Can a gateway be assigned to an interface?
-
What part do you not understand here?
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html
You can route whatever IPs you want that are in a specific vlan, with a simple policy route rule on that vlans interface.
If you want 192.168.1.X to use tun1, then set a rule for that. Then you could have 192.168.1.Y use tun2.. And .Z use default or anything you want really.
If a client does not trigger a specific rule that shoves it a specific wan gateway.. Then it would use whatever you have as a default catch all rule at the end, which could go out any of the tunnels or just the default wan. If it doesn't match any rules then it would be denied.
You would not put a gateway directly on an interface, unless its a WAN interface.
-
Yeah I understand all of that, and also thank you to both for answering, what I mean is a default per gateway but not a catch all rule, for those tighter-controller interfaces where there's soo much repetition that something simple like clicking on advanced and scrolling down to select a non-default gateway is a huge task.
Something more or less like voici:
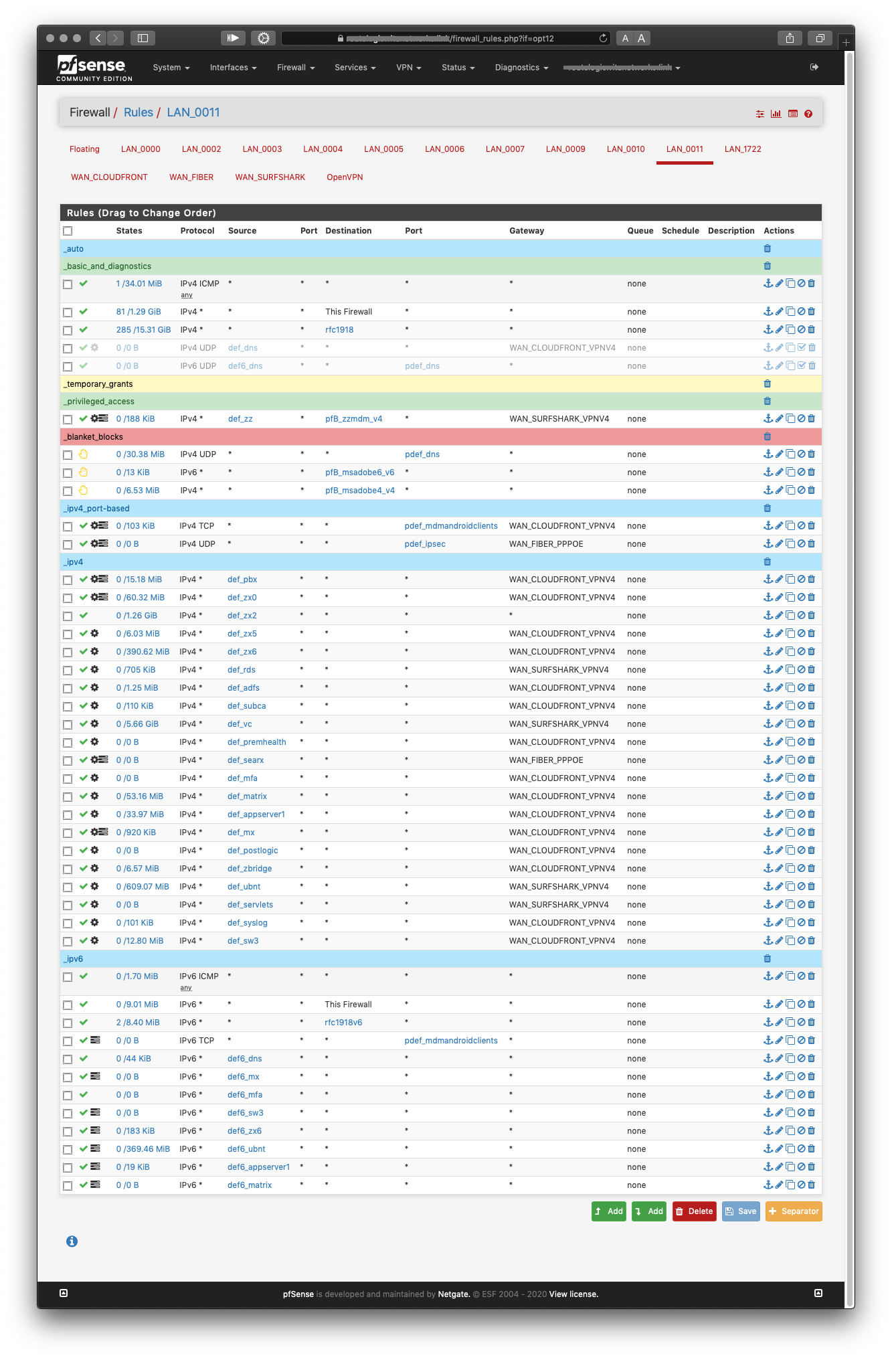
…now picture that on a haphazardly populated /22 or bigger with most of the hosts not going out via the default route. Just copying random text from one browser window to another side by side, is enough disorient me…
If you look in the closely the shot, under _ipv4 you'll notice that only 1 host is using the default gateway (2 with the other that has it enforced) and there is no catch all rule because, well, what you guys said. Fortunately my network is very small but it still got me thinking how would that work for huge deployments. Where it's so random maybe with even more gateways you can't just set an alias to group them nor employ dynamic routing, like I assume most people would.
