 *:* root ntpd 37361 28 udp6 fe80::20c:29ff:fe82:c841%em4:123 *:* root ntpd 37361 29 udp4 172.16.200.2:123 *:* root ntpd 37361 30 udp6 ::1:123 *:* root ntpd 37361 31 udp4 127.0.0.1:123 *:* root login 80435 3 dgram (not connected) root charon 22942 5 dgram (not connected) root charon 22942 8 stream /var/run/charon.wlst root charon 22942 11 udp6 *:500 *:* root charon 22942 12 udp6 *:4500 *:* root charon 22942 13 udp4 *:500 *:* root charon 22942 14 udp4 *:4500 *:* root charon 22942 20 stream /var/run/charon.ctl root charon 22942 21 stream /var/run/charon.vici root starter 22764 5 dgram (not connected) root nginx 57467 5 tcp4 *:443 *:* root nginx 57467 6 tcp6 *:443 *:* root nginx 57467 7 tcp4 *:80 *:* root nginx 57467 8 tcp6 *:80 *:* root nginx 57350 5 tcp4 *:443 *:* root nginx 57350 6 tcp6 *:443 *:* root nginx 57350 7 tcp4 *:80 *:* root nginx 57350 8 tcp6 *:80 *:* root nginx 57077 5 tcp4 *:443 *:* root nginx 57077 6 tcp6 *:443 *:* root nginx 57077 7 tcp4 *:80 *:* root nginx 57077 8 tcp6 *:80 *:* root dpinger 27696 5 dgram (not connected) root dpinger 27696 6 stream /var/run/dpinger_GW_WAN~192.168.101.40~192.168.101.2.sock root devd 415 4 stream /var/run/devd.pipe root devd 415 5 seqpac /var/run/devd.seqpacket.pipe root check_relo 358 3 stream /var/run/check_reload_status root php-fpm 322 3 dgram (not connected) root php-fpm 322 4 udp4 *:* *:* root php-fpm 322 5 udp6 *:* *:* root php-fpm 322 13 stream /var/run/php-fpm.socket root php-fpm 321 3 dgram (not connected) root php-fpm 321 4 udp4 *:* *:* root php-fpm 321 5 udp6 *:* *:* root php-fpm 321 13 stream /var/run/php-fpm.socket root php-fpm 321 14 dgram (not connected) root php-fpm 319 3 dgram (not connected) root php-fpm 319 4 udp4 *:* *:* root php-fpm 319 5 udp6 *:* *:* root php-fpm 319 15 stream /var/run/php-fpm.socket -
@Hekmil as you see, service unbound is listening on all interfaces.
So nslookup shouldn't be complaining.
This is really strange.Can you telnet 172.16.1.2 (pfsense lan) on port 53 from pf cli?
-
@netblues Yes indeed
Yes it works :
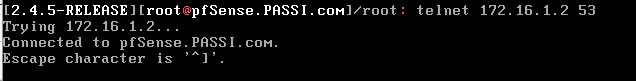
-
@Hekmil so unbound works.
dig @172.16.1.2 cnn.comalways from cli.
-
You need to let the
unboundDNS server within pfSense do the name resolution for you. Forget your NAT gateway DNS. And remove those two IP addresses from the General Settings tab in pfSense. Out of the box,unboundis ready to operate in resolver mode, which means it will query the root servers and proceed down the domain tree to find the IP for the FQDN. If you want to put any address on the General Settings page in that DNS box, put 127.0.0.1. And uncheck that "DNS Server Override" box. You don't want that in your setup.Once you do that, go under DIAGNOSTICS > DNS LOOKUP and see if a domain such as "cnn.com" or "google.com" resolves properly. It should.
Once you get that working, then go back and point your AD DNS Server to forward to pfSense instead of that NAT gateway. DNS lookups should then work properly.
Last tip -- sounds like you may not be fully versed in DNS terminology. Make sure you understand the distinction between a DNS resolver and a DNS forwarder. They are not the same. In your case, I think letting
unboundon pfSense operate in its normal resolver mode is what you need. However, if you truly want to use DNS forwarding, then you will need to configure that setup inunboundon pfSense. -
And you may have an issue with routing while trying to use that NAT gateway DNS server. Does it have a proper route back to your Windows client? In other words, can it find it?
The fact you mentioned pings not working from the Windows client side would indicate either a firewall rule or rules that is blocking it, or there is a routing problem upstream such that the pinged host doesn't know where to send the reply.
First thing to check would be to sniff the WAN interface of pfSense while pinging an external host from the Windows client. Do you see the packet leave the pfSense WAN? If not, check firewall rules and default routes on the Windows client. If you see the packet leave the WAN but no reply comes back, then check upstream routing and/or firewall settings. You can use the built-in sniffer tool available under the DIAGNOSTICS menu on pfSense.