DMZ not working
-
Did you setup your NAT outbound rules for the DMZ network?
-
And what rules did you created on opt1? When you create new interface be it native or a vlan - no rules are created.
While the automatic outbound nat (default) would create the needed outbound nat - without rules to allow access on opt1, no nothing would have any access.
-
https://www.youtube.com/watch?v=QFk5jX-oeSo
-
@johnpoz thx for the pointers. no rules in DMZ on firewall. Have now put these. nothing so far but am remote so could be working
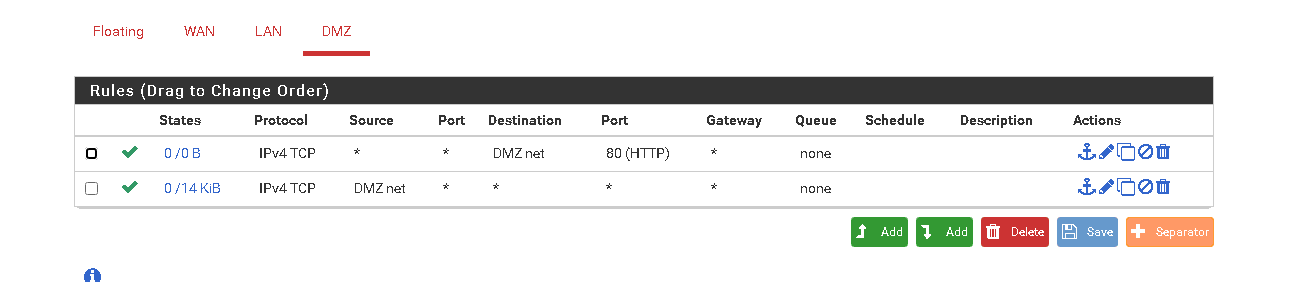
-
not sure if this should be better.
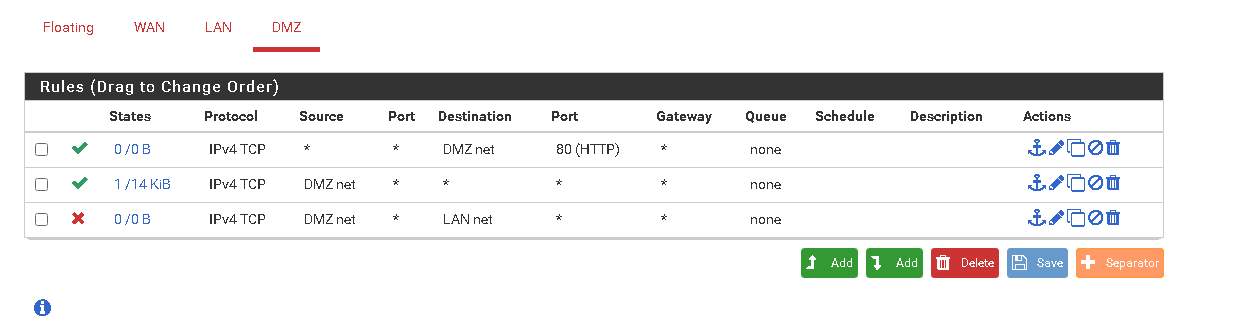
-
Well without allowing udp, how you going to get DNS?
Also zero reason to add any rules to dmz net, since devices don't talk to pfsense (the gateway) to talk to other devices on their own network.
You prob want to block "dmz" from talking to the rest of your network, or pfsense gui for example.. Here this would prob be a good example of dmz setup.
