Firewall rules to create a guest network
-
@netblues This wouldn't help at all, because he just has one AP for all of his devices, trusted and untrusted.
-
@Bob-Dig The op also says that he has valuable pc's, so we can assume they are wired.
But even if thats the case, the wifi lan can be segmented with firewall rules and access cam be given to specific devices
Yes its not top security, macs can be spoofed et al. Finding an old wifi router and using it as a second ap is also a zero cost scenario -
Thank you @netblues.
@Bob-Dig is right. I currently have a single AP (which is the old wifi router) for my trusted and untrusted devices (even my trusted PCs are wireless, not wired).
Do you know if they sell WiFi APs that have the ability to create a guest network?
Related but slightly different question, is there a WiFi AP that comes highly recommended to work well with Netgate hardware (specifically SG-1100)?
thanks.
-
Yes many APs can do that. The one you're using might be able to, what is it?
The AP (or router running as an AP) needs to be able to create multiple SSIDs and assign them as VLANs. Then you can add that VLAN (or multiple VLANs) as a new interface is pfSense and filter traffic to/from it as required.
Steve
-
I am using Netgear Nighthawk R7000 (my old router as an AP).
It can create a separate SSID, but an option "Allow guests to see each other and access my local network" is grayed out in AP mode. I am reading that to mean that as an AP, both SSID's will be on the same subnet. Which sort of doesn't make sense to me. Why have the option to create a 2nd SSID, if it cannot be separated logically?
(Please excuse me - I am using words that I don't understand)
-
@DrPhil Same with my Asus. But with modified/alternative Firmware, you can have vlans...
-
@DrPhil said in Firewall rules to create a guest network:
I am using Netgear Nighthawk R7000 (my old router as an AP).
IWhy have the option to create a 2nd SSID, if it cannot be separated logically?
Its rather straight forward.
When the router is in router mode all ssid's terminate on the router and are natted to the Internet.
In ap mode this is not possible, since there is no direct internet access on the ap.
It could be possible if vlans were supported or if the router is used in router mode behind pfsense (typically with double nat). -
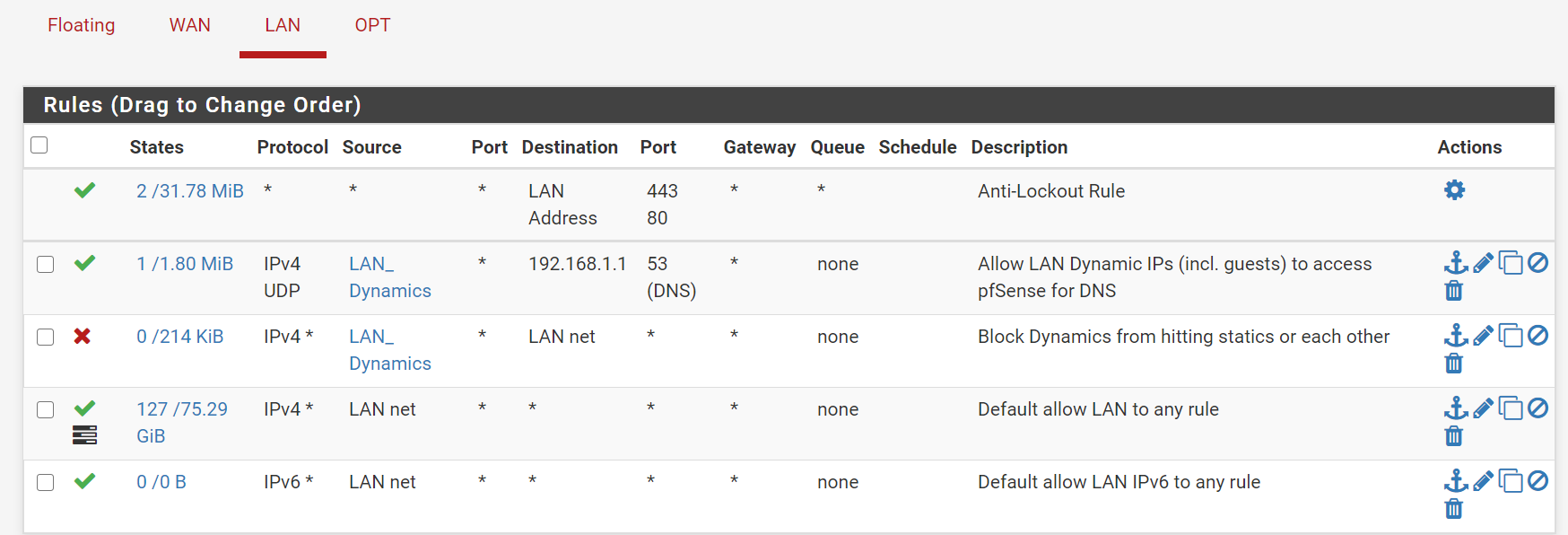
1 - Create VLANs with guest on its own VLAN and subnet.
