Need to put PFSense behind a NAT and double nat, looking for config recommendations to mitigate issues.
-
@akuma1x said in Need to put PFSense behind a NAT and double nat, looking for config recommendations to mitigate issues.:
@gawainxx Lots of ISP modems have a "DMZ" feature. You could use this, if available, since it will pass ALL (or most) ports right into the pfsense WAN port. Once there, you can deal with the pfsense box doing the port forwarding, like it was at the edge of your network.
Jeff
Should I still be able to access the management interface of the modem/router?
-
Yeah you should be able too.. Might will want to turn off the default rfc1918 wan block rule.
-
So far so good, I've not had an opportunity to verify whether the port forwarding for openVPN is working correctly in the DMZ, i'll be checking that shortly and seeing whether I need to define that in the modem port forwarding as well.
Yep, also created a rule on the client interface so that I can access the modem's webui
-
port forwarding looks good, was able to connect to OpenVPN on celluar..
Going to run like this for a bit.
-
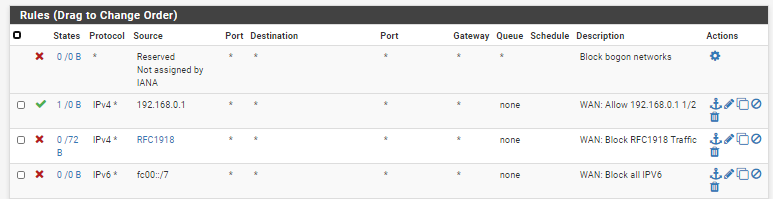
Why would you be blocking bogon on your lan side interfaces? That makes no sense.. How would something with a bogon be on your lan side? And even if allowed, where exactly do you think it could get to? It wouldn't be natted, since its not the interfaces network...
Also what is the point of the block IPv6? If not allowed its blocked by default. That rule doesn't do anything.
-
@johnpoz said in Need to put PFSense behind a NAT and double nat, looking for config recommendations to mitigate issues.:
Why would you be blocking bogon on your lan side interfaces? That makes no sense.. How would something with a bogon be on your lan side? And even if allowed, where exactly do you think it could get to? It wouldn't be natted, since its not the interfaces network...
Also what is the point of the block IPv6? If not allowed its blocked by default. That rule doesn't do anything.
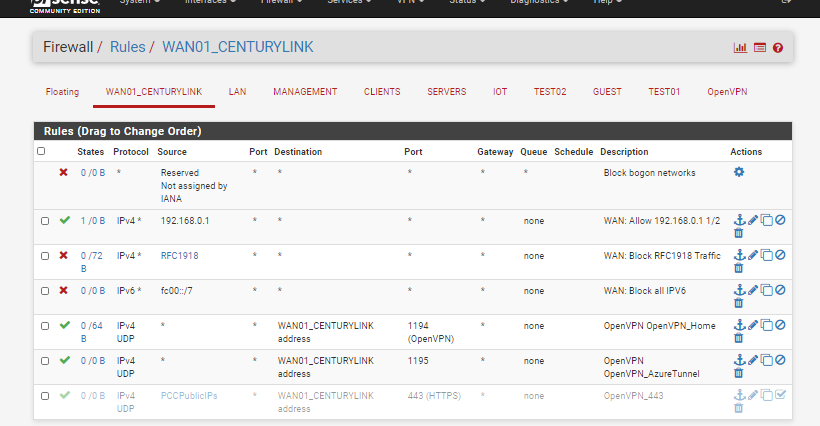
That my WAN IF in the screenshot I have ipv4 traffic from the centurylink modem allowed and all other rfc1918 blocked.
-
Then none of those rules really make sense.. You have no port forwards.. Blocking bogon only makes any sense if your actually have a port forward, and you want to stop some noise from hitting it..
You hitting your router in front of pfsense at some 192.168.0.1 address has nothing to do with the wan rules. You would really only need to turn off rfc1918 rules if you had devices on this network between your router and wan that you would like to get to stuff behind pfsense via a port forward.
I guess the ipv6 stuff stop logging of ipv6 traffic hitting your wan from being logged in the default block log.
port forwarding looks good, was able to connect to OpenVPN on celluar..
To where you have no rules that allow access to openvpn ports listed if that is your wan.
-
@johnpoz said in Need to put PFSense behind a NAT and double nat, looking for config recommendations to mitigate issues.:
Then none of those rules really make sense.. You have no port forwards.. Blocking bogon only makes any sense if your actually have a port forward, and you want to stop some noise from hitting it..
You hitting your router in front of pfsense at some 192.168.0.1 address has nothing to do with the wan rules. You would really only need to turn off rfc1918 rules if you had devices on this network between your router and wan that you would like to get to stuff behind pfsense via a port forward.
I guess the ipv6 stuff stop logging of ipv6 traffic hitting your wan from being logged in the default block log.
It's dmz'd so to my understanding that means that it's essentially directly accessible on the wan, which matches the traffic I'm seeing in the filter logs. I'm able to directly access VPN on the pfsense firewall externally without any port forwarding set up on the ISP modem.
I may be mistaken as this is my first interaction with DMZ but from what I can see those rules are needed in this case?The openvpn rules are there, just deliberately cut off from the screenshot.
-
@gawainxx said in Need to put PFSense behind a NAT and double nat, looking for config recommendations to mitigate issues.:
access VPN on the pfsense firewall externally without any port forwarding set up on the ISP modem.
Yeah the isp modem would send traffic into pfsense wan IP if you put that in the dmz setting on your ISP... But you have NOT rule to allow vpn access.. So how would you actually get to pfsense wan IP.
The openvpn rules are there, just deliberately cut off from the screenshot.
Then how would anyone be able to evaluate your rules? Which is why you should always show which interface the rules are from, and show the bottom of the rule list so you can actually tell that is all of them.
-
@johnpoz
Good point