randomly blocking network access from one lan to another, reboot helps
-
Yes that should be fine.
If you are policy routing the traffic from LAN_1 you may find it is able to reach LAN_2 until the gateway comes up. So a VPN gateway defined there might see changing connectivity.
You should generally have a pass rule for local traffic above any policy rule if that is the case.If you see no states opening at all then it's not matching any rules or something is blocking it.
Or potentially that traffic never arrives at pfSense at all. Like the client on LAN1 gets a bad subnet mask from somewhere, a rogue dhcp server for example. I would run a pcap on LAN_1 to prove that traffic is arriving there.
Steve
-
Thanks a lot for your reply :)
I will test this. As this is a long-term problem, it will take some time to verify that the gateway is the problem. I already realized that my vpn-client connection sometimes drops, so i think that your explanation is plausible
I will also try running pcap to verify that traffic arrives -
If you have policy routing rules on LAN1 they could well be doing something differently.
Can we see those rules?Steve
-
Sure, here they are:
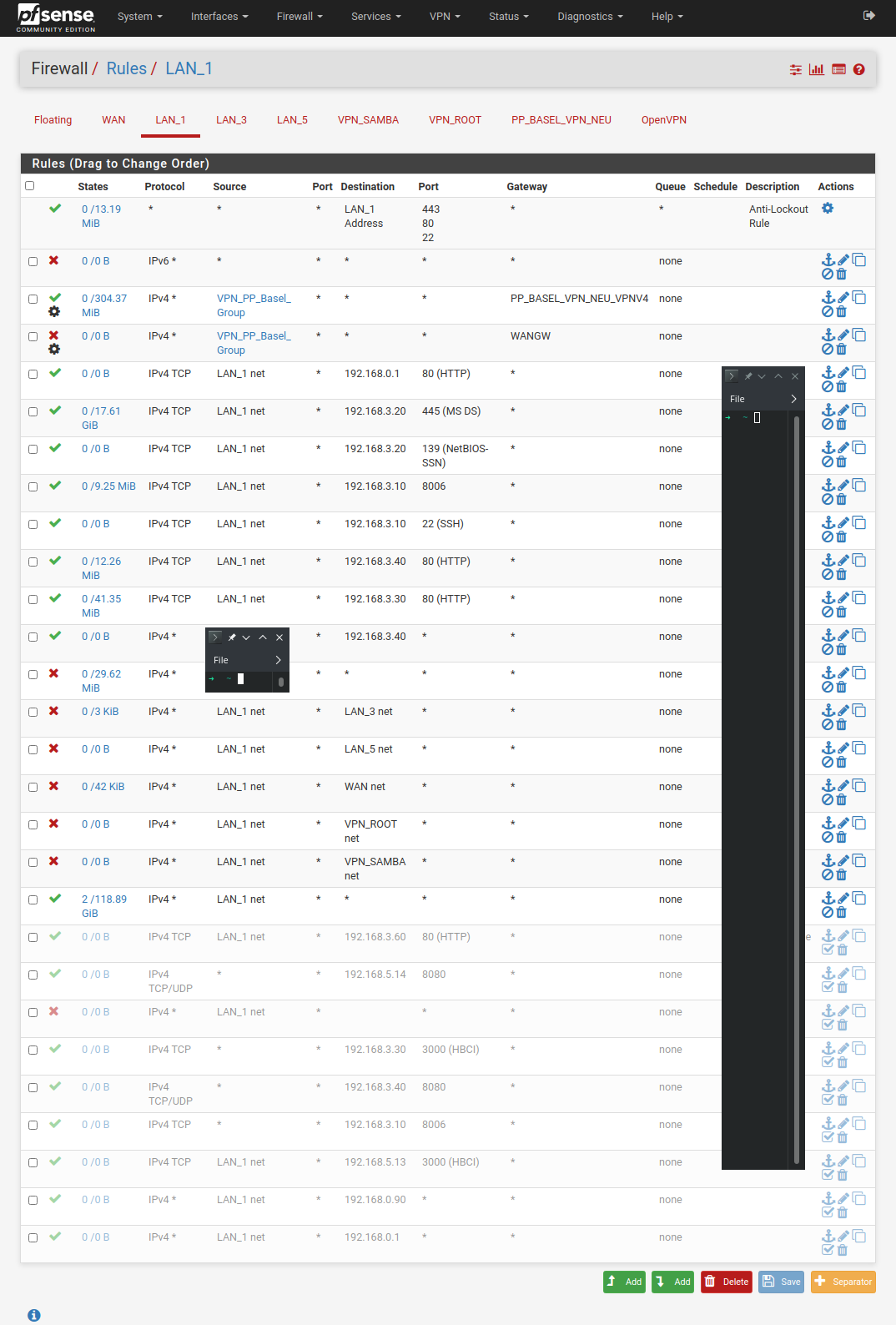
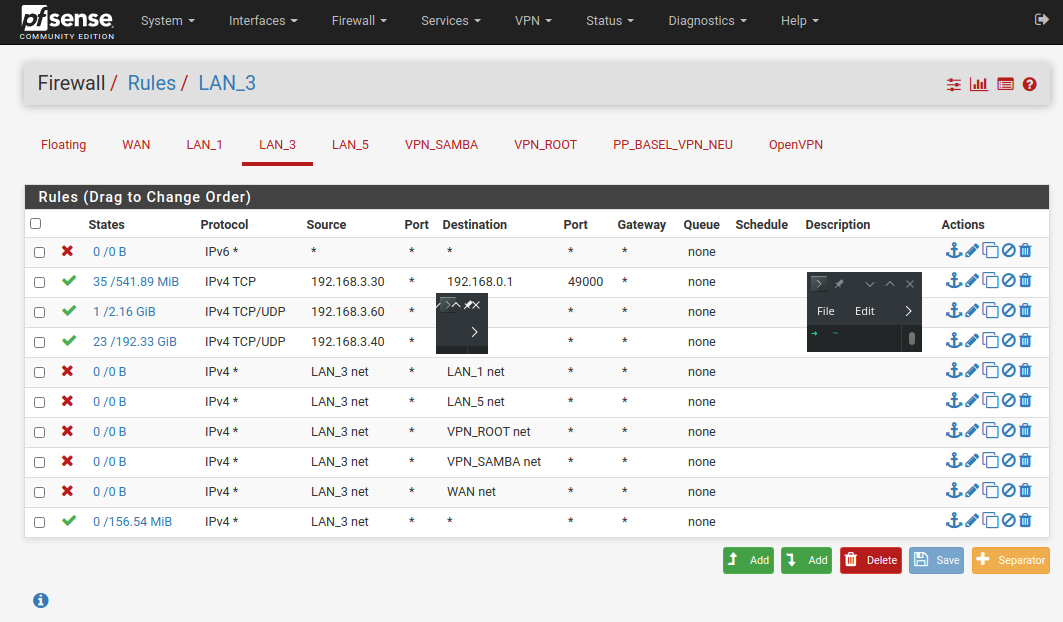
-
So is the client you're testing from in the VPN_PP_Basel_Group?
In System > Advanced > Misc do you have 'Skip rules when gateway is down' set?
Setting a gateway on a block rule like that is invalid. It doesn't block only traffic to that gateway. That may be what you're hitting.
Steve
-
@stephenw10 said in randomly blocking network access from one lan to another, reboot helps:
Skip rules when gateway i
No, the client i am testing is from the LAN_1 NET
No, i dont have 'Skip rules when gateway is down' enabled
I will try to change the gateway block rule and see if that changes the behavior.
-
Right but the VPN_PP_Basel_Group alias must contain hosts that are in the LAN_1 subnet since it's being applied on LAN_1?
It shows 0 state creation though so it hasn't matched any traffic since the last filter reload.
Steve
-
yes, they are in the lan_1 subnet
and it hat 0 states because the VPN_PP_Basel_Group is only used occasionally.
