Print from OPT1 to LAN printer
-
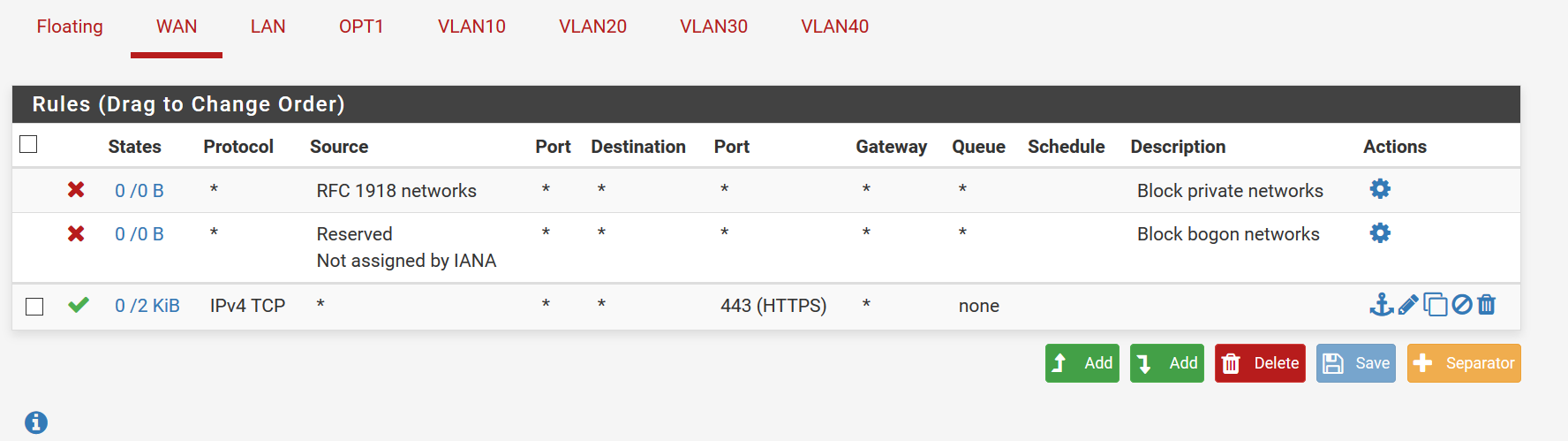
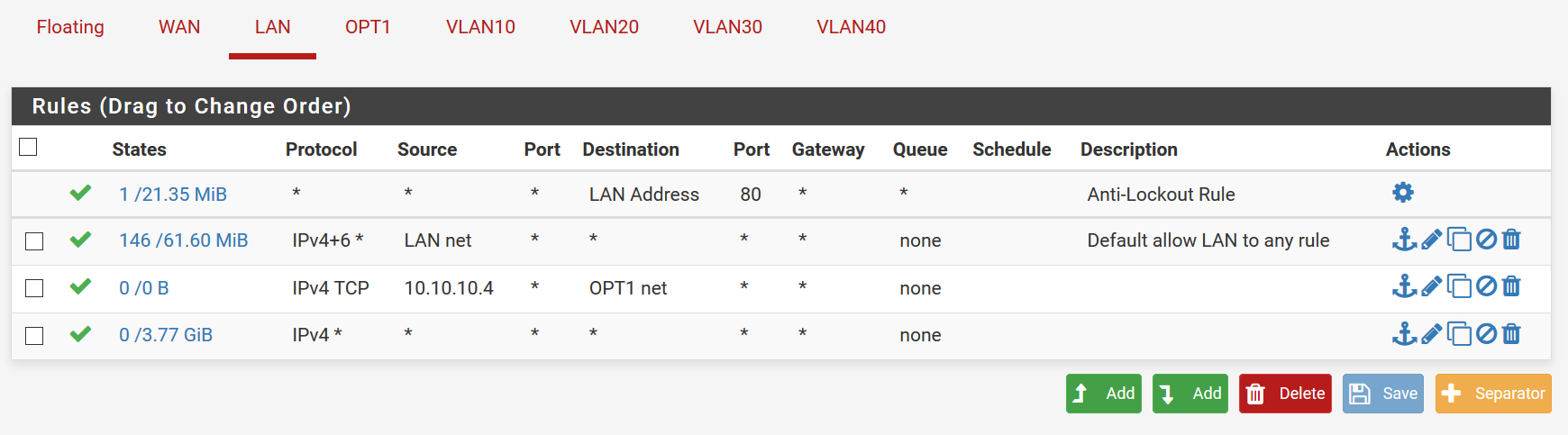
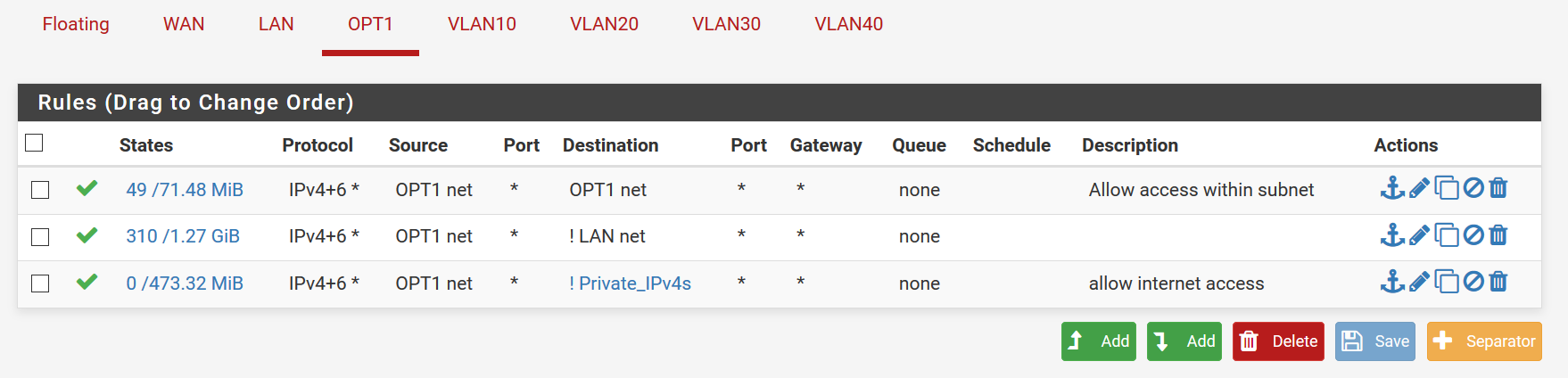
I may have messed up rules due to watching too many videos on this.... WAN, LAN,OPT1 are as follows: (ignore the VLANS, that is just for a future managed switch...possibly) The "Private_IPv4s" is just an alias for all private IP addresses (192.168.0.0/16; 172.16.0.0/12; 10.0.0.0/8) and the 10.10.10.4 is the IP address of the printer on LAN
-
Yeah those rules don't make a lot of sense.
Rules are evaluated top down, as traffic enters an interface, first rule to match wins, no other rules evaluated.
So on your opt, that first rule is pretty pointless to be honest, since you don't even talk to pfsense to talk to other devices on your opt network.. Your prob just seeing hits on that because opt1 address would be included in opt net
The rule at the end makes no sense since your already allowing anything that is not lan net.. Which would include any that is ! private IPv4
For lan, that 10.10.10.4 to opt, is that not your lan net? the 10.10.10? Then the rule above it already allows that.
Same goes for the last rule, unless you have downstream router on this lan net that makes no sense since any traffic on lan would be in the lan net..
-
Ok, so if I'm understanding correctly, I have disabled the last 2 rules in LAN, and disabled the 1st rule in OPT1 (I will completely delete them once all this is figured out... I don't want to break the network right now as people are using it...and right now everyone has internet access for school work..that way if they loose access I can just enable everything again..)
