Routing between two pfsense on ISP's with proxy behind
-
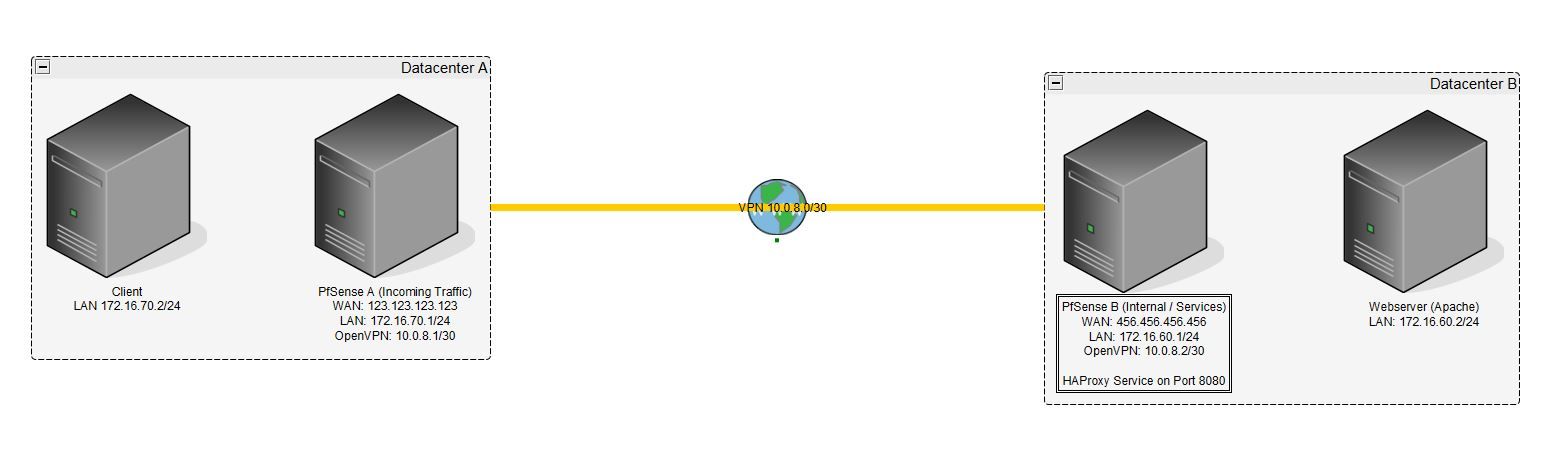
I have two pfsense. PFSense A is the "main" pfsense which should handle all public traffic. PFSense B is for the internal webserver. Both pfsense are located in different datacenters and each has its own WAN interface.
To connect these both I use a site to site openvpn.The main reason why I use two pfsense is, "Datacenter B" is able to provide better servers while "Datacenter A" gives me more traffic and has a free Anti-DDOS service. Thats the only reason for using these second "Pfsense A".
My issues now...
mywebsite.com is pointing to the WAN IP of PFsense A.
There is a firewall rule which says everything on port 80/443 go to 172.16.60.2 on port 8080 (which is the reverse proxy on "pfsense B" and forwards it to port 80/443 to the webserver)But I can't access it via the proxy.
1.) Which Interface do I need to set the reverse proxy to listen on? The "pfsense B" gets the traffic from the wan, but its through the vpn on 10.0.8.0/24. So in the firewall logs in see these traffic on the vpn interface which should mean, that the vpn interface is the right one? Or do I need to say "listen on LAN" because the webserver itself ls also on the LAN? I am confused.
2.) Under Gateway / Routes there is a option to say "Default Gateway". In my mind I am thinking about to give PFsense B the option and select the VPN Gateway because pfsense B should never send out anything from itselfs WAN and should always go the way over PFSense A.
3.) For best practice, would you guys set up the HA Reverse Proxy on Pfsense A or Pfsense B?
Thank you so much!
-
The proxy musy be listening on the OpenVPN interface since that's where the traffic arrives.
You should be able to put the proxy at either end but I would probably put it at A since that's where traffic is arriving. I'm not sure how the proxy would reply to traffic at B either.
Importantly you must have the OpenVPN interface assigned at B and make sure the rules passing the traffic are on the assigned interface and not on the OpenVPN tab. Without that you will not get reply-to tags on the states and the replies from the server (or proxy) will just go out the WAN rather than back over the VPN. That creates an asymmetric route and traffic will be blocked.
Steve