Fetching package: connection reset by peer
-
@float said in Fetching package: connection reset by peer:
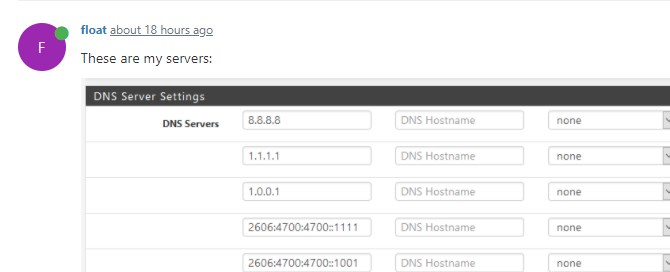
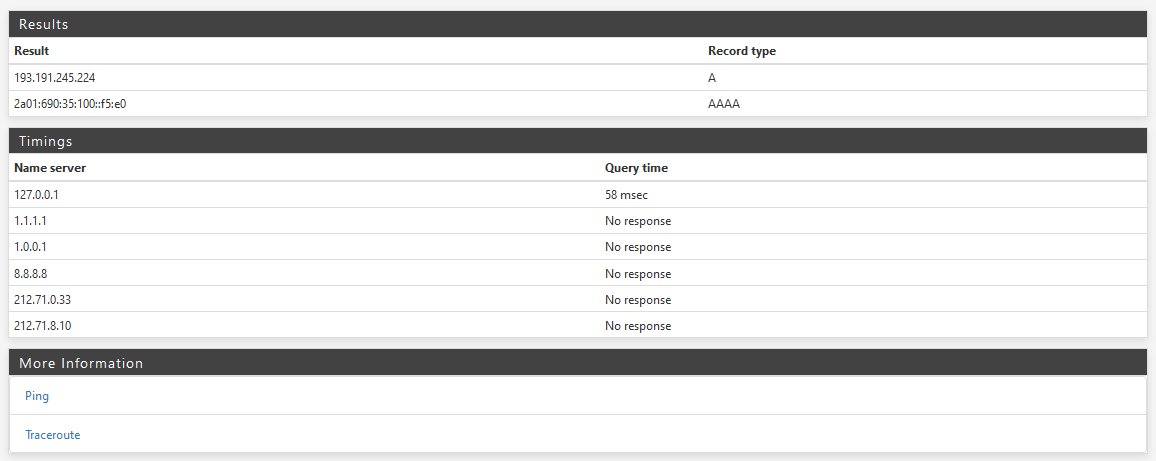
All my IPv4 DNS-servers are not responding.
because the Suricata
home NET / external NET
or pfBlockerNG blocks lists CloudFlare DNS IPs in a stupid way
-
The problem occurred before installing pfblocker.
Installed packages:
-
@float said in Fetching package: connection reset by peer:
The problem occurred before installing pfblocker.
Temporarily stop all packages and PING out the box to 1.1.1.1
-
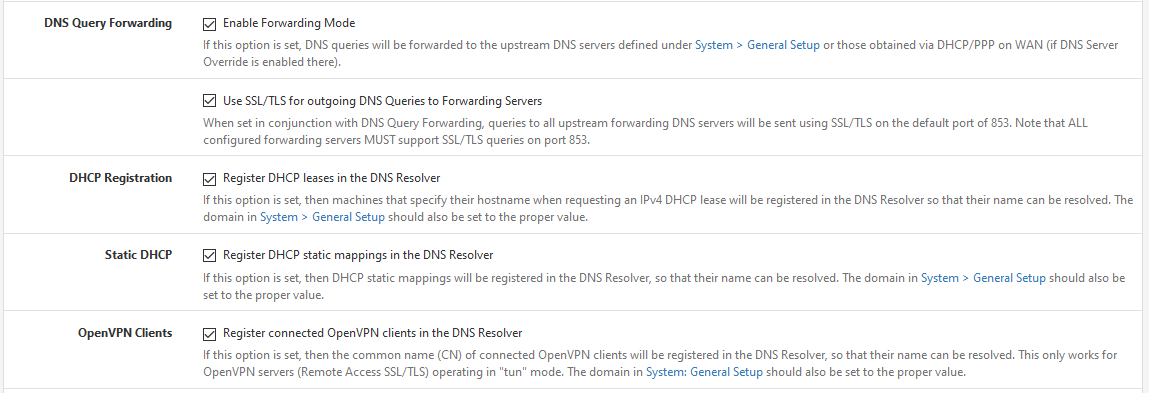
Are you even using those? Unbound running in forwarding mode?