A per-interface default gateway sounds like the way to go if it was real, then I would've just chosen "…CLOUDFRONT…" and just add basic rules, and only select it to enforce it, to skip the intranet, for instance. Basically like 1:1 NAT firewall rules but for gateways.
Um… Did I just invent something?

-
Huh?
If you don't want to shotgun your access, then put all the devices you want using tun1 on vlanX, and devices using tun2 on vlanY.
And create the policy route on that vlan to use the gateway you want on that vlan.
What do you think a per-interface gateway would be, other than a catchall rule that sends all traffic hitting this interface out a specific gateway. Or just using the default routing of pfsense to determine which gateway traffic should flow.
You know you can create routes that use specific gateways right, now depending on where the traffic is destined to go would determine which gateway is used.
-
You mean floating rules right? Filter on the out?
If so sure, I'm using floating rules as well, I actually very recently redid a lot of stuff in floating to clean it up, there are just times when you can't separate hosts at layer 2.
As I said, I'm lucky my network is easy to deal with but I daydream and stuff. I imagine like a dropdown on top of the interface view where you'd select that allowed traffic without a gateway set would go to the default route, except this would not be the global default but the default for that imaginary example interface, y'know? Like setting a catch all that won't actually allow anything in unless it's actually added as another rule.
I believe Match rules do this too, but TBH that's the one topic (policy filtering, right?) I can't get my head around, it's not as extensively documented as the rest.
-
If you want to use a floating rule to send all traffic out a gateway, yeah you can do that..
Im having a hard time getting where your having trouble..
If you want all clients on vlan X to use tun1, then create rule on vlan X, or ok a floating that says use tun1..
If you want clients to use tunX to get to dest 1.2.3.4, then create that rule, or just create a route entry and use the default routing. Or if you want them to use tunY for http or ftp, or some protocol you can do that too.
Having a hard time getting the use case on why you would want some shotgun approach to why client A uses tun1, or client B uses tun2 and in what scenario that could change, etc.
From my take your over complicating it.. You can sure set vlanX to always use tun1, and if you want some specific client on vlanX to use either just the wan or tun2 you can do that too - with a simple rule..
If your doing this for 100 or 1000's of clients then yeah it can get complicated.. How would an interface gateway make that any different? If you want to simplify it, simplify your choice of which gateway to use.. Just let pfsense do load sharing, or whatever or set all vlanX to use 1, and all vlanY to use 2.. Don't start picking some client in X to use 2.. Move him to vlanY if you want him to use 2.
