Outgoing traffic being blocked to strange dns servers
-
that IP is a cloudflare IP
cf-198-41-223-131.cloudflare.com
I don't think pfsense would do would be talking to that for its own stuff, but it could be some package using loopback (unbound) directly that is resolving.
Out of the box pfsense would just check if there is an update, and pull listing of packages, etc.
But if you have say pfblocker trying to download lists of IPs and such, then it could be asking unbound directly, which would resolve where ever that domain is..
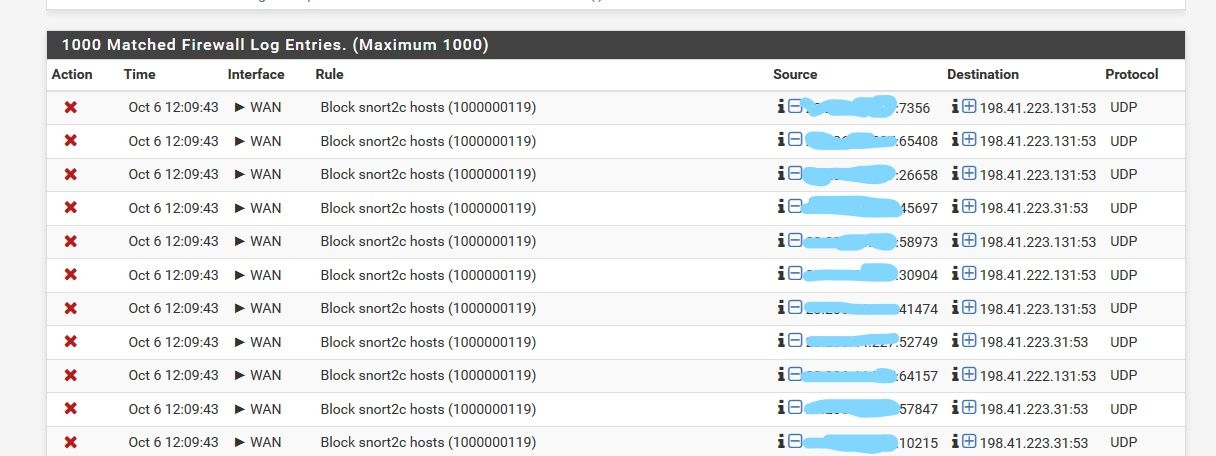
Why is snort blocking it? What does the snort log say? Snort likes to block specific tlds that it feels are not legit.. or used for bad stuff.
-
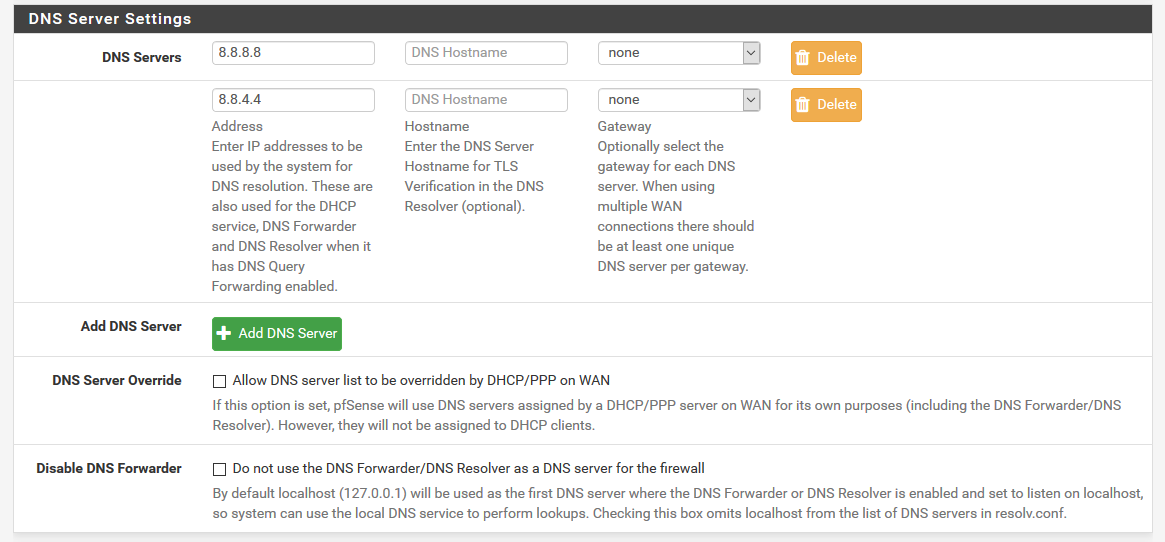
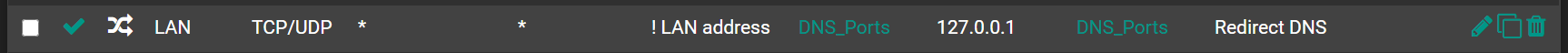
Try a NAT rule. Will force all LAN DNS to pfSense.
