Continual radius authentications from admin user
-
Hi,
I've configured radius authentication on my HA Pair of pfSense firewalls, it authenticates without issue. My issue is that it is continually sending radius requests as the admin user which is flooding my radius servers logs which is not ideal.
I have tried a couple of things to no avail.
I tried setting the authentication to authenticate only, not authenticate and authorize.
I tried adding the admin user on my radius server to see if it just needed to authenticate once and authentication would stop.
I tried setting the authentication timeouts to the max timeout values.a sample of what i see on my radius server.
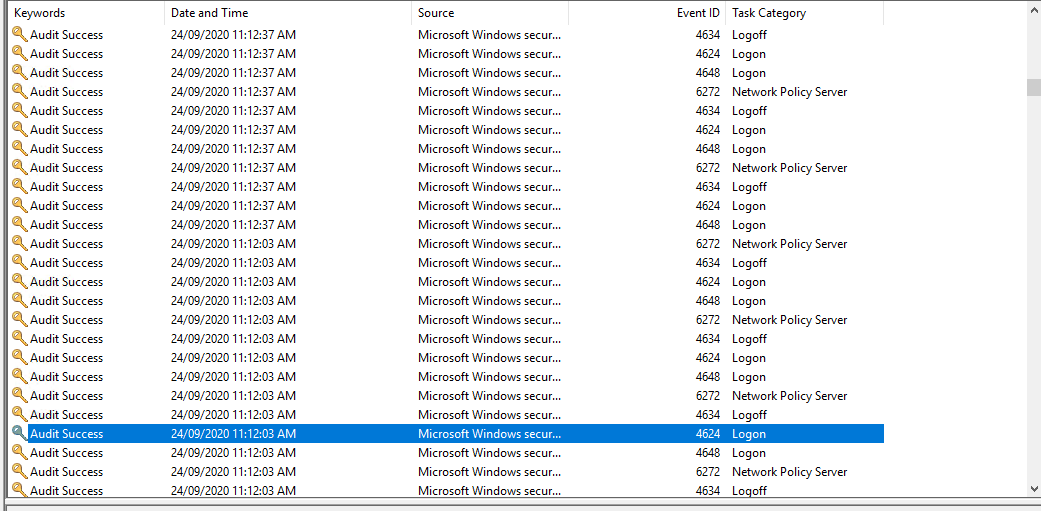
If you want any further info configuration setup etc let me know.
version: 2.4.5-RELEASE-p1 (amd64)
Thanks,
Scott -
It sends a request on every page load to ensure that the user still has access. To do otherwise is insecure. For example, if "baduser" was logged into the firewall and you terminated their account in AD, the very next page would fail to load. Without that per-page check, they'd continue to be able to work in the firewall until their session was invalidated (idle timeout, rebooting the firewall, etc)
-
Thanks for coming back to me, that makes complete sense. however we don't have the admin user logged in at all.
I am thinking that this could be caused by CARP using the admin user to perform operations with the admin user. I believe this is most likely going to be expected behaviour.
I'll look to filter out the logs.