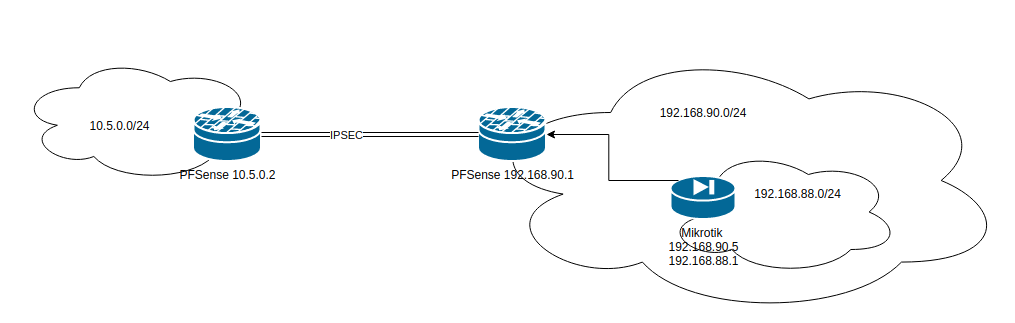
Issues routing 2 LAN's through VPN Tunel
-
Have you set a static route for 192.168.88.0/24 pointing to the Mikrotik on the right pfSense?
-
Thank you for your reply @viragomann .
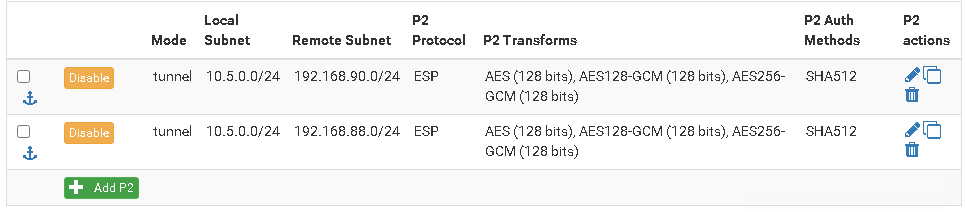
Yes I did set the route as it was required for network 192.168.90.0 to reach 192.168.88.0
this is a gateway:
This is the route:

I think the issue is in the fact that network 10.5.0.0 doesn't know that it needs to use 192.168.90.0 to reach 192.168.88.0 -
@Stefan-Cplanet said in Issues routing 2 LAN's through VPN Tunel:
I think the issue is in the fact that network 10.5.0.0 doesn't know that it needs to use 192.168.90.0 to reach 192.168.88.0
There is no need to use 192.168.90.0.
By adding the phase 2 for 192.168.88.0/24 pfSense should know to route that subnet to the remote VPN endpoint. Have you added the second phase 2 to both nodes?
You may also go with a single phase 2 by modifying the right side netword to 192.168.88.0/22.What to you get from traceroute from 10.5.0.0? At least you should see the remote endpoint.
Also check firewall rules for allowing the access.
-
Thank you for reply @viragomann ,
I have put it on both side.On 10.5.0.2:
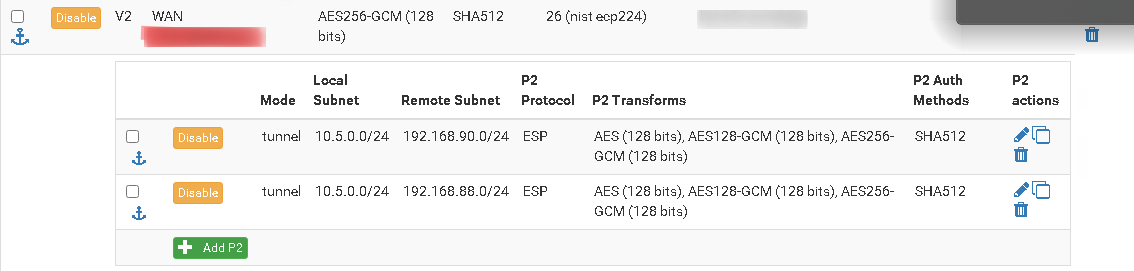
On 192.168.90.1:
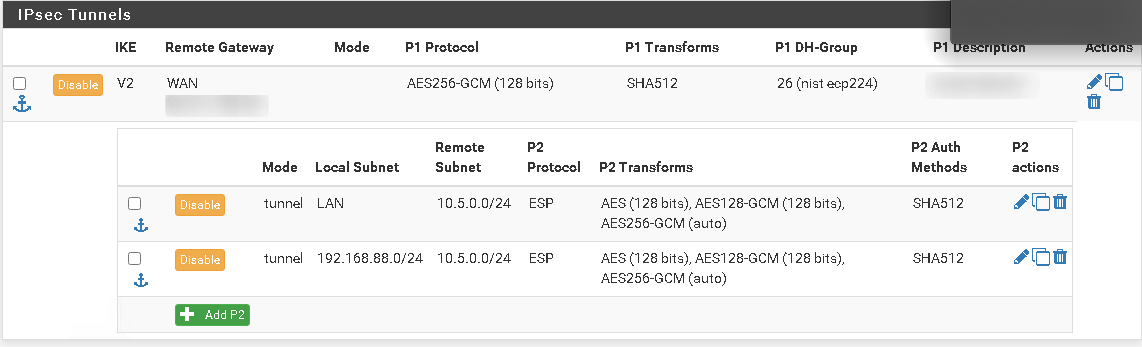
Trace route seems to give me some issues from 10.5.0.2 even if I use ICMP,it would only show 127.0.0.1 even for 192.168.90.1, so I will show you ping. Ping passes towards 10.168.90.1:
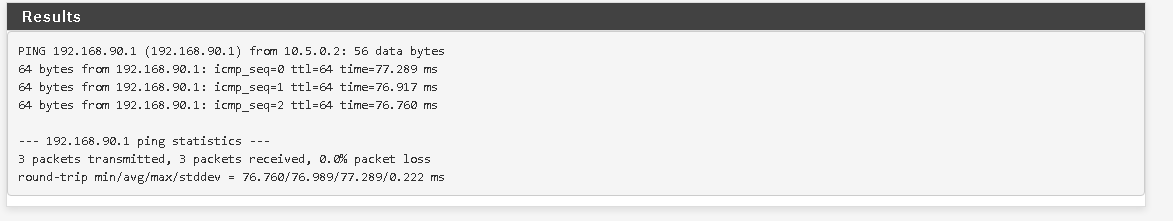
but it won't pass towards 192.168.88.1
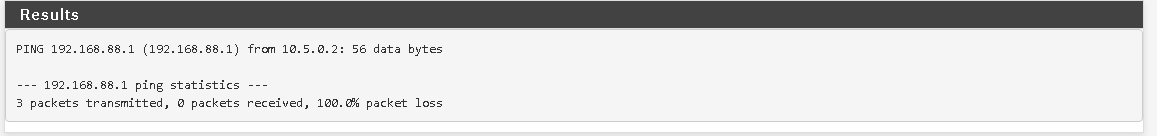
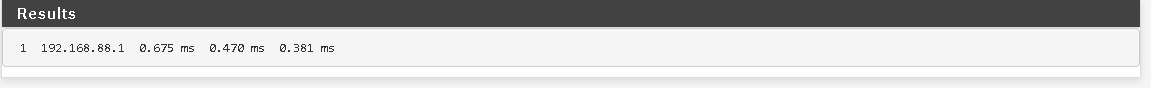
Meanwhile from 192.168.90.1 traceroute can reach 192.168.88.1:
Also worth noting that firewall rules are allowing traffic TCP/UDP and ICMP without limit.