2 - Guest forbid traffic to firewall services, main LAN subnet, and also whatever parts of internet you want blocked off, e.g. my guest lan is HTTP, HTTPS only.If you create the VLANs they need to be configured on any switches as well.
-
@chrcoluk said in Firewall rules to create a guest network:
2 - Guest forbid traffic to firewall services, main LAN subnet, and also whatever parts of internet you want blocked off, e.g. my guest lan is HTTP, HTTPS only.
Would like to see those rules, if you don't mind, need some inspiration.
-
@Bob-Dig Here's my guest rules:
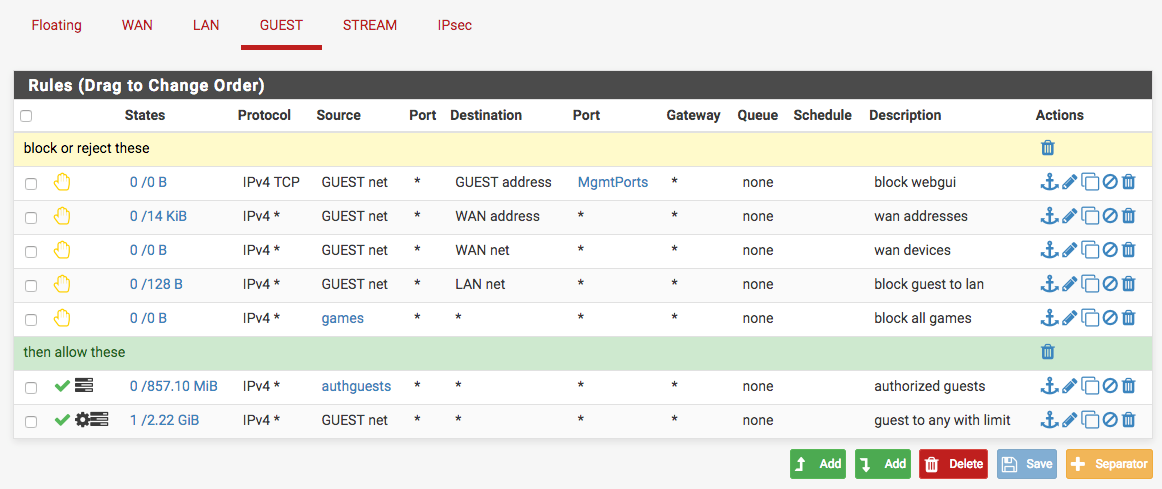
Blocks access to the webgui, other stuff on the WAN network of my modem, blocks to the LAN network, and keeps my kids game boxes off the guest wifi network. Some of the rules say "0 states/0 traffic" because I don't have guests too often, and they certainly aren't poking around in those specific areas.
Jeff
-
@akuma1x That is some advanced ruling.
I like it.
Although, if you have a cable-modem, it will probably not blocked by this. -
@Bob-Dig said in Firewall rules to create a guest network:
Although, if you have a cable-modem, it will probably not blocked by this.
I don't understand what you mean here... And, I've got a DSL internet connection.
Jeff
-
@akuma1x I just thought about the block of WAN net and why someone would want that, but my "explanation" for that was wrong.