Your 2nd image is very possible - and easy to setup... But yeah if you start getting complicated with your choice of what client uses what - then yeah its going to get complicated ;)
example: vlan 7
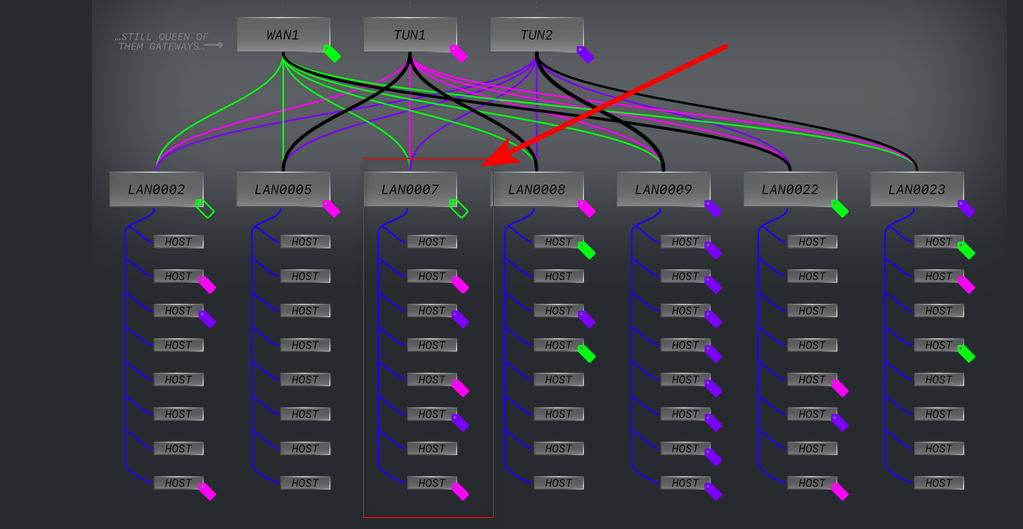
Way I read that is if client IP doesn't see any rules that sends him out a gateway, he just uses the default wan1.. if client X, can be set to go to tun1 or tun2 based on your rules.
This is basic policy routing.. be it the rules that send them out the gateway are in floating, on the interface. And could be based on his IP, his dest IP, or port, etc.. But yeah if you have 1000's of clients and start wanting to say XYZ for this client, and ABC for that client, and then XAY for that client -- sure it gets complicated very quickly.. Not sure how that has anything to do with pfsense? How would setting a gateway on an interface fix your choice of shotgunning what client uses what wan gateway?
If you choose to make it complicated, then yes its going to be complicated. Or you could simplify it.. Lets say you want all clients on your network to use tun1 when they go to 1.2.3/22 - then create a normal route pointing 1.2.3/22 to use tun1.. etc..
Can not help you with what I don't understand... Why does client X need or why do you want it to use tun1 vs 2?
example of trying to simplify it... Let all your vlans just default to use wan. Create an alias for tun1 and tun2.. No put all the clients you want to use tun1 in alias1, and all client that use tun2 in alias2
Now on your floating that is quick and on all interfaces set a rule that alias1 clients use tun1, and clients in alias2 use tun2..
edit: Anything can get complicated if you choose to..
I have some coffee beans.. I can put them all in a jar labeled coffee.. Or maybe I want to sort them by type (Arabica or Robusta, Liberica), also by roast, then by size of bean. Then by if free market or fair trade.. Pretty soon I have 1 single bean in a 1000 different jars.. And then how do I choose which bean goes in which jar when the bean meets multiple criteria.. So I have another jar for beans that match multiple criteria, and it goes on an on..
Looks like here your picking your beans on some different criteria (IP) - but then putting them all in the same jar? (cloudfront_vpn)
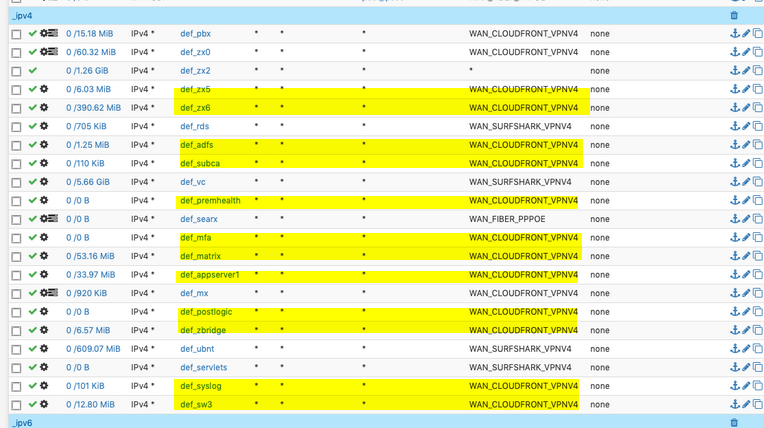
Why not just have 1 alias, that lists all the IPs you want to use cloudfront_vpn4 gateway? That would simplify it vs this bean free market, and this bean is dark roast, and that bean is Arabica..