They are identical for .90.0 and .88.0 so should not cause any issues.
Thank you for all your help -
You can try a packet capture on 192.168.90.1 on the IPSec and on the internal interface, while trying to ping 192.168.88.1 from remote to investigate if packets arrive and are routed correctly.
-
@viragomann said in Issues routing 2 LAN's through VPN Tunel:
2.168.90.1 o
Thank you for the reply,
I tried that but there are no packets, it doesn't reach the network -
Even on IPSec?
And on the remote side. Do you see the packets there? Or do they go out on WAN?
-
Sorry for late reply, No packets do not go from 10.5.0.0 to 192.168.88.0, its as it doesn't know the route. I was looking at NAT/BINAT settings os IPSec, do I perhaps need to set that one in order to work?
-
@viragomann Actually if I traceroute from
10.5.0.5 (windows pc) towards 192.168.90.1 packets go through IPSec Tunel as expected.
however
10.5.0.5 towards 192.168.88.1 ( packets go to) 10.5.0.2 ( router) and then 127.0.0.1 after which they go onto public IP's before getting lost, so actually its trying to route it through WAN and not IPSec? -
@Stefan-Cplanet said in Issues routing 2 LAN's through VPN Tunel:
10.5.0.5 towards 192.168.88.1 ( packets go to) 10.5.0.2 ( router) and then 127.0.0.1 after which they go onto public IP's before getting lost, so actually its trying to route it through WAN and not IPSec?
On the left pfSense?
You may see the packets on WAN interface.So pfSense is presumably missing the route, though the IPSec phase 2 is set correctly.
You may check the route in Diagnostic > Routes, however I can't give more help here, since everything seems to be configured as it should be.I'd set up an OpenVPN site-to-site instead, that's more reliable regarding routing.