-
You would usually block the WAN subnet because it includes the WAN address and any VIPs you have on it which would otherwise allow GUEST hosts to access the firewall services listening on those. You can also use the system alias 'This firewall' for that and that also includes all other firewall IPs. For exmaple:
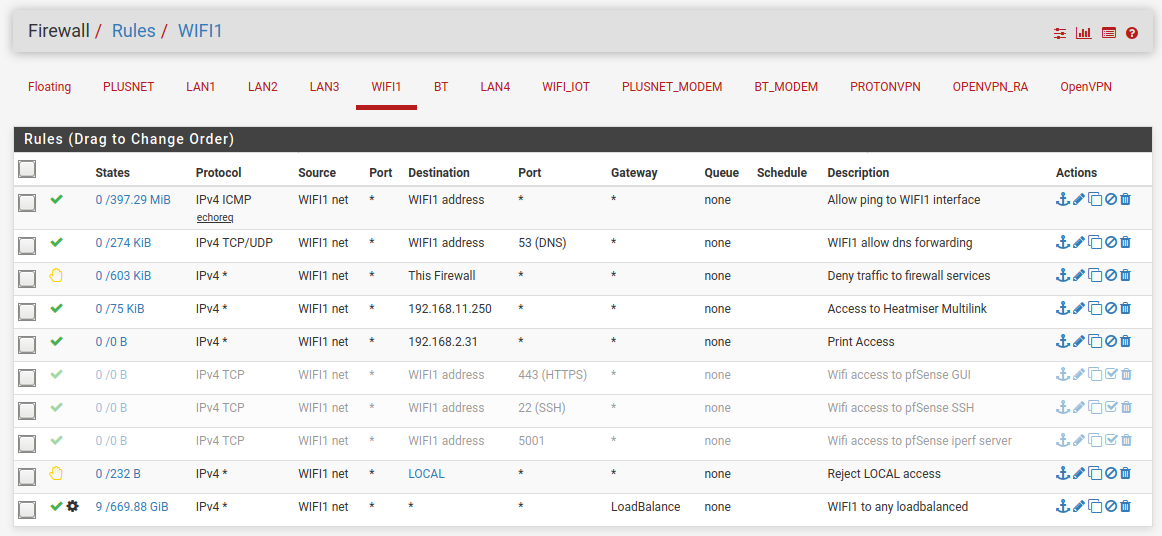
In that case I have to allow DNS access to the firewall because it would otherwise be passed by the policy routing load-balance rule which would send it out of the WAN uselessly.
The LOCAL alias contains all my local subnets.
Steve
-
I highly recommend implement VLANs to isolate your guest and office traffic since pfsense (installed on netgate hardware or desktop) is very much capable of doing that.
from the guest vlan you can simply block access to office vlan + pfsense, etc. And to allow access to Internet create another allow rule and put it below the block rule.
refer to the links below to help get your idea about vlans
https://www.youtube.com/watch?v=CDUyMpBC8bw -
@akuma1x said in Firewall rules to create a guest network:
and keeps my kids game boxes off the guest wifi network.
This won't happen with a rule on the guest network./
You have to filter them on the interface they are connected.
-
@DrPhil
Both SSID you see are on the same network. Your router supports dual band. One SSID is 2.4 GHz and the other is 5GHz. Your laptop or smart-phone is probably seeing both bands ... older devices can see 2.4 GHz only ... I don't understand if there is really an option in your router that can isolate the traffic being grey out -
@DrPhil
You can try create another alias for static IPs and name it LAN_Statics and populate it with a list of static ips. Then in the block rule you've already created set the source to LAN_Statics. Also make this rule as the second (below the default Anti-Lockout Rule). -
@wintok said in Firewall rules to create a guest network:
@DrPhil
You can try create another alias for static IPs and name it LAN_Statics and populate it with a list of static ips. Then in the block rule you've already created set the destination to LAN_Statics. Also make this rule as the second (below the default Anti-Lockout Rule). -
@netblues said in Firewall rules to create a guest network:
@akuma1x said in Firewall rules to create a guest network:
and keeps my kids game boxes off the guest wifi network.
This won't happen with a rule on the guest network./
You have to filter them on the interface they are connected.
Um, yes it does. If they happen to join the guest wifi network ('cuz the password is hanging on a bulletin board in the kitchen for guests to see) with their game boxes, they get assigned an IP address. It is with this IP address that I can then set NO ACCESS and block them from getting to any other destination. Essentially, it's a dead end. I don't know if this is the best way to accomplish my goal, but it works and is pretty simple to implement.
On the interface they are connected to 99.9% of the time, the LAN network, there is filtering there for the game boxes, like throttling and scheduling. Works perfectly.
Jeff