-
So, I tried blocking requests on lan for port 53 that weren't going to the firewall directly, and all of a sudden my zimbra server started complaining. Not sure what it's doing, since it's resolv.conf file is the same as every other client, i.e. use the firewall for dns. It starts to fail to respond to smtp requests of all things.
-
Also, I suspected pfBlocker and such, but like I said, I have the same configuration on a different firewall and I don't see it. I only have zimbra on the firewall that's giving me a problem.
-
@stepariley said in Outgoing traffic being blocked to strange dns servers:
So, I tried blocking requests on lan for port 53 that weren't going to the firewall directly, and all of a sudden my zimbra server started complaining. Not sure what it's doing, since it's resolv.conf file is the same as every other client, i.e. use the firewall for dns. It starts to fail to respond to smtp requests of all things.
If you cannot change the DNS settings on the host, however, by adding the NAT suggested by @provels you can direct its request to pfSense without taking a notice.
-
I just added the NAT rule suggested. Checking the log, I still see the same snort messages. So, I'm not sure what this means.
-
Also, putting some filtering in place, I don't see any logs showing requests coming from LAN that don't go to the LAN address of the firewall or the 8.8.8.8 server.
-
You make not mention of actually setting up forwarding in unbound or using dnsmasq.
You do understand that out of the box unbound is a resolver right? Doesn't matter what you put in the dns settings under general.. Unless you told unbound to forward.
-
Where do you configure that? I don't know anything about unbound.
-
unbound is the default dns for pfsense, out of the box. It resolves, it doesn't forward by default.. So you have no need to put anything in dns for general, or even get dns from isp.
Its under services menu, dns resolver.
-
Ok, so I looked in the resolver, and I saw that my Enable Forwarding was turned off. I turned it on, and I haven't seen any snort warnings in the last 10 minutes since then. So, maybe this is snort being overly aggressive on outgoing dns queries? My other firewall was the same, and I never got any snort errors.
-
So you would have to look in the snort log for why something was specific blocked. But I do know it can be very aggressive for specific tlds, like biz as example.. and some of the other ones that are cheap and not really used for normal major business..
I do see with that specific IP a wuai.biz related to it - atleast at one point in time, as well as ns4.cloudflare.net etc.
-
Yeah, I will look at the snort logs for that, but I think for now, I'm happy with the firewall not going out to the root dns servers. Just makes me nervous to see queries like that, especially when they are going outside the country.
-
And where do you think they go when you forward to 8.8.8.8 ;)
That is an anycast IP, you have no idea where the actual server that answers you might be..
-
Yeah, I realize that, but at that point, I feel it's someone else's problem.

-
Huh, Im not talking about where they go to resolve.. You have no idea where the actual servers are that your asking.. While you hope they are close to you - its an anycast IP.. It could be anywhere on the planet, in your country or not, etc.
Not sure why should be concerned with directly talking to the authoritative NS you asked for.. Its not like your resolving for anything your own devices didn't ask to resolve, etc.
But sure if you feel better handing over everything you look for to 1 company.. Then sure do that.
-
My main concern is that snort trusts it. Before, all my dns queries were being blocked by snort. Maybe I'll spend time figuring out why that is at some point, but I have other things to do.
-
@stepariley said in Outgoing traffic being blocked to strange dns servers:
My main concern is that snort trusts it.
Not sure what you mean by this statement?
Before, all my dns queries were being blocked by snort.
This statement says that you have Snort misconfigured and are most likely running it in Blocked Mode. Until you get it tuned to your system, YOU SHOULD NOT run it in Blocked mode. Also you should not enable ALL the rules in Snort until you learn what each rules is looking for other wise you will get all kinds of false positives blocks with it. It can take several days, weeks or even months to get it tuned to your system depending on what your doing on your network.
-
No, I'm not.
-
@stepariley said in Outgoing traffic being blocked to strange dns servers:
My main concern is that snort trusts it.
Yeah, lol, Snort trust 8.8.8.8. .....
@stepariley said in Outgoing traffic being blocked to strange dns servers:
Before, all my dns queries were being blocked by snort
Snort will trust the main 13 Internet Root servers., as without them, you might as well cut the connection and go live in the forest. Snort will probably 'trust'"all tld servers, like com net org etc.
But Snort might kick in when the resolver hits the final stage : the third level is reached : the domain name servers. because they are listed as they give the IP to sites that are listed - and you want them to visit these sites.
8.8.8.8 will hide all this for you, as it does the job for you, it a resolver just like Unbound (and data mine while doing so - so they can give you the 'right' answer for you ^^).So, again :
@stepariley said in Outgoing traffic being blocked to strange dns servers:
Before, all my dns queries were being blocked by snort
You are trying to visit sites that are listed in Snort.
Up to you to decide :
The lists are wrong - adapt them,
Or,
Stop going there.