10.10.10.4 is the printer on the LAN network, yes.
I guess what I am looking for, as I am still green on networking (studying for Network+ now)... is what rules SHOULD I apply? is there a good example of what rules should be there in this forum somewhere, or elsewhere on the internet? I am still unsure what exactly I need to allow, and where...and what should be blocked... so that the OPT1 network can't see the LAN, except for the printer, but LAN network can see things on the OPT1 network).
Ideally, I would love to be able to set up all of the IoT devices (Roku, Smart TVs, Amazon Echo, Nest, Security system, etc..) on a different network so all of our laptops and personal devices are protected...but thats for another day...
No downstream router. I have only pfSense handling routing, my other wireless routers are in access point mode only.
-
@5cub4f1y said in Print from OPT1 to LAN printer:
is what rules SHOULD I apply?
Well what do you want? That is a pretty open ended sort of question.. How would anyone know what you should do, its your network.
What you should apply is the rules you want to setup the network how you want it, and to allow or block what you want to block..
Its like asking me what what you want for dinner. I think you should have pizza, when your really in the mood for a burger ;) But I think you should have pizza for dinner!!!
More than happy to help you setup "specific" something... But asking general terms what you should apply... Doesn't make a lot of sense.. Since I do not know the ins and outs of your network, nor do I know how tight or loose your tinfoil hat is, etc.
Here is a "typical" locked down network
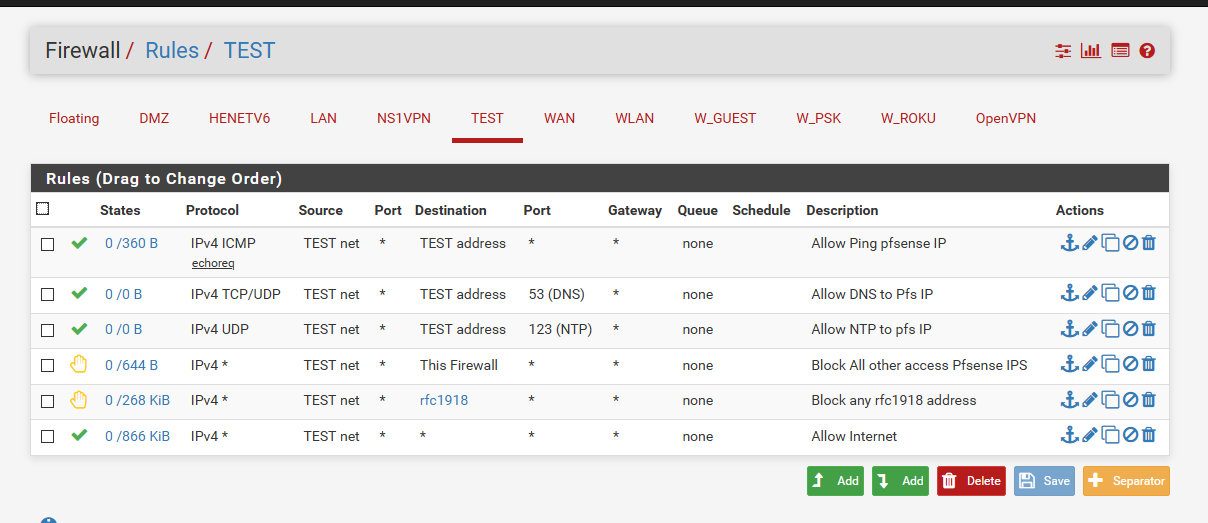
Where this vlan is limited. Something like that would be a common sort of setup for a iot sort of vlan.. Or maybe you don't even want devices to use your dns or ntp, if so then pull those rules out and hand the iot clients say a public dns.. Maybe you don't even want them to be able to ping pfsense? But I see that is a very valuable test of connectivity, etc.