-
Yes in forward mode - I have no issues on the network clients - everything is resolved by pfsense
-
-
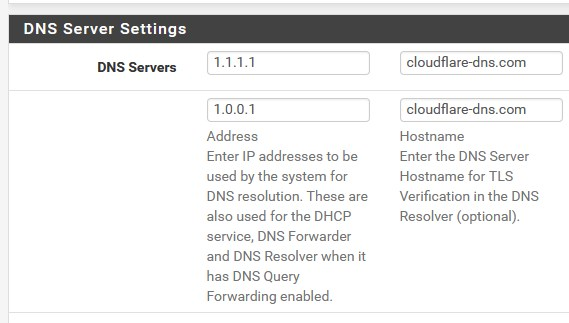
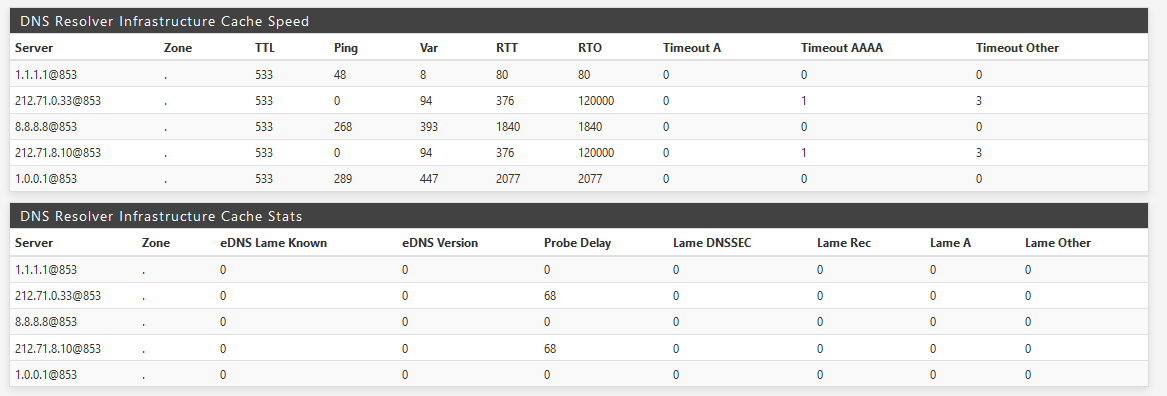
Yes, I changed them 5 minutes ago to test and take a screenshot
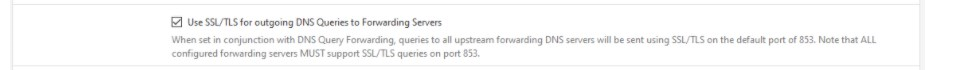
Do you mean that the no response is normal in "dns lookup" because they have to use port 853 and not the standard port 53? -
TRY:
DNS hostname - cloudflare-dns.com -
@float said in Fetching package: connection reset by peer:
because they have to use port 853 and not the standard port 53?
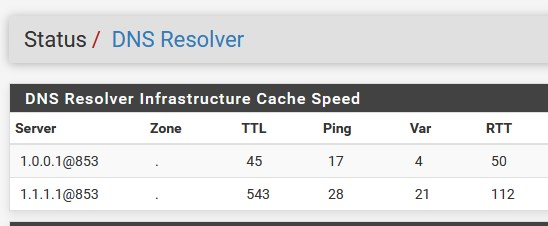
BINGO
-
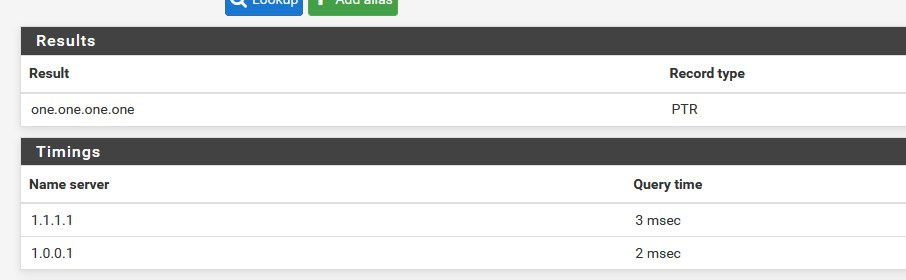
Ok, thanks. So I don't have to worry about the "dns lookup" saying no response?