(havent used it since i reloaded it in that screenshot, it should be configured to route all traffic through the vpn-gateway when using an ip address above 192.168.1.200) -
Hmm, Ok. Nothing else has a gateway set so I would not expect any policy routing issues to affect it. The block rule with a gateway is still invalid though. I would not expect it to do anything but I'm not sure I've ever tried so I'd remove/disable it anyway.
I assume whatever you're trying to hit in LAN_3 is covered by one of those pass rules? 192.168.3.20?
Steve
-
Okay. i have had the problem that if the PP_BASEL_VPN Gateway is down, the traffic for VPN_PP_BASEL_GROUP is then routed through the normal WANGW. But i want to make sure that no traffic is leaving the VPN_PP_BASEL_GROUP through the WANGW.
Is there an other way to do this?Yes, i am trying to reach the samba server on 192.168.3.20. But its not only 192.168.3.20, its the whole subnet that i cannot reach when it happens.
-
If you set 'Skip rules when gateway is down' then the firewall will omit the pass rules for that source alias entirely rather than using a rule without a gateway set.
The block rule after it will then block all outbound traffic from it when the PP_BASEL_VPN Gateway is down.That is a global setting so bare in mind how it might affect other policy routes.
Steve
-
Thanks for your answers, i will try to fix the problem by changing the rules and by setting the 'Skip rules when gateway is down' option. i will write here when i know if it helps.
-
The Problem came back.
The PP_BASEL_VPN rules have been disabled, the "Skip rules when gateway is down" option was enabled.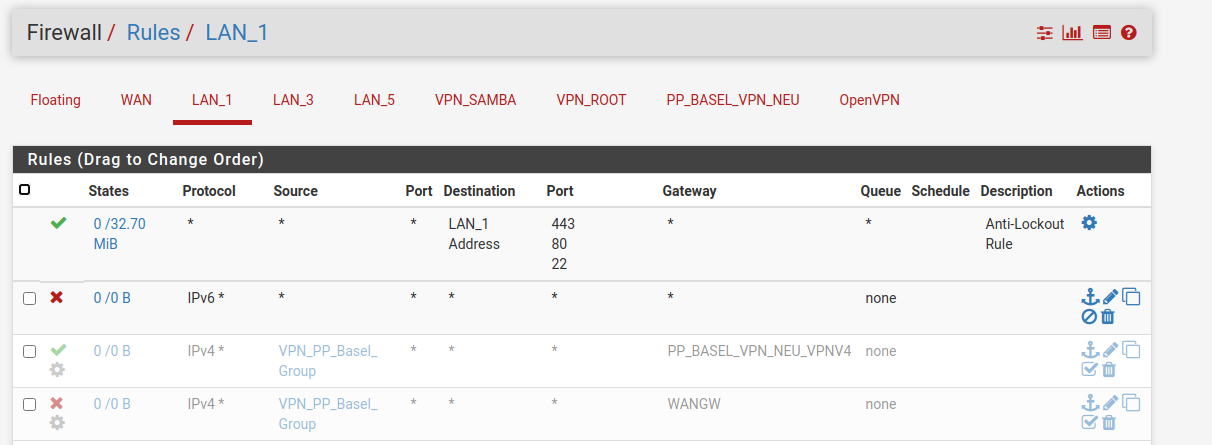
Is there anything i can do to investigate this problem further?
-
So you are still trying to reach the LAN3 subnet from LAN1?
There are no rules shown in that screenshot to allow it but I assume you still have them below that?
That traffic could be blocked by a floating rule. Or by Snnort/Suricata if youlre now running either.
