ATT BGW210 pfsense bypass with multiple static ip addresses
-
Hello all,
I purchased from ATT a block of 8 ip's 5 usable and I'm trying bypass the ATT RG using the pfatt solution found in the following github repo. https://github.com/MonkWho/pfatt
I'm using a Protectli FW4B loaded with pfsense.
I configured everything using the readme from the repo and the following reddit link.
https://www.reddit.com/r/PFSENSE/comments/ag43rb/att_bgw210_true_independent_bridge_mode_uverse/
This is my setup.
[AT&T ONT] | {Protectli FW4B} |___________[ngeth0/igb0] [igb1]__________________[RuckusSwitch] [igb2] [igb3]__________________[BGW210-700's ONT port]Here is what it physically looks like.
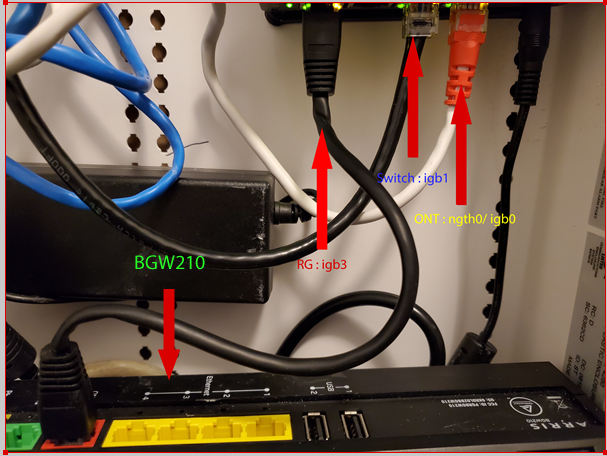
I have the pfatt script running and it seems to be working fine but I'm not sure its configured properly.
I have 5 usable IP's assigned by ATT.
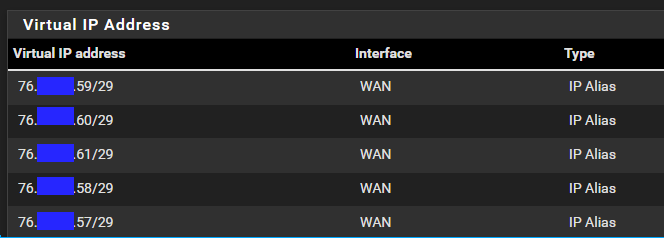
5 Ip Address range76.x.x.57 - 61
gateway: 76.x.x.62The addresses are setup as Virtual IPs.
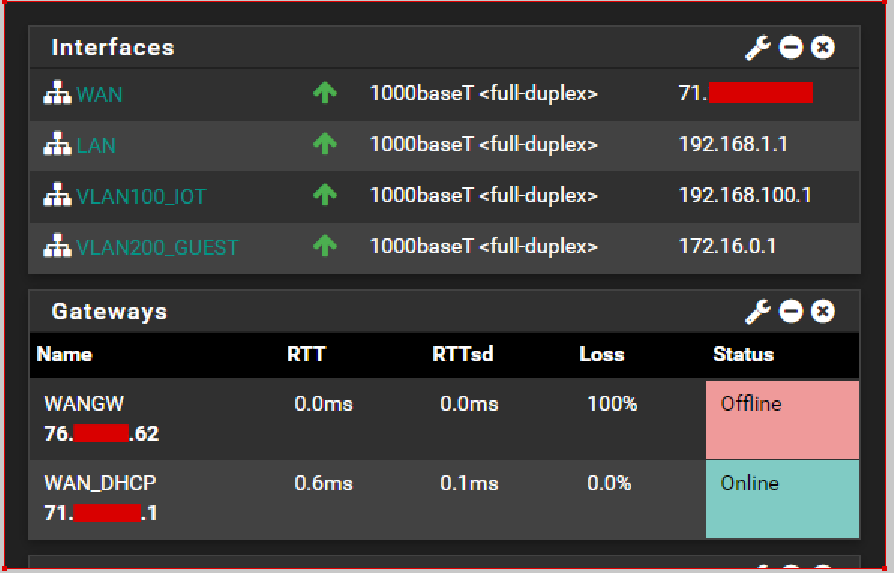
My WAN is getting is getting a DHCP address from ATT of 71.x.x.x.
 .
.I have some Nat/Rules in place that seem to be doing what I want to do.