-
@float said in Fetching package: connection reset by peer:
dns lookup" saying no response?
but yes and it's getting weirder
-
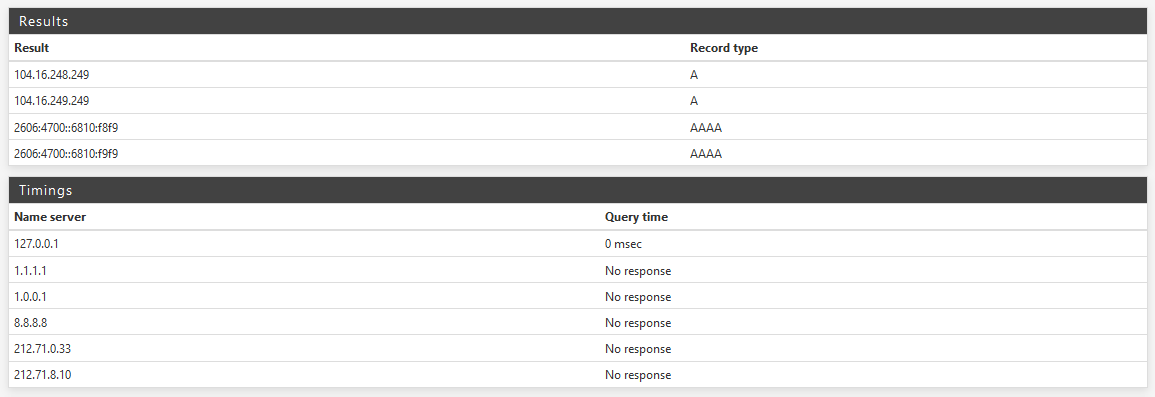
No that not OK. All of those servers should respond to DoT queries.
If you have a host name there it must match as it will be used for verification. But you don't need to have one.
Steve
-
Try something, really just optional
DNS hostname - cloudflare-dns.com
-
-
can you PING 1.1.1.1 under windows or linux (behind pfSense)
what do you see in the firewall log then?+++edit:
this can also be interesting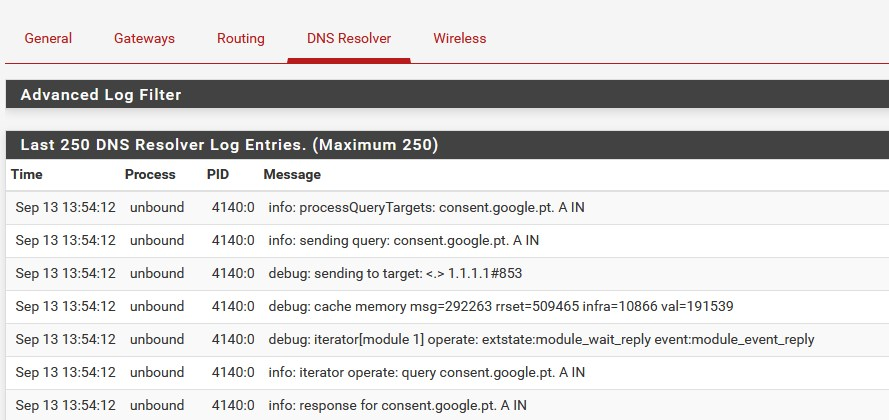
-
I changed the dns server to only 8.8.8.8
I can ping it:
I can resolve hosts:
Sep 13 15:03:07 unbound 36154:0 info: control cmd: stats_noreset Sep 13 15:03:02 unbound 36154:1 info: validation success 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:1 info: validate(nxdomain): sec_status_secure Sep 13 15:03:02 unbound 36154:1 info: validated DNSKEY 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:1 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:1 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:1 info: response for 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:0 info: validation success 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:0 info: validate(nxdomain): sec_status_secure Sep 13 15:03:02 unbound 36154:0 info: validated DNSKEY 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:0 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:0 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:0 info: response for 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:1 info: resolving 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:1 info: validated DS 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:1 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:1 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:1 info: response for 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:0 info: resolving 193.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:0 info: validated DS 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:0 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:0 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:0 info: response for 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:1 info: resolving 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:1 info: query response was NXDOMAIN ANSWER Sep 13 15:03:02 unbound 36154:1 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:1 info: response for 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:0 info: resolving 193.in-addr.arpa. DS IN Sep 13 15:03:02 unbound 36154:0 info: query response was NXDOMAIN ANSWER Sep 13 15:03:02 unbound 36154:0 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:0 info: response for 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:1 info: resolving 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:0 info: resolving 157.228.27.193.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:2 info: validation success time-a.timefreq.bldrdoc.gov. AAAA IN Sep 13 15:03:02 unbound 36154:2 info: validate(cname_noanswer): sec_status_secure Sep 13 15:03:02 unbound 36154:2 info: validation success time-c.timefreq.bldrdoc.gov. AAAA IN Sep 13 15:03:02 unbound 36154:2 info: validate(cname_noanswer): sec_status_secure Sep 13 15:03:02 unbound 36154:2 info: validation success time-b.timefreq.bldrdoc.gov. AAAA IN Sep 13 15:03:02 unbound 36154:2 info: validate(cname_noanswer): sec_status_secure Sep 13 15:03:02 unbound 