OpenVPN not routing all traffic despite Redirect Gateway checked
-
I have an OpenVPN server configured on my SG-1100. I am able to connect and authenticate with my Android phone as a client, and access local IP on the LAN. The phone is not able to access the internet, despite having checked the box for "Force all client-generated IPv4 traffic through the tunnel." under Redirect IPv4 Gateway in the Tunnel settings. The Firewall rules for LAN and OpenVPN are attached, and look correct to me, but I am a new user and still learning. Help is much appreciated.
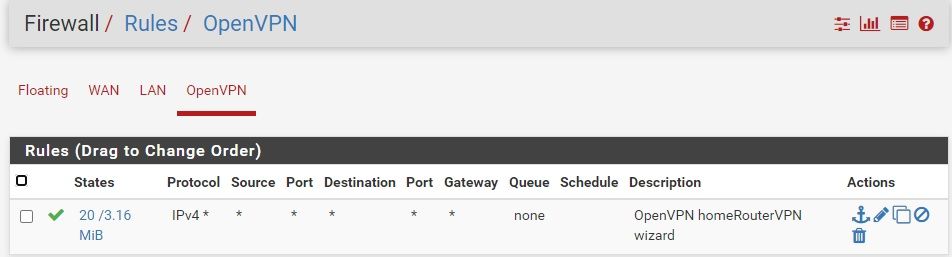
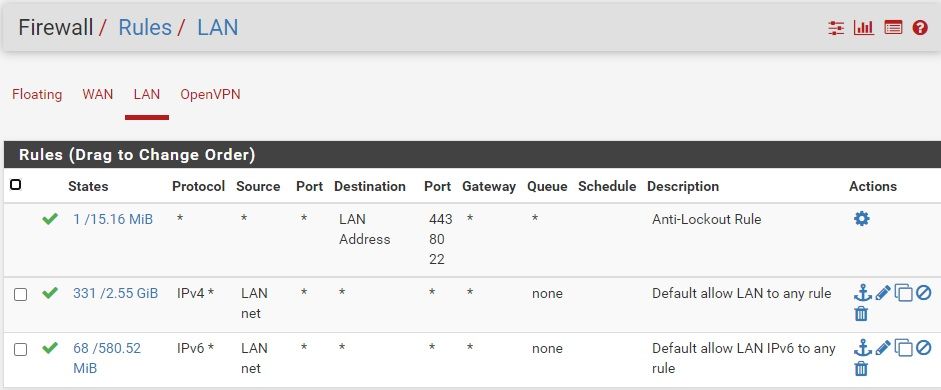
-
This is expected.
Pushing all your traffic through vpn won't get you internet!
For this to happen, pf needs to also nat your vpn ip ip to the Internet.
Check your outbound nat rules. -
@netblues thanks for your response
I checked the outbound NAT (shown below), and it does have the OpenVPN tunnel subnet (10.55.201.0/24) in the automatically generated rule:
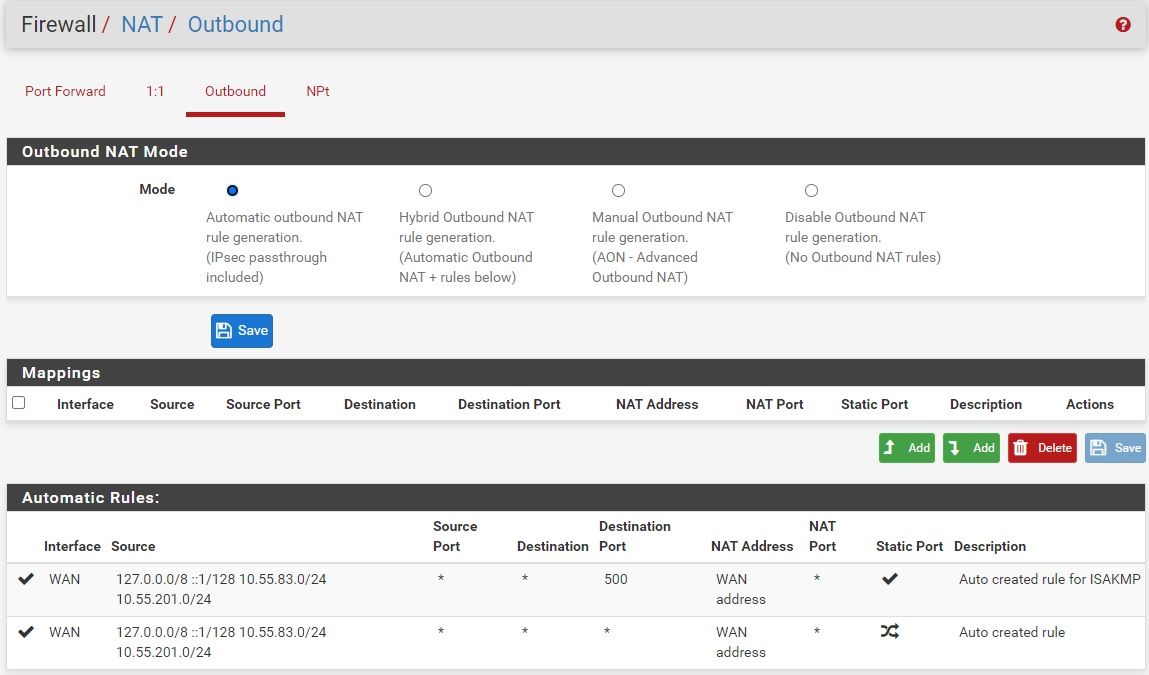
-
@wmcneil Can you possibly ping some internet ip from vpn?