-
No-no-no!
 I'm not saying it has to do with pfSense, I'm saying it'd be nice shortcut to selectively assign default gateways per interface. A quality of life improvement, like the widgets on Dashboard page.
I'm not saying it has to do with pfSense, I'm saying it'd be nice shortcut to selectively assign default gateways per interface. A quality of life improvement, like the widgets on Dashboard page.I get what you're saying, seriously I do, but can we agree that it is not always possible to sort hosts based on a common predominant trait no matter how much sense it makes? (I'll just assumed you begrudgingly nodded, arms crossed)
Sometimes, like on my network here, the real one, not the example, most hosts that will be allowed out, actually happen to have on characteristic in common, the chosen gateway for them. It also happens not to be the default gateway of the router and there's NAT involved on each gateway, a no-no with floating rules, right? (you nodded again)
My solution was pretty straightforward, I just cloned a similar rule and changed the host. But it could be a valid choice to to just switch the overall default for that interface because there are times when you still need it defined in a rule, like bypassing the network and the firewall itself, like I mentioned earlier, then if I were to change these rules (again, it's just hypothetical) instead of creating a fresh set of clones, changing a single setting would be much quicker.
Ain't that the whole reason behind pfSense? Making things easier, understandable, CLI-less…?
I gotta run to the vet, it's been fun though, I'll check what I miss later. :)
-
I don't believe that this is a problem in most scenarios. Either you have only a few "pass" rules, then it's easy to maintain, or you have very many "pass" rules, then it's just one additional parameter to maintain for each rule. I get your point, but for me, the main problem would be to maintain so many rules and not so much maintaining one parameter more for each rule. So the main goal should be to reduce/combine rules, e.g. using aliases.
Having a different default gateway per interface could maybe reduce some maintenance work a bit in very specific scenarios, but I believe in most cases it would cause even more confusion which gateway is used in which case by adding a additional layer to the already existing ones. And the solution would be only for one parameter, the gateway. After your last post, I believe what you are actually asking for and what would be a bit more generic, is some kind of "template" rules, or rule "inheritance", so you set the common parameters (like the gateway) only once in the parent/template rule and can overwrite it in the child rules.
-
@skilledinept said in Can a gateway be assigned to an interface?:
s not always possible to sort hosts based on a common predominant trait no matter how much sense it makes?
Agreed.. But you don't put a gateway on the interface... Your catch all rule at the bottom of the rule list is the rule that allows the traffic if it does not meet any other criteria.. This is where you would say hey traffic that doesn't meet any of the above criteria - send it out this gateway.. Which would be default routing ie no gateway selected "*" or some specific gateway..
This is how you put a default gateway on a interface, not on the actual interface.. Doing so tells pfsense hey - this is a WAN interface..
edit: Here 1 sends all traffic that got to that last rule and passes out the default gateway, using pfsense routing. 2 sends all traffic that last rule catches out my vpn gateway..
Its really that simple.