Nat:
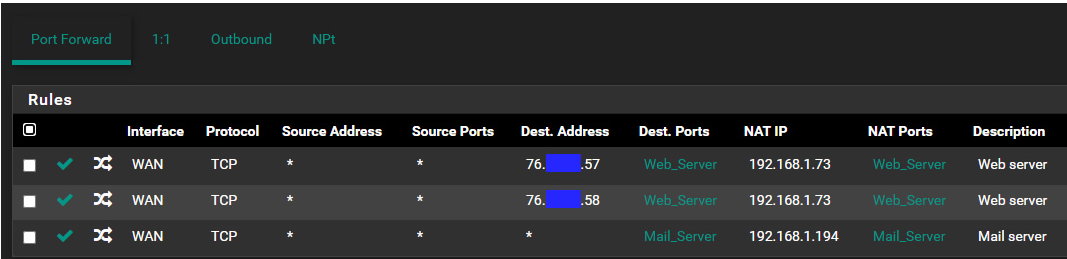
Rules:
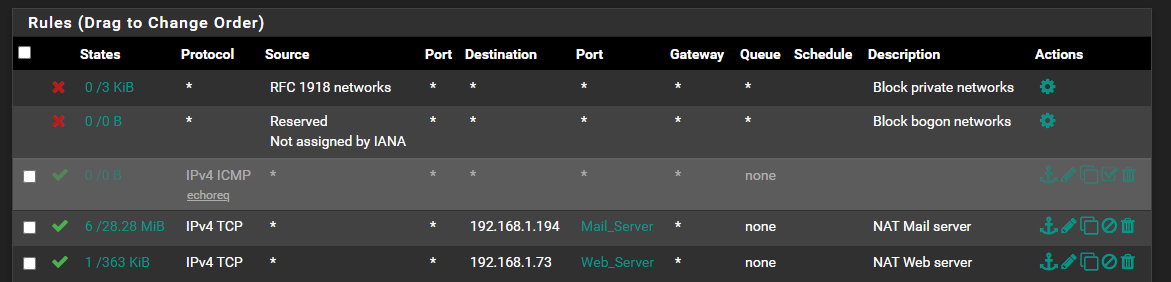
I guess the one thing I don't understand is that I would think I could bind the Wan to one of my static IP and the use the rest as Virtual Ips. However when I try to bind to one my of my IP, I loose all outside access.
Question, is this the way its supposed to be setup or am I missing anything?
Thanks in advance,
KC -
Bump!
-
Our setup was very similar, so what I did may also work for you. I wanted to be able to access a VPN with one of the static IP addresses, and use 1:1 NAT for the other static IP addresses. What I did may not be optimal, so if anyone has suggestions or recommendations, that would be great.
- When you do the pfatt setup, a virtual interface (ngeth0) is created for the Alcatel-Lucent ONT connection and the physical network adapter (ibg0) remains unassigned in the interfaces menu. The pfatt instructions said to not do anything with the ibg0 assignment in pfsense, but I deviated from that instruction.
- I didn't create an additional gateway for the static IP block, I think you should delete that, and any static routes you defined.
- Delete the virtual IP address assignment for the static IP address that you want to associate with any services running on pfSense. I'm going to assume you deleted the VIP for 76.xxx.xxx.57.
- Go to Interfaces > Assignments, for your setup, add the interface for ibg0, call it something (OPT1), and configure it with the static IP address that you made available in step 3> 76.xxx.xxx.57/32, for example. I left the mac address blank so it is automatically assigned. I set the IPv6 option as Track interface, and set it to track the WAN (ngeth0) interface. Gateway set to none. Save settings.
- After this, I deleted the P1 and P2 ipsec tunnels and disabled l2tp. I recreated those things, but selecting the physical interface created in step 4 (OPT1) as the interface for ipsec P1 and L2TP. After saving, disable the L2TP server, hit save, wait, enable the L2TP server, hit save, wait. Then check the L2TP log to make sure it's listening on the correct IP address.
- I had to add some firewall rules to pass the VPN traffic, but I'm not sure why, that was done automatically when I used the dynamic IP to access the VPN.
- The interface for the virtual IP addresses should still be WAN, not OPT1. 1:1 NAT still works as expected.
Additional notes:
- If you are trying to setup a static IP address for a VPN, I suggest to get the VPN settings to work reliably with the dynamic IP address, record all of your settings, and then make these changes for the static IP address. It is much easier to troubleshoot one thing at a time.
- The interface assignment for L2TP seemed to be picky and difficult to assign. If you're having trouble with the VPN connection when switching to the static IP, check the L2TP log to make sure it is listening on the correct IP address.
- I didn't explicitly use the "public gateway IPv4 address" that was provided (76.xxx.xxx.62 in your example) anywhere in this configuration.
- My internet speed varies during the day, and it doesn't seem to be any different after these changes.
Any feedback on ways to improve this configuration are welcome.
It's almost Friday!
-
Although unrelated, how much do those ip addresses cost?
-
@user_three $15 a month with ATT.