Sourcing default firewall blocks
-
Previously my firewall logs were filling up with many LAN blocked sites and I could not find the source of the rules that were causing each block. Recently I had trialed pfBlocker and Snort. Although those packages have been removed I thought maybe that the rules that either of those packages was still in place somewhere and didn't get removed properly.
I've decided to reset the Netgate to factory defaults to rule out any sticky configs. Well, it's still logging some sites and I don't know the reason.
The only changes I have made from default was:
*changing the Netgate LAN ip address
*disabled logging of default WAN rules
*created a bottom rule to log what was being blocked
*reset all states
*reset all logsThis is what my LAN rules currently look like:
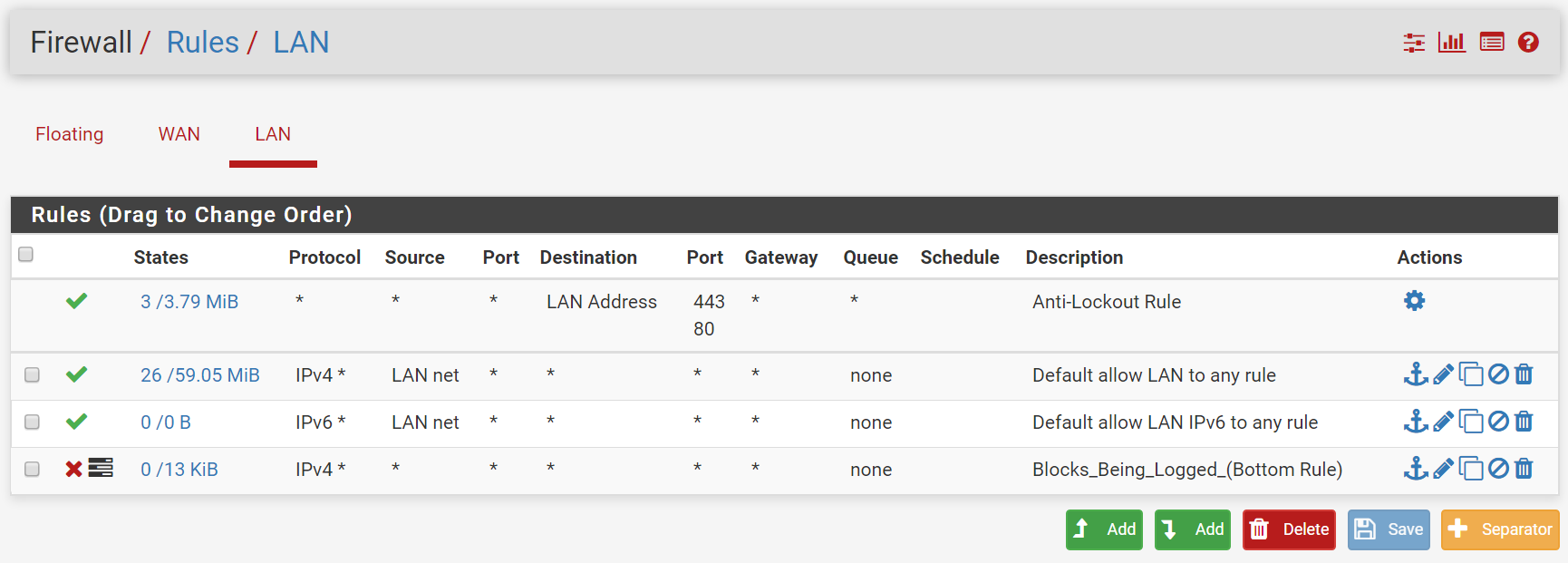
Here's what's being logged as blocked.
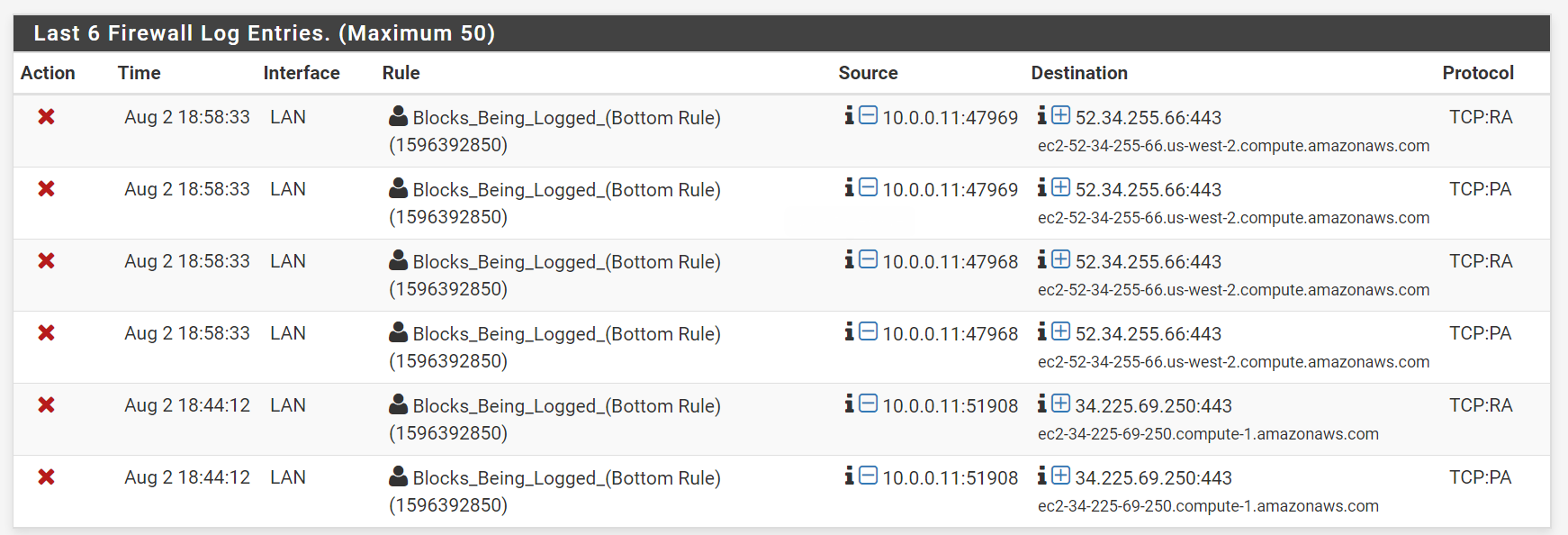
10.0.0.11 is my laptop. I simply surfed a few sites to attempt to generate some logs.
I should also note, i am not seeing any interruption of web viewing or degrading of performance to these sites that i tested surf capabilities. So essentially, Im not experiencing any problems. I just would like to know the source of these blocks.
-
Those are all TCP ack packets. The client is sending them after the connection has closed.
See: https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html
Steve
-
@stephenw10 said in Sourcing default firewall blocks:
TCP ack packets
Makes sense. Thank you very much.