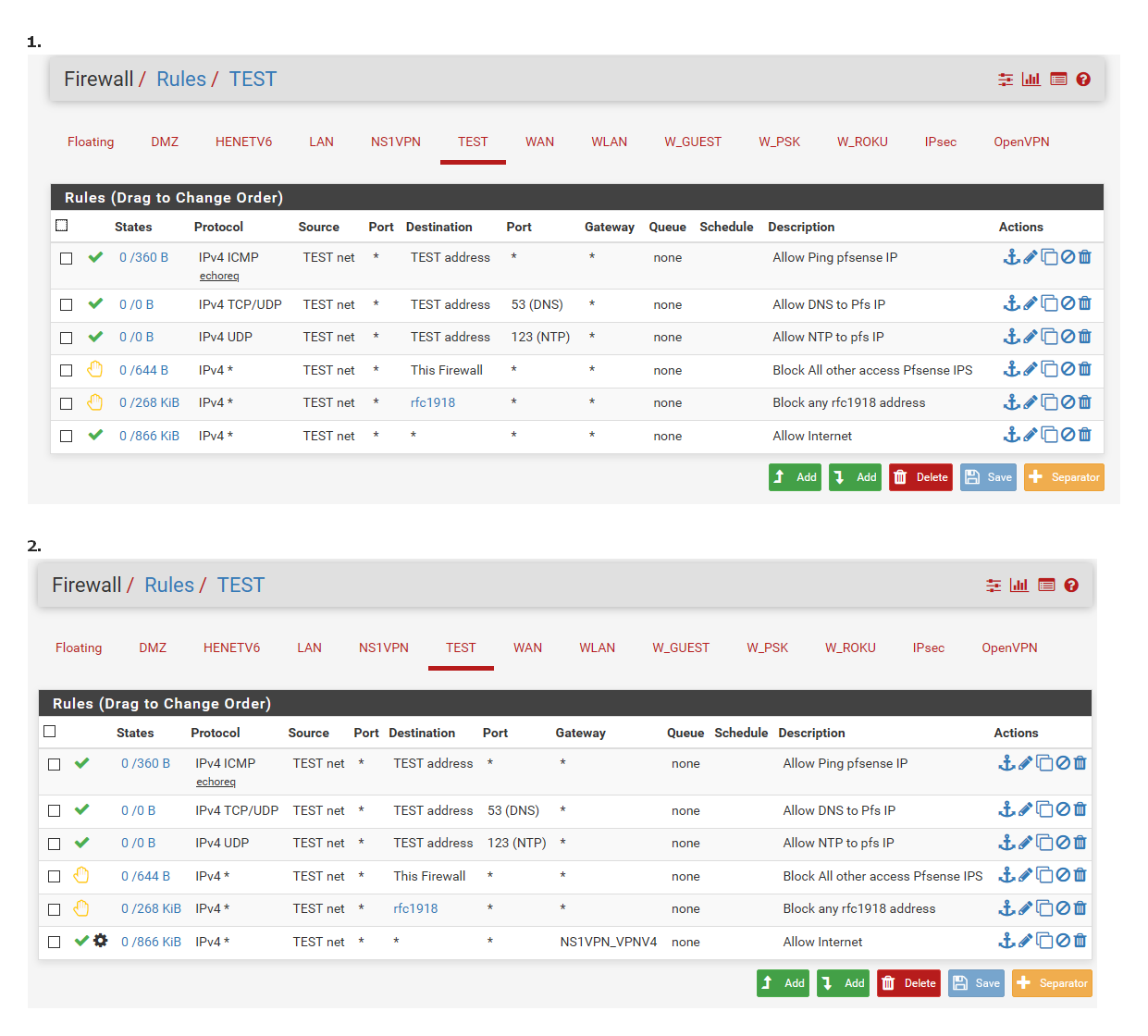
If some traffic doesn't pass any rules, and either use the default routing gateway, or get showed out some other gateway.. Then its denied by default.. Traffic always has to hit an allow rules to go out any gateway... Setting a gateway directly on the interface is not what you do, this again tells pfsense - this is a WAN connection and treat it as such, ie setup it for outbound nat, etc.
-
@johnpoz said in Can a gateway be assigned to an interface?:
send it out this gateway..
I believe @skilledinept doesn't what to say "send it out this gateway", but "send it out this gateway, but only if I allowed it to pass in another rule (but didn't set the gateway there because of the effort)", because he still wants to control host by host who can go to the Internet at all. But he could use an alias for the source of course instead of the whole net.
-
You could get fancy with the rules, and use rules that mark the traffic based on criteria, and then use those markings in your rules to allow or block, etc.
You can do that with floating rules, that are not set as quick..
So you could mark or tag traffic based on criteria XYZ, and then in later rule on floating do something else with it like send it out a specific gateway. Or on your interface rules look for specific tag and then do X with it..
So he could in his floating rules, non quick set a tag for traffic to tun1, or tun2 or wan.. Then in the interface or floating (later down the rule set) set a rule that is quick that sends it out a specific gateway, or on the interface have rules that say if tagged tun1 send out tun1, if 2 out tun2 if wan out wan, etc. etc..