e.g 1.1.1.1 or 8.8.8.8
If nat is ok, and internal resources are reachable, then it could be dns
Check advanced client settings on openvpn server config page. -
@netblues Running ping on the VPN Client, I am able to reach 8.8.8.8, as well as a DNS server (209.18.47.62) that has been assigned by DHCP on the WAN. When I try and ping www.intel.com, I am getting Unknown Host
-
@wmcneil Post client dns settings from openvpn server.
Seems like your vpn clients don't have a dns.
Are you using dns resolver (unbound) on pf? -
@netblues VPN DNS and DNS Resolver(it is enabled) Settings below.
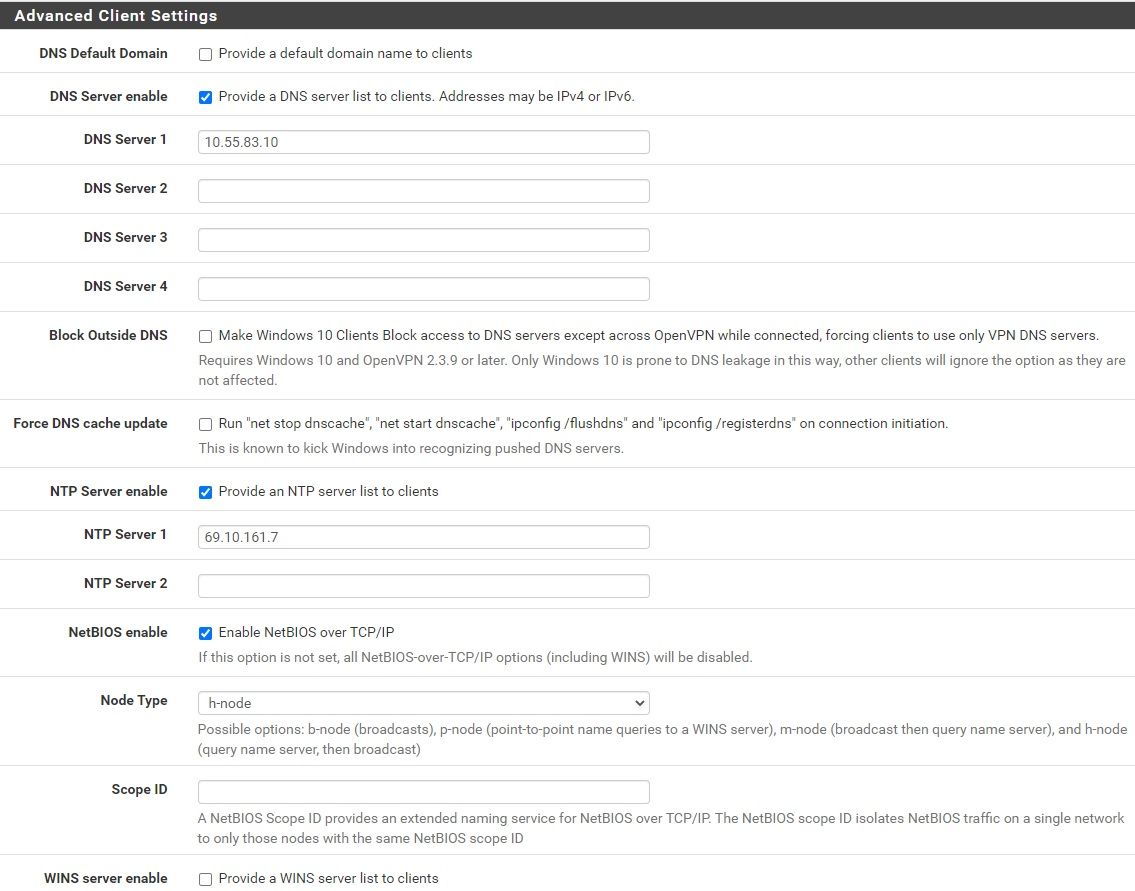
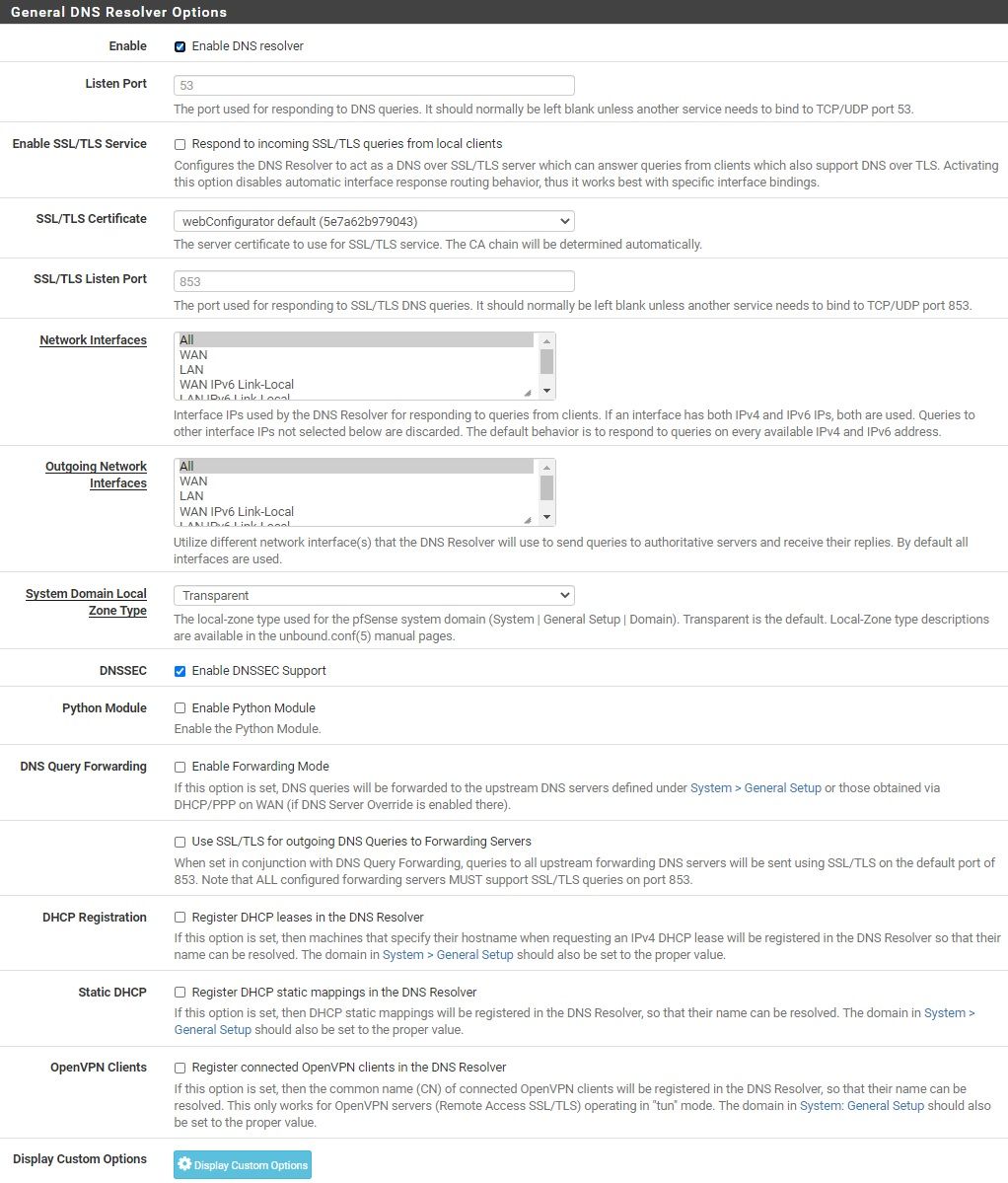
-
@wmcneil So what is on 10.55.83.10? Can you ping it?