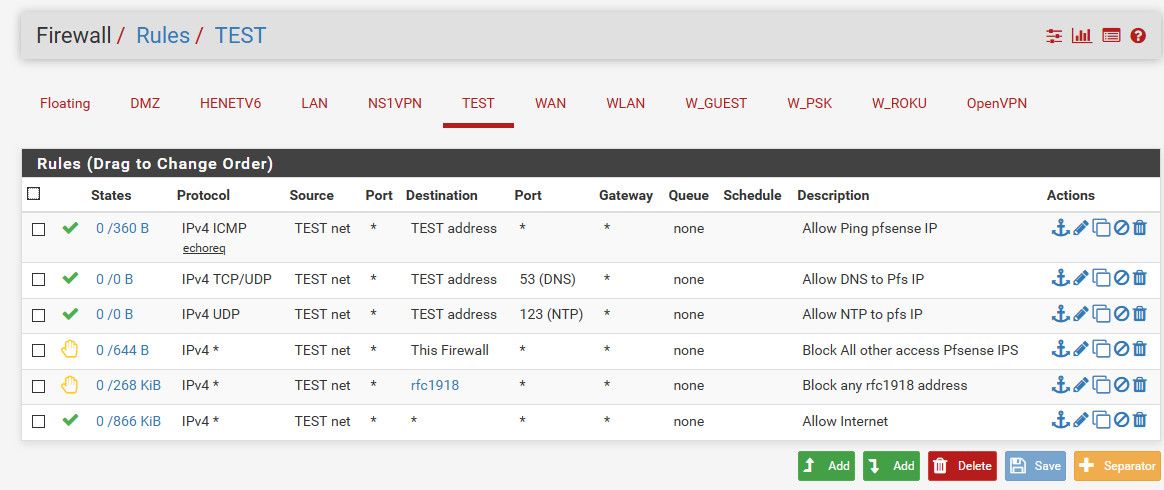
If you only have 1 other network you could just use say lan net there for destination, where I have the alias. Or just create an alias that has all the rfc1918 networks in it (10/8,192.168/16,172.16/12)
-
working now. thx all. Did have an option to blick rfc1918 so just blocked to lan net.
Thanks again.chris
-
you would need to create the alias, you could call it whatever you want ;)
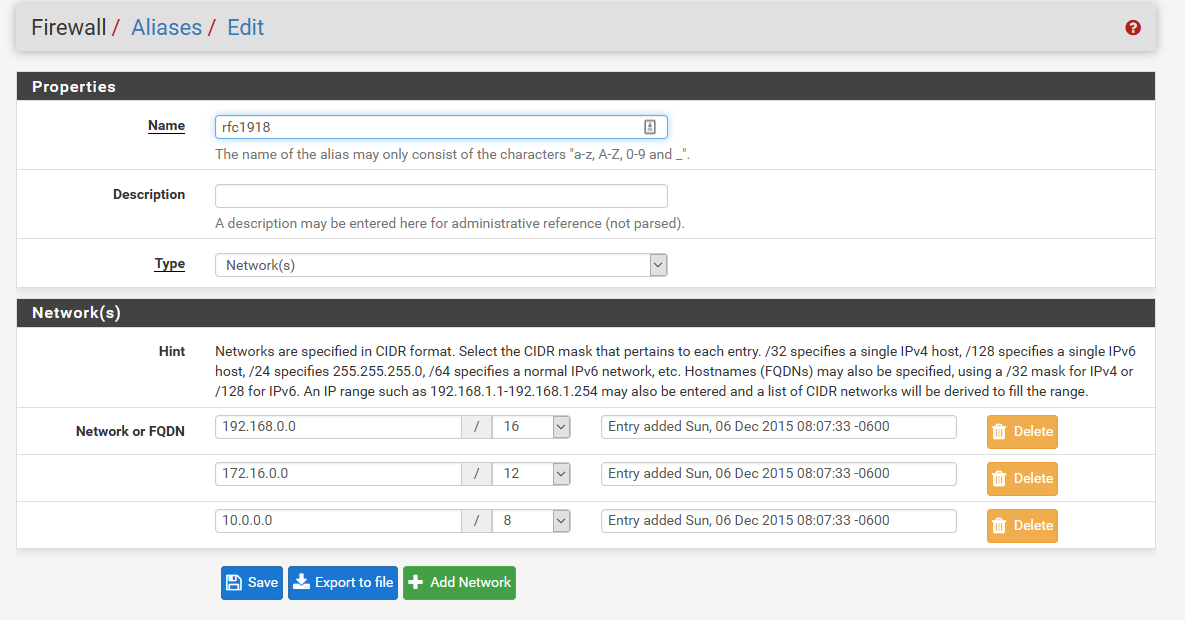
Can come in handy if you plan on adding more networks at future date. That you will want to block access too.
-
@frog said in DMZ not working:
not sure if this should be better.
the first rule in your screen made me wonder what you're trying to do. I'd advise to go with John's ruleset. Allow Ping to pfSense from the DMZ, allow DNS, NTP and reject all others. Rejecting "This firewall" is indeed important as it also blocks access via pfSense' WAN IP that otherwise gets overlooked quite often!
I'd vote to include the RFC1918 Alias as pfSense default in future releases as it's simply that useful in larger rulesets.
-
Reject or Block is fine - I use reject on many a local rule that I block, because that way you "know" instantly its blocked because the firewall send you back info - hey your not getting there, go away! ;)
Reject on a wan side rule is almost always a very bad idea.. Since you rarely want the firewall to send anything in response.