36154:2 info: validated DNSKEY nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: validated DNSKEY nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: validated DNSKEY nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:2 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:2 info: response for nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:3 info: validation success time-b.timefreq.bldrdoc.gov. AAAA IN Sep 13 15:03:02 unbound 36154:3 info: validate(cname_noanswer): sec_status_secure Sep 13 15:03:02 unbound 36154:3 info: validation success time-a.timefreq.bldrdoc.gov. AAAA IN Sep 13 15:03:02 unbound 36154:3 info: validate(cname_noanswer): sec_status_secure Sep 13 15:03:02 unbound 36154:3 info: validated DNSKEY nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:3 info: validated DNSKEY nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:3 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:3 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:3 info: response for nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:1 info: validation success 124.25.26.194.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:1 info: validate(nxdomain): sec_status_secure Sep 13 15:03:02 unbound 36154:1 info: validated DNSKEY 194.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:1 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:1 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:1 info: response for 194.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: validation success 124.25.26.194.in-addr.arpa. PTR IN Sep 13 15:03:02 unbound 36154:2 info: validate(nxdomain): sec_status_secure Sep 13 15:03:02 unbound 36154:2 info: validated DNSKEY 194.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:2 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:2 info: response for 194.in-addr.arpa. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: resolving nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:2 info: validated DS nist.gov. DS IN Sep 13 15:03:02 unbound 36154:2 info: validated DS nist.gov. DS IN Sep 13 15:03:02 unbound 36154:2 info: validated DS nist.gov. DS IN Sep 13 15:03:02 unbound 36154:2 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:2 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:2 info: response for nist.gov. DS IN Sep 13 15:03:02 unbound 36154:3 info: resolving nist.gov. DNSKEY IN Sep 13 15:03:02 unbound 36154:3 info: validated DS nist.gov. DS IN Sep 13 15:03:02 unbound 36154:3 info: validated DS nist.gov. DS IN Sep 13 15:03:02 unbound 36154:3 info: query response was ANSWER Sep 13 15:03:02 unbound 36154:3 info: reply from <.> 8.8.8.8#853 Sep 13 15:03:02 unbound 36154:3 info: response for nist.gov. DS IN -
@float said in Fetching package: connection reset by peer:
and inside pfSense? (nslookup)
-
[2.4.5-RELEASE][admin@]/root: nslookup www.facebook.com 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53Non-authoritative answer:
www.facebook.com canonical name = star-mini.c10r.facebook.com.
Name: star-mini.c10r.facebook.com
Address: 157.240.210.35
Name: star-mini.c10r.facebook.com
Address: 2a03:2880:f121:83:face:b00c:0:25de -
Okay, if you like 8.8.8.8
just a little plus, you might want to disable 53 if you only want to use DoT
and point all DNS requests to pfSense (manualy or DHCP)
try to use only static entries (DHCP) and uncheck it, this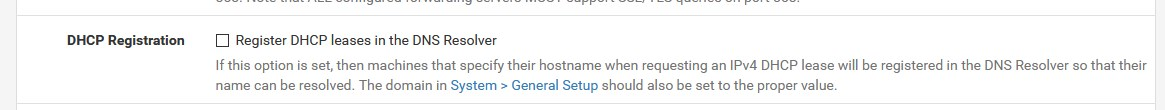
oh and get ready for the new craziness DoH

-
Thank you. Everything is working as it should, only pfsense is being funny, right?