Can you use it via nslookup? -
@netblues 10.55.83.10 is the LAN address of my pfSense box (SG-1100). Should I be using something else here?
I can successfully ping that IP from my vpn client. I don't have a nslookup on my vpn client (it is my android phone), but I do have traceroute, and that failed to receive any response.
-
@netblues I removed 10.55.83.10, and passed no DNS servers to the VPN. Things are now working....Looks like DNS resolver is working for the VPN clients by default, so no list has to be passed.....thank you very much for your help.
-
@wmcneil actually vpn clients are using their internet provider dns. You might have issues accesing internal resources by name.
-
@netblues I could provide the same list of DNS servers that the WAN is using to the VPN. The only drawback is that I am allowing the WAN DHCP DNS servers to override (be placed before) the primary and secondary servers specified in System / General Setup. So I can specify the current numeric IP of those servers for the VPN, but if they change they will not be automatically updated.
-
@wmcneil The correct way is to have openvpn clients use pf sense resolver, for long term stability.
Perhaps specifying the openvpn server ip as dns would work for you. -
@netblues How do I configure pfsense so that the openvpn clients use pfsense resolver?
-
@wmcneil First assign an interface to openvpn.
Then restart openvpn.
dnsresolver should be listening to this new interface too.
So specifying a dns of 10.55.201.1 should work. -
@netblues I created a new interface named OPT2, and assigned it to my OpenVPN server. (settings and status below). I have not assigned any DNS to the OpenVPN yet, because I'm not following why you think 10.55.201.1 will work, as that is an available IP for assignment to a tunnel client?
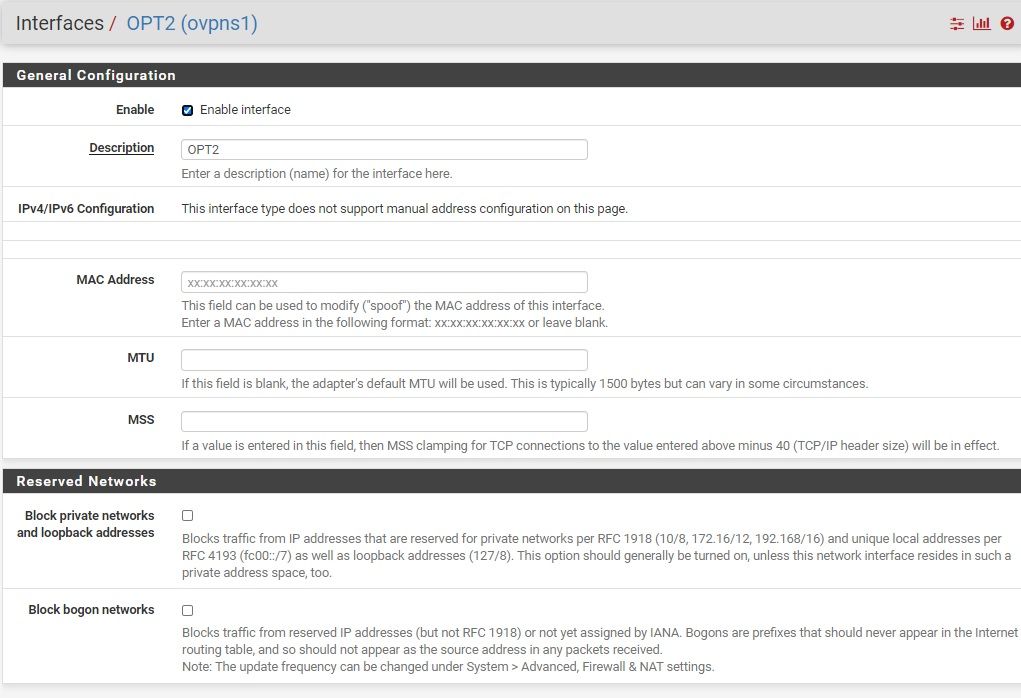
-
@wmcneil In openvpn the first ip of openvpn tunnel network is always assigned to the server, ie pfsense
-
@netblues Yes, I see now that a client is connected to the VPN the interface assigned to it (OPT2) has been assigned the first tunnel address (10.55.201.1). That said, it does not work to use 10.55.201.1 as the VPN DNS server. If I use the SG-1100 LAN IP (10.55.83.10) as the VPN DNS server, things are working.
-
@wmcneil Ok then, the important thing is to have a pf working dns.
Just remember not to block access to dns with rules.