Steve
-
yes, i am stil trying to reach LAN3 from LAN1
i have not changed any rules, only the two greyed VPN-PP-Basel_Group rules are disabled, thats the only difference
Here are my floating rules:
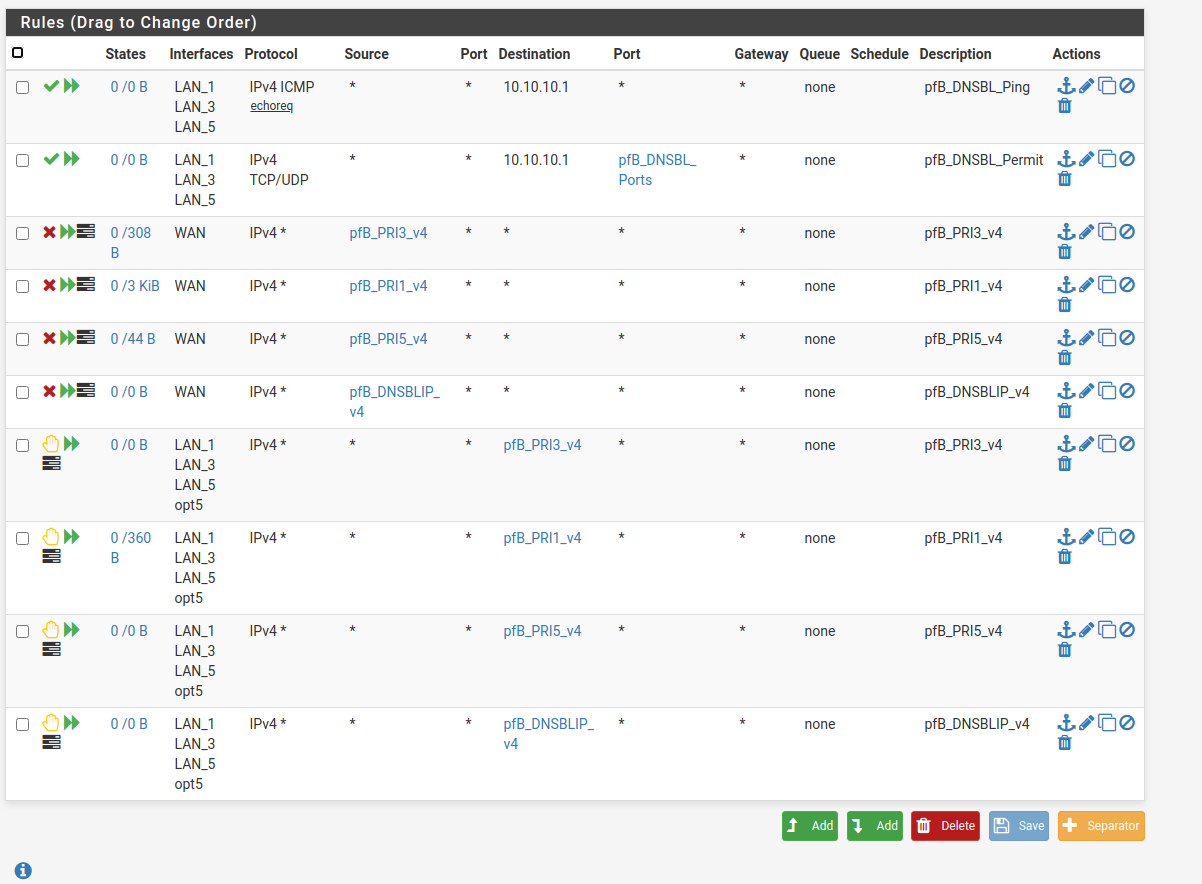
I am not running Snnort/Suricata
-
OK well, as before, try to connect, start a continuous ping for example, then check the state table to see where it's opening states. Is it just trying to leave the WAN? Is it opening no states?
Check the firewall log.Steve
-
i tried pinging from LAN_1, LAN_3 and LAN_5, resulting in total packet loss everytime.
the state table does not show any related state, it is nothing showing up when i start pinging.
the firewall also does not contain anything regarding the ip address i am trying to ping or the source address i am trying to ping from.The whole subnet is totally unreachable.
One of my services running in LAN_3 is a Telegram Bot. It is also not responding to messages. -
Ok, so if it's not opening states anywhere then the firewall is preventing that. You don;t have rules that are allowing that traffic.
Post your full LAN_1 rules and the exact test you are using from a client on LAN_1.
Steve
-
@rafthebee , Did your try to create a pass rule to allow LAN3 to talk LAN1? Make sure the protocol set to ANY and the rule is above other rules and don't forget to apply changes.