-
I thought I had stated this in the original post, and subsequent. I apologize if it wasn't clear. I simply want to :
-
Allow everything on LAN and OPT1 access to the internet
-
Allow LAN access to OPT1 network (allowing me access to the security system, Nest device, Alexa Echo devices, etc...)
-
Only allow OPT1 access to the printer on the LAN network
-
Printer IP is 10.10.10.4
-
-
And already gave you how to do that!
Do you really need a picture?
Just create a rule that allows access to your printer IP, on whatever port your using for printing, 9100, 631, etc.. Then below that block all access to your lan net. Then the any any rule to allow internet. -
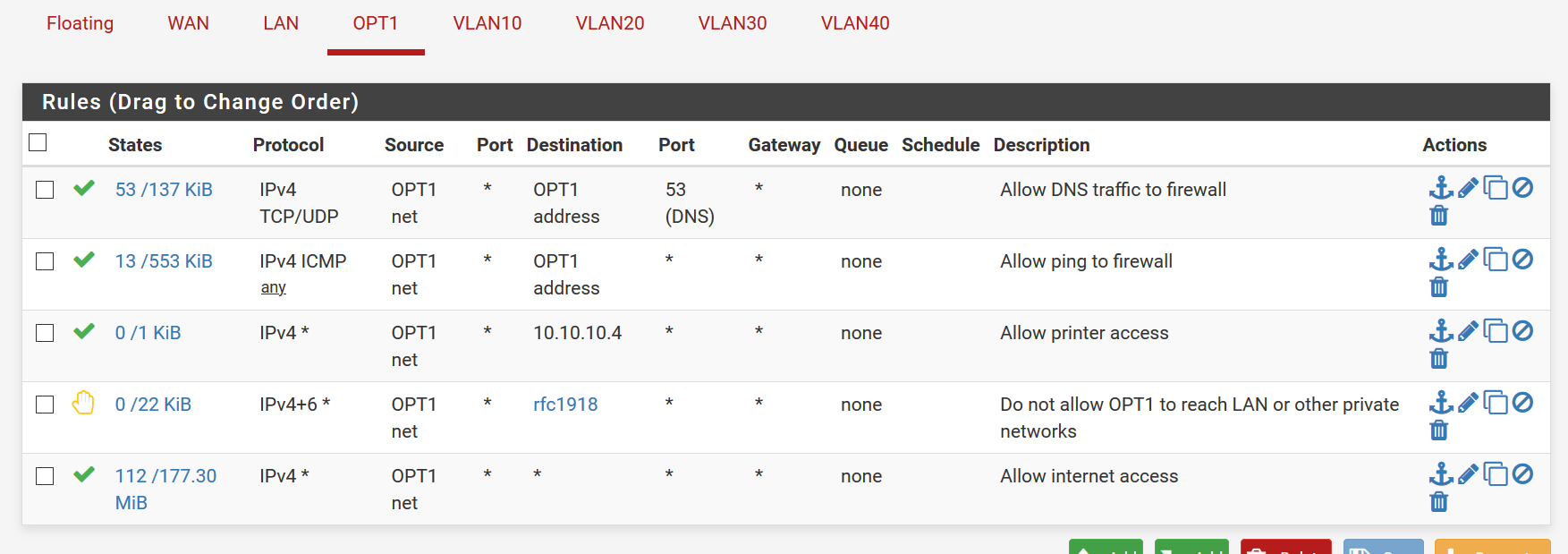
Ok. Obviously I needed to find the "complete newb" forums. However, I thank you for your time. I believe through looking at what you posted, doing a lot of research on what you posted as well as cross-referencing the NetGate Docs, I have found what I needed. This configuration seems to work, at least my OPT1 devices can now ping the printer. I THINK I understand how the rules are applied:
- Basically, for OPT1 for example, the rules are applied as
- ALLOW any DNS traffic out of the firewall ..to cloudflare or Google DNS servers for example
- ALLOW any OPT1 host to ping through the firewall
- ALLOW any host on OPT1 to access the printer at the specific address on LAN subnetwork.
- REJECT ANYTHING else trying to get from OPT1 subnet to any other subnet that is not OPT1
- ALLOW all other traffic EXCEPT what was specified before this rule, essentially allowing internet access.
- For LAN:
- ALLOW access from any network (internet or private) and any address to port 80 on any LAN subnet address.
- ALLOW DNS traffic (TCP/UDP protocol only) from anything on the LAN subnet through the firewall to the DNS servers listed in General settings.
- ALLOW any traffic from anything on the LAN subnet to any port 80 (HTTP) on the internet or any other address.
- ALLOW any traffic from anything on the LAN subnet to any port 443 (HTTPS) on the internet or any other address.
- ALLOW any LAN subnet host to ping through the firewall
- REJECT any attempt at access from a host on the LAN subnet to any private IP address NOT included in any rule above
- ALLOW any host on the LAN subnet to access any other address, NOT excluded in any rules above. (allowing access to anything on the internet)
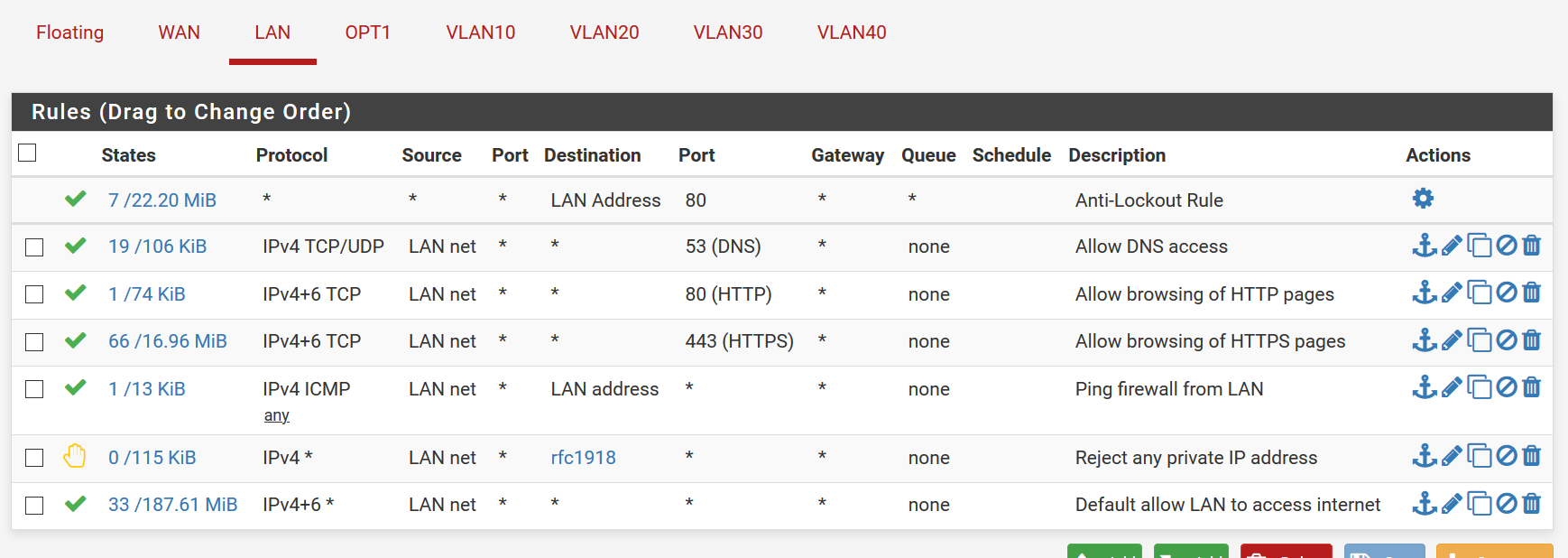
Hopefully I am interpreting all of this right. If not please correct so hopefully this will help me and others understand better in the future.
