Are the Autocreated ISAKMP rules needed?
-
Are the Autocreated ISAKMP NAT rules needed if I am not using IPSEC?
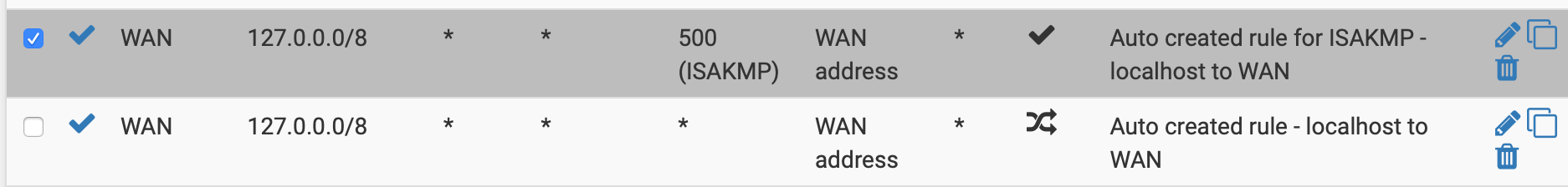
The above is for the loopback. But are they needed for the LAN network ?
THanks!
-
Less and less these days. Most modern IPsec clients you'd have on your network will happily use NAT-T and won't need that static source port rule for udp/500.
The primary exception is if you have a device on your local network which needs its own site-to-site IPsec tunnel to a remote endpoint, but even those are more forgiving. Unless the remote end has some seriously outdated VPN setup.
It's still in the config because it's relatively harmless to keep. Unlikely to cause problems and still benefits some (admittedly rare, now) cases.
-
The static port section under NAT in the docs explains that default rule.
https://docs.netgate.com/pfsense/en/latest/book/nat/outbound-nat.html#static-port.Found this as well, which kind of says its a requirement.

-
@Raffi_ said in Are the Autocreated ISAKMP rules needed?:
Found this as well, which kind of says its a requirement.
That is only for IPsec endpoints (like if pfSense was terminating the connection itself) -- that doesn't apply to routers/firewalls/NAT in between endpoints.
-
@jimp said in Are the Autocreated ISAKMP rules needed?:
@Raffi_ said in Are the Autocreated ISAKMP rules needed?:
Found this as well, which kind of says its a requirement.
That is only for IPsec endpoints (like if pfSense was terminating the connection itself) -- that doesn't apply to routers/firewalls/NAT in between endpoints.
Meaning if an IPsec tunnel is setup in pfSense? So would it make sense to auto add this rule only if someone adds a IPsec tunnel?
-
That NAT rule is not relevant to IPsec on pfSense -- only connections passing through pfSense. strongSwan wouldn't initiate from localhost or LAN and go out and have NAT applied. It binds directly to the WAN interface(s).
-
In the past I believe these rules caused me problems when multiple IKEv2 clients tried to initiate connections too close together (i.e., before the states from the previous attempt expired). I created my own patch to disable generation of these rules while still letting me use "Automatic Outbound NAT". My clients are now using WireGuard so I'm no longer applying the patch.
It would be convenient if you could disable generation of these rules with, for example, a checkbox in "System / Advanced / Firewall & NAT".
-
Thanks for the answers folks. Follow-up:
So I can delete these rules and have no issues?
@jimp How did you get WireGuard running on the pfSense?
-
Also, why is the loopback address using ISAKMP?
-
@powerextreme said in Are the Autocreated ISAKMP rules needed?:
Also, why is the loopback address using ISAKMP?
It normally isn't, but it's included in the networks for automatic outbound NAT rules, and each entry in that list gets the udp/500 static port rule.