DNS leak
-
@stephenw10 said in DNS leak:
Unfortunately there are a great number if people out there who have no idea what DNS leak tests actually do. That means the signal to noise ratio for reports like this low inducing skepticism!
I found the config issue on my side. Sorry for the Spam.
-
You'll have to try a lot harder to get classified as spam.

There's a lot of misinformation out there.
-
This post is deleted! -
@PowerSing funny how both of the two posts you have ever made are about the FUD a "friend" has told you about pfsense.
@stephenw10 can we get this account banned for being a troll?
-
We can certainly keep a close eye out!
I agree that is just FUD.
-
He is putting up names from linked in with another key word to boost their SEO rating.. Banned and posts deleted.
-
@emammadov DNS leaks can happen because of your configuration, ISP and bugs.
- Disconnected cable of your ISP on your Pfsense device.
- Go to System > General Setup > DNS server setting > DNS server > Enter 2 IP addresses from Quad9 DNS: 9.9.9.9 and 149.112.112.112 > Unchecked DNS Server Override > Save.
- Go to Services > DNS Resolver :
√ Checked Enable DNS resolver box
Network Interfaces - ALL
Outgoing Network Interfaces - ALL
√Checked Enable Forwarding Mode box
√Checked Use SSL/TSL for outgoing
√Checked DHCP Registration
√ Checked Static DHCP
Save. - Reboot Pfsense, Diagnostics > Reboot and reconnect your ISP cable.
Hope this helps.
-
So 'leaking' all of your queries to quad9 as opposed to resolving it yourself?
It really depends what you're trying to achieve. If that's hiding DNS queries from your ISP that would do it. If the test is checking if clients are sending DNS over a VPN that would show as all leaked.

Steve
-
I feel really guilty for reviving this 3 months old thread.

-
@stephenw10 said in DNS leak:
So 'leaking' all of your queries to quad9 as opposed to resolving it yourself?
It really depends what you're trying to achieve. If that's hiding DNS queries from your ISP that would do it. If the test is checking if clients are sending DNS over a VPN that would show as all leaked.

Steve
But Steve, it is still not quite right. A DNS leak is still a leak, that means ISP can still see visited hosts.
Pfsense configurations need some tweaking. For those who use VPN provider with DNS leaks please follow these steps:-
Go to Firewall > Wan > add new rule:
Action: Block
Interface: Wan
Address Family: IPv4+IPv6
Protocol: TCP/UDP
Source: Any
Destination: Any Port Range Custom: 53
Save -
Go to Firewall > Lan and/or Opt1 tab
Action: Pass
Interface: Lan and/or Opt1
Address Family: IPv4
Protocol: UDP
Source: Lan net or Opt1 net
Destination: any Port Range Custom: 53
#Click button# Display Advance
Gateway: Choose your VPN Interface
Save -
Go to Services > DHCP server > Lan and/or Opt1>Servers>DNS server (Quad9 DNS):
9.9. 9.9
149.112. 112.112
2620:fe::fe
2620:fe::fe:9
Save
Reboot your Pfsense and test it again for DNS leak https://ipleak.net
Hope this helps. -
-
That site does not respond for me. Which I'm finding quite ironic!
Any DNS leak test simply shows you where your clients queries are being resolved. You have to device for yourself if those are correct.
There is no reason to have a block rule for DNS on WAN. All inbound traffic is blocked on WAN by default anyway.
Steve
-
@stephenw10 said in DNS leak:
That site does not respond for me. Which I'm finding quite ironic!
Any DNS leak test simply shows you where your clients queries are being resolved. You have to device for yourself if those are correct.
There is no reason to have a block rule for DNS on WAN. All inbound traffic is blocked on WAN by default anyway.
Steve
Good morning Steve, theoretically the default configs is blocked on Wan, but for some odd reason Pfsense responds differently with different hardware ;)
Also the second rule (pass 53), you need to assign to all interfaces (opt1,opt2,..) and place it above all others rules.Then test again for DNS leak https://ipleak.net
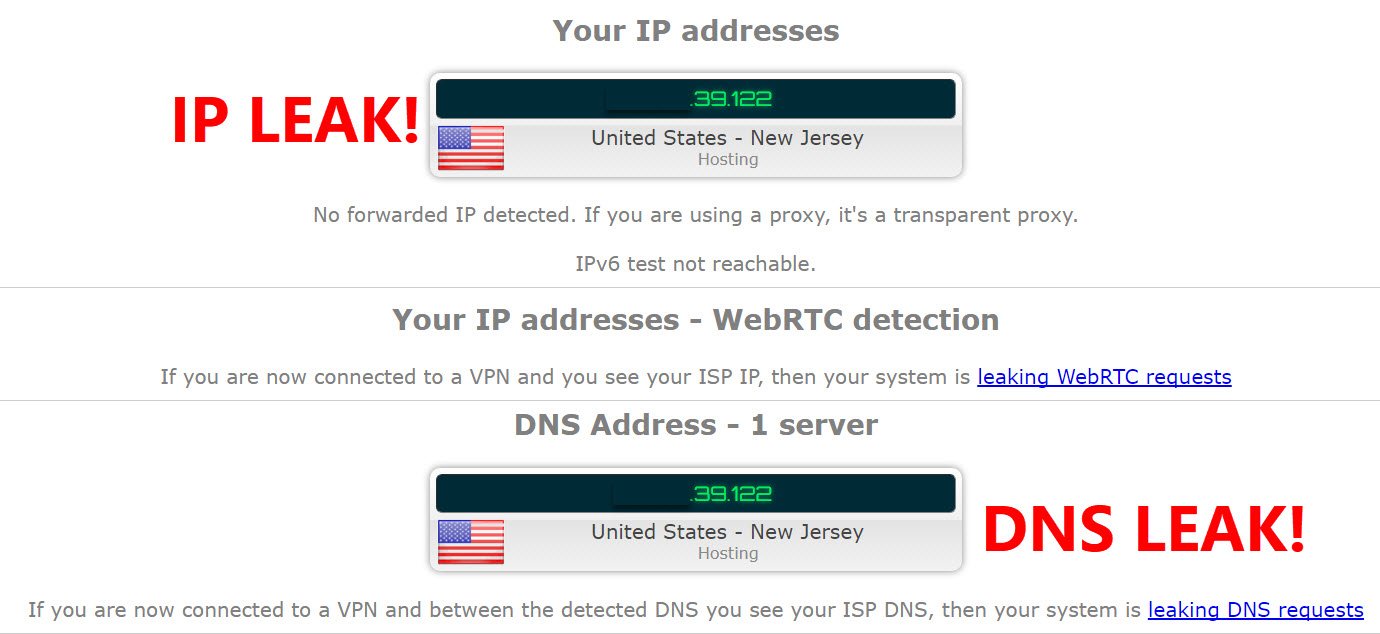
-
@AKEGEC : your second rule : include TCP.
Your first rule : WAN is blocking everything, even for these devices :
but for some odd reason Pfsense responds differently with different hardware
so the default block all rule will do it's job. If for some "odd reasons" devices could penetrate the firewall I recommend changing the firewall and/or the person that admin's it.