Enable DNS over TLS via DHCP
-
Seems like it's not ready yet:
option-code: TODO (two octets)Unbound can accept DoT requests if clients are sending them as long as you have enabled it and added a cert.
Steve
-
I followed this and it worked great, until I restarted my router. Now, unbound doesn't seem to be handling any DNS requests and my router is defaulting to my ISP's DNS servers. The Cloudflare DNS servers are in the config, as well as in /etc/resolv.conf and in the Luci interface config for WAN & WAN6. If I try to use nslookup, I get "Illegal Instruction". Any ideas as to what is going on? I've checked my configs, tried restarting unbound several times, redid all of the configs, and still nothing from unbound.
-
Luci is an OpenWRT component, did you mean to use that term?
-
I followed this and it worked great, until I restarted my router. Now, unbound doesn't seem to be handling any DNS requests and my router is defaulting to my ISP's DNS servers. The Cloudflare DNS servers are in the config, as well as in /etc/resolv.conf and in the Luci interface config for WAN & WAN6. If I try to use nslookup, I get "Illegal Instruction". Any ideas as to what is going on? I've checked my configs, tried restarting unbound several times, redid all of the configs, and still nothing from unbound.
-
You followed what? You just reposted the exact same thing.....
-
Oh I see you just copied it from here: https://blog.cloudflare.com/dns-over-tls-for-openwrt/#comment-3858797960

Your spam game is weak, try harder.
-
DoT is working for me with this option in DNS Resolver and I'm using Cloudflare as the forwarding server.
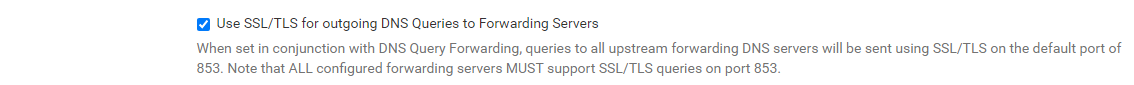
However, I'm not using the option below, so my clients are talking to pfSense over standard 53 and pfSense goes out to the web over TLS 853 only when it's not already cached by unbound locally.
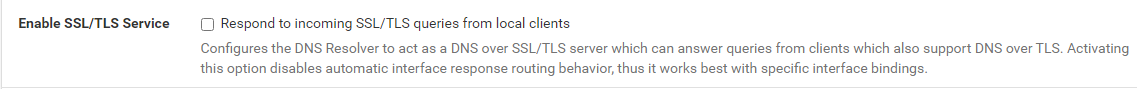
I personally don't care if my DNS query is encrypted between pfSense and my local clients, I'm mostly concerned with what goes out to the world.
-
@Raffi_ said in Enable DNS over TLS via DHCP:
I personally don't care if my DNS query is encrypted between pfSense and my local clients, I'm mostly concerned with what goes out to the world.
That is exactly what I do and I think, it works well...

-
Yup, as do I. In fact I'd rather internal clients were not using DoT so I can troubleshoot it.
It's interesting to note as an option though.
Steve
-
@stephenw10 said in Enable DNS over TLS via DHCP:
In fact I'd rather internal clients were not using DoT so I can troubleshoot it.
Good point, yea could be more difficult to figure out what's going on with DNS if everything was encrypted end-to-end.
-
@Raffi_ said in Enable DNS over TLS via DHCP:
Good point, yea could be more difficult to figure out what's going on with DNS
The point is, don't release the 53 port out of the inner world...