-
All of those rules between antilock and your rfc1918 are kind of pointless.. Other than just allowing access to pfsense lan address.. I wouldn't write them that way, I would set them to just being the lan address, since your rule below your rfc1918 rule allows all of those anyway to everything else.
And its kind of rare to want to block your lan from talking to your other vlans, normally lan is your most trusted and open network.. While I get block your other vlans from talking to it.. Normally lan is allowed to really go where it wants.
Thought you wanted your lan to able able to talk to opt? Do you just want it to be able to talk to 53,80 and 443 on opt?
-
Ok. I was following the Netgate Doc page https://docs.netgate.com/pfsense/en/latest/config/example-basic-configuration.html under Basic Firewall Configuration Example/ "Setup isolating LAN and DMZ, each with unrestricted internet access" (I am assuming DMZ is OPT1?). I do want the LAN to be able to access anything on OPT1. Which rule is blocking that? Or is it an ALLOW rule that needs to be added?
-
The rule that rejects all rfc1918 (I assume you created an alias with all the rfc1918 networks in it) would block access to your opt network, which I assume is rfc1918 ;)
So as the rules are currently written you would only be able to access ports 53,80 and 443 on opt network, since right under that you block all access to any rfc1918 address.
-
Ok got it. I thought maybe I was misunderstanding what the rule was for, because it did look to me like it was blocking LAN from seeing OPT1, but the Netgate docs said to add that rule....I just removed it.
-
With that rule removed, then all your other rules are pointless between the anti lockout and your any any. So why have them if they don't do anything?
To work out what rules you need, just come up with your traffic pattern.
say 10.10.10.X wanting to talk to IP:port
Now walk down your rules - is it allowed, or blocked? In your case the last rule would allow it, and no other rule above that would block it - so its allowed.
-
Ok so the rules filter DOWN...as in, if the bottom rule allows EVERYTHING, then that overrides any rules above it that allow or deny anything? So If I did want to block something, then I need to have the Allow any/any as the very top rule (under the anti-lockout)?
-
@johnpoz said in Print from OPT1 to LAN printer:
Rules are evaluated top down, as traffic enters an interface, first rule to match wins, no other rules evaluated.
Yup.. as I already stated ;) and is in the docs on how rules are evaluated, etc.
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.htmlSo If I did want to block something, then I need to have the Allow any/any as the very top rule (under the anti-lockout)?
Not always.. Maybe you want to log something specific, say you wanted to log when something on the lan accesses your plex server sitting on opt.. Then you could put a rule above the any any that logs that specific traffic.
Or maybe you want to policy route some specific traffic out a specific gateway, which again you would put above your any any, etc. Or maybe you wanted to mark some specific traffic, or maybe you wanted to redirect something.. There are more things to do with rules then just allow or block.
-
But if I put the Allow any any above any blocking rules, then wouldn't the firewall see that I have allowed anything and not go any further?
-
This post is deleted! -
Yes.. I never said anything about putting block rules below your any.. Block rules would need to be above a rule that allows any..
-
@johnpoz said in Print from OPT1 to LAN printer:
In your case the last rule would allow it, and no other rule above that would block it - so its allowed.
This is what confused me. I see that and think that because the any any is on the bottow, everything above it is ignored..
-
You didn't have any block rules - you only had allow rules!!
Dude... This is not difficult... Come up with your traffic pattern that you want to do something with.. Now walk down your rules top to bottom.. What rule triggers? On that traffic pattern - that is what happens... Once you hit a rule that matches, stop looking at any othe rules.
If you get to the bottm and and no rules match, then it would be blocked! Default Deny, if rule does not allow it.
-
Got it. So should the LAN have any blocking on it at all? Or just basically have the anti-lockout, and the allow any/any. (I am talking about my network only, where I want the LAN to be able to access anything on OPT1, and the internet..and anything on OPT1 to access the internet, but only the printer on LAN)
