DNS Leak Issues
-
I have DNS Resolver setup with the outgoing interface as the WAN port and responding to all other interfaces.
I use two ExpressVPN connection as OpenVPN Client in failover config.
I have by default all traffic routed via the ExpressVPN and a bypass rule to route over the WAN for vpn blocked sites like this forum or sites in China.
If i run the DNS Leak Test, it correctly shows my VPN connection, but either the standard or extended test shows my true IP.
If i make DNS Resolver to use the VPN Connections, two things happen;
- the VPN clients are unable to establish - because they use pool dns entries, rather than an IP address
- the pfsense box can't resolve until the VPN is established.
What the correct way that, that i can provide;
- DNS resolver to the local network protected
- continue to provide DNS lookup for pfsense and OpenVPN to establish the initial connection / ntp, etc
-
Try
SystemGeneral > Setup
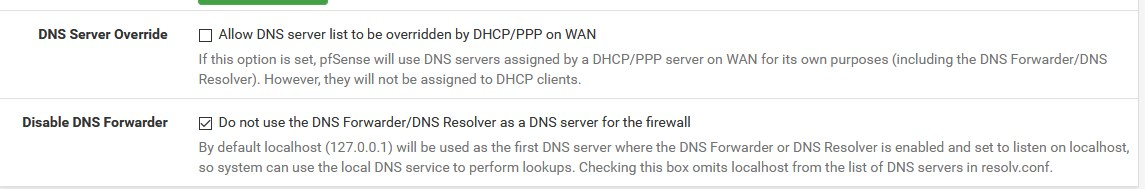
Disable DNS Forwarder > Do not use the DNS Forwarder/DNS Resolver as a DNS server for the firewall -
@Bob-Dig i didn't that, but don't see how it would help as the dns server in the general setup is 127.0.0.1 anyway.
If pfsense is not using DNS Resolver, then it still has to resolve over the WAN anyway to be able to get updates, etc.
I think the issue is, DNS resolver is going over the WAN instead of the VPN. But is i remove WAN as an outgoing interface, then then the vpn client can't resolve the pool name to get a connection.
-
@gwaitsi
@Bob-Dig is absolutely right with this addition
-
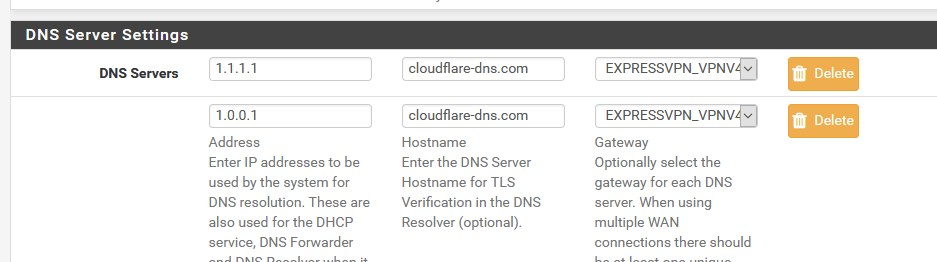
@DaddyGo I am using DNS Resolver as my own dns server. Doesn't this defeat the purpose of caching the root servers locally, or are you saying this config causes pfsense to use the cloudflare servers, while clients use the DNS Resolver
-
@gwaitsi
PfSense queries DNS from CloudFlare with DoT, which is behind pfSense.....receives DNS from pfSense... with Unbound
In addition, CloudFlare DNS queries are pushed through the ExpVPN WANwe do not use root servers directly as they do not support DoT
(even now and / or perhaps never) -
Can't say i really understand. I followed the below
https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
but what is the difference between this config and simply checking to operate as a forwarder over 853. It solves the dns leak problem, but i don't see any difference in the status page to when i previously had it setup as a forwarder.
-
@gwaitsi said in DNS Leak Issues:
I followed the below
this is an older description, but good with the difference that there is already a GUI option since 2.4.4
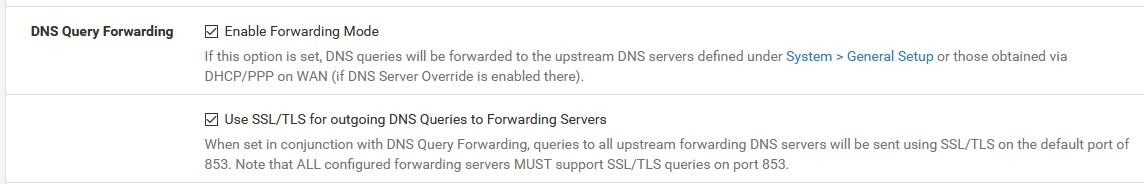
this will be the result:
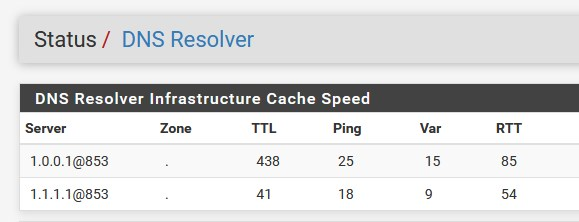
DNS leakage does not come from here,....or is it not so clear.....
all hosts must obtain DNS from pfSense!!!
(it may leak next to it anyway)and
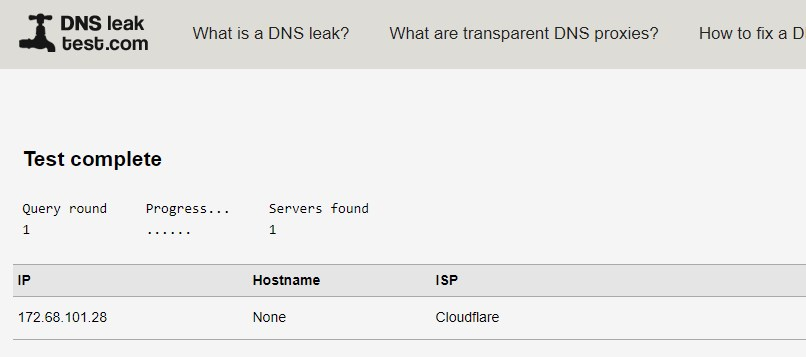
btw:
by no